Privileged Identity Management (PIM) is an important aspect of Azure Active Directory that helps organizations manage and secure their critical resources and systems. However, just having PIM in place is not enough. It is equally important to have proper controls in place to ensure that only authorized users can access the privileged resources. This is where the Conditional Access Authentication Context comes in.
To make things more convenient, Microsoft has also extended the capabilities of Azure AD authentication context to Azure AD Privileged Identity Management (PIM), which is currently in public preview. Let’s get started with authentication context in Privileged Identity Management!
To understand the configurations better, let’s begin from scratch.
What is Privileged Identity Management (PIM)?
Privileged accounts have extensive access to critical resources in an organization, making them a prime target for attackers. Azure Active Directory Privileged Identity Management (AAD PIM) helps manage these accounts, reducing the risk of abuse and unauthorized access. AAD PIM helps organizations achieve this by providing just-in-time access and access reviews for privileged roles, limiting the risk of privilege abuse and unauthorized access. As an admin, you have the flexibility to choose between managing Azure AD roles, Azure resource roles, or PIM for groups based on organizational needs. Azure AD Premium P2 license is required to use Privileged Identity Management in Azure AD.
PIM provides protection at the role level. If you want to apply protection at the task level in your organization, you can implement privileged access management in Microsoft 365 to safeguard your critical resources.
What is Conditional Access Authentication Context?
Authentication context in Microsoft 365 is a security-enhancing feature that adds more details to access requests, including device information, user location, etc. To put it simply, authentication contexts are more like sensitivity labels. With the authentication context, a tag is created that allows you to label the resources that need protection and control access to those resources in a more granular way. Authentication context labels can be used in conditional access policies as well as sensitivity labels.
In addition to protecting sensitive data, authentication context can also be used to protect applications that are hosted in Azure. This can prevent unauthorized access to critical applications and reduce the risk of security breaches.
Setup Conditional Access Authentication Context in Privileged Identity Management
As mentioned earlier, extended capabilities of Azure AD authentication context to AAD Privileged Identity management are in public preview now! Wondering, what can be done with this new functionality? Check out its benefits below.
- By combining AAD PIM with authentication context, organizations can create a robust security framework for privileged identities.
- When a user requests access to a privileged role or resource, authentication context is used to evaluate whether the user meets all the security requirements for that role.
- With authentication context, organizations can monitor and track user access to privileged roles or resources, providing greater visibility and insights into potential security threats or compliance issues.
Note – To configure Authentication Context in Azure Active Directory Privileged Identity Management, you must have global administrator permission with Azure Active Directory P2 license.
Create Conditional Access Authentication Context
Learn how to configure Authentication Context in Azure Active Directory below:
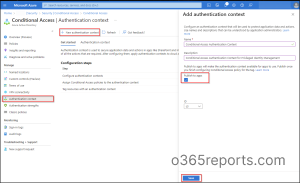
- Sign into the Microsoft Azure Portal.
- Navigate to Azure Active Directory –> Security –> Conditional Access –> Authentication Context.
- Select + New Authentication Context.
- Then add the authentication context by providing a proper name and a description.
- Make sure the Publish to apps box is checked in.
- Click Save.
Create a New Conditional Access Policy with Authentication Context
It is recommended to create a Conditional Access policy before configuring the authentication context in PIM settings because it provides an extra layer of protection for your system. When someone elevates their role using Azure AD PIM, we can trigger a Conditional Access policy to be executed.
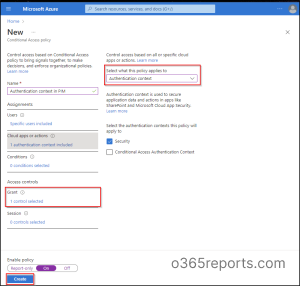
- Sign into the Microsoft Entra admin center.
- Navigate to Azure Active Directory –> Security –> Conditional Access –> Create new policy.
- Give the policy a proper name.
- Scope the policy to eligible users of the role.
- Under Cloud apps or actions, set the policy applies to Authentication context.
- Then choose the respective authentication context you want to apply to the policy.
- Under grant, go to Grant access –> Require authentication strength –> Phishing-resistant MFA and click Select. If you want, you can also use the “Sign-in frequency – Every time” to activate Privileged roles in Microsoft 365.
- Set the policy status to On.
- Click Create to save your policy.
Note – You shouldn’t create a Conditional Access policy that is scoped to both authentication context and directory role during activation since the user does not have a role yet.
How to Tag Authentication Context in Privileged Identity Management Role Setting?
Learn how to tag authentication context in Azure AD privileged identity management role setting. We previously had only the option to require MFA for the elevation of an Azure AD when defined in PIM.
Now Microsoft has elevated Privileged Identity Management capabilities by allowing us to specify the Azure AD Conditional Access authentication context!
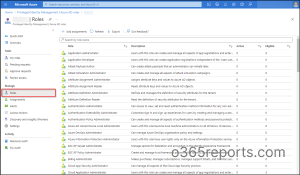
- Sign into the Azure Active Directory portal.
- Navigate to Azure AD Privileged Identity Management –> Azure AD Roles –> Roles.
- Select the role whose settings you would like to configure.
- Open the Role settings of the selected role. Your current PIM role settings will be displayed there. Here I have selected ‘Application Administrator’.
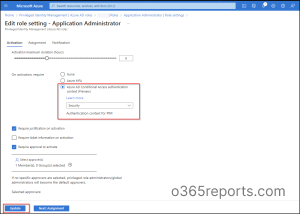
5. Click on Edit.
6. Choose the Azure AD Conditional Access authentication context (Preview) under the activation setting.
7. Select its dropdown there you can spot the existing authentication contexts.
8. Select the suitable Conditional Access authentication context.
9. You can specify approver based on requirements. If no one is specified, privileged role administrators/global administrators will become the default approvers.
10. Select Update.
Real-Time Testing on Azure AD Role Activation:
Learn what will happen when a test account that is not part of the Authentication context tries to activate the role.
- Sign into the Azure Active Directory Portal.
- Navigate to Azure AD Privileged Identity Management –> My Roles.
- Select the Application Administrator role and click Activate.
- Then you will be prompted to a window where you will see the following message. “A conditional access policy is enabled and may require additional verification. Click to continue.”
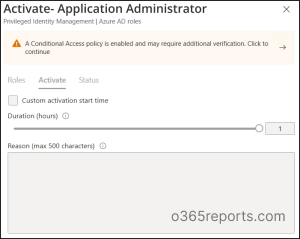
Additional Verifications during PIM Role Activation:
So, what will happen during PIM Role Activation?
If the user does not configure the strong authentication method, you will be asked to add an additional authentication to complete the sign-in.

If the strong authentication method is already included, you must complete the verification process to access the intended Azure AD role.
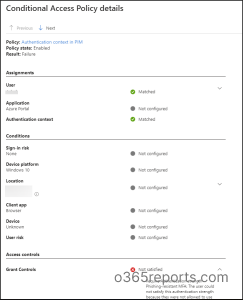
Check Azure AD Sign-in Logs for CA Policy Insights and Reporting
By monitoring the sign-ins in Azure AD, it is possible to verify if the user has fulfilled the conditional access policy requirements or not. These Azure AD sign-in logs help organizations in identifying potential security threats and proactively implement appropriate measures.
Here’s how to access Azure sign-in logs:
After signing into Microsoft Azure portal, navigate to Azure Active Directory –> Sign-in logs.
In conclusion, Azure Active Directory Privileged Identity Management and Authentication Context provide organizations with the means to efficiently manage their privileged identities and safeguard sensitive resources from unauthorized access. It’s worth noting that CA authentication context is not only applied for Azure roles but can also be equipped in PIM for Groups. Therefore, you can enhance PIM group security by incorporating Conditional Access within PIM for groups.
I hope this blog helped you understand authentication context integration in Azure AD privileged Identity management. If you have any queries, feel free to reach us in the comments!