Auditing mailbox activities play a vital role in security and compliance. Mailbox auditing allows you to track user’s actions on their own mailbox and others’ mailboxes. So, you can track who logs on to the mailbox and what operations are performed.
Things to Know Before Enabling Mailbox Audit log:
You must know a checklist for effective mailbox auditing before enabling it.
- Everyone believes that Mailbox auditing is enabled in Office 365 by default. But that is not 100% true. Only specific actions are audited by default.
- Mailbox audit log includes actions performed by administrators, delegates, and owners.
- Owner Audit – Activities done by the mailbox owner
- Delegate Audit – Actions performed by the user with full access, send as or send on behalf permission on mailbox and admin with full access permission to a mailbox.
- Admin Audit – When Microsoft eDiscovery tools search the mailbox.
- Specific audit actions do not apply to delegate or admin roles.
- By default, mailbox audit log entries are retained for 180 days. You can change this period using the ‘AuditLogAgeLimit’ parameter.
Enable Mailbox Audit Logging in Office 365:
You can’t use the Exchange Admin Center to enable or disable mailbox audit logging. You have to use the PowerShell cmdlets.
In this blog, we will show you how to easily enable mailbox audit logging for Office 365 mailbox. We will show multiple methods, and you can choose the one that’s easier for you.
1. (Recommeded) Method 1: Quickly enable mailbox auditing for Office 365 users (PowerShell script)
2.Method 2: Enable mailbox audit logging in Office 365 (Mailbox based)
Enable mailbox audit logging for a specific mailbox
Enable mailbox audit logging for all mailboxes
3.Method 3: Enable mailbox auditing in Office 365 by default (Tenant wide)
Verify whether the mailbox audit logging is enabled by default
How to opt-out of default mailbox auditing
Bypass a user account from mailbox audit logging
4.More cmdlets to configure mailbox audit logging
5.What actions are logged in the mailbox audit log
Method 1: Quickly Enable Mailbox Auditing for Office 365 Users (PowerShell Script)
I have written a script to take care of every nuance in enabling Office 365 mailbox auditing. You can just run a script to enable all applicable actions on all mailboxes in your environment. If required, you shall enable the auditing only for specific mailbox actions.
Download Script: EnableMBAuditLogging.ps1
Script Highlights:
- You can enable mailbox audit logging for all mailboxes using single cmdlet
- This script allows you to enable mailbox auditing for all mailbox actions or set of actions
- The script can be executed with MFA enabled account also.
- This script automatically installs Exchange Online PowerShell Module upon your confirmation
How to execute “Enable Mailbox Auditing in Office 365 PowerShell Script”
This PowerShell script supports multiple parameters/switches for more granular configuration. We have listed some of the use cases below.
Note: Few actions are specific to the subscription type. For ex,
- MessageBind available for E3 users,
- MailItemsAccessed, SearchQueryInitiated, Send available for E5 or E5 Compliance add-on subscription users.
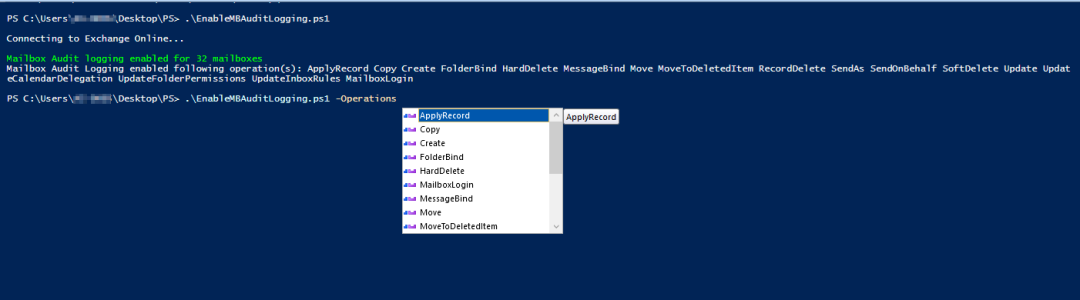
1.Enable Mailbox Audit Logging for all Office 365 Mailboxes:
To turn on mailbox audit logging for all mailboxes with all supported mailbox actions, execute the script as follows:
|
1 |
./EnableMailboxAuditLogging.ps1 |
Now, all mailbox actions are audited for all logon types.
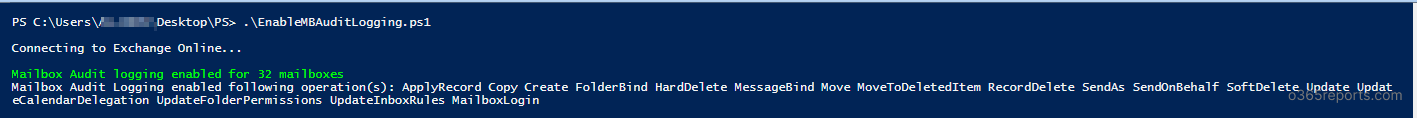
2.Turn on Mailbox Audit Logging for Specific Mailbox Actions:
If you don’t want to enable mailbox audit logging for mailbox actions, you can enable mailbox audit logging for set of mailbox actions. To specify list of mailbox actions, you can use –Operations param.
|
1 |
./EnableMailboxAuditLogging.ps1 -Operations SendAs,ApplyRecord,Copy |
Above script enables mailbox auditing for SendAs,ApplyRecord and Copy actions. You can choose whatever actions that you need to audit.
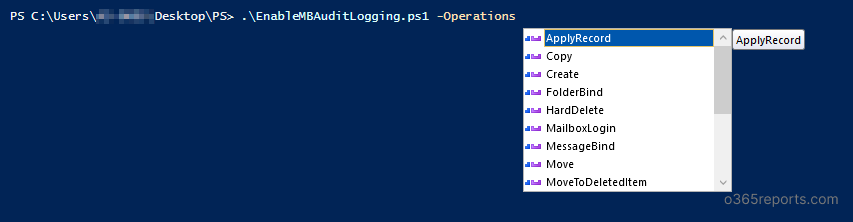
Note: SendAs action available for Admin and Delegate audit and Copy action available for Admin audit only. So, the above cmdlet enables following actions.
Admin audit – SendAs,ApplyRecord,Copy
Delegate audit – SendAs,ApplyRecord
Owner audit – ApplyRecord.
3. Enable Audit for Mailbox Logins:
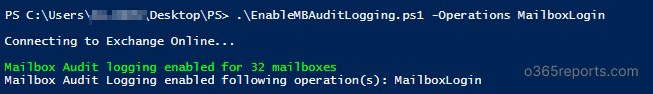
Logons are the one common activity in most attack patterns. Since mailbox logins are not audited by default, you need to configure audit logging to capture mailbox login events. To enable auditing for mailbox logins, run the script as shown below.
|
1 |
./EnableMailboxAuditLogging.ps1 -Operations MailboxLogin |
4.PowerShell Script to Enable Mailbox Auditing in Office 365
You can pass the credential as parameter to connect Exchange Online. So, you can use this PowerShell script in Task scheduler.
|
1 |
./EnableMailboxAuditLogging.ps1 -UserName Admin@contoso.com -Password XXX |
Method 2: Enable Mailbox Auditing in Office 365 (Mailbox based)
When you enable mailbox audit logging for a mailbox, actions performed by administrators, delegates, and owners are logged by default. Set-Mailbox cmdlet is used to enable or disable audit logging for mailbox.
Note: To enable mailbox audit logging, you need to connect Exchange Online PowerShell. If your account is MFA enabled, you can connect Exchange Online PowerShell through EXO module.
Enable Mailbox Audit Logging for Specific Mailbox:
To enable mailbox audit logging, run the Set-Mailbox cmdlet with AuditEnabled value set to $True.
|
1 |
Set-Mailbox –Identity Kathy@Contoso.com -AuditEnabled $True |
Above example enables mailbox audit log for Kathy’s mailbox.
|
1 |
Set-Mailbox –Identity Kathy@Contoso.com -AuditEnabled $False |
This code disables mailbox audit log for Kathy’s mailbox.
Enable Mailbox Audit Logging for All Users:
To enable mailbox audit logging for all mailboxes, run the below code:
|
1 2 |
Get-Mailbox -Resultsize Unlimited | Select PrimarySmtpAddress | Foreach{ Set-Mailbox -Identity $_.PrimarySMTPAddress -AuditEnabled $true } |
This will enable mailbox auditing for each mailbox available in Office 365 environment.
Method 3: Enable Mailbox Audit Logging for Office 365 by Default (Tenant-wide)
Instead of mailbox specific settings, Microsoft launched tenant-wide audit Logging configuration. This feature enables mailbox auditing by default. i.e., Exchange automatically audits set of actions performed by admin, delegate, and owner for all user mailboxes, Office 365 group mailboxes, and shared mailboxes.
Note:
- When Microsoft releases a new action, the action (precisely, actions that help you to protect your organization) is automatically added to the actions that are audited by default.
- If you had customized the mailbox actions to audit before ‘mailbox auditing ON by default was enabled’, the personalized settings are preserved, and default mailbox actions are not overwritten.
Verify Whether the Mailbox Audit Logging is Enabled by Default
To check the configuration, run the Get-OrganizationConfig cmdlet
|
1 |
Get-OrganizationConfig | Select AuditDisabled |
By default, the AuditDisabled value is $False. I.e., audits are tracked. Even if the AuditEnabled (retrieved from Get-Mailbox) setting for the mailbox is $false, the default set of actions are audited.
How to Opt-out of Default Mailbox Auditing?
To stop capturing mailbox audit log for tenant-wide, run the Set-OrganizationConfig cmdlet with AuditDisabled setting is true.
|
1 |
Set-OrganizationConfig -AuditDisabled $True |
The above cmdlet, disables default mailbox audit logging for all mailboxes.
Bypass a User Account from Mailbox Audit Logging:
When your organization turned on the ‘enable mailbox audit logging by default’, the mailbox audits are logged even when the mailbox’s AuditEnabled setting was false. Still, you can disable mailbox audit logging for specific mailboxes.
You can configure a mailbox to bypass mailbox audit logging, so actions taken by that account aren’t logged. By bypassing authorized accounts/trusted accounts that need frequent access to mailboxes, you can reduce the flood of audit entries.
Use the Set-MailboxAuditBypassAssociation cmdlet to configure the mailbox audit logging bypass.
Enable ‘mailbox audit logging bypass’ for an account:
To bypass a user account from mailbox audit logging, run the below cmdlet:
|
1 |
Set-MailboxAuditBypassAssociation –Identity kathy -AuditBypassEnabled $true |
This example bypasses the Kathy account from the mailbox audit logging
Disable ‘mailbox audit logging bypass’ for an account:
To disable ‘mailbox audit bypass’, run Set-MailboxAuditBypassAssociation cmdlet with AuditBypassEnabled setting false.
|
1 |
Set-MailboxAuditBypassAssociation –Identity Kathy -AuditBypassEnabled $false |
This example removes the bypass association for the Kathy account.
Checking mailbox associations:
To check mailbox audit bypass associations, run the below cmdlet
|
1 |
Get-MailboxAuditBypassAssociation –ResultSize Unlimited |
Above cmdlet will retrieve all user accounts configured for mailbox audit logging bypass.
Additional Cmdlets to Configure Mailbox Audit Logging:
1.Configure mailbox audit logging settings for specific logon type (owner, admin or delegate)
|
1 |
Set-Mailbox –Identity Kathy –AuditDelegate SendAs,SendOnBehalf –AuditEnabled $true |
This example lists SendAs and SendOnBehalf actions performed by delegate users will be logged for Kathy’s mailbox.
2.Configure mailbox audit logging for specific actions (Copy, FolderBind, HardDelete, etc.
|
1 |
Set-Mailbox –Identity Kathy –AuditDelegate HardDelete,SoftDelete –AuditAdmin HardDelete,SoftDelete -AuditOwner HardDelete,SoftDelete –AuditEnabled $true |
Above cmdlet audits HardeDelete and SoftDelete actions performed by all logon type.
3.Configure mailbox audit logging to append actions, without overwriting the existing list
If you run above two cmdlets, it will overwrite the existing lists. If you want to append actions to an existing list, run the below code.
Consider, AuditDelegate has already configured to audit HardDelete and SoftDelete for Kathy.
|
1 |
Set-Mailbox –Identity Kathy –AuditDelegate @{Add=SendAs,SendOnBehalf} |
This example appends SendAs and SendOnBehalf actions to existing HardDelete and SoftDelete actions.
4. Increase retention period for audit logs
By default, mailbox audit logs are kept for 90 days. If you want to keep the audit log for more than 90 days, you need to increase ‘AuditLogAgeLimit’.
|
1 |
Set-Mailbox –Identity Kathy –AuditLogAgeLimit 365 |
This example increases the age limit for mailbox audit log entries in Kathy’s mailbox to 365 days.
5.How do you know this worked?
To verify that you have successfully configured the mailbox audit logging, use the Get-Mailbox cmdlet
|
1 |
Get-Mailbox –Identity Kathy | Format-List Audit* |
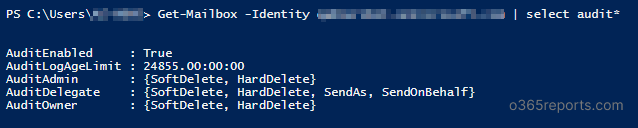
The output shows AuditEnabled, AuditLogAgeLimit, actions configured for administrator, delegate, and owner.
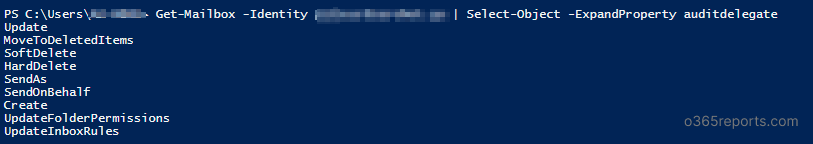
6.Display the mailbox actions that are being logged on for each logon type
When the mailbox has multiple actions for each logon type, then all the actions are displayed using the last cmdlet. It will be shown as the screenshot below.
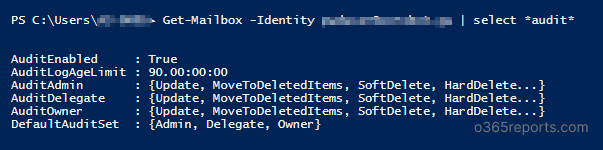
To display all actions that logged for specific logon type, use the ExpandProperty parameter.
Here, the example lists actions that audited for AuditDelegate logon type.
|
1 |
Get-Mailbox -Identity Kathy | Select-Object -ExpandProperty AuditDelegate |
What Actions are Logged in the Mailbox Audit Log?
After enabling the mailbox audit log, you can search audit logs using Search-MailboxAuditLog cmdlet.
The audit log gives the following information
- Who accessed the mailbox and when?
- What operations are performed?
- The affected message and its folder location
- Operation status. I.e. whether the action was succeeded or failed
The following image describes the mailbox actions that are available in mailbox audit logging for user mailboxes and shared mailboxes.
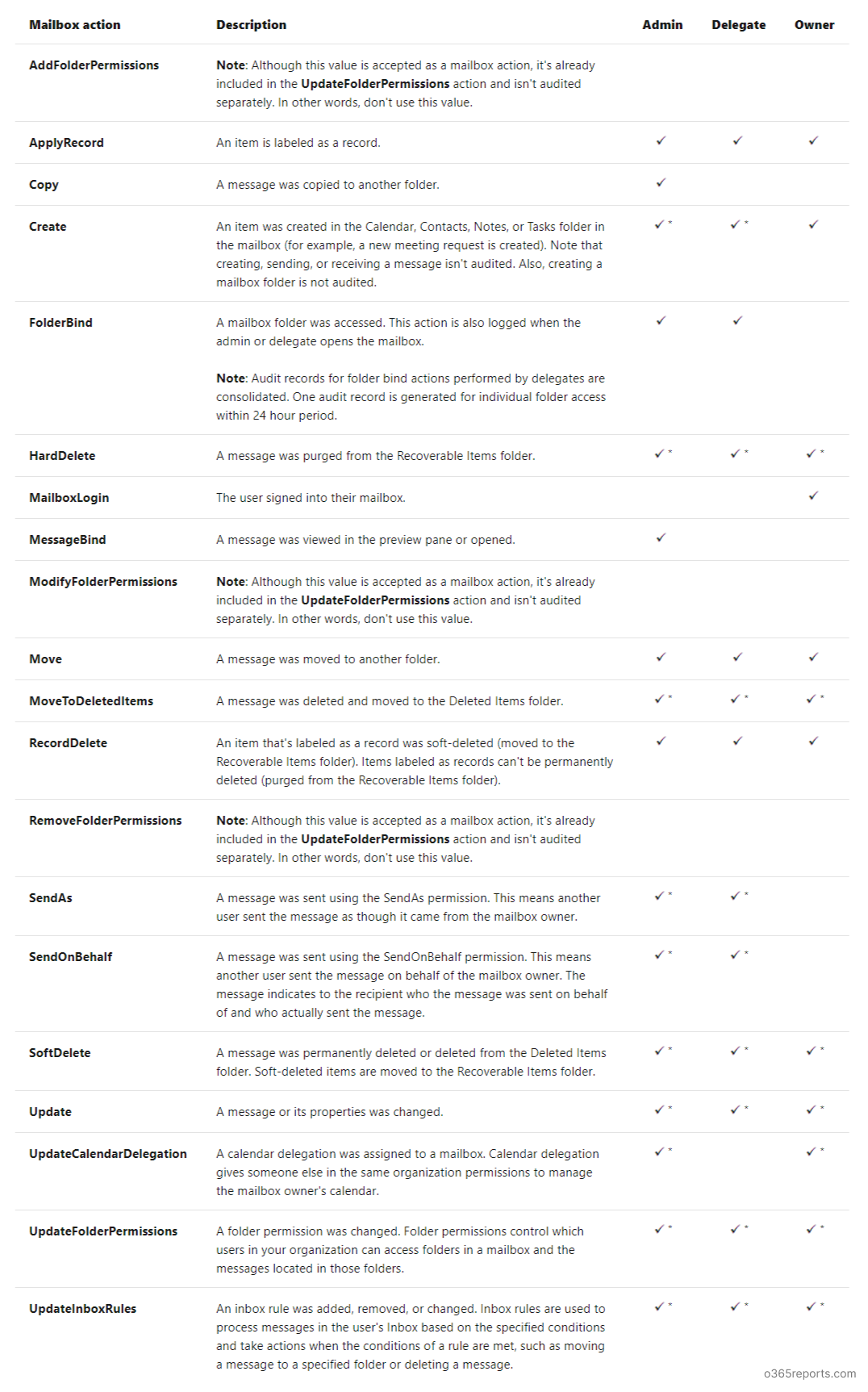
A check mark (tick) indicates the mailbox actions that can be logged for the logon type (some actions are available only for specific logon type)
An asterisk (*) after the check mark indicates the mailbox actions that are logged by default when default audit logging is enabled.
AdminDroid – Seamless insights and details on Exchange mailbox audit logging
We have explored how to enable mailbox auditing using PowerShell and respective use cases. Do you believe that you can get mailbox auditing status without using a PowerShell script? Of course, yes! Let’s see it in detail.
How AdminDroid improve the experience of reporting mailbox audit log?
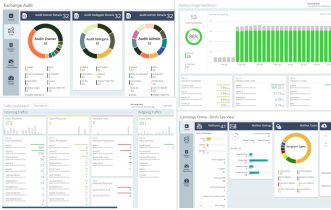
AdminDroid Exchange Online reporting tool provides explicit dashboard and statistical reports for mailbox audit configurations. Let’s see how the stats help you to stay updated on mailbox configuration changes.
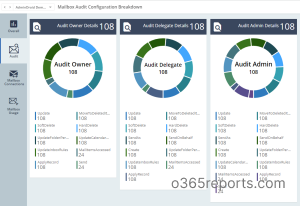
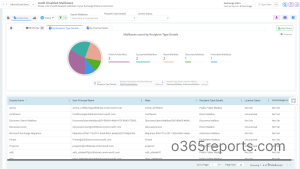
Intuitive Mailbox Audit Dashboard
The ‘Mailbox Audit Configuration Breakdown’ shows clear insights into the auditable actions of the mailbox owner, mailbox delegate, and admin.
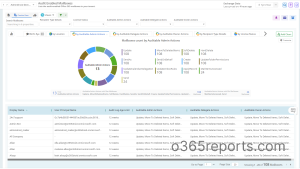
All-inclusive Mailbox Audit Reports
Get reports on mailbox audit configurations, including audit–enabled mailboxes, audit–disabled mailboxes, admin auditable actions, owner auditable actions, and delegate auditable actions with in-depth details. Thus, admins can easily find out the missing auditable actions and enable them for any mailbox.
Moreover, AdminDroid is a comprehensive tool for auditing mailbox activities in Microsoft 365, including non-owner access, guest access, bulk message operations, inbox rule configurations, mailbox permission changes, ATP, role scope changes, and more. The tool provides detailed reports with insightful charts, allowing you to monitor and analyze mailbox data effortlessly. You can set up alerts for crucial mailbox activities in real-time or schedule reports to monitor data at a preferred time. Start exploring AdminDroid Exchange Online auditing tool today and boost your Microsoft 365 mailbox management effortlessly!
Don’t limit yourself to AdminDroid’s Exchange Online management. It goes beyond that and offers insightful reports and exciting features for an entire suite of Microsoft 365 services. Check out AdminDroid now and indulge in its numerous features!
In this blog, we have seen how to enable mailbox auditing through PowerShell. What’s your preferred approach when it comes to mailbox auditing? Let us know your thoughts in the comments section.