Nowadays, security is paramount and multifactor authentication (MFA) stands as a critical line of defense in protecting sensitive information within Microsoft 365 environments. As organizations increasingly adopt to configure MFA, it becomes essential for administrators to monitor the authentication methods registered by users. Understanding the types of MFA methods in use, ensuring they are appropriately configured are key steps in maintaining a robust security posture.
To track user registration details for authentication methods, go to the Microsoft Entra admin center and navigate to Protection > Authentication > User registration details. Please note that this report does not include filtering options for admins or licensed users and may time out or fail when downloading for very large tenants.
To simplify this process, we have developed a PowerShell script by analyzing all the challenges and use cases. This script will help you get users with registered authentication methods and system-preferred MFA details.
Download Script: GetUsersRegisteredAuthenticationMethodsDetail.ps1
Script Highlights:
- This script exports registered authentication methods for all users.
- Allows to get users with system preferred MFA enabled/disabled details.
- It specifically identifies registered authentication methods for admins alone.
- Tracks MFA authentication registration method for licensed users only.
- Retrieves users with no registered authentication method.
- Automatically installs the module Microsoft Graph with your confirmation.
- The script can be executed with an MFA-enabled account too.
- Exports report results as a CSV file.
- The script is schedular-friendly, making it easy to automate.
- It supports certificate-based authentication (CBA) too.
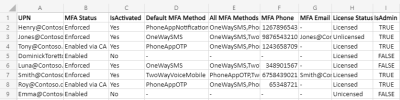
Sample Output:
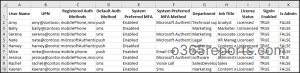
The script analyzes and exports registered MFA authentication methods for all users with the following attributes:
- User Name
- UPN
- Registered Auth Methods
- Default Auth Method
- System Preferred MFA Status
- System Preferred MFA Method
- Department
- Job Title
- License Status
- Sign-in Status
- Is Admin
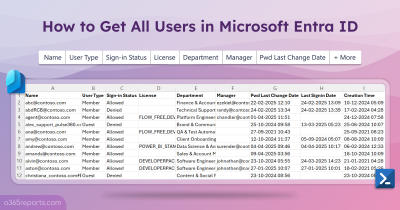
The exported registered authentication methods in Microsoft 365 looks like the screenshot below.
Users’ Registered Authentication Methods Details Using PowerShell – Script Execution Methods
- Download the script.
- Start the Windows PowerShell
- Select any of the methods provided to execute the script.
Method 1: You can run the script with MFA and non-MFA accounts.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 |
The above example lets you export registered authentication methods for sign-in enabled users into a CSV file.
Method 2: Run the script using certificate-based authentication (CBA).
When you want to run the script unattended, you can choose this method. To use certificates, you must register the app in Microsoft Entra which helps you connect to MS Graph using certificate. Depending on your requirements, you can create a self-signed certificate.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> |
Note – The method is schedular-friendly. You can schedule the script using Task schedular or Azure Automation.
Get the Most Out of “Users Registered Authentication Methods Detail Report”
- Export M365 Users with Registered Authentication Methods and System-Preferred MFA Details
- Identify Registered Authentication Methods for Admins
- Find MFA Authentication Registration Method for Licensed Users
- Get Users with At least One Registered Authentication Method
- Track Users with No Authentication Method Registration
- Analyze Who Registered System Preferred MFA
- Check Users Without System Preferred MFA
Export M365 Users with Registered Authentication Methods and System-Preferred MFA Details
Maintaining strong authentication methods is crucial for safeguarding your organization’s data and to prevent MFA fatigue attacks and SIM swapping attacks. If any weak authentication methods are identified, the IT team can quickly remove the less secure phone-based MFA options for those users.
To export the users registered authentication methods and system-preferred MFA details in Microsoft 365, run the following.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 |
By analyzing this report, organizations can export the MFA status and registered authentication methods in the organization.
Identify Registered Authentication Methods for Admins
Admin accounts hold high privileges, making it essential for registered authentication methods to be more reliable and secure. To export all Microsoft 365 admins and their registered authentication methods in Microsoft 365, run the script specifying –AdminsOnly switch.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -AdminsOnly |
The above example exclusively exports all the MFA authentication methods registered by the admins.
Even when admin accounts are configured with system-preferred MFA, they can still select less secure authentication methods during sign-in. To prevent this, you can reset MFA for admin accounts to remove less secure methods, like Phone authentication (SMS and Voice calls).
Find MFA Authentication Registration Method for Licensed Users
Licensed users typically have more sensitive roles and permissions, so ensuring their MFA registration methods are properly configured is crucial. It can also help defend against phishing attacks and unauthorized access.
Execute the script including –LicensedUsersOnly param to track registered authentication methods for licensed users.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -LicensedUsersOnly |
With this report, you can identify MFA enabled licensed users and their registered authentication methods.
Get Users with At least One Registered Authentication Method
Knowing users with at least one registered authentication method is essential to ensure they can securely access services and recover accounts if needed. View the list of users with registered authentication method(s) using –RegisteredUsersOnly switch.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -RegisteredUsersOnly |
The exported report will contain users with registered MFA authentication methods like Phone authentication, FIDO2, Windows Hello for Business, and Microsoft Authenticator app. Additionally, you can identify users’ MFA deployment source, whether it is configured via Conditional Access policy, security defaults, or per-user MFA. If the MFA is configured via per-user MFA, you can plan to migrate to per-user MFA to Conditional Access MFA for enhanced security.
Track Users with No Authentication Method Registration
Users with no authentication method are more susceptible to unauthorized access, as they lack an additional layer of security beyond just their password. To specifically identify users with no authentication method registration, run the script along with –UserswithNoRegistration parameter.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -UserswithNoRegistration |
Additionally, Microsoft has initiated a registration campaign encouraging users to set up the Microsoft Authenticator app for more secure sign-ins.
To track admins without authentication method registration, run the below.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -UserswithNoRegistration -AdminsOnly |
By referring to this report, you can enable MFA for admins to secure their accounts.
Analyze Who Registered System Preferred MFA
System-preferred MFA methods ensure that users are authenticated using the most secure and verified methods, reducing the risk of impersonation or fraudulent access. Use –UsersWithSystemPreferredMFA switch to get the list of users who registered system preferred MFA in the organization.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 –UsersWithSystemPreferredMFA |
Preferred MFA methods can be integrated with conditional access policies in the organization. This integration allows organizations to enforce stronger authentication requirements based on the user’s location, device, or risk level.
Check Users Without System Preferred MFA
Users without system-preferred MFA settings might be using outdated authentication methods like SMS and Voice call, which could be more vulnerable to attacks. To identify users without system preferred MFA, run the script with –UsersWithoutSystemPreferredMFA switch.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -UsersWithoutSystemPreferredMFA |
To track the licensed users without the system preferred MFA, execute the following.
|
1 |
./GetUsersRegisteredAuthenticationMethodsDetail.ps1 -UsersWithoutSystemPreferredMFA -LicensedUsersOnly |
Knowing which users are not compliant helps IT teams quickly assess and respond to security incidents, as these users may be at higher risk.
Get Detailed MFA Reports with Registered Authentication Method using AdminDroid
Are you frustrated with the complexities of PowerShell scripts for detailed user registered authentication method in Microsoft 365? Say goodbye to the hassle of manual efforts! Meet AdminDroid’s Microsoft 365 reporting and auditing tool—a straightforward solution that delivers comprehensive detailed MFA reports with ease.
You can schedule these reports and send them to preferred email addresses. Additionally, you can apply filters on any columns to view only the required information. Some of the reports on MFA authentication methods are:
User MFA Status
- MFA registered users
- MFA non-registered users
- Users and their registered authentication methods
- MFA device details
- Users per-user MFA status (Enabled/Enforced/Disabled)
MFA Sign-in Auditing
- Organization Sign-Ins Count Based on Authentication Method
- User’s Sign-ins Count Based on Authentication Method
- MFA User Sign-Ins Verified via Text Message
- MFA User Sign-Ins Verified via Mobile App Notification
- MFA User Sign-Ins Verified via Mobile App Verification Code
- MFA User Sign-Ins Verified via Phone Call
- Sign-ins failed to pass the MFA challenge
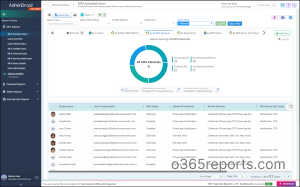
And that’s not all! AdminDroid goes above and beyond MFA reports by providing 1800+ pre-built reports and 30+ smart dashboards to know about your Office 365 environment at a glance. This tool provides a 15-day premium version trial with all functionalities like reporting, alerting, delegation, and compliance. Download and simplify your Microsoft 365 management with AdminDroid today!
I hope this blog is useful to users’ registered authentication methods in Microsoft 365. If you have any queries, reach us through the comment section.