Ever wondered who activated a privileged role at 2 AM last night? Or why someone deactivated a critical admin role right before a deployment? If you’re managing Microsoft 365 environments, questions like these are part of the job. That’s where Privileged Identity Management (PIM) auditing comes into play.
Auditing PIM role activations and deactivations is an essential part of maintaining control over privileged access. Keeping track of who’s activating or stepping away from sensitive roles helps strengthen your organization’s security posture and compliance requirements. This also complements your efforts to manage PIM policies and enforce role settings effectively.
In this blog, we’ll walk you through everything you need to know about monitoring PIM role activity—from understanding what gets logged during role activations and deactivations to identifying who elevated or stepped down from privileged roles and when.
Ways to Audit PIM Role Activations
There are three main ways to audit PIM role activations and deactivations in your Microsoft Entra environment:
- View PIM audit logs in Microsoft Entra admin center
- PIM role assignment history using Microsoft purview
- Export PIM role activity using PowerShell (Recommended)
1. View PIM Audit Logs in Microsoft Entra Admin Center
Follow the steps below to review and filter PIM role activity from the Entra admin center.
- Sign in to the Microsoft Entra Admin Center and navigate to Identity Governance > Privileged Identity Management
- In the PIM window, select Microsoft Entra roles under Manage
- Then, select Resource Audit under Activity. To export your data, click Export at the top of the table and hit Download.
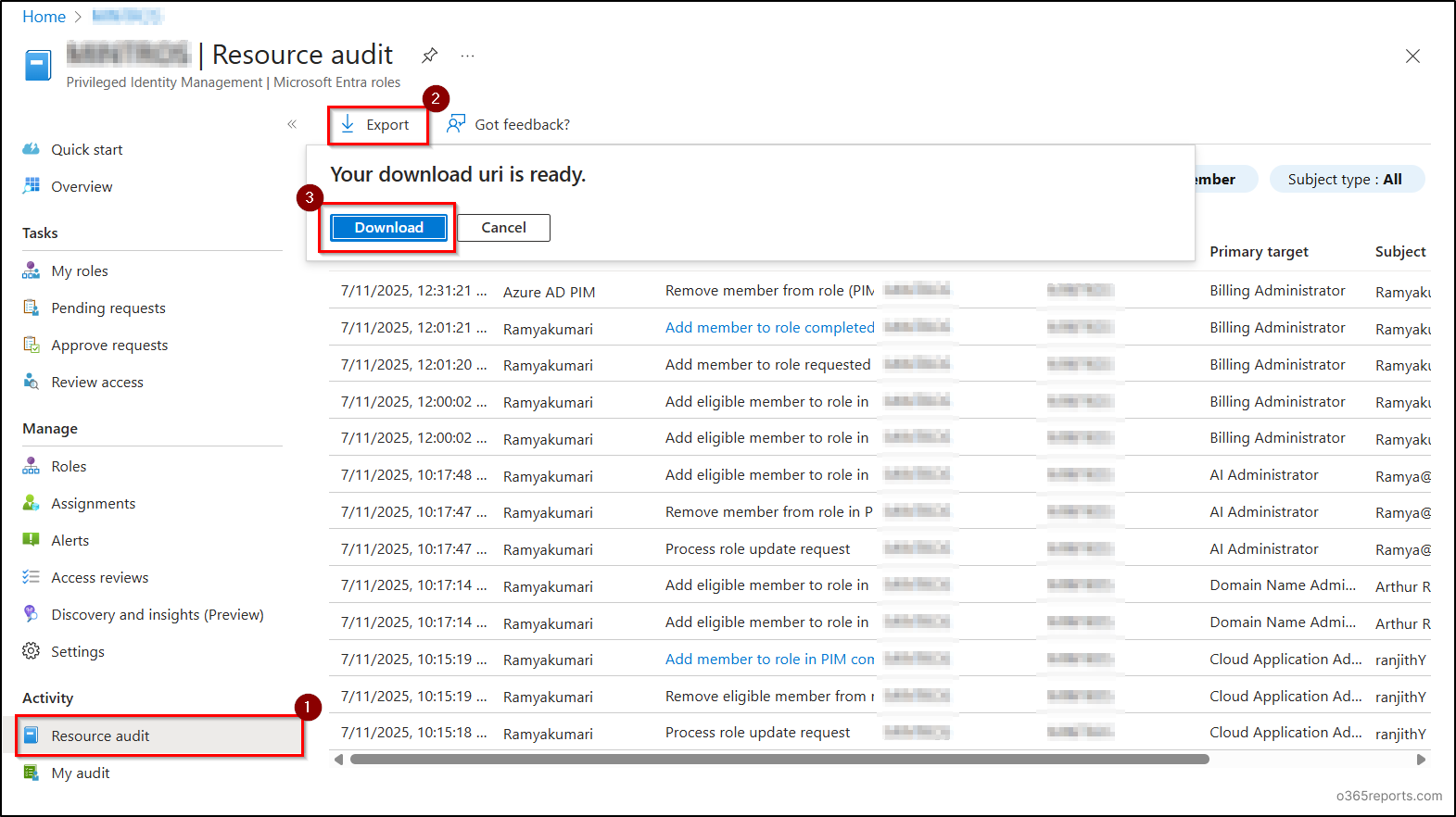
This method provides a simple way to review recent PIM role activities, including both direct role assignments and activations through role assignable groups. However, keep in mind that only the last 30 days of audit data are available in Entra audit log.
2. View PIM Role Activations Using Microsoft Purview
If you want to audit data for more than 30 days, Microsoft Purview provides up to 180 days of privileged role activities.
You can follow the steps below to get PIM role assignment history.
- Sign in to the Microsoft Purview Admin Center and navigate to Solutions and select Audit.
- Enter the time range for which you must audit and enter the operation valuses Add member to role,Remove member from role under Activities – operation names for role activation and deactivation and hit Search.
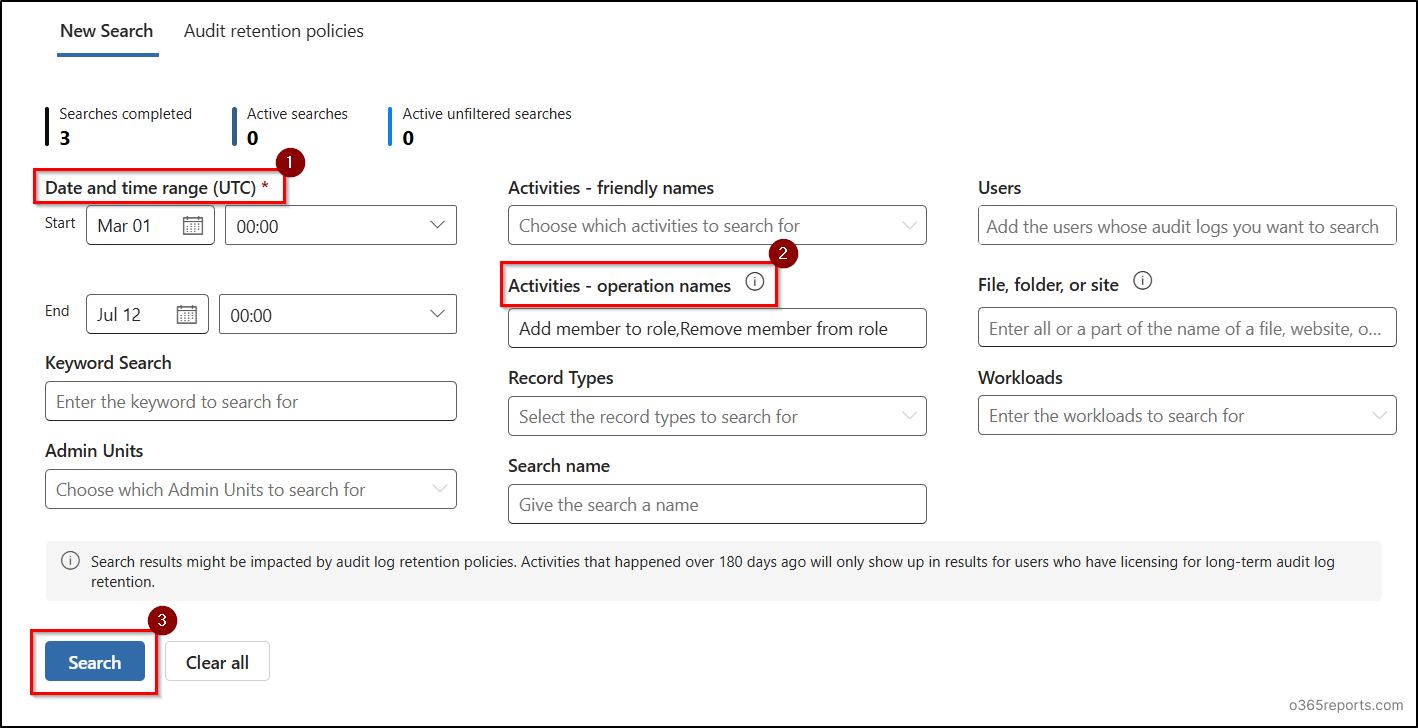
Your search will be queued. Check after some time and when the Job Status is Completed, you can view the audit data.
- Now, select your audit search and click Export. Your data will be available for download in a few minutes. Then, click on the Downloads file to export your PIM role assignment status.
This method shows all role assignment changes, not just PIM-related actions. Since Microsoft Purview doesn’t support advanced filtering like narrowing by initiator (who performed the action), identifying only PIM activations or deactivations may require manual review after exporting the data.
3. Audit PIM Role Changes Using PowerShell
To make things easier, we’ve built a PowerShell script that automates the entire process from retrieving PIM role activations and deactivations to exporting the report and delivering it straight to your inbox.
Download script: AuditPIMRoleActivations.ps1
Script Highlights
- Supports generating report for PIM role activations only.
- Supports generating report for PIM role deactivations only.
- Automatically installs the Exchange Online PowerShell module (if not installed already) with your permission.
- Sends PIM role activation report via email to one or more recipients.
- Filters activity logs for a specific admin.
- Exports report in both HTML and CSV formats.
- Scheduler-friendly for automated PIM audits.
- Supports certificate-based authentication too.
PIM Role Activations and Deactivations Report – Sample Outputs
PIM Role Activation and Deactivation Report
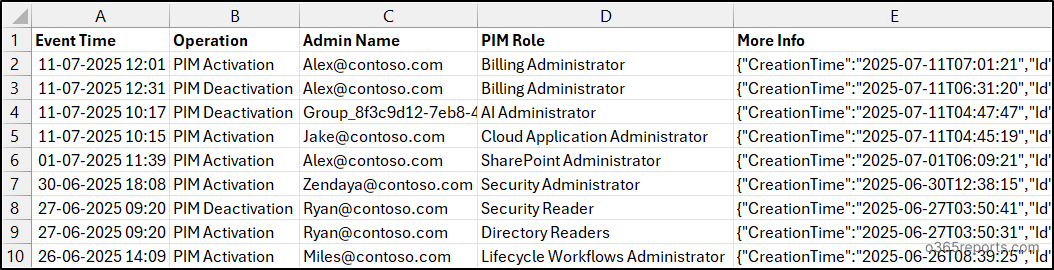
Automated Email Notification for PIM Role Activations

PIM Role Activity Logs PowerShell – Script Execution Methods
- Download the PowerShell script shared above.
- Open Windows PowerShell and navigate to the folder where the downloaded script is stored.
- You can choose any of the following methods to execute based on your requirements.
Method 1: Execute the script with an MFA or non-MFA account.
|
1 |
.\AuditPIMRoleActivations.ps1 |
This script exports a report of all PIM role activities in the last 180 days.
Method 2: Execute the script using certificate-based authentication.
To use certificate-based authentication, you need to register the application in Entra ID, which enables you to connect Exchange Online using certificate. Based on your requirements, you can either create a self-signed certificate or use a CA certificate.
|
1 |
.\AuditPIMRoleActivations.ps1 -Organization <DomainName> -ClientId <AppId> -CertificateThumbprint <CertThumbPrint> |
This approach is scheduler friendly.
Method 3: Schedule the script by explicitly mentioning credential (Less recommended).
|
1 |
.\AuditPIMRoleActivations.ps1 -Username admin@contoso.com -Password XXX |
The above method supports only non-MFA accounts. If the admin account has MFA, you need to disable MFA using CA policy use it for scheduling purposes.
Automate PIM role audit PowerShell script – Unlock the full potential
With flexible filtering options, this script makes auditing PIM role activity in Microsoft Entra both efficient and customizable.
Here’s how the script helps you stay on top of every PIM role activity:
- Audit PIM role activations
- Audit PIM role deactivations
- Generate PIM audit report for a custom period
- Track PIM role activations by a specific user
- Automate PIM audit report delivery via email to multiple recipients
- Schedule and send PIM role activations report daily
1. Audit PIM Role Activations
Need to audit elevated access specifically for users assigned to an admin role? Use the -PIMActivationsOnly switch to filter the results for activation events only. It’s perfect for reviewing recent privilege elevations or during access reviews.
|
1 |
.\AuditPIMRoleActivations.ps1 -PIMActivationsOnly |
This format fetches all PIM role activations that occurred in the last 180 days. Based on this report, you can monitor admin activities to understand what actions were performed during their privileged access.
2. Audit PIM Role Deactivations
Want to check who deactivated their role and when? The -PIMDeactivationsOnly parameter lets you filter just the deactivation events, ideal for post-deployment checks or unexpected role removals.
|
1 |
.\AuditPIMRoleActivations.ps1 -PIMDeactivationsOnly |
This lists all recent PIM role deactivations in your tenant.
3. Generate PIM Audit Report for a Custom Period
Want to pull PIM activity for a specific audit window or compliance period? Use the -StartDate and -EndDate parameters to narrow down the report to just the timeframe you care about.
|
1 |
.\AuditPIMRoleActivations.ps1 -StartDate -StartDate "06-27-2025" -EndDate "07-14-2025" |
This format fetches all PIM activations and deactivations that occurred between June 27 and July 14, 2025.
4. Track PIM Role Activations by a Specific User
If a particular admin is under review, or you’re validating activity during a critical change window, use –PIMAdminName to isolate their activations and deactivations.
|
1 |
.\AuditPIMRoleActivations.ps1 -PIMAdminName alex@contoso.com |
The above format exports PIM activations and deactivations performed by the user alex@contoso.com in the last 180 days.
5. Send PIM Audit Reports via Email
Need to notify your security or compliance team? The script supports sending audit reports via email. Use the –Recipients parameter to specify one or more addresses, and the -FromAddress to define the sender.
|
1 |
.\AuditPIMRoleActivations.ps1 -Recipients "Alex@contoso.com,security@contoso.com" -FromAddress alerts@contoso.com |
This format generates a report of all PIM role activations and deactivations and sends report to the specified recipients from the given sender address.
Note: If using certificate-based authentication (CBA), the -FromAddress is mandatory. For interactive logins, the logged-in user will be considered the sender by default.
6. Automatically Send Daily PIM Activation Reports to Email
Privileged access can change in a flash. An admin might activate a role, complete a task, and deactivate it just minutes later. That’s why it’s important to monitor PIM activations on a daily basis.
However, digging through audit logs or running PowerShell scripts manually can be time-consuming. Instead, simply schedule this script in Task Scheduler or Azure Automation to receive the PIM role activation report directly in your inbox, making daily reviews effortless.
|
1 |
./AuditPIMRoleActivations.ps1 -StartDate (Get-Date).AddDays(-1).ToString("yyyy-MM-dd 00:00:00") -EndDate (Get-Date).ToString("yyyy-MM-dd 00:00:00") -Recipients 'secops@contoso.com,compliance@contoso.com' -FromAddress 'alerts@contoso.com' -HideSummaryAtEnd |
This format sends a daily PIM activation report for the previous day to multiple recipients, with no UI interruptions. It’s ideal when integrating with task schedulers or other automated tools.
Whether you’re responding to a security incident or conducting regular audits, this script gives you the clarity and control needed to keep privileged access in check! You can also view admins with permanent role assignments to get a complete picture.
Go Beyond Basic PIM Auditing with AdminDroid
Tracking who activated or deactivated privileged roles through PIM is critical. But without clear visibility into role changes, important access events can easily go unnoticed.
That’s where AdminDroid’s Azure AD management tool comes in. With pre-built reports and real-time dashboards, AdminDroid gives you instant visibility into every PIM activation and deactivation happening across your tenant.
- Want to know who activated a Global Admin role last week?
- Need to audit deactivations of the Exchange Administrator role during an incident review?
- Looking for trends in hourly role activations across your tenant?
- Want to get alerted the moment someone activates a high-privilege role?
AdminDroid answers all these questions instantly!
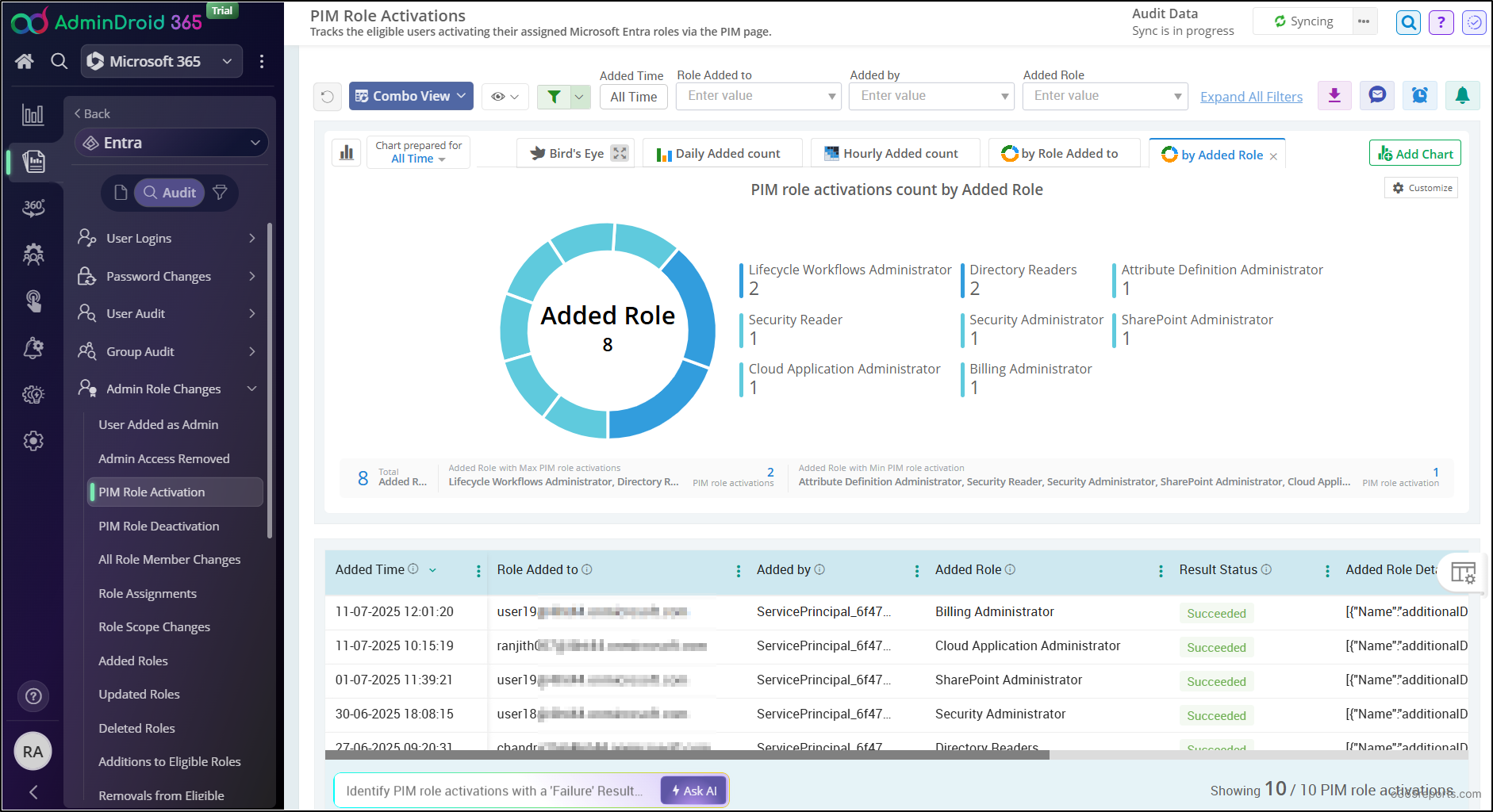
But AdminDroid doesn’t stop at PIM. It’s a complete Microsoft 365 analytics platform that helps you monitor everything, from user sign-ins in Entra ID to mailbox activities in Exchange Online, file sharing in OneDrive and SharePoint, and collaboration trends in Teams.
With 3500+ pre-built reports and 100+ interactive dashboards, and 450+ management actions, AdminDroid makes it easy to audit, visualize, and manage data across your entire tenant!
👉 Download AdminDroid today and see how effortlessly you can manage and monitor your entire Microsoft 365 environment.
We hope this blog helps you take control of PIM role auditing in Microsoft 365, making it easier to monitor privileged access and review role changes. If you have any further questions or feedback, feel free to drop them in the comments. We’re here to help!






