As the cybersecurity landscape evolves, a well-executed MFA deployment acts as a fortified shield, tirelessly safeguarding M365 from malicious intruders. However, in some cases, like when using a break glass account to sign in or when running unattended scripts, bypassing MFA’s shield becomes necessary. So, how can you exempt such specific accounts from MFA ? That’s where the Conditional Access policies have come in💥!
Conditional Access policies can be utilized to disable MFA for a specific user account. This approach ensures that you can handle exceptional situations without compromising the overall security posture.
So, let’s learn how to disable MFA for a single user using the Conditional Access policy.
Choose CA Policies to Skip MFA for a Single User
While Security defaults provide a robust baseline for overall security, they might not offer the granularity needed to customize MFA settings for individual accounts. To address this need, organizations can leverage Conditional Access (CA) policies.
By the way, having an Azure AD P1 or P2 license is the only prerequisite for creating a Conditional Access policy.
Points to Remember: Make sure to turn off Security defaults, if you have enabled for your tenant. Because you can’t use Security defaults and Conditional Access polices simultaneously.
Disable MFA for a Single User Using Conditional Access Policies
To enable MFA for your organization and exclude a specific user from MFA, follow the steps below.
- First, sign-in to Microsoft Entra admin center.
- Then, navigate to the ‘Protection’ drop-down box and select the ‘Conditional Access’ option.
- Click on ‘ + Create new policy ‘ to create a new policy and give a suitable name for your policy.
- Under Assignment, add ‘ All users ‘ in the Include section and choose the exempted account in the Exclude section shown in ‘Users’ blade.
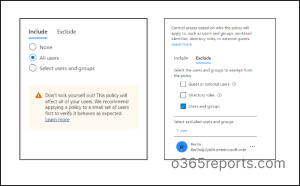
- Under the Access controls section, grant access by selecting ‘Require multifactor authentication‘ from the ‘Grant blade’, and then click ‘ Select‘ to confirm your choice.
- Finally, enable the policy to ‘On’ mode and click ‘ Create ‘.
Thus, a Conditional Access policy that does not require MFA for the specified user account has been successfully created. So, the user is not prompted for Multifactor authentication.
Note:
If your organization already has Conditional Access (CA) policies in place, it’s best to create new ones instead of modifying existing policies. Remember, the more restrictive policy applies if a user is included in two conflicting policies regarding Multi-Factor Authentication (MFA).
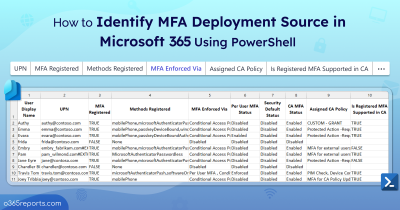
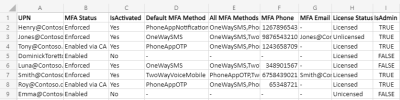
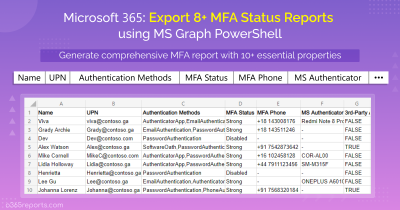
If managing this feels overwhelming, use this PowerShell script to identify which Conditional Access policies require MFA for each user. This way, you can pinpoint the exact policies impacting your users’ MFA requirements and avoid policy conflicts.
In clear, let’s consider the two policies:
- Policy A: This policy will exclude a user from the MFA requirement.
- Policy B: This policy will include the same user in the MFA requirement.
In this scenario, since Policy B is the one that enforces MFA for the user, it will take precedence over Policy A. The user will be subject to MFA as per the requirements set in Policy B, and the exclusion mentioned in Policy A will not apply.
We have covered some additional cases below, which depict the importance of Conditional Access policies to skip MFA for specific organization needs.
- Exclude MFA for Users and Groups Under Certain Conditions
- Disable MFA for Users with Azure AD Roles Using CA Policies
Exclude MFA for Users and Groups Under Certain Conditions
Case 1: Users/Groups Sign-in to Resources via Trusted Network
Apart from the above-mentioned case, you can skip MFA for users or Groups under certain conditions. For example, you can skip MFA for a user or a group of members when they are accessing critical resources from a trusted office network using CA policy.
To achieve this, you need to create a named location using trusted IP range. Subsequently, add the named location in the conditions blade of the policy, targeting the selected users or groups based on your requirements.
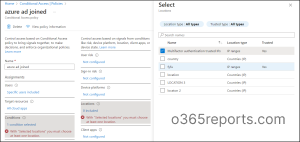
The configured policy will exempt MFA for users/groups, when accessing critical resources from the trusted office network. However, when these users attempt to access the same resources from outside the office network, they will still be required to complete the MFA process.
Case 2: Users/Groups Sign-in to Microsoft 365 Resources via Compliant Devices
Multi-Factor Authentication (MFA) requirement can be skipped for users and groups who are accessing resources from devices that comply with the organization’s security standards and policies. In simpler terms, you can reduce the necessity of MFA for users and groups signing in from compliant devices. To achieve this, create a device condition as shown in the image below.
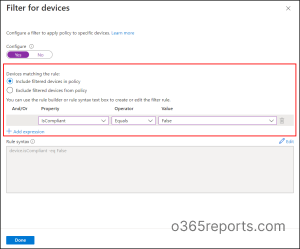
Then include specific users/groups based on your requirement, and grant access by requiring Multifactor authentication.
This policy will require MFA for users logged in using non-compliant devices, while users from compliant devices will have access without MFA.
Disable MFA for Azure AD Roles Using CA Policies
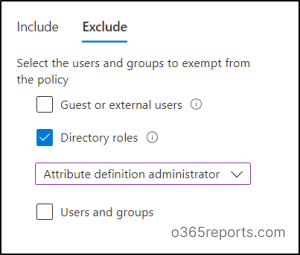
As an added advantage, you can skip MFA for users with a specific Azure AD role. To achieve this, you can follow the same procedure as mentioned earlier, but this time, instead of excluding specific users, add the designated directory role to the “Exclude” section of the policy.
This modification will ensure that users with the specified role can seamlessly access M365, enhancing their efficiency in critical situations.
Note: Misconfigurations in Conditional Access policies can lead to sign-in failures, affecting both the security and functionality of your Microsoft 365 environment. In such cases check which Conditional Access policy is blocking user’s sign-in and troubleshoot the policies effectively with “Conditional Access insights and reporting workbook“.
Viewing CA policy changes helps identify and rectify misconfigurations promptly.
Monitor Conditional Access Policies Effectively Using AdminDroid
After setting up the policies, you are required to monitor whether the designated individuals have successfully signed in and whether others have undergone MFA authentication. While native reporting methods offer some insights into user sign-ins, they often lack in-depth details such as the exact count of successful sign-ins for each user, the number of failed sign-ins, and other critical metrics. To provide you with deep-drilled insights into Conditional Access policies, AdminDroid comes in!
AdminDroid Azure AD reporter provides you with extensive insights into Conditional Access policy configurations, assessments of policy effectiveness, user behavior analysis, and other valuable information. These insights help you have a keen eye on the configured Conditional Access policies in Azure AD.
Below are some of the reports available with AdminDroid that facilitate efficient management of Conditional Access policies.
Sign-in Audit Reports
- Sign-ins blocked by CA policy
- Sign-ins successfully passed the policy
- Sign-ins failed to bypass CA policy
Conditions Configured in CA policies
- Role-based CA policies
- Platform/location specified policies
- Location/device-based policies
CA Policies with MFA Requirement
- MFA configured CA policies
- Assignment conditions of MFA enabled policies
In addition to monitoring Conditional Access policies, AdminDroid provides extensive insights into the entire Microsoft 365 environment! And here’s the jaw-dropping part! AdminDroid offers a whopping 120+ auditing and statistical reports, 10+ insightful Azure AD dashboards, all completely free of charge.
Achieve complete control over Azure Active Directory management with AdminDroid!
Importantly, with AdminDroid, you can access 1800+ reports providing insights into usage, security, and compliance across Microsoft 365 resources such as Exchange Online, OneDrive, SharePoint Online, Yammer, and more.
So, discover the full potential of AdminDroid with a 15-day free trial. Once you witness its capabilities, we’re certain you’ll be hooked and won’t want to look back.
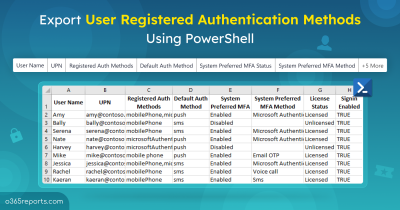
Thus, Conditional Access policies provide the most effective and flexible solution for deploying granular MFA. By leveraging Conditional Access policies, you can customize MFA settings to meet your specific needs without compromising the security of your Microsoft 365 environment. Moreover, admins can export Conditional Access policies to Excel using PowerShell for verifying deployed MFA policies.
Hope you have gained enough information on how to disable MFA for a single user using CA policy. Furthermore, feel free to reach us in the comments section for any assistance.