With Microsoft 365’s powerful suite of tools like SharePoint, OneDrive, and Teams, users can easily share files and collaborate in multiple ways. While this flexibility is great for productivity, it can also cause mix-ups. In large organizations, it’s common for files to be shared more broadly than necessary. Sensitive documents might be accessible to entire departments or even external guests who no longer need access. ⚠️
This kind of oversharing creates serious risks, including data leaks, compliance violations, and reputational damage. Fortunately, oversharing can be greatly reduced with the right safeguards. 🛡️ In this blog, we’ll look at the key measures admins can use to keep sharing under control and prevent accidental exposure in Microsoft 365.
Before we explore the solutions, let’s first take a closer look at how oversharing happens and why it’s risky.
How Oversharing Happens in Microsoft 365?
Oversharing in Microsoft 365 can take many forms, often leading to unintended data exposure.
Common examples include:
- Sharing confidential files in public Teams channels.
- Using “Anyone with the link” settings that grant open access.
- Leaving guest accounts active long after a project ends.
- Assigning permissions to entire groups instead of specific individuals.
Regardless of intent, oversharing in Microsoft 365 increases the risk of security breaches and demands immediate action to protect your organization’s data.
Why Oversharing in Microsoft 365 Is Risky?
Oversharing in Microsoft 365 isn’t just a small slip-up. It can quickly turn into a chain of serious problems such as:
- Compliance violations, resulting in fines or legal issues.
- Reputational damage due to data leaks.
- Increased security vulnerabilities like phishing and attacks.
- Accidental changes or deletions of critical data.
When these issues combine, the damage can be far more costly than the initial oversharing incident. That’s why it’s essential to have preventive measures in place before things go wrong.
How to Prevent Oversharing in Microsoft 365?
There’s no single switch to stop oversharing in Microsoft 365 — it takes a combination of settings, policies, and ongoing monitoring. Thankfully, Microsoft 365 provides admins with a wide range of controls to manage how files and folders are shared.
Now, let’s look at the key configurations that help reduce the risk of files and folders being shared more widely than intended:
- Set restrictive defaults in SharePoint & OneDrive
- Organization-level Sharing Settings in SharePoint
- Configure Default File and Folder Link Settings
- Site-level Sharing Settings in SharePoint
- Restrict Unmanaged Access to SharePoint and OneDrive
- Configure Secure Guest Sharing
- Manage Guest User Expiration in SharePoint
- Configure External Sharing by Domain
- Restrict External Sharing to Security Groups
- Limit user access for secure collaboration
- Enforce Data protection & compliance
Set Restrictive Defaults in SharePoint & OneDrive
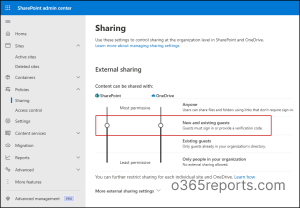
Start with the most restrictive SharePoint sharing settings by default and loosen them only when needed. This ensures new files, folders, and sites aren’t accidentally exposed to more people than intended, reducing the risk of internal oversharing before it even starts. By default, Microsoft 365 allows sharing with “Anyone” (anonymous access links) unless your organization’s admin has changed it.
You can control the default sharing level for both SharePoint and OneDrive directly from the SharePoint admin center. To do this,
- Go to the SharePoint admin center.
- Navigate to Policies → Sharing.
- Under External sharing, select the most restrictive option that fits your organization’s needs.
The recommended choice for most businesses is “New and existing guests.” This option allows sharing only with invited guests. It requires guests to sign in with their work or school account if their organization uses Microsoft 365.
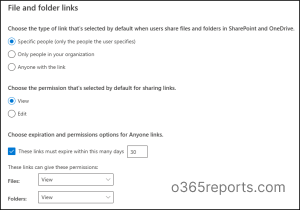
2. Configure Default File and Folder Link Settings
The File and folder link settings in the SharePoint admin center control the default link type users get when sharing files and folders in SharePoint and OneDrive. This setting covers everything related to links like the link types, permissions, expiration dates, and more.
- Set default sharing to “Specific people” – Ensures content is accessible only to explicitly named individuals.
- Set default link permission to “View” – Safer option to prevent unintended edits. Use “Edit” only when recipients must modify content.
- Enable link expiration – Recommended to set links to expire within 7–30 days based on the sensitivity of the content.
3. Site-level Sharing Settings in SharePoint
Sometimes you may need to adjust sharing restrictions at the site level, especially for sites containing sensitive or regulated data:
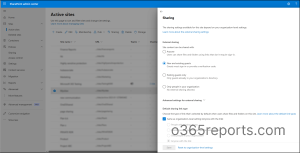
- Navigate to SharePoint admin center → Sites → Active Sites.
- Select the target site, then go to Settings → More sharing settings.
- Customize the sharing settings here to tighten or loosen access based on the sensitivity of the site’s content.
Limiting site-level sharing can prevent users from accidentally sharing sensitive site content beyond authorized users.
4. Restrict Unmanaged Access to SharePoint and OneDrive
Access control settings in SharePoint and OneDrive prevent oversharing in following ways:
- Unmanaged devices – Prevent access from devices that aren’t domain-joined or meeting security requirements.
- Idle session sign-out – End idle browser sessions to reduce unauthorized access risks.
- Network location – Allow sign-ins only from trusted IP ranges, ensuring access is limited to approved network locations.
- Apps that don’t use modern authentication – Block older Office versions (like Office 2010) and apps that can’t enforce device-based security.
- OneDrive access restriction – Allow only approved security groups to view or use specific OneDrive content.
More Ways to Control External Sharing & Guest Access in SharePoint
1. Configure Secure Guest Sharing
Enabling secure guest sharing in Microsoft 365 helps prevent oversharing and protect sensitive data when working with external users. Configuring guest access settings in Microsoft Entra, SharePoint, Teams, and Purview strikes the right balance between collaboration and security, reducing the risk of data misuse or unauthorized access.
2. Manage Guest User Expiration in SharePoint
Setting automatic guest account expiration ensures that external users lose access when they no longer need it. This avoids forgotten accounts lingering in your tenant and accidentally retaining access to sensitive files long after a project ends.
3. Configure External Sharing by Domain
Limiting external sharing to approved domains ensures your data can only be shared with verified organizations you trust. This block sharing with personal accounts or unknown companies that could misuse the information.
4. Restrict External Sharing to Security Groups
Limiting external sharing to security groups ensures that only authorized users can share files externally for collaboration. This control helps prevent accidental oversharing outside the organization and strengthens your overall OneDrive security.
💡 Tip: In addition to the above, follow best sharing link practices to maintain proper access and protect data security. Consider the purpose, audience, and content sensitivity, and regularly clean up unused or outdated links.
Limit User Access for Secure Collaboration
1. Apply Least Privilege to Limit Access
Implementing least privilege access in Entra ID reduces the risk of accidental or intentional data exposure. By ensuring users can only interact with files relevant to their roles, sensitive information remains contained within appropriate teams.
2. Limit File Sharing in SharePoint
Controlling file-sharing permissions for specific users is an effective way to prevent oversharing in SharePoint Online. You can disable users from sharing files in SharePoint through the admin center or by using PowerShell. This proactive approach strengthens data protection and keeps collaboration secure without compromising productivity.
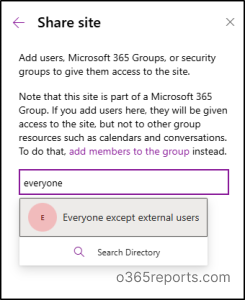
3. Restrict Permissions to Smaller Groups Instead Of “Everyone Except External Users”
The security group called “Everyone Except External Users” (EEUU) includes all your internal users. Many users tend to share content with this group because it’s convenient – just one group that automatically grants access to everyone inside the organization. Although this approach is quicker than adding individuals separately, it often leads to oversharing. As a result, hundreds or even thousands of people who don’t actually need access end up having it.
4. Control and Approve Guest Invitations with Azure B2B
Azure B2B invitation controls let you approve who can invite guests, customize invitation messages, and require approval before external users get access. This ensures only approved, legitimate partners or clients are onboarded — reducing the risk of strangers or unverified accounts accessing your resources.
5. Use Access Reviews to Clean Up Stale Guest Accounts
Guest accounts can accumulate over time, posing security risks if inactive. Setting up access reviews in Microsoft Entra ID lets admins regularly verify and revoke guest access to SharePoint, Teams, and other resources.
Enforce Data Protection & Compliance
1. Restrict Cross-Group Communication with Information Barriers
Information barriers in Microsoft 365 prevents communication and collaboration between specific groups in Microsoft 365. They ensure that users in separate business units or departments can’t accidentally share sensitive information. This is especially critical in regulated industries where strict separation is required, such as between finance and research teams.
2. Protect Shared Files with Sensitivity Labels and Encryption
You can apply sensitivity labels to classify and protect documents or emails. These labels can apply encryption, watermarks, and usage restrictions so that even if a file is shared externally, only authorized users can access it.
3. Prevent Sharing of Sensitive Information with DLP Policies
Data Loss Prevention (DLP) policies detect and block the sharing of sensitive data such as credit card numbers, personal IDs, or health records. This helps ensure compliance with data protection regulations by preventing sensitive data from being sent to unauthorized recipients.
4. Limit File Distribution by Blocking Downloads
You can apply the block download policy in SharePoint and OneDrive to specific files or libraries, allowing users to view the content in the browser without saving or sharing it further. This prevents uncontrolled distribution beyond the intended audience.
5. Address Oversharing Risks in Microsoft 365 Copilot
Microsoft 365 Copilot is increasingly used in organizations to draft reports, prepare documents, and simplify daily tasks. However, Copilot can generate content using organizational data from Microsoft 365 apps and services, there is a risk of unintentional data exposure or oversharing if it’s not managed properly.
To reduce these risks, Microsoft 365 provides built-in features available in E3+, SharePoint Advanced Management, and Purview to help prevent data oversharing through Copilot. The diagram below highlights key controls and their functions.
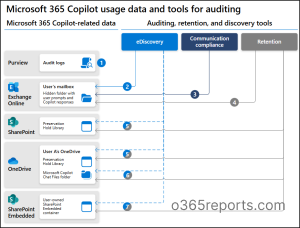
The Microsoft 365 Copilot Oversharing Deployment Blueprint provides a staged approach – Pilot, Deploy, and Operate to help administrators address oversharing risks during Copilot rollout.
Additionally, you can restrict access to Copilot using Conditional Access policies, so that only authorized and trusted users can interact with it, reducing the risk of accidental data exposure.
Ways to Monitor Sharing in Microsoft 365
After setting up preventive measures, it’s equally important to keep an eye on how sharing actually happens in your environment. Here are some effective ways to monitor sharing activities in Microsoft 365.
1. Generate SharePoint Online Sharing Reports
Built-in SharePoint Online sharing reports provide a valuable way to monitor and identify potential oversharing within your organization. These reports give insights into who has access to shared content, the types of sharing links created (such as anonymous or internal), and the extent of external sharing. With the help of these reports, admins can quickly spot excessive or unintended sharing, allowing timely action to revoke unnecessary permissions.
2. Run DAG Reports to Spot Overexposure
Microsoft’s Data Access Governance (DAG) reports help identify sites, files, or folders that are accessible to broad audiences like “Everyone” or large security groups. Regularly reviewing these reports helps close exposure gaps before they turn into oversharing incidents.
3. Audit SharePoint Online External Sharing
Auditing external sharing in SharePoint Online is essential to safeguard organizational data from unauthorized access. Efficiently monitoring external sharing activities helps administrators identify who is sharing content outside the organization, what files or folders are being shared, and the type of sharing links used.
4. Track Teams File Sharing Activities
Monitoring file sharing in Microsoft Teams helps ensure that sensitive documents aren’t unintentionally exposed through chats or channels. Regular audits allow admins to track what files are being shared, with whom, and through which type of link, enabling quick action to remove risky access and maintain compliance.
By applying these controls, admins can drastically cut down the risk of both accidental and intentional oversharing — keeping sensitive information safe and ensuring compliance with internal and external policies.
We hope this blog has provided enough insights to help you identify, prevent, and manage oversharing in Microsoft 365. Thanks for reading! If you have any queries or need further guidance, feel free to drop them in the comments or reach out for more details.