As a Microsoft 365 admin, ever pondered how your sub-admins wield their privileged powers? We get it – managing multiple admins is no small feat. Microsoft 365 administrators hold significant responsibilities like getting users on board, handling passwords, overseeing various user activities, user offboarding, and many more. While their roles are essential, the potential for the misuse of such extensive powers is a persistent concern.
Fear not, as auditing Microsoft 365 admin activities comes to your rescue! This practice allows you to monitor every admin activity closely. In this blog, we’ll explore the significance of auditing and various methods of auditing admin activities in Microsoft 365. But that’s not all – to make your Microsoft 365 admin auditing process a breeze, we have crafted a handy PowerShell script and discussed it for your convenience.
Why Audit Admin Activities in Microsoft 365?
Auditing admin activities in Microsoft 365 is imperative for several key reasons:
- Security Monitoring: Admin accounts in Microsoft 365, with elevated privileges, demands vigilant monitoring. This is crucial to swiftly detect and respond to potential security threats or unauthorized actions that could compromise your Microsoft 365 security.
- Risk Mitigation: Admins possess the authority to make configuration changes, manage permissions, and access sensitive information. Regular audits are essential for identifying risks and ensuring adherence to best practices to protect Microsoft 365 admin accounts.
- Incident Response: In the unfortunate event of a security incident or data breach, auditing logs of admin activities offers valuable insights for incident response efforts. This information is crucial for identifying the root cause, determining the scope, and assessing the impact of the incident.
- Compliance Requirements: Numerous industries and organizations are bound by compliance requirements and regulations that necessitate the constant monitoring and auditing of admin activities. Thus, continuously auditing Microsoft 365 admin activities is significant.
How to Audit Admin Activity in Microsoft 365?
Admin activities in Microsoft 365 can be audited from two primary places:
1. Microsoft Entra Admin Center (Azure AD Audit Logs):
Azure AD audit logs within the Microsoft Entra admin center offer a focused way to monitor both Microsoft 365 user and admin activities. Microsoft Entra (Azure AD) audit logs specifically helps to track Azure AD activities of M365 admins, providing detailed records of actions such as user additions, password resets, policy updates, group member additions, and license changes.
Monitoring Azure AD activities of admins alone may not be sufficient, especially considering the multitude of Microsoft 365 admin roles across various workloads. Additionally, if you wish to investigate the distribution of admin privileges in your organization, you can utilize this PowerShell script to export Office 365 admins and their roles.
2. Microsoft 365 Purview Portal (Unified Audit Logs):
Moving beyond Azure AD activities, the unified audit logs in the Microsoft 365 Purview portal provides a comprehensive view of admin activities across all workloads. This portal allows you to observe admins’ activity throughout Office 365 and even download the audit log search results to a CSV file. However, it’s important to note that this approach is not user-friendly, as it requires conducting multiple searches repeatedly to achieve the desired results.
Audit Admin Activities in Microsoft 365 using PowerShell
Microsoft 365 admins often turn to PowerShell for its granular control, automation capabilities, local control and offline access, as well as efficiency in handling bulk operations. In this context, the Search-UnifiedAuditLog cmdlet plays a crucial role in capturing activities across various workloads, including Exchange Online, Microsoft Teams, SharePoint Online, Microsoft Entra ID (Azure AD), and other M365 services.
However, obtaining audit logs using this cmdlet poses challenges, and improper data retrieval can lead to potential data loss. To address this, we introduce the AdminActivityReport PowerShell script designed to export Office 365 admin activities to a CSV file. You can download the script from here and explore its functionality in the following sections.
Download Script: AdminActivityReport.ps1
Script Highlights
- The script uses modern authentication to connect to Exchange Online.
- The script can be executed with MFA-enabled accounts.
- It exports the report results to a CSV file.
- The script exports an audit log for 180 days by default.
- You can generate an admin activity report for a custom period.
- The script installs the EXO module upon confirmation, if not already installed.
- The script is scheduler-friendly; credentials can be passed as parameters.
- Finally, the script also supports certificate-based authentication (CBA).
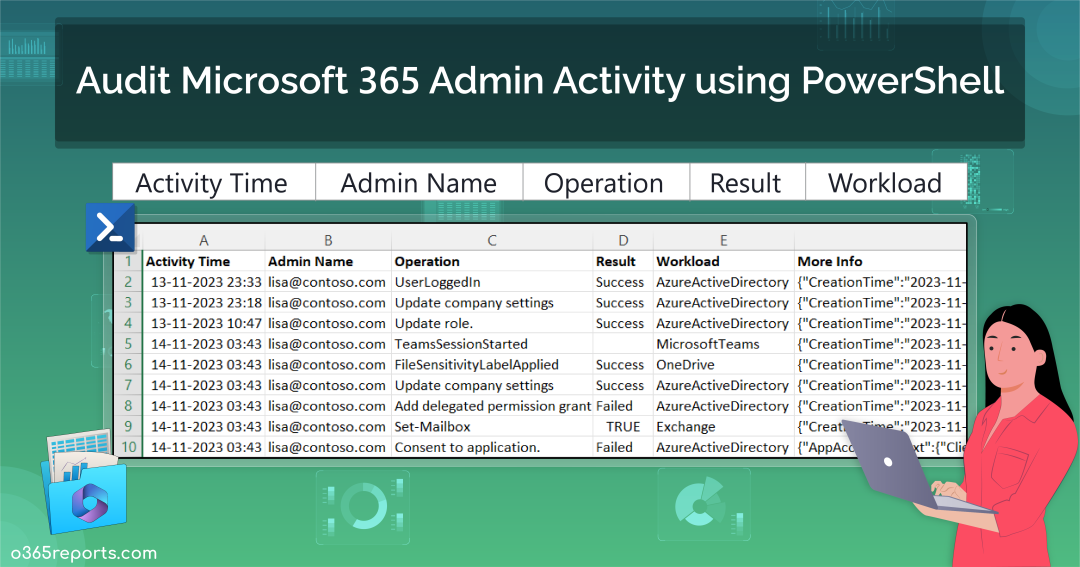
Microsoft 365 Admin Activity Report – Sample Output:
The exported Microsoft 365 admin activity report shows the following attributes:
- Activity Time
- Admin Name
- Operation
- Result
- Workload
- Detailed Audit Data
Here is a sample output image generated by the PowerShell script:
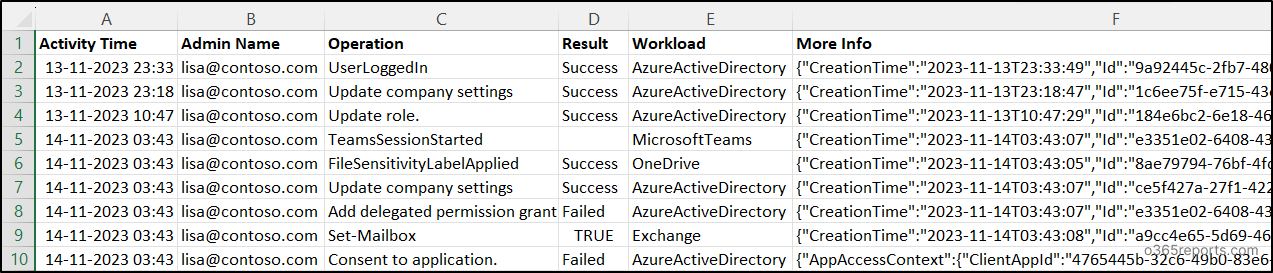
NOTE: For certain workloads that lack a Result Status column, it is displayed as empty.
How to Execute the Script?
- Download the provided PowerShell script and open it in Windows PowerShell.
- Execute the script using one of the following methods:
Method 1: You can run the script with MFA and non-MFA accounts.
|
1 |
./AdminActivityReport.ps1 -AdminId <AdminUPN> |
NOTE: If the “-AdminId” is not provided, the script will prompt the user by asking for the admin’s UPN (User Principal Name) with the message “Enter admin UPN.”
Method 2: Execute the script with explicit credentials (Scheduler-friendly).
|
1 |
./AdminActivityReport.ps1 -AdminId <TargetAdminUPN> -AdminName <ExecutingAdminUPN> -Password <Password> |
NOTE: While the method is compatible with schedulers, it’s essential to highlight that it is effective exclusively for non-MFA accounts. To disable MFA for an individual user and execute the script, leverage Conditional Access.
Method 3: You can also execute the script with certificate-based authentication (Scheduler-friendly):
Depending on your needs, use a certificate authority (CA) or create a self-signed certificate.
|
1 |
./AdminActivityReport.ps1 -AdminId <AdminUPN> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -Organization <Organization> |
NOTE: Most importantly, before using the certificate-based authentication method, you should register an app in Azure AD.
Audit Microsoft 365 Admin Activity using PowerShell Script
With this PowerShell script, you can
- Export Microsoft 365 admin activity history for the past 180 days
- Audit Microsoft 365 admin activity within a particular interval
- Schedule admin activity report
- Get a monthly Microsoft 365 admin activity report
Track Microsoft 365 Admin Activities for Past 180 Days
Admins typically use the PowerShell cmdlet Search-UnifiedAuditLog to export a 90-day report for Microsoft 365 audit logs, aiding in threat detection, pattern recognition, and forensic investigations. However, with the recent extension of audit logging retention to 180 days, administrators can now retrieve audit logs over a longer timeframe. Execute the provided script to export the admin activity history for the extended 180-day period.
|
1 |
./AdminActivityReport.ps1 -AdminId lisa@contoso.com |
The above example will export activities performed by admin lisa in the past 180 days.
In the unfortunate event that an admin falls victim to a brute force or phishing attack, resulting in compromise, exporting admin activities becomes a critical measure. If you discover that an admin account is compromised, you can enhance security by enabling MFA for admin accounts.
Audit Microsoft 365 Admin Activities for a Custom Period
While monitoring an admin’s activity over the past 180 days provides a comprehensive overview, there are instances where it’s necessary to specifically identify and focus on events that occurred within a narrower timeframe.
In situations where an admin engages in suspicious activities, such as adding themselves as a delegate to others’ mailboxes and accessing emails from a specific period, retrieving the entire log for such information can be cumbersome. To address this, parameters like -StartDate and -EndDate come in handy, allowing you to generate a targeted activity report for custom periods.
|
1 |
./AdminActivityReport.ps1 -AdminId lisa@contoso.com -StartDate 11/25/23 -EndDate 12/13/23 |
The above example provides a report on the activities of admin lisa during the period from Nov 25, 2023, to Dec 13, 2023. Utilizing these parameters, you can generate an Office 365 admin’s audit report for the last 7 days, 30 days, 90 days, 180 days, or any other required duration.
Schedule Admin Activity Report
Scheduling reports goes beyond routine monitoring and reviewing; it’s essential for preserving historical audit data. Configure periodic scheduling to preserve audit data for longer, since the Search-UnifiedAuditLog cmdlet retrieves data only within this 180-day window. Use the provided format to seamlessly run PowerShell script from the Task Scheduler.
|
1 |
./AdminActivityReport.ps1 -AdminId lisa@contoso.com -AdminName shan@contoso.com -Password XXX |
Moreover, admin activity logs can be analyzed to identify any changes or updates that might have contributed to system instability. This helps in quickly resolving performance issues and maintaining a healthy IT environment.
View a Monthly Microsoft 365 Admin Activity Report
Imagine a scenario where a user transitions to an admin role or adds new users without proper permissions or notifications. The potential harm resulting from these suspicious admin activities to your organization’s security can be alarming. Therefore, it’s crucial to regularly monitor admin activity. Run the script below to conduct a monthly audit of Microsoft 365 admin activities.
The following example retrieves audit data for the admin lisa@contoso.com over the past 30 days.
|
1 |
./AdminActivityReport.ps1 -StartDate ((Get-Date).AddDays(-30)) -EndDate (Get-Date) -AdminId lisa@contoso.com |
You can utilize the above format to schedule the script for monthly execution on the 1st, ensuring it retrieves audit data from the previous month.
Up until now, our focus has been on exploring methods to audit Microsoft 365 admin activity through PowerShell. However, if the prospect of wrestling with PowerShell has left you fatigued, it’s time to consider a much simpler solution.
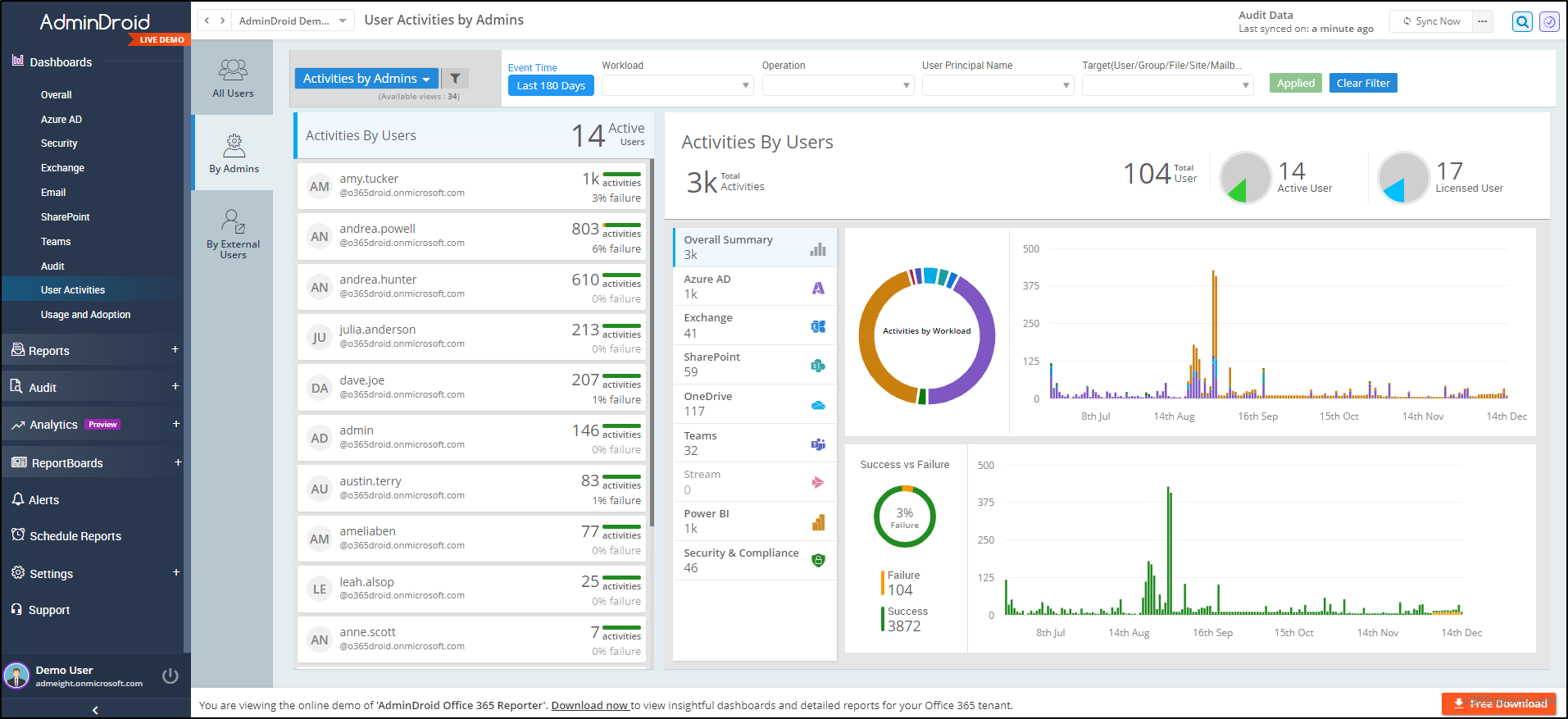
Introducing AdminDroid Microsoft 365 Reporter, your effortless solution to streamline Microsoft 365 admin auditing.
Simplify your Microsoft 365 Admin Auditing with AdminDroid Reports!
AdminDroid simplifies Microsoft 365 admin monitoring with 80+ detailed admin reports, covering aspects such as admin activities, login details, licenses, role changes, password settings, MFA settings, and more. Reports include,
- Admin Reports
- All Admins
- All Global Admins
- Admins with Management Roles
- Licensed/Unlicensed Admins
- Recently created Admins
- Admin Role Changes
- User Added as Admin
- Admin Access Removed
- All Role Operations
- Admin Security Settings
- Password reset by Admins
- Admins with/without MFA
- Admins with Password Never Expires
- Admin Login
- All Admin Login Activities
- Admin Login Failures
- Admins Daily Login Summary
AdminDroid goes beyond reports, offering a comprehensive dashboard for a detailed overview of Microsoft 365 admin activities. Such that it ensures complete monitoring of all your admins, leaving no trace unnoticed!
And AdminDroid’s Free Azure AD reporting tool provides an extensive range of 190+ Free reports, offering a 360-degree view of your Azure environment including Azure AD auditing reports for enhanced Azure AD management.
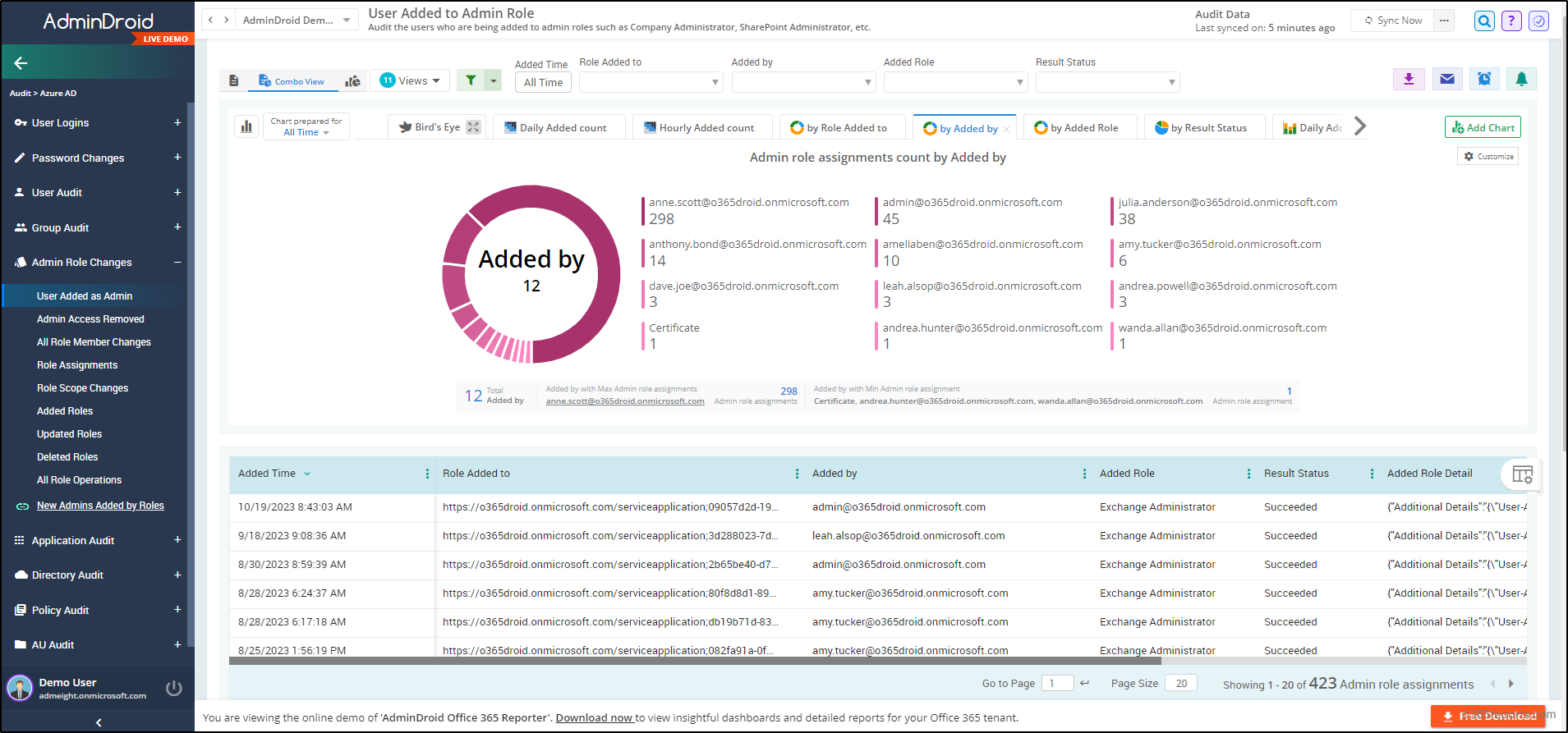
AdminDroid stands as a dedicated solution addressing IT admins’ challenges with a wealth of 1800+ comprehensive reports 📊 and 30+ visually engaging dashboards. These resources cover various services including Exchange Online, Microsoft Teams, OneDrive, SharePoint Online, Power BI, Stream and Viva Engage.
Furthermore, AdminDroid presents remarkable features which will leave you amazed! They are,
- AdminDroid Alerting
- Quick Scheduling
- Granular Access Delegation
- Advanced Customization Filters
Don’t hesitate! Experience the power of Microsoft 365 reporting firsthand by downloading AdminDroid now, for an amazing hands-on experience.
In summary, audit Microsoft 365 admin activity for a secure and well-managed environment. Furthermore, to enhance security posture, Microsoft has started to roll-out Conditional Access policies that require MFA for admins to access admin portals. We trust this blog has simplified the Microsoft 365 admin auditing process for you. Feel free to share any concerns or questions in the comments section. Thank you for reading!