In the dynamic realm of Microsoft 365, your organization’s first line of defense lies in the hands of your key administrators. The Exchange admin, SharePoint admin, and numerous other admins have a lot of control over your email systems, collaborative platforms, and the heart of your Microsoft 365 environment. But what if they were to fall victim to a cunning brute force or phishing attack? The stakes couldn’t be higher!
The new Conditional Access policy for Microsoft 365 Admin Portals enables administrators to exert finer control over who can access Microsoft administrative portals (e.g., Entra ID, Microsoft 365 admin center, and Exchange admin center) by mandating multi-factor authentication (MFA) for interactive access.
In this blog, we’ll delve into why CA policies are important and how to use them to protect your Microsoft 365 admin portals. So, fasten your digital armor, and dive into the world of Conditional Access policies to access M365 Admin Portals, where safety meets simplicity.
Conditional Access Policy for Microsoft 365 Admin Portals Cloud App
Microsoft Entra Conditional Access uses specified signals for informed decisions. Think of these policies as if-then statements: if you want to access, certain conditions must be met. With the addition of the Microsoft 365 admin portals app, admins can create a CA policy targeting admin portals and require multi-factor authentication for login. This added security layer ensures authorized access, safeguarding your organization’s data and resources. Additionally, admins can use PowerShell to export CA policies and verify their configurations, ensuring the effectiveness of the CA policy.
NOTE: Conditional Access policies require either a Microsoft Enterprise ID P1/P2 license or a Microsoft 365 Business Premium license to use them.
Why Securing Access to Microsoft 365 Admin Portals is Important?
There are several compelling reasons to establish a Conditional Access (CA) policy for granting access to the Microsoft 365 Admin Portals cloud app. They are,
- Enhanced Security: Microsoft 365 admin portals are vital entry points that must be safeguarded. Implementing a CA policy mandating MFA combines various MFA strengths with a password (e.g., smartphone or hardware token), significantly bolstering security against unauthorized access.
- Protection Against Credential Theft: Passwords can be compromised through various means, including phishing attacks, brute-force attacks, or password reuse. Configuring CA policy that requires MFA helps safeguard against these cyber threats because even if an attacker manages to steal a password, they won’t have the second factor required for access.
- Privileged Access: Administrators often have access to highly sensitive systems and data. By requiring MFA through a Conditional Access policy, you can protect Microsoft 365 admin accounts, ensuring only authorized personnel can access critical resources and make configuration changes. This approach effectively reduces the risk of unauthorized access and data breaches.
- Account Recovery: MFA can assist with account recovery in the event of a forgotten password or a compromised account. Microsoft 365 admins can use their second factor to regain access to their accounts securely, enhancing security and workflow efficiently.
So, without further delay, let’s look at how we can create a conditional access policy that requires MFA for admins accessing Microsoft admin portals.
Create a Conditional Access Policy to Access Microsoft 365 Admin Portals
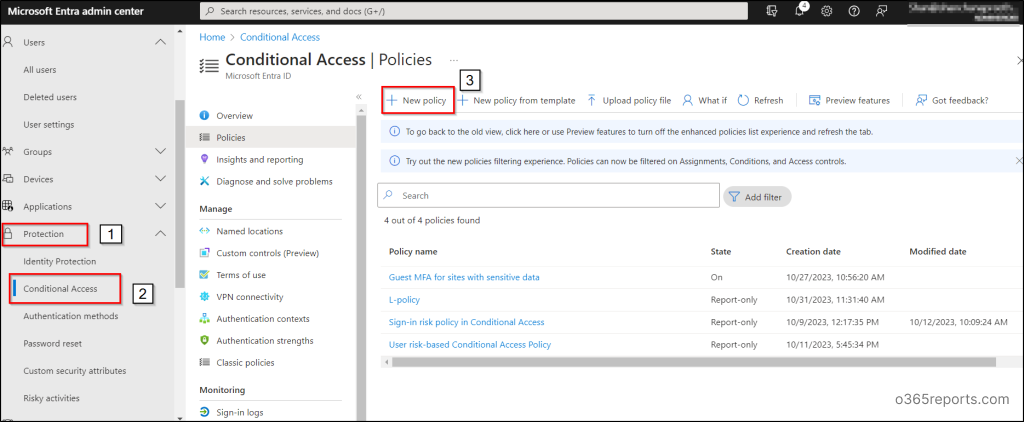
To create a Conditional Access Policy in the Microsoft Entra admin center with at least the Conditional Access Administrator role, follow these steps:
1. Navigate through the path below to configure Conditional Access policy to access the Microsoft 365 Admin Portals app.
Microsoft Entra admin center 🡢 Identity 🡢 Protection 🡢 Conditional Access 🡢 Create new policy
2. Choose a descriptive name for your Conditional Access (CA) policy, in line with Microsoft’s recommendation to use meaningful names for policies.
3. In the Assignments section, select “Users” to define who the policy will apply to.
4. In the “Include” section, click “Select users and groups” and add from the following built-in roles as per your organizational requirements.
- Global Administrator
- Application Administrator
- Authentication Administrator
- Billing Administrator
- Cloud Application Administrator
- Conditional Access Administrator
- Exchange Administrator
- Helpdesk Administrator
- Password Administrator
- Privileged Authentication Administrator
- Privileged Role Administrator
- Security Administrator
- SharePoint Administrator
- User Administrator
5. In the “Exclude” section, select “Users and groups” and remove one of the emergency access accounts from CA policy as a security best practice.
6. Under Target resources, choose “Cloud apps.”
7. In the “Include” section, select “Select apps” and search for and select “Microsoft Admin Portals.”
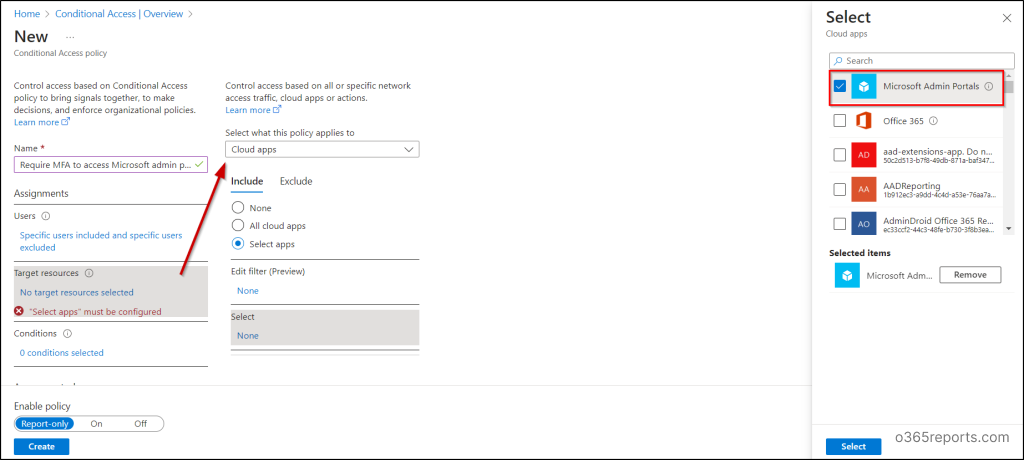
When you choose the Microsoft Admin Portals cloud app, the Conditional Access (CA) policy applies to tokens issued for application IDs related to several administrative portals. These currently include:
- Azure portal
- Exchange admin center
- Microsoft 365 admin center
- Microsoft 365 Defender portal
- Microsoft Entra admin center
- Microsoft Intune admin center
- Microsoft Purview compliance portal
It’s worth noting that Microsoft is continually expanding this list, so additional admin portals may be subject to the CA policy in the future. This flexibility ensures that your organization can maintain robust security measures across a wide range of administrative interfaces as the Microsoft ecosystem evolves.
NOTE: The Microsoft Admin Portals cloud app is for interactive logins to admin portals, not for resources like Microsoft Graph or Azure Resource Manager APIs. To secure those resources, the Microsoft Azure Management app is used. This approach lets admins gradually adopt MFA without disrupting automation via APIs and PowerShell.
8. Next, under Access controls, choose “Grant access.”
9. For “Require authentication strength,” select “multi-factor authentication” and then click “Select.”
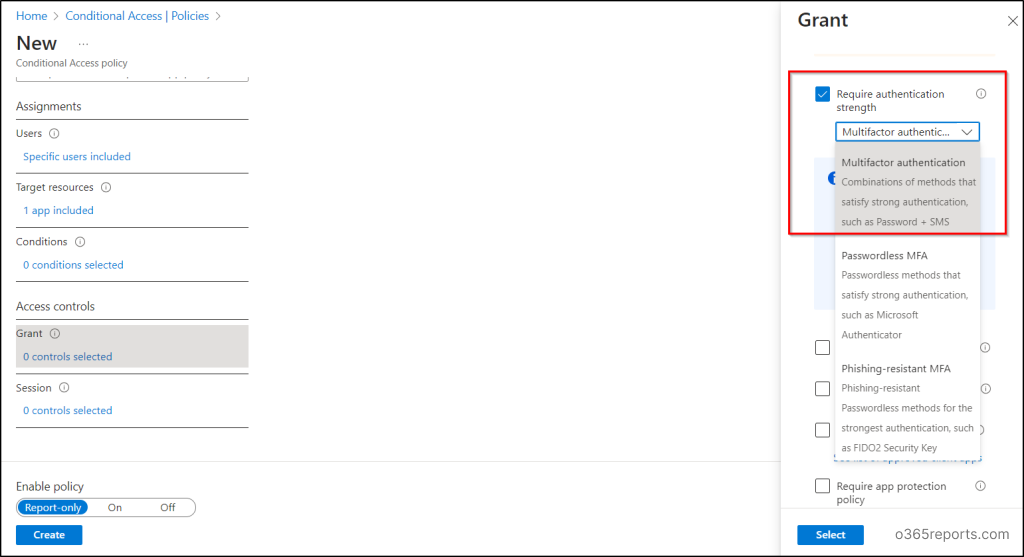
10. Review your settings and set the Enable policy to “Report-only mode”.
11. Finally, click “Create” to create and enable your Conditional Access policy.
User Exclusions in CA Policy
Microsoft provides specific recommendations for exclusions in Conditional Access policies, recognizing their robust enforcement capabilities.
- It’s advised to exclude break-glass or emergency access accounts to prevent tenant-wide lockout. These accounts serve as a safety net in scenarios where administrators are locked out of the tenant, allowing them to log in and take recovery measures.
- Excluding service accounts, like Microsoft Entra Connect Sync, is advisable. Service accounts can’t perform MFA programmatically and are typically used by backend services for programmatic access. Conditional Access policies for users won’t affect service principals, ensuring smooth backend service operation. To target service principals, use CA policies for workload identities. If your organization uses these accounts in scripts, consider replacing them with managed identities or temporarily removing them from the baseline policy.
Things to be Considered
- Conditional Access policies are designed to work with built-in roles and do not apply to other role types, such as administrative units based roles or custom roles.
- Assess the impact of the Conditional Access policy within your organization by initially enabling the ‘Report-only’ mode. Once it demonstrates the desired outcomes, administrators can transition the ‘Enable policy’ setting from ‘Report-only’ to ‘On’.
Microsoft is set to implement an auto-rollout of Conditional Access policies in November 2023, as per their latest update on the Microsoft 365 roadmap. This initiative aims to automatically safeguard customers by applying managed Conditional Access policies to eligible Microsoft tenants.The specific policies to be enforced include Multi-Factor Authentication (MFA) for Admin portals, per-user MFA, and MFA for sign-ins that are considered as high-risks. However, to boost your organization’s security without delay, you can choose to activate these policies yourself right now, instead of waiting for the automatic rollout.
So far, we’ve looked at creating a CA policy to make sure admins use MFA for accessing Microsoft 365 Admin Portals. Beyond just configuring security measures like multi-factor authentication (MFA), it is imperative for administrators to gain visibility into its effectiveness and monitor user activities. Simply configuring it isn’t enough. To strengthen your MFA strategy in M365, it’s essential to have clear visibility and oversight of all MFA-related activities.
Note: Along with implementing CA policies, follow these top Entra ID secure score recommendations to boost up your organization’s security.
Thus, AdminDroid Microsoft 365 Reporter comes to your aid, helping you monitor MFA activities and improve your organization’s security posture.
Monitor MFA Activities Effectively with AdminDroid Reports!
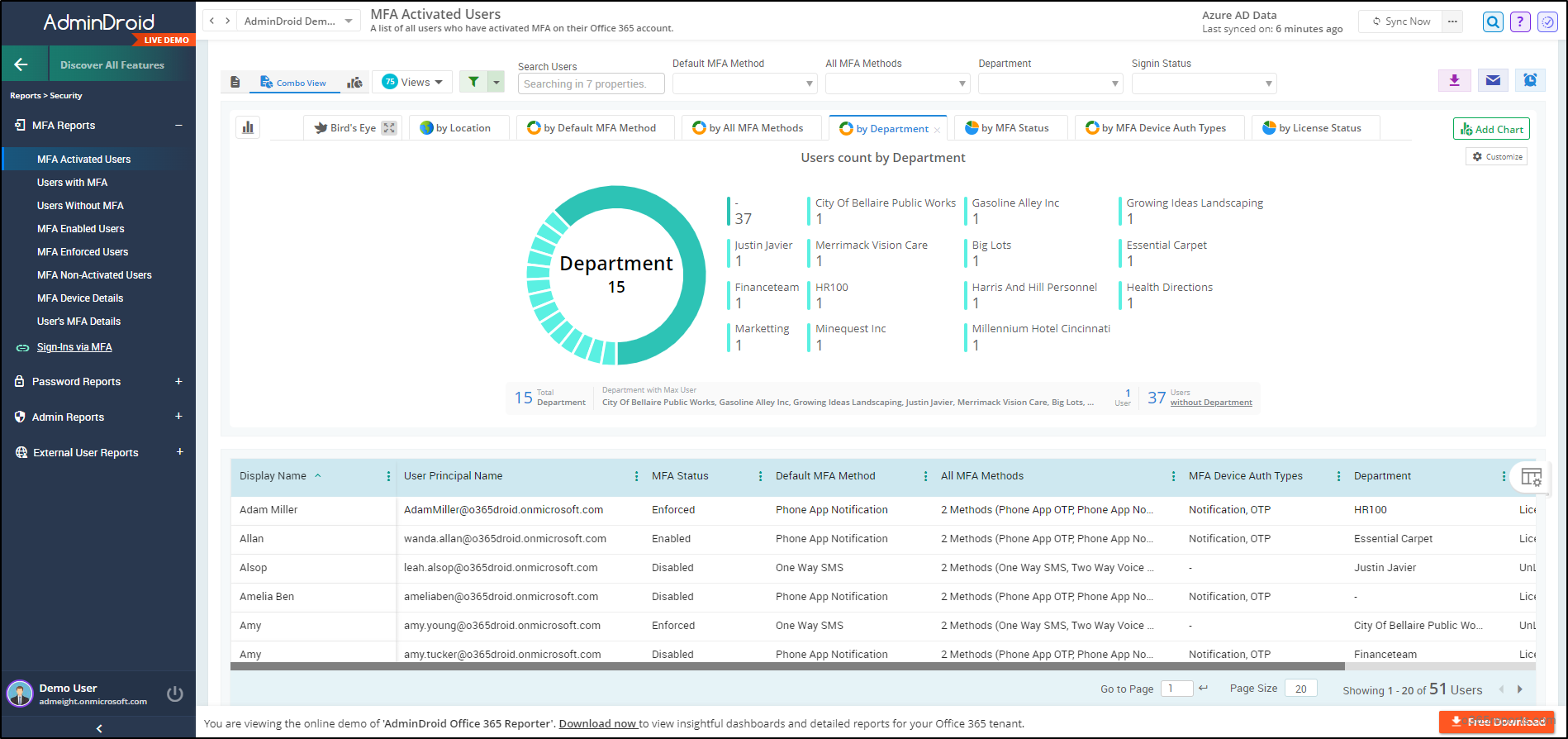
AdminDroid ‘s MFA reports serve as a strategic lens, offering a comprehensive view of your organization’s MFA landscape, ensuring thorough security coverage. The MFA reports include:
- MFA activated/non-activated users – Discover the Microsoft 365 users who have activated/not activated MFA within the organization.
- Users with/without MFA – View the list of users with/without MFA enabled or enforced.
- MFA-Enabled Users – Utilize this report to identify users who haven’t completed MFA setup and ensure MFA enforcement for them as required.
- MFA-Enforced Users – Analyze this report to identify users who have completed their MFA configuration.
- MFA Device Details – Retrieve the list of devices used by users for MFA configuration.
- Users’ MFA Configuration Details – Find the MFA details of the Microsoft 365 users along with the properties.
- Admins without MFA – Identify Microsoft 365 administrators who haven’t implemented multi-factor authentication.
Each report contributes to a holistic understanding, empowering admins to proactively manage and secure the MFA environment.
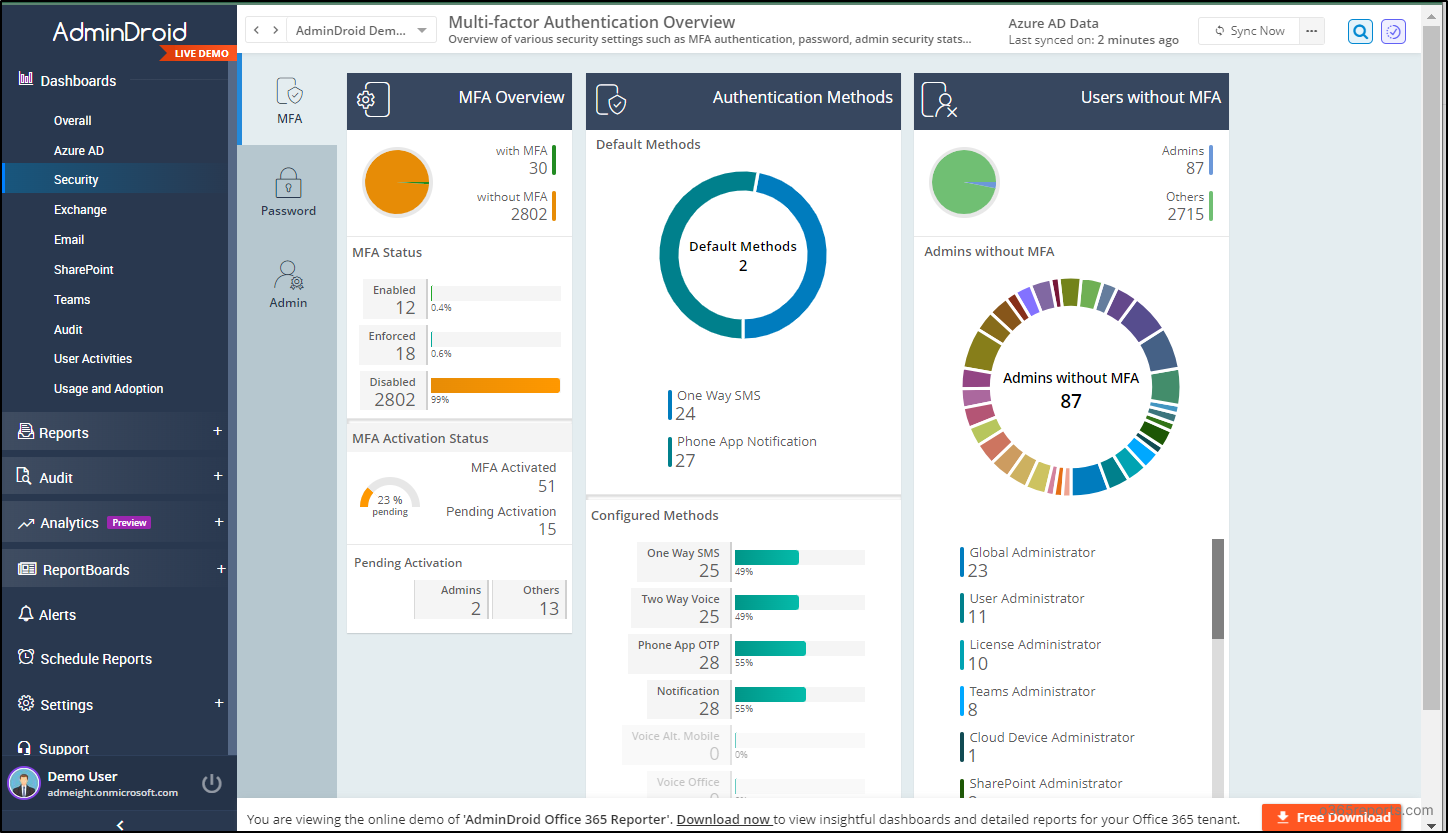
In addition, AdminDroid’s Free Azure AD reporting tool offers over 120+ insightful reports. It allows you to track Microsoft 365 user login activities, monitor subscription usage, get a concise breakdown of group members’ information, track password changes, and stay informed about license expiration & changes. Moreover, AdminDroid Azure AD dashboards have a dedicated MFA dashboard that offers a panoramic view of MFA authentication, passwords, admin security stats, etc.
AdminDroid goes beyond the confines of Microsoft 365 MFA reporting and Azure AD management, offering an extensive solution with 1800+ dedicated reports and 30+ visually appealing dashboards. Explore insights across various Microsoft services such as Exchange Online, MS Teams, SharePoint Online, OneDrive, Viva Engage, Power BI, and Stream.
AdminDroid doesn’t stop at reporting – it offers a spectrum of spectacular features for Microsoft 365 administration. With quick alerting, granular access delegation, enhanced report scheduling, and advanced customization filters, AdminDroid elevates your administrative capabilities.
Don’t delay any further! Download AdminDroid now and start a 15-day free trial to unlock the full potential of Microsoft 365 reporting and auditing.
Final Takeaway
In conclusion, by configuring a Conditional Access policy for Microsoft 365 Admin Portals, you can grant access to authorized administrators while keeping unauthorized intruders at bay. Additionally, features like device-based Conditional Access policies and session timeouts for the Entra portal provide an extra layer of security to your access controls. To further protect admin accounts, consider implementing regular audits of Microsoft 365 admin activities. This comprehensive approach ensures the protection of your critical resources and data, thereby enhancing your overall Microsoft 365 security.
Hope this blog has helped you configure the Conditional Access policy for Microsoft 365 Admin Portals. If you have questions or need more information, please feel free to ask in the comments. Thank you for reading!