Are you sure organization users are accessing only via the authorized device? Are all the devices used by your users utterly safe?
Nah! Every device used to access cloud-based resources possesses a severe risk of becoming a pathway to cause major cyber-attacks like data breaching, phishing, ransomware, and many more. Devices usually don’t play a role in identity-based attacks, rather they are used as trump cards to trick security with the impersonation of users.
Therefore, as an admin, it’s essential to monitor devices used within your organization for effective defense systems, Azure AD device management, and compliance management and maintain security & regulatory compliance.
And therefore, to help admins with this task, this blog provides a PowerShell script to get Entra ID devices report. With this script, admins can gain a better understanding of their organization’s device landscape, and easily identify potential issues or risks. Without further delay, let’s get into the reporting zone quickly!
How to View Devices in Entra ID?
Cybercriminals may attempt to breach the security of your organization by registering unauthorized devices, using Primary Refresh Tokens on trusted devices, or stealing Primary Refresh Tokens from trusted user devices.
- Therefore, monitoring Azure AD devices essentially becomes the only solution to reduce such threats and massive attacks against your organization. Also, monitoring devices are the primitive step for managing the devices and troubleshooting unusual events related to devices.
Moreover, you can get reports on Azure AD devices either through the Azure portal or through PowerShell. These approaches are considered traditional workarounds to retrieve the necessary information. Let’s explore how to get Azure AD device reports by using these methods in the following section.
Find Azure AD Devices in the Microsoft Entra Portal
The Entra portal provides centralized management for devices, allowing admins to perform essential Azure AD device management tasks. These include configuring device join types, registering and updating devices, also reviewing audit logs for device registration activities. Furthermore, admins can easily enable or disable device access, delete devices, and manage device settings through the portal. Navigate to the path below to get all Azure AD devices in your organization.
Microsoft Entra admin center 🡢 Devices 🡢 All devices
Here you will find the details of the devices, such as name, operating system, version, Join Type, etc. But generating customized device reports is a crucial task for administrators in the Azure portal.
Moreover, the Azure portal’s reporting features are limited in terms of customization, scalability, automation, and integration, which may not be suitable for organizations that require detailed and customized reports on a large scale. Therefore, switching to the PowerShell method is the perfect solution for organizations to meet their specific reporting requirements.
Get All Azure AD Devices Using PowerShell
Previously, the ‘Get-AzureADDevice’ cmdlet in PowerShell was a workaround for slow Azure AD reporting. It helped admins quickly list all Azure AD devices in their organization and tailor output using filters and loops.
However, Azure AD and MSOnline cmdlets are being deprecated in favor of the Microsoft Graph API. Therefore, sticking to these Azure AD cmdlets for retrieving devices is not advisable!
Thus, to lend you a hand in tracking the finer details of the devices in a single click, we have provided a PowerShell script. This script is designed to simplify your device tracking process, providing a comprehensive overview of all the Entra ID devices. Let’s dive into the script’s features and explore its full potential!
Export All Entra Devices Report to CSV Using PowerShell
The Entra ID devices report shows the complete list of devices with their attributes in the organization. Therefore, admins can efficiently use this report to monitor and analyze the critical events of device registration, deletion, etc., around the workspace. Download the script now and unleash the benefits you can avail with a click!
Download Script: GetAzureADDevicesReport.ps1
Script Highlights:
- Exports all Azure AD devices in your organization.
- Automatically checks the Microsoft Graph PowerShell module and installs it upon your confirmation if it’s missing.
- Enables filtering based on following device registration types:
- Entra registered
- Entra joined
- Entra hybrid joined
- Generates a report that retrieves enabled devices alone.
- Helps export disabled devices alone.
- Find inactive devices based on inactive days.
- Includes ownership filtering to show company, personal, unknown devices.
- List all devices that have BitLocker key.
- The script can be executed with MFA-enabled accounts too.
- Facilitates filtering devices by users, owners, and groups.
- Exports the report results in CSV format.
- Allows exporting devices that match the selected filters
- Device management status – Managed / Unmanaged
- Device compliance status – Compliant / Non-compliant
- Device rooted state – Rooted / Nonrooted
- Compatible with certificate-based authentication (CBA).
- Filter devices by profile types such as IoT, Printer, Secure VM, Shared device, and Registered device.
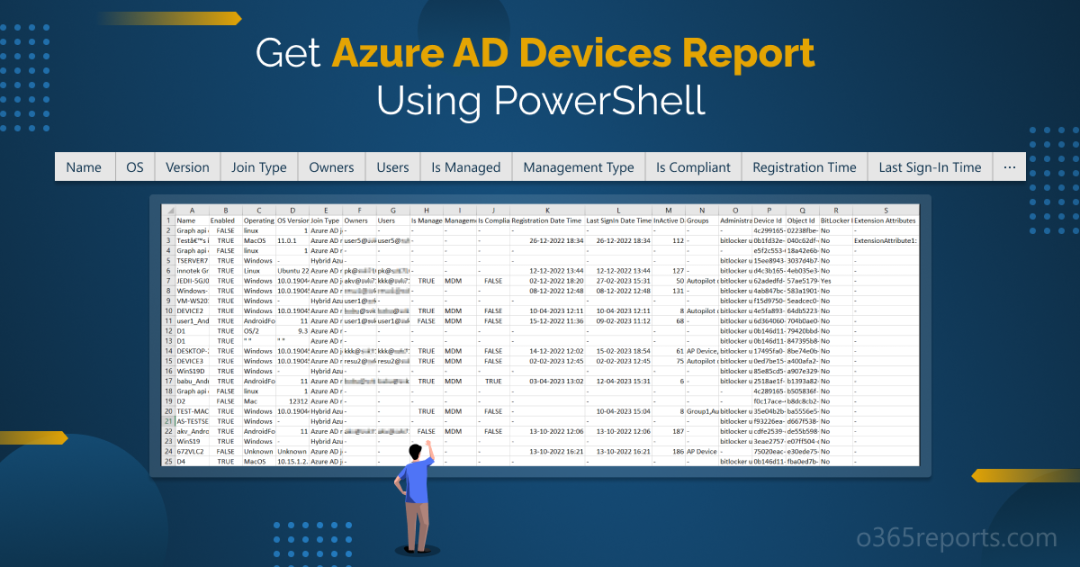
List All Entra ID Devices in Microsoft 365 – Sample Output
The exported ‘Entra ID Devices’ report looks like the screenshot below.

The exported report contains the following attributes of devices:
- Name – Device name is displayed here.
- Enabled – States whether the devices are enabled or not with true or false value.
- Operating system – The name of the Operating system is shown.
- Version – The Operating system version is listed here.
- Model – Specifies the type of the device.
- Serial Number – The unique serial number assigned by the device manufacturer.
- Join Type – States the JoinType of devices such as Entra registered, Entra joined, and Entra hybrid joined.
- Owners – Device owner names are mentioned here.
- Users – Users of the device are mentioned in this place.
- Is Managed – Concludes whether the device is managed or not with true or false value.
- Management Type – If the device is managed, the management type of the device is recorded here.
- Enrollment Type – Specifies the method used to enroll the device into management (e.g., automatic, manual).
- Profile Type – Represents the device scenario: Registered, Shared, SecureVM, Printer, IoT, etc.
- Device Ownership – Indicates who owns the device: Company, Personal, or Unknown.
- Is Compliant – Returns true value if the device is compliant otherwise it returns false value.
- Is Rooted – Identifies whether the device is rooted or jailbroken.
- Registration Date Time – Shows the registration date and time of the devices.
- Last Sign-in Date Time – Displays the Last Sign-in date and time of the devices.
- Inactive Days – The number of days since the device last signed in.
- Groups – Groups that a device belongs to are listed here.
- Administrative Units – Indicates the administrative units of the devices.
- Device Id – Specifies the ID of device here.
- Object Id – A unique identifier related to the device in Azure AD is shown here.
- BitLocker – Encrypted Indicates whether BitLocker drive encryption is enabled on the device.
- Extension Attributes – Azure AD extension attributes are an additional way of storing extra pieces of info on user objects and other directory objects.
Microsoft Entra ID Devices Report – Script Execution Methods
- Download the script.
- Start the Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1: Execute the script for both MFA and non-MFA accounts.
|
1 |
./GetAzureADDevicesReport.ps1 |
Executing this script will export the details of all registered devices in Azure AD, along with their associated attributes, to a CSV file.
Method 2: Also, you can execute the script with certificate-based authentication (App-only access). This method is also scheduler friendly.
Before you can connect Microsoft Graph PowerShell with certificate authentication, you’ll need to register the app in Entra ID. Based on your flexibility, you can obtain one from a certificate authority (CA) or Create a self-signed certificate.
|
1 |
./GetAzureADDevicesReport.ps1 -TenantId< TenantId> -ApplicationId <AppId> -CertificateThumbprint<CertThumbprint> |
Note: If you are using this method, the script generates output only if directory permissions like Directory.Read.All is granted in your app registration.
More Use-cases of ‘Entra ID Devices Report’ Script
The script supports some built-in filtering parameters according to your needs, and its use cases are listed below.
- Find the managed devices in Azure AD
- Track devices with BitLocker key
- Identify inactive devices in Entra
- Get devices used by specific users
- List devices owned by specific users
- Find enabled devices in Azure AD
- Filter Entra ID devices by registration type
- Refine devices by their profile type
- Export non-compliant device report
- Get rooted device in Microsoft Entra
- Reterive devices in the groups
- View devices in Entra ID by ownership type
- Spot disabled devices in Azure AD
1. Find the Managed Devices in Entra ID
Managed devices are the devices that are completely controlled and managed by the organization, giving users no control over them. And it’s always crucial to manage and control access to the organization’s managed devices. This is where the -ManagementStatus parameter comes in handy, allowing administrators to view and export a list of all managed Azure AD devices.
This information can provide insights into the volume of managed devices, which can help identify any unmanaged devices that may need attention. By using the -ManagementStatus parameter, organizations can ensure that all their devices are properly managed and secure, helping to protect against potential security threats and unauthorized access.
|
1 |
./GetAzureADDevicesReport.ps1 -ManagementStatus Managed |
Similarly, to get all unmanaged Entra ID devices in your Microsoft 365, you can use the following cmdlet.
|
1 |
./GetAzureADDevicesReport.ps1 -ManagementStatus Unmanaged |
2. Track the Devices with Bit Locker Key in Microsoft 365
BitLocker is a Microsoft encryption product that is used to conceal and protect sensitive user data on a computer. In which BitLocker keys were significantly required to recover the encrypted drives of your work environment. With the -DeviceWithBitLockerKey parameter, you can track the devices with BitLocker keys in your tenant. This helps to transparently monitor and secure BitLocker-encrypted devices within your organization. This will eventually retrieve only the devices with bit locker key and export them into a CSV file.
|
1 |
./GetAzureADDevicesReport.ps1 -DevicesWithBitLockerKey |
Important: You can retrieve bit locker key enabled devices only with interactive authentication (password authentication) and can’t be retrieved from a certificate-based authentication method. This is because BitLocker can only be accessed through delegated permissions and not application permissions. If you attempt to fetch BitLocker-enabled devices using certificate-based authentication, you will encounter an error message stating that
“You don’t get device with BitLocker key info while using certificate-based authentication. If you want to get BitLocker key enabled devices, you should connect Graph with interactive sign-in method”.
3. Identify the Inactive Devices in Azure AD
Unfortunately, the biggest challenge for Azure AD admins is to locate stale or inactive devices, to reduce the potential security risks caused by them. If an inactive device falls into the wrong hands, it could be used to gain unauthorized access to your organization’s resources. Therefore, it’s essential to monitor inactive devices in Azure AD to identify devices that may pose a security risk and take appropriate action, such as removing them from your organization’s Azure AD or resetting their passwords.
No worries now! To locate all the inactive devices in your Azure AD environment, use the –InactiveDays parameter, and mention the minimum number of days. Therefore, it exports the device details that have been inactive for the specified period.
|
1 |
./GetAzureADDevicesReport.ps1 -InactiveDays <NumberOfDays> |
4. Identify Devices Used by Specific Users in Microsoft 365
Monitoring devices used by a specific users help ensure they’re accessing resources from secure and compliant endpoints. For example, if a user’s account is suspected of suspicious activity, you can easily filter devices they’ve signed in using -Users parameter to check whether those devices comply with organizational policies.
|
1 |
./GetAzureADDevicesReport.ps1 -Users "gennady_golovkin@contoso.com" |
Running this action helps to track devices used by the ‘Gennady Golovkin’ in Microsoft 365.
5. Get Report of Devices Owned by Specific Users in Entra
Checking devices owned by specific users provides visibility into their access footprint and ensures accountability. This is especially useful if your organization supports Bring Your Own Device (BYOD), it’s important to regularly check what personal devices are registered by specific users. This helps validate that these devices meet the organization’s security posture.
To filter devices by its owners, execute the script with the –Owners param along with owners’ UPN like below.
|
1 |
./GetAzureADDevicesReport.ps1 -Owners "floyd_mayweather@contoso.com","nick_fury@contoso.com" |
The exported report contains all devices owned by the ‘floyd mayweather’ and ‘nick fury’.
6. Find Enabled Devices in Entra ID
Enabled devices in Azure AD refer to devices that have been registered and authorized by organizations, which allows them to authenticate and access resources such as applications and data. Moreover, it permits access to the resources protected with conditional-based access.
It’s important to monitor enabled devices in Azure AD to identify the devices and users with most inclusive permissions. By monitoring enabled devices, you can identify potential security risks, identify the misuse of resources and detect the potential indicators of insider threats.
Easily spot all your enabled devices in the Azure AD environment by executing the script below after mentioning the required parameter –DeviceStatus in the script.
|
1 |
./GetAzureADDevicesReport.ps1 -DeviceStatus Enabled |
7. Filter Entra ID Devices by Registration Type
Focusing on device join types helps assess the trust level and management state of devices accessing organizational resources. For instance, if you’re investigating a security breach, knowing whether the device was Microsoft Entra registered, Entra joined, or Entra hybrid joined can reveal whether it was a personal, unmanaged device or a fully trusted corporate device.
To filter devices got identity from specific registration type, you can use the –JoinType parameter like below.
|
1 |
./GetAzureADDevicesReport.ps1 –JoinType 'Entra registered' |
Similarly, to filter more than one registration type like ‘Entra registered’ or ‘Entra joined’, adjust the join type filter accordingly.
|
1 |
./GetAzureADDevicesReport.ps1 –JoinType 'Entra registered','Entra joined' |
This execution will output the report that contains devices registered using ‘Entra registration’ and ‘Entra join’ methods.
8. Refine Entra Devices Based on Profile Type
Focusing on device profile types helps you manage devices based on their intended roles. For instance, during an access review, you might want to exclude infrastructure devices like printers. By filtering devices by their profile types, you can narrow down results that focus only on user-owned devices and ensure compliance checks are applied where they matter most.
To filter devices by their profile type, you can use the –ProfileType parameter like below.
|
1 |
./GetAzureADDevicesReport.ps1 -ProfileType RegisteredDevice |
By narrowing down to relevant device profile types, you can reduce noise and make your access review more effective.
9. Identify Non-Compliant Devices in Microsoft 365
Device compliance status reflects whether a device meets the security and configuration policies defined by your organization. Compliant devices are those that follow all required Intune device compliance policies for accessing Microsoft 365 resources. On the other hand, non-compliant devices are those that violate Intune device compliance rules and posing a risk to your environment.
Therefore, monitoring non-compliant devices allows you to quickly identify at-risk endpoints and helps reduce the chance of data exposure. to identify compliant or non-compliant devices, you can use the –ComplianceStatus parameter with values “Compliant” or “NonCompliant” as shown below.
|
1 |
./GetAzureADDevicesReport.ps1 –ComplianceStatus NonCompliant |
Running this format will return a report that includes all devices flagged as non-compliant within your Microsoft 365 environment.
10. Export Rooted or Jailbroken Devices Report in Entra ID
Rooted (or jailbroken) devices are those that have been modified to bypass manufacturer security controls, making them highly vulnerable to threats. In contrast, NonRooted devices retain the native security configurations of the OS and are generally safer to allow access to Microsoft 365 services.
Monitoring device root status is vital for enforcing zero-trust principles and improving your Microsoft Secure Score for devices. For example, you might want to block access from rooted devices entirely or alert security teams when such devices appear in your directory.
To filter devices based on their rooted status, use the –RootedStatus parameter with values “Rooted” or “NonRooted” accordingly.
|
1 |
./GetAzureADDevicesReport.ps1 –RootedStatus Rooted |
This format will export the report of all rooted devices in Microsoft 365.
11. Generate Report on Entra ID Devices in Groups
Organizing devices into Intune groups from Microsoft Entra ID is a common practice for targeting specific configurations. These groups can represent departments, device types, geographic location, hardware characteristics, and more. By filtering devices in specific groups, you can quickly assess whether they are managed and actively used, especially in high-privilege groups.
To identify the devices assigned to a particular group, you can use the –Groups parameter with the desired group’s displayname, as shown below.
|
1 |
./GetAzureADDevicesReport.ps1 -Groups "servers" |
The exported report contains all devices from the ‘servers’ security group.
12. Classify Entra ID Devices by Ownership Type
Device ownership helps distinguish between company-owned, personal (BYOD), and other devices. This classification is critical for applying the right security controls based on who owns the device.
To get a report on devices by their ownership type, use the –DeviceOwnership parameter with values “Company”, “Personal”, or “Unknown” as shown below.
|
1 |
./GetAzureADDevicesReport.ps1 –DeviceOwnership Personal |
This script execution will return all devices with personal ownership in your Microsoft Entra.
13. Get to Know the Disabled Devices of Entra ID
Devices are disabled as an immediate response of threat and cyber security problems instead of deleting them completely. Basically, disabled devices are devices which can’t access Microsoft 365 services at this state but can be enabled later if the reason for disabling is found to be false positive. Also, by monitoring disabled devices, you can identify devices that are no longer needed and remove them from your Azure AD, freeing up resources and reducing licensing costs.
Therefore, to identify all sign-in disabled devices in Microsoft Entra, you can use the same –DeviceStatus param with value “Disabled” like below.
|
1 |
./GetAzureADDevicesReport.ps1 -DeviceStatus Disabled |
Simplify Your Device Management with AdminDroid!
Despite giving reports on Entra ID devices, the Entra and Intune portals eventually failed to provide exclusive reports on devices and their details. Aren’t you tired of finding those Entra ID devices report? Still, surfing the web for a perfect solution?
Don’t worry, AdminDroid is at your rescue! Yes, the AdminDroid’s Microsoft Entra reporting tool provides comprehensive records and statistics on Entra devices.
With Entra device overview reports, you can gain insights into every aspect of devices and simplify Azure AD device management and monitoring. Reports includes,
- Device Reports
- All Devices
- Enabled / Disabled Devices
- Entra Registered / Joined / Hybrid Joined Devices
- Recently Created / Registered Devices
- Stale / Never Logged In Devices
- Autopilot Enrolled Devices
- On-Premises Sync Devices
- Deleted Devices
- Device Management Reports
- Managed / Unmanaged Devices
- Compliant / Non-Compliant Devices
- Company Owned / Personal Devices
- Windows / Linux / Mac / Android / iOS Devices
- Rooted Devices
- Device Membership Reports
- Device with only Local-Admin privilege
- Device Users / Owners / Multiple Owners / Without Owner
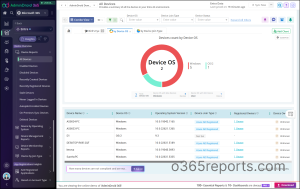
Additionally, AdminDroid provides explicit dashboards and offers 140+ Free reports on users, groups, licenses, and the list goes on. Apart from these, AdminDroid’s M365 management tool gives you a panoramic view of your entire Microsoft 365 ecosystem with over 3000+ ready-to-use reports, 490+ management actions, and 100+ engaging dashboards. This includes SharePoint Online, Microsoft Teams, Exchange Online, Microsoft Entra ID, and OneDrive for Business.
Download AdminDroid now to find everything you desire within no time!
In conclusion, try this script to get your Azure AD devices report in minutes instead of searching for the details for the whole day in the portal. We hope this blog has been helpful and eased your burden in obtaining the details of Azure devices. For any questions, feel free to reach us in the comments section.