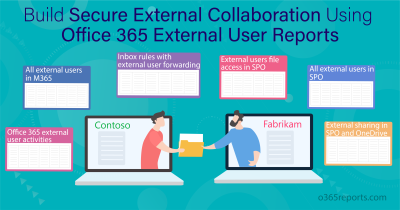
As we all know, external collaboration is part of various Microsoft workloads such as Microsoft 365 Groups, SharePoint, OneDrive, Teams, etc. each serving a distinguished mode of communication with external users. However, it’s crucial to maintain a balance between effective communication, sharing information, and collaboration without slipping into miscommunication, over-sharing, or misuse of data by external users. Therefore, having the right settings in place is important. If not properly configured, these permissions could potentially lead to significant data exploitation. Microsoft already has a handful of settings that you may overlook for securing guest sharing in Microsoft 365.
We have brought together some of the most recommended guest-sharing settings that you can configure for a safer external collaboration in Microsoft 365.
Guest Sharing in Microsoft 365
Some of the configurations require the guests to have an account in Microsoft 365, To ensure that guests are included in your directory, you can rely on the user reports in the Microsoft 365 admin center. When you share files and folders with users outside your organization, it is important to secure them using different combinations of the available sharing settings in Microsoft 365 such as the SharePoint and OneDrive integration with Microsoft Entra B2B Preview.
How to Secure Guest Sharing in Microsoft 365?
While most of these features are already known to you, many people are unsure of when to use which settings. We’ll provide you with guidance on using these features across various scenarios in Microsoft 365 to secure guest sharing efficiently.
Sharing settings to secure guest sharing are dispersed within various admin centers across Microsoft 365. Let’s bring them together! We have categorized them based on the locations they are in such as Microsoft Entra, Microsoft 365, Teams, and SharePoint admin centers.
Microsoft 365 Guest Sharing Settings – When to Use What?
Explore the various scenarios and the respective guest access settings to be utilized across Microsoft 365.
Microsoft Entra ID
1. To avoid attackers gaining access to guest accounts by exploiting their credentials:
Use: MFA for guest users with Conditional access
MFA acts as an additional layer of security, requiring guests to verify their identity using a second-factor authentication, such as a code sent to their phone or an approval from the authentication app. Without multifactor authentication (MFA), anyone with the account credentials could easily access your sensitive data.
To set up MFA for guests in Microsoft Entra ID, choose “Guest or external users” in the user selection, and set up a conditional access policy for B2B collaboration guest and member users. Then, select the ‘Require MFA’ check box and enable the policy. Now, guests must complete multifactor authentication before gaining access to shared content, sites, or teams.
2. To require guests to accept your terms of policy before getting access:
Use: Microsoft Entra terms of use policies for guests
To ensure the confidentiality of your organization’s information when working with external guests, you can leverage a Terms of Use agreement in Microsoft Entra ID. This document, accessible as a PDF file, outlines specific conditions and limitations for guests accessing shared files and resources. When someone tries to access a shared file or website for the first time, they’ll see the terms of use displayed. To set this up, begin by creating a document using Word or a similar program. Save the document as a .pdf file and upload it to Microsoft Entra ID. After this, any guest attempting to access content, such as a team or a site within your organization will need to accept these terms of use before proceeding.
3. For regular permission reviews & to ensure only authorized individuals have access:
Use: Microsoft Entra access reviews
Using Microsoft Entra ID’s access reviews, you can automate regular checks on user access to different teams and groups. Focusing on access reviews ensures that guests don’t maintain access to sensitive company information longer than needed. With access reviews, you can also identify inactive guest accounts that have not been actively used to sign into Microsoft Entra ID.
4. To grant temporary and controlled access to external users:
Use: Microsoft Entra access packages
Using access package to onboard external users in Microsoft Entra ID ensures they receive only the necessary permissions for a defined period. Through an approval workflow, guests can request access to specific resources such as teams, SharePoint sites, applications, and Microsoft Entra roles via an access package link. This approach minimizes security risks by automatically removing access when no longer needed while reducing IT administrative workload.
5. For automatically logging out guest users after a defined period of inactivity:
Use: Session management with Conditional access policy
Regular guest authentication can help prevent unauthorized access to your organization’s data, especially if a guest’s device lacks security measures. Microsoft Entra ID allows you to set up conditional access policies, such as idle session timeouts, specifically designed for guests, enhancing overall security measures.
6. To enable partners manage their own user access and reduce IT burdens:
Use: B2B extranet with managed guests
Enabling Entra ID entitlement management facilitates the creation of a B2B extranet, facilitating secure collaboration with partner organizations utilizing Entra ID. This system empowers users to self-register for extranet sites and teams while accessing permissions through an approval process.
Microsoft Purview Compliance Portal
1. To provide controlled and time-bound access to sensitive content for guests:
Use: Sensitive labels in Microsoft 365
When collaborating on projects that involve sharing sensitive data with external partners or contractors, Microsoft 365 sensitivity labels ensure that the shared information maintains its security and protection. Sensitivity labels serve as watermarks for sensitive documents, ensuring they maintain protection whether within or outside your organization. These labels categorize documents based on preset security policies, employing encryption, and content identification. Once sensitivity labels have been applied, admins can ensure constant protection, regardless of the document’s location.
2. For precise identification of sensitive data when working with guests:
Use: Custom sensitive information types
Microsoft Purview offers over 100 pre-built “sensitive information types” (SITs) like social security numbers and more. You can also create custom SITs for your specific needs, like highly confidential project information. A custom sensitive information type is a user-defined data classification. These SITs identify and protect sensitive information that is not covered by pre-built SITs and can then be used to automatically apply sensitivity labels.
3. To prevent unauthorized sharing of sensitive content to guests:
Use: Data Loss Prevention
Microsoft Purview’s Data Loss Prevention (DLP) feature enables the prevention of unauthorized sharing of sensitive content to guests. It allows actions to be taken based on a file’s sensitivity, such as the presence of social security numbers or credit card numbers, etc. DLP is one among the various security best practices for sharing files & folders with unauthenticated users.
SharePoint Admin Center
1. If you want to restrict guests accessing data through unmanaged devices:
Use: Access control to restrict unmanaged devices access
Devices that aren’t hybrid AD joined or compliant with Intune are classified as unmanaged. To balance productivity and security, restricting access allows users on these devices to use browsers. However, they won’t be able to download, print, sync files, or access content through various apps, including Microsoft Office desktop apps. You can block unmanaged device access in the SharePoint admin center and customize it using conditional access policies.
2. If you want to restrict guests sharing information to untrusted domains:
Use: Domain sharing restriction in SharePoint
You can use domain restrictions in SharePoint Online to identify the domains you trust and add them to your SharePoint domain whitelist. Domains not on the whitelist will be restricted from external sharing. For instance, if you add gmail.com to the list of blocked domains, any attempts to share externally with a gmail.com account will result in an error message.
3. If you want to disable guests accessing resources using Anyone links:
Use: Turn off anyone links
You have the disable Anyone links option to ensure that only authenticated users within your organization can access and share content. This setting can be adjusted at both the organization-wide and site-specific levels.
4. If you want to allow sharing with certain guests but block others:
Use: Allow/block list policy for B2B users
Microsoft Entra ID allows you to control invitations to specific organizations for secure B2B collaboration through allowlist. This helps to manage external access and improve security within your organization. Here’s how allow/block policies in Microsoft Entra ID work:
Allowlist:
- Limits invitations to users from specific organizations.
- Offers the highest level of control over B2B collaboration.
- Useful for scenarios where you only collaborate with a small number of trusted partners.
Blocklist:
- Prevents invitations to users from specific organizations.
- Useful for blocking collaborations with unwanted or potentially risky organizations.
- Offers less restrictive control than an allowlist
5. If you allow only certain people in your org to collaborate with guests:
Use: Limit sharing to specified security groups
If you want only a certain trusted user, while preventing all others from collaborating with external users, you should restrict access by security groups. When enabled, only designated security group members can access their OneDrive accounts. Users outside of this security group won’t be able to access their own OneDrive or the stuff shared within it even if they are licensed for OneDrive.
Teams Admin Center
To control guest sharing in Microsoft Teams:
Use: Manage Microsoft 365 guest access, calling, and messaging in Teams
The control of external collaboration in Microsoft Teams entails a series of settings managed within the Teams admin center, specifically under the “Guest access” section.
- Guest Calling Options: Controls whether guests can engage in peer-to-peer calls within Teams.
- Guest Meeting Settings: Determines if guests can utilize video during calls and meetings, screen sharing options.
- Guest Messaging Settings: These settings govern messaging capabilities for guests in Teams.
To manage the above settings effectively, you can rely on the group membership report in Microsoft 365 and list out the guest users in your organization.
You can also limit external user access by blocking some important settings across Microsoft 365. I hope that this blog has guided you with best practices to secure guest sharing. Thanks for reading. Feel free to reach us in the comment section for any assistance.