As a way to ensure that your organization stays on top of security, Microsoft introduced the
Office 365 Audit Log. With audit logging, you can keep track of, record, and retains activities performed in the tenant. Office 365 mailbox auditing is part of the audit logs because mailboxes contain the most sorts of confidential information. Tracking the mailbox audit actions helps to track mailbox access and actions performed by owners, delegates, and admins. Thus, organizations can monitor mailbox activities with detailed audit logs and stay on top of potential security breaches.
List All the Non-audited Mailbox Actions:
Microsoft has enabled mailbox auditing by default, but this is not cent percent true. Only specific mailbox actions are enabled by default. Due to this, it is hard for the admins to differentiate which mailbox actions are audited and which are not audited, for each logon type (Audit Administrator, Audit Owner, Audit Delegate).
Then, how will you ensure that all the mailbox activities are audited or not? Don’t panic!! We’ve got you covered.
To overcome this difficulty, we’ve prepared a PowerShell script that lets you see which mailbox actions aren’t being audited. Thereby, reducing one of the complex tasks into a much more facile one. Make sure nothing goes unnoticed with our PowerShell script!
Download Now: GetMB_NonAuditedActions.ps1
Script Highlights:
- The script uses modern authentication to connect to Exchange Online.
- The script can be executed with MFA enabled account.
- Exports the report result to a CSV file.
- Lists the non-audited mailbox actions for each logon type (Admin, Owner, Delegate).
- Helps to identify audit bypassed mailboxes.
- Automatically installs the EXO module (if not installed already) upon your confirmation.
- The script is scheduler-friendly
- Supports Certificate-based authentication (CBA) too.
List All the Non-audited Mailbox Actions – Script Execution:
To run this script, you can choose any one of the below methods.
Method 1: You can use the below method to run the script with both MFA and non-MFA accounts.
|
1 |
.\GetMB_NonAuditedActions.ps1 |
Method 2: To run a script non-interactively, you can use the below format.
|
1 |
.\GetMB_NonAuditedActions.ps1 -UserName admin@contoso.com -Password XXX |
You can also use this format to automate the PowerShell script in Windows Task Scheduler.
Method 3:
To run the script with certificate-based authentication, you can use the below method. You can also utilize this method when you want to run the script unattended.
|
1 |
.\GetMB_NonAuditedActions.ps1 -Organization <Domain> -ClientID <AppId> -CertificateThumbPrint <CertThumbPrint> |
Note:
You must register the app in Azure AD and obtain a certificate. You can either use a CA certificate or create a self-signed certificate for this method.
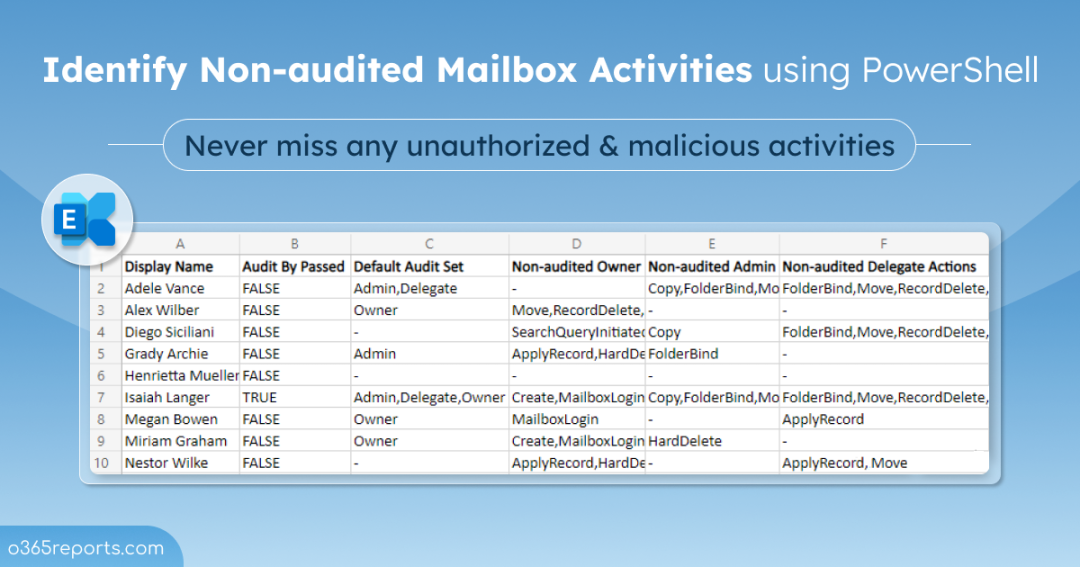
Export Non-audited Mailbox Actions Report – Sample Output:
Once you run this script, it’ll export a CSV file that contains the non-audited mailbox actions on each logon type. The output file will be stored in the current working directory.
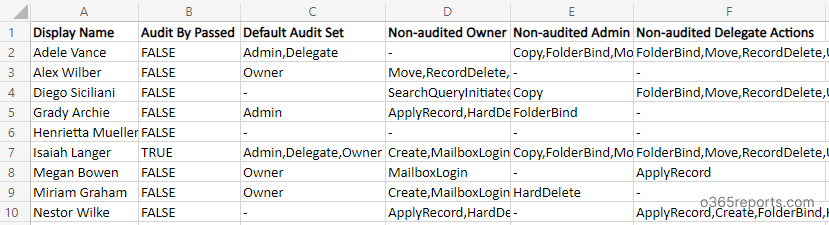
Detailed Look at CSV Attributes:
- Display Name – Displays the mailbox name.
- Audit Bypass Enabled – This shows whether the mailbox is set to bypass mailbox audit logging. If an account is configured to bypass mailbox audit logging, then the actions performed by the accounts for any mailbox will not be logged.
- Logon Type with Default Audit Set – Mailbox auditing on by default included a DefaultAuditSet property. This indicates whether default mailbox actions are being audited on all mailboxes or not.
- The DefaultAuditSet property value is initially set to Admin, Delegate, or Owner when mailbox auditing is enabled by default. If the value is blank, it shows that the admin had changed mailbox audit actions for all the three logon types.
- Owner, Admin, Delegate.
-
- Owner Audit – Lists the non-audited mailbox owner actions on mailboxes.
- Delegate Audit – This displays the non-audited delegate actions.
- Admin Audit – The non-audited admin actions are displayed here.
Why Enable Mailbox auditing in Office 365?
Okay! After getting to know about the non-audited actions, what would you do?
The best practice is to enable the mailbox audit actions that were previously turned off or not even enabled from the start based on your auditing requirements. Because, mailboxes contain sensitive information and information with high business impacts. So, it’s imperative to audit the mailboxes and stay informed about the actions performed in the mailboxes.
You can use the pre-built PowerShell script to enable mailbox auditing based on your requirements.
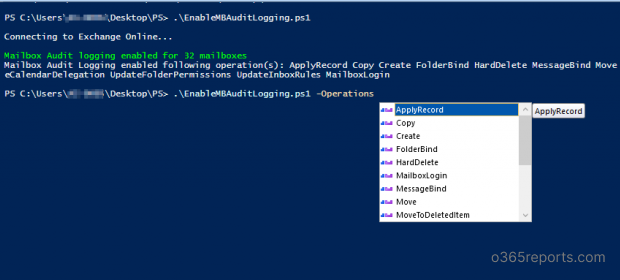
Script Highlights:
- You can enable mailbox audit logging for all mailboxes using a single cmdlet.
- This script allows you to enable mailbox auditing for all mailbox actions or sets of actions.
- This script supports MFA-enabled accounts too.
- This script automatically installs Exchange Online PowerShell Module upon your confirmation.
Wrapping Up:
With these scripts, you can effectively manage Exchange Online auditing and monitor activities performed by all the mailboxes. But, audit log search is challenging to find suspicious activities or non-owner accesses, as it contains 1000s of audit records for a day. Also, native audit log has tons of limitation like 90 days retention period, no build-in reports, poor filtering capability, etc. To overcome this difficulty, you can use Exchange Online auditing tool. The tool provides an easy-to-understand web interface that displays statistical information through charts, graphs, and a list view of canned and customized reports.
With this blog, I hope I helped admins how to identify the non-audited mailbox actions in your mailbox. If you require any more assistance, drop your queries in the comments. We would love to solve it for you!