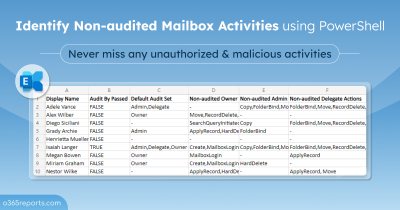
Since mailboxes have sensitive data, granting access permission to multiple users increases the risk of a security breach. You can use the audit log to detect and prevent such security vulnerabilities. Using the audit log, you can track who has accessed the mailbox and what actions are performed by them.
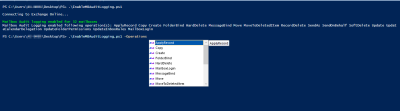
In some organizations/tenants, mailbox auditing is not enabled by default. So, you need to enable mailbox auditing. Else you will end up with empty audit records.
Note: The default audited actions are sufficient for most organizations. But, if you determine they aren’t, you need to configure it manually. You can use PowerShell script to enable mailbox auditing for all mailbox actions.
How to Detect Who Accessed Another User’s Mailbox?
The Office 365 non-owner mailbox access report lists the mailboxes that have been accessed by someone who is not an owner of the mailbox. You can get who has permissions on others’ mailboxes by using a non-owner mailbox permission report.
You can use the Exchange Admin Center (EAC) to run a non-owner mailbox access report, but you can’t export them, and you need to click each mailbox to view their non-owner access. This is where PowerShell gets into the play. But, getting all audit logs and analyzing them is a difficult task. Don’t worry! Let me help you!
I have created a PowerShell script to export Office 365 Non-owner mailbox report to CSV.
Export Non-Owner Mailbox Access Report Using PowerShell:
The Non-owner access report shows the actions performed by administrators and delegates. The report provides following information.
- List of mailboxes accessed by non-owner,
- Who accessed the mailbox and when,
- Actions performed by the non-owner,
- Result whether the action is succeeded or failed.
Download Script: NonOwnerMBAccessReport.ps1
Script Highlights:
- Allows you to filter out external users’ access.
- The script can be executed with MFA enabled account too.
- Exports the report to CSV
- This script is scheduler friendly. I.e., credentials can be passed as a parameter instead of saving inside the script.
- You can narrow down the audit search for a specific date range.
- The script supports Certificate-based Authentication (CBA)
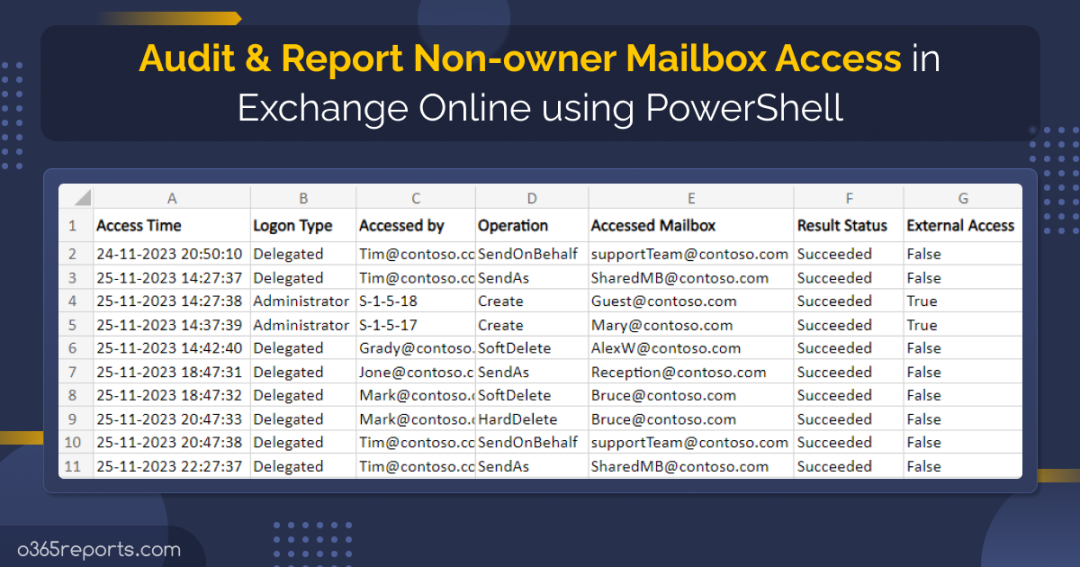
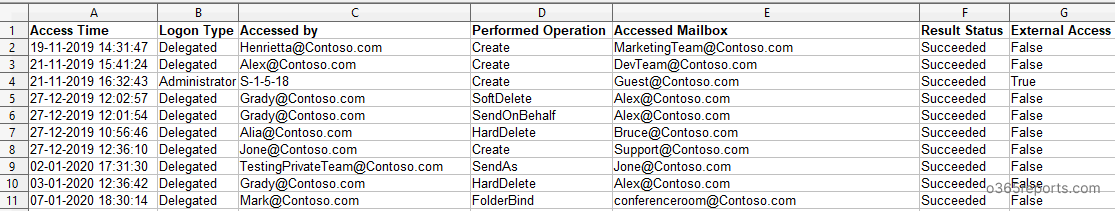
Sample Output – Office 365 Non-Owner Mailbox Access Report:
The exported report contains following attributes: Access Time, Logon Type, Accessed by(Non-owner), Performed Operation, Accessed Mailbox(Delegated Mailbox), Result and the External Access.
Export Non-Owner Mailbox Access Report-Script Execution:
The script can be executed with both MFA enabled account and non-MFA account. You can use the below format to run the script.
|
1 |
./NonOwnerMBAccessReport.ps1 |
By default, the script excludes External user access. I.e., system-generated events.
More Use-cases of ‘Non-Owner Mailbox Access Report’ Script:
Audit Non-Owner Mailbox Access Report for Past 90 Days:
By default, the script audits non-owner mailbox access for the past 90 days. To export Office 365 non-owner mailbox auditing report for the last 90 days, run the script as follows.
|
1 |
./NonOwnerMBAccessReport.ps1 |
Export Non-Owner Mailbox Access Report within a Given Interval:
To export office 365 delegate access report for a specific period, execute the script with –StartDate and –EndDate params.
|
1 |
./NonOwnerMBAccessreport.ps1 -StartDate 01/15/23 -EndDate 1/30/23 |
The date should be formed as MM/DD/YY. The above script will export non-owner mailbox access from Jan 15, 2023, to Jan 30, 2023.
Audit Mailbox Access by Delegates and Admins:
In general, non-Owner mailbox access includes administrators, delegates, and external users. In Exchange Online, external users refer the access by Microsoft datacenter administrator.
To export mailbox access by delegates and admins (excludes external users), run the script as follows.
|
1 |
./NonOwnerMBAccessreport.ps1 |
Export Non-Owner Mailbox Activity Report including External Access:
You can export all non-owner accesses that performed by admins and delegated users inside the organization and access by external users (Microsoft datacenter administrator in Exchange Online).
To audit non-owner mailbox access with external users’ activity, run the script with –IncludeExternalAccess param set to $True.
|
1 |
./NonOwnerMBAccessReport.ps1 -IncludeExternalAccess $True |
Schedule Non-Owner Mailbox Activity Report:
Since Search-UnifiedAuditLog has the past 90 days of data, you may require old audit logs for analysis. In that case, scheduling will help you to keep the audit log for more than 90 days.
You can schedule a non-owner mailbox action report in Task Scheduler. If you schedule the script to run once in 90 days, you can audit non-owner mailbox access at any time you want. So, you can store years of audit logs further analysis.
|
1 |
./NonOwnerMBAccessReport.ps1 -UserName admin@contoso.com -Password XXXX |
You can use Task Scheduler to run the PowerShell script.
Run the PowerShell Script using Certificates:
When you want to run the script unattended, you can choose this method. To use certificates, you must register the app in Azure AD and connect to MS Graph using certificate.
|
1 |
.\NonOwnerMBAccessReport.ps1 -Organization <Org> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> |
You can use either a CA certificate or create a self-signed SSL certificate. Most admins prefer self-signed certificates for internal use.
Overcome the Security Issues Effortlessly with AdminDroid
The above reports provide information on non-owner mailbox access by delegates, admins, and external users and even pull data for specific intervals. But do we require only these reports? Nah, you must keep a close eye on more than just this, and a few of them are:
- Access by Suspicious IPs: If non-owner mailbox access is coming from an unfamiliar/suspicious IP address, it could be a sign of malicious activity.
- Multiple Access from the Same User: If a single user accesses a non-owner mailbox multiple times in a short period, it could be a sign of a potential data breach or unauthorized access.
The list goes on and on, such as monitoring access during non-business hours, auditing only a specific mailbox, etc. Therefore, if you prefer to have everything in one dashboard, AdminDroid Exchange Online monitoring tool is the right choice.
Get a Step Closer with Non-Owner Mailbox Access
AdminDroid’s non-owner mailbox access report provides admins with a high-level overview of the mailbox accessed time, failed access attempts for each non-owner mailbox, find user activity during off-hours, etc. Not stopping here! You can further analyze the IP login info and spot suspicious activities instantly without doing much work.
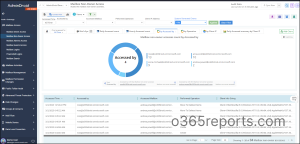
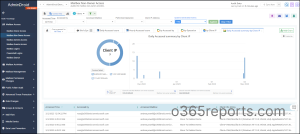
Moreover, the AdminDroid Exchange Online auditing tool comes packed with a whopping 170+ Exchange Online reports to track, schedule, and receive alerts on every activity. Get started now and experience the full potential of the AdminDroid Exchange Online management tool. And the best part is the AdminDroid Microsoft 365 reporter provides 120+ free reports on Azure AD management completely!
Don’t let the complexities of Office 365 management bring you down – let AdminDroid take the wheel!
AdminDroid features over 1800+ reports and 30+ insightful dashboards on Exchange Online, SharePoint Online, Microsoft Teams, OneDrive for Business, and every other Office 365 service in an easy-to-use, intuitive interface with sleek graphical dashboards. Download AdminDroid now and explore the features with a 15-day free trial!
I hope this blog will help you to detect who accessed another user’s mailbox and identify accidental or malicious operations performed by non-owner. This report will help you with compliance and litigation requirement.