Technology is growing and so are cyber-attacks! Cybercriminals are always on the lookout for opportunities to breach security and compromise data in Microsoft 365. To defend against such security threats, it’s crucial to have strong security practices in place like implementing the Continuous Access Evaluation (CAE).
To make things even better, a new feature called “Enforce Location Policies with Continuous Access Evaluation” has been introduced.
This feature adds an extra layer of protection by blocking access to a resource immediately if the user is not within the allowed location range.
Let’s delve into the topic and explore how to enable strictly enforce location policies in CAE!
What is Continuous Access Evaluation in Microsoft Entra?
Continuous Access Evaluation (CAE) is a way to control access to certain resources or information in a more responsive and immediate manner. Instead of waiting for access permissions to expire after a set time, CAE keeps a constant watch on important events and rules. If any critical event occurs or if a policy configuration is violated, access tokens can be quickly taken away, as an act of token protection in Azure AD conditional access. CAE is enabled by default in every conditional access policy.
What’s New About Continuous Access Evaluation in Azure AD?
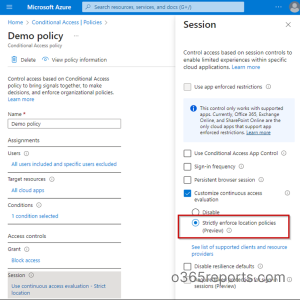
To customize continuous access evaluation in Azure AD, you can use the conditional access session controls section. Earlier, there were only options to disable Continuous Access Evaluation. Now Microsoft has added a new feature to the CAE configuration – that is the ‘Strictly enforce location policies’ option. This feature is currently in preview.
Strictly Enforce Location Policies with Continuous Access Evaluation
CAE’s strictly enforced location policies deny user access based on IP-based named locations. With this, CAE–enabled applications like Exchange Online, SharePoint, Teams, and Microsoft Graph now have the ability to quickly and effectively revoke access tokens in response to any network changes detected by the application.
Configure Strictly Enforce Location Policies
To enable strict location enforcement in CAE, follow the steps outlined below.
Step 1: Sign into the Azure portal and open the Conditional Access page.
Step 2: Create one from the CA policy template or open an existing policy in Azure AD.
Step 3: Reach out to the ‘Session controls’ section of the policy.
Step 4: Select the ‘Customize continuous access evaluation’ option on the flyout page.
Step 5: Enable the ‘Strictly enforce location policies (Preview)’ option and then save it (Make sure to check the list of supported clients and resource providers).
Step 6: Control user access based on location by configuring it from the ‘Conditions’ tab of the policy (The location must fall into any one of the categories as explained below).
Control User Access Based on Location in a CA Policy
As CAE supports only IP-based named locations, after configuring named locations by IP ranges, you can use them to strictly enforce location policies with CAE.
You can choose one of these location types and then configure the access policy to either allow or restrict access from specific locations.
- Any Locations: This option includes all locations, such as named locations, trusted locations, and any unspecified locations. Choosing “Any Locations” allows you to grant or block access for users from any location.
- All Trusted Locations: This option covers both named locations (those marked as trusted locations) and MFA-trusted IPs. It ensures access from all trusted locations.
- Selected Locations: This option shows only the named locations that administrators have configured. These named locations can be determined by country range, IP ranges, and MFA-trusted IPs.
Important: Make sure that you have included all IP addresses from which users can access resources in the IP-based named locations policy. To ensure this, you can make use of the CAE workbooks or Sign-in logs to decide the IP addresses that are seen by Azure AD and resources.
Scenario-based Explanation for Location Policy Enforcement
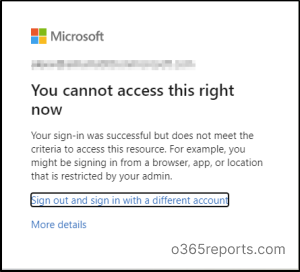
Let’s say your employee, John, usually works from the company’s office, which is within an approved location range. But one day, John’s access token gets stolen by a cyber attacker while he is using a public Wi-Fi network! The thief attempts to use the stolen token to access Microsoft 365 from an unauthorized location.
Now, with the strict location enforcement in Azure AD, the Microsoft 365 applications (like Exchange Online, Teams, and SharePoint Online) are constantly checking for changes in conditions related to user access. When they notice a network change event, such as John trying to access Microsoft 365 from an unexpected location, they immediately alert the Identity Provider (Token Issuer) that something seems off.
The Identity Provider then communicates with the Microsoft 365 applications and tells them to stop respecting John’s stolen token, effectively revoking his access in near real-time.
So, even if the thief managed to steal the token and attempt to use it, they would be blocked instantly because the token has been invalidated due to the detected unauthorized location.
Pro Tips:
- Set up IP-based named locations correctly.
- Utilize CAE workbooks or Sign-in logs to ensure IP coverage.
Some Concerns Regarding the Location Policies Enforcement
- The traditional notion of “named locations” may not be the best fit in today’s remote-first world.
- When malware steals access tokens from remote locations, users do not receive any emails or alerts to be notified about it.
As a remote worker, I find the new feature both a boon and a bane. I would be remotely working from a coffee shop, which leads to issues with violating their policies. Regarding the feature’s impact, it seems to play both the role of a hero and a villain in a play! It provides flexibility but may also create complications depending on the situation and location.
In terms of account security, the “strictly enforce location policies” feature could be valuable for protecting against unauthorized access, but it may also limit the flexibility needed for remote work. Also, how valuable do you think the ‘strictly enforce location policies’ feature would be in protecting your account security?
I hope you have gained a good understanding about the importance of CAE and its new feature from the above information. Thanks for reading. If you have any further queries, feel free to reach us through the comment section.