Enabling Single sign-on in Microsoft 365 is a positive step, balancing both user security and productivity. Yes, it relieves you of the repetitive chore of entering M365 credentials every time you access any M365 resources and mitigates the risk of credential reuse. However, it’s good enough only up to this point alone!
Nowadays, token theft attacks are becoming increasingly common. Once attackers steal the issued token, they can leverage the access token to enter Microsoft 365 services.
To prevent such cases, Microsoft implemented “Sign-in frequency – every time” session control in Microsoft 365 Conditional Access to prompt users for reauthentication. It’s like the safety net, which confirms users’ identity more often to prevent cyberattacks. Initially confined to specific applications and actions, this feature has now undergone a crucial expansion. Yes! Azure AD Conditional Access can now require reauthentication for any resources and sensitive actions.
Let’s get into the blog to know the importance of reauthentication and how the latest update will prompt reauthentication on sensitive apps and high-risk actions.
Session Controls in Microsoft Entra Conditional Access
Reauthentication in Microsoft 365 is nothing, but the users are asked to provide their credentials again, which then generates a fresh token to regain access to the M365 resources.
One way to require reauthentication in Microsoft 365 is through Conditional Access policies, specifically by implementing the “sign-in frequency” session control. This control determines how often users are required to reauthenticate to continue accessing Microsoft 365 resources.
Within this Azure AD sign-in frequency session control, there are two options available:
- Periodic reauthentication: This prompts reauthentication during specified intervals. For example, you can make users reauthenticate every 12 hours when they connect to the Office 365 services.
- Every time: This prompts users for reauthentication each time they log in to critical resources or perform any sensitive actions.
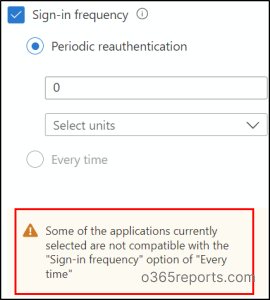
The latter option has recently been updated to facilitate reauthentication across any resources or authentication contexts protected by Conditional Access. Let’s explore when this update proves beneficial.
Benefits of Reauthentication on Sensitive Apps and High-risk Actions in M365
- Activating a Privileged Role in PIM: By configuring the Conditional Access authentication context in PIM, you can prompt users for reauthentication for any actions within PIM. For instance, you can force reauthentication with Conditional Access during the activation of privileged roles in PIM.
- Protected Access to Sensitive Site Contents: You can easily protect sensitive SharePoint Online sites with this reauthentication capability. When users access content within these SharePoint Online sites, even if authorized, they will be prompted to re-authenticate every time. This granular Conditional Access on SharePoint sites helps mitigate the risk of unauthorized access even if credentials are compromised.
- Secure Access from Anywhere: You can ensure secure access to sensitive apps, even from remote networks, by configuring reauthentication for sensitive apps. This measure guarantees that only authorized users gain entry, bolstering overall Microsoft 365 security.
- Mitigating Token Theft Risks: You can mitigate the token theft issue in Microsoft 365 by requiring reauthentication with MFA prompts when accessing critical resources. This measure ensures that legitimate users receive fresh tokens every time, rendering stolen tokens ineffective for attackers.
This feature is also beneficial for scenarios such as requiring reauthentication during Intune enrollment, VPN access, changing personal information in apps, and much more!
Now, let’s verify how this update helps in prompting reauthentication to active privileged roles.
Prompt Reauthentication to Activate Privileged Role in Privileged Identity Management
Consider prompting users for reauthentication with phishing-resistant MFA when attempting to activate PIM roles. To achieve this, you’ll need to establish a Conditional Access authentication context within Privileged Identity Management (PIM) by following the steps below.
1. First, you need to create a Conditional Access authentication context.
2. Then, you need to create a Conditional Access policy that prompts reauthentication with phishing-resistant MFA. To do it, follow the steps.
- Sign in to the Microsoft Entra Admin Center.
- Navigate to the Protection drop-down menu and choose Conditional Access.
- Click on + Create new policy to initiate the creation of a new policy and give it an appropriate name.
- From the Target resources section, set the policy to Authentication Context.
- Then, select the respective authentication context.
- Under the Grant section, select Phishing-resistant MFA from the Require authentication strength dropdown menu.
- In the Session control section, set the Sign-in frequency to Every time.
- Once configured, activate the policy by toggling the switch to On. Then save the policy.
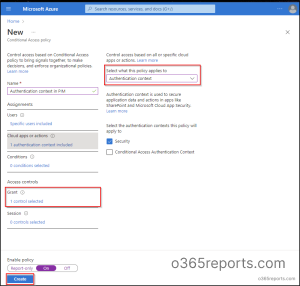
3. Once done, you need to tag the authentication context in the PIM role setting.
That’s it. Once these steps are implemented, users will be prompted for credentials and phishing-resistant MFA every time they attempt to activate PIM roles. Don’t just stop configuring the Conditional Access policy. It is crucial to monitor Conditional Access policies regularly to check their enforcement.
I hope this blog has provided insight into the recent update prompt reauthentication on sensitive apps and high-risk actions. We encourage you to share your thoughts and reach out in the comment section for any further assistance or queries.