As organizations increasingly rely on Microsoft 365 for their day-to-day operations, offboarding plays an important role in upholding enterprise security and data governance. Microsoft 365 offboarding goes beyond merely deactivating an email account, involving the removal of user access across various Microsoft 365 applications and services such as SharePoint, OneDrive, Teams, etc.
Admins must follow the Office 365 offboarding best practices and should make use of Microsoft 365 offboarding tools to avoid data-related risks in the organization. It is also possible for the admins to automate M365 user offboarding using lifecycle workflows, which streamlines the user management task same as Power Automate. Once offboarding is complete, it is also crucial for admins to verify that departing employees no longer have access to company resources. One method to ensure this is by thoroughly auditing the logs of Microsoft 365 offboarded user activity. Additionally, consider converting ex-employee mailboxes into inactive mailboxes to safeguard their data while retaining access for compliance purposes.
Why Should Admins Audit Offboarded User Activity?
Auditing offboarded user activity in Microsoft 365 is crucial for several reasons, including security, compliance, and data protection.
- Security Reasons: Auditing helps detect and prevent access attempts by compromised credentials, even after deactivating a user account.
- Data Protection: Admins can track offboarded users to ensure they don’t try to access or download sensitive data, safeguarding against potential breaches.
- Compliance Requirements: To meet industry regulations, auditing provides a clear record of data access, aiding in compliance verification and demonstrating adherence to standards.
- Legal and Investigative Purposes: In the event of a security incident or a data breach, monitoring the activities of offboarded users helps in understanding the scope of the incident. Further, audit log of offboarded users serves as a useful backup for future legal reference and investigations.
- Preventing Insider Threats: Auditing offboarded user activity helps identify any unusual or suspicious behavior that might indicate malicious intent, preventing potential harm to the organization.
Audit Offboarding User Activity with PowerShell
Given the dynamic nature of Microsoft 365 admin portals and user interfaces, many administrators find it more convenient to utilize PowerShell for their tasks. While Microsoft Purview Audit Log Search and the Search-UnifiedAuditLog cmdlet offer some capabilities in this regard, it may not provide a comprehensive view or allow for extensive customization. If the data retrieval process is not executed accurately, there is a risk of potential data loss.
To address this challenge: Opt for a dynamic PowerShell script to seamlessly audit offboarded user activities and conquer challenges effortlessly.
Script Highlights
- The script uses modern authentication to connect to Exchange Online.
- The script can be executed with MFA-enabled accounts as well.
- Exports report results to CSV file.
- The script exports the audit log for 180 days by default.
- Allows you to track audit log report for a custom period.
- Automatically installs the EXO module (if not installed already) upon your confirmation.
- The script is scheduler friendly. I.e., Credentials can be passed as a parameter instead of saving inside the script.
- The script supports certificate-based authentication (CBA).
Script Download: TrackOffboardedM365UserActivities.ps1
Microsoft 365 Offboarded User Activity Report – Script Execution Steps:
- Download the script and launch Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1: You can run the script with MFA and non-MFA accounts.
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId <OffboardingUserUPN> |
Note – You have to enter the username of the offboarding employee.
Method 2: Execute the script with explicit credentials (Scheduler-friendly).
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId <OffboardingUserUPN> -AdminName <ExecutingAdminUPN> -Password <Password> |
While the method is compatible with schedulers, it’s essential to highlight that it is effective exclusively for non-MFA accounts. To disable MFA for an individual user and execute the script, leverage Conditional Access policy.
Method 3: You also have the option to run the script using certificate-based authentication, which is scheduler-friendly.
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId <OffboardingUserUPN> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -Organization <Organization> |
Note – Depending on your requirements, you can create a self-signed certificate. Before employing certificate-based authentication, it is crucial to register an application in Azure AD.
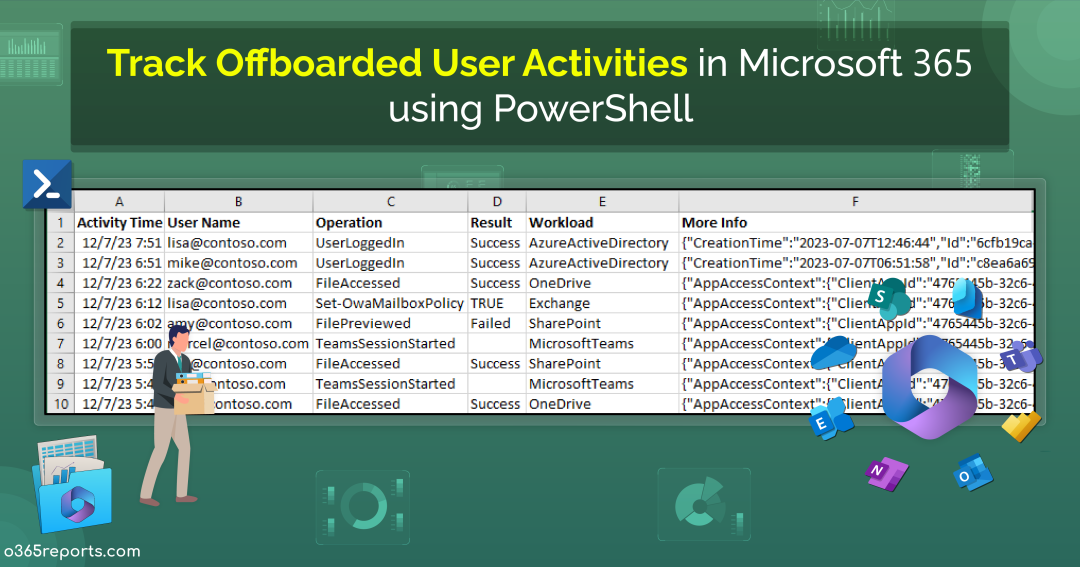
Microsoft 365 Offboarded User Report – Sample Output
The exported Microsoft 365 offboarded user activity report shows the following attributes:
- Activity Time
- User Name
- Operation
- Result
- Workload
- Detailed Audit Data
Here is a sample output image generated by the PowerShell script:
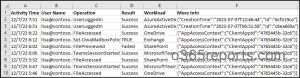
Note – For certain workloads that lack a Result Status column, it is displayed as empty.
Get the Most Out of the Microsoft 365 Offboarded User Activities PowerShell Script
The script provides some built-in filtering parameters according to your needs, and its use cases are listed below.
- Export Microsoft 365 offboarded user activity history for the past 180 days
- Audit Microsoft 365 offboarded user activity within a particular interval
- Schedule offboarded user activity report
- Get a monthly offboarded user activity report
Export Microsoft 365 Offboarded User Activities for 180 days
Admins commonly employ the PowerShell cmdlet Search-UnifiedAuditLog to generate a report spanning 90 days. Notably, due to the recent extension of audit logging retention to 180 days, admins now have the capability to extract audit logs covering an extended timeframe. Utilize the script provided to export the audit log of offboarded user activities for an extended 180-day period.
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId lisa@contoso.com |
The above example will export activities performed by offboarded user lisa in the past 180 days.
Track Microsoft 365 Offboarded User Activity for a Custom Time Interval
Admins can also create a customized activity report by specifying the desired timeframe using the –StartDate and –EndDate parameters. With these parameters, you have the flexibility to generate an Office 365 user’s audit report for the past 7 days, 30 days, 90 days, or any other specific period as needed.
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId lisa@contoso.com -StartDate 12/21/23 -EndDate 12/31/23 |
The above example provides a report on the activities of offboarded Lisa during the period from Dec 21, 2023, to Dec 31, 2023.
Schedule Offboarded User Activity Report
Scheduling an offboarded user activity report in Microsoft 365 ensures timely identification and mitigation of potential security risks. For example, if a former employee’s account is accessed post-offboarding, regular report scheduling enables admins to promptly revoke access and safeguard sensitive data, maintaining the organization’s cybersecurity posture. Make use of the provided format to seamlessly run PowerShell script from the Task Scheduler.
|
1 |
./TrackOffboardedM365UserActivities.ps1 -UserId lisa@contoso.com -AdminName admin@contoso.com -Password XXX |
Get a Monthly Offboarded User Activity Report
To obtain a monthly summary of offboarded user activity, simply run the following script:
|
1 |
./TrackOffboardedM365UserActivities.ps1 -StartDate ((Get-Date).AddDays(-30)) -EndDate(Get-Date) -UserId lisa@contoso.com |
For example, when an employee, such as Lisa in this case, leaves the company, it is crucial to track and document the user’s activity. It serves as a proactive measure to identify any anomalous or suspicious activity, preventing potential unauthorized downloads of official documents by the departing employee.
Gain Seamless Insights and Details on Microsoft 365 User Activities with AdminDroid
AdminDroid simplifies Microsoft 365 offboarding by automating all critical steps, from session revocation to role removal. With bulk offboarding, and instant revert capabilities, it delivers unmatched efficiency, accuracy, and confidence.
But offboarding isn’t the final step! You also need to verify and monitor user activities to ensure there are no loose ends. While PowerShell can do this, it’s tedious and time-consuming. AdminDroid’s Microsoft 365 Automation tool offers a far simpler, code-free way to get full visibility.
With AdminDroid’s dynamic user activity reports, you can track:
User Logins:
- All successful & failed login attempts
- Users failed to pass MFA challenge
- Disabled user login attempts
- User password changes
User Mailbox activities:
- All emails sent and received
- Emails sent to and received from external domains
- Spam/Phish/Malware sent & received
- Bulk email deletions
- Inbox rule creations
File Transfer activities:
- SharePoint file/folder/page external sharing
- SharePoint file deletion and restoration activities
- OneDrive file/folder access activities
- OneDrive file deletion and restoration activities
- File/Folder sharing in Teams chat
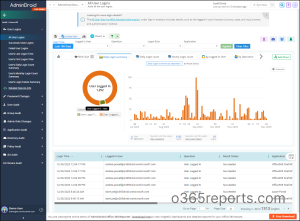
AdminDroid provides more than just reports; it delivers a comprehensive dashboard that offers a detailed overview of user activities within Microsoft 365.
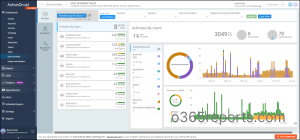
In addition, AdminDroid provides a wide range of features, including 1800+ pre-built reports and 30+ Office 365 dashboards. These reports provide comprehensive insights, covering areas such as reporting, auditing, analytics, usage statistics, security, and compliance.
Besides, AdminDroid offers a free Azure AD reporting tool that includes 120+ reports & dashboards covering various categories. These reports come with features such as exporting, sending reports via email, and scheduling.
Download AdminDroid Microsoft 365 management tool now and experience the power of simplified administration!
I hope this blog is useful for auditing Microsoft 365 offboarded user activities in your organization. If you have any queries, you can reach us through the comment section.