Email serves as a fundamental communication tool, offering flexibility for handling emails and coordinating communication. Organizations often use email forwarding to avoid missing important conversations during users’ absence, to distribute workload, etc. This includes forwarding to external domains, which introduces potential risks. Unmonitored email forwarding can lead to data breaches, compliance issues, and other security concerns.
This blog will guide you to identify and block external email forwarding in Exchange Online using PowerShell. This approach is critically used in remediating compromised accounts by removing unauthorized forwarding rules, enhancing email monitoring and security.
Review and Block External Email Forwarding in Microsoft 365
External email forwarding can be identified by checking the mailbox’s forwarding configuration and inbox rules in the Exchange Admin Center. However, you need to navigate to each mailbox to verify all the external forwarding configuration details, which is difficult and time-consuming.
To streamline this process, we have crafted a PowerShell script, which generates reports on external email forwarding configuration for each mailbox and the inbox rules configured with external forwarding. Upon your confirmation, the external forwarding will be blocked, and the inbox rules will be disabled. Isn’t it outstanding? Disabling external forwarding in one go! No navigation and no time-consuming!
Note: By default, the script considers guest users, mail contacts, and mail users as external accounts only. You will have the option to exclude guest users before blocking external forwarding.
Script Highlights:
- The script automatically verifies and installs the Exchange PowerShell module (if not installed already) upon your confirmation.
- Exports the ‘External email forwarding report’ and ‘Inbox rules with external forwarding report’ into a CSV file.
- Blocks external forwarding configuration for all mailboxes upon confirmation.
- Disables all the inbox rules with external forwarding configuration upon confirmation.
- Allows to verify external email forwarding for specific mailboxes and blocks them.
- Allows users to modify the generated CSV report and provide it as input later to block the respective external forwarding configuration.
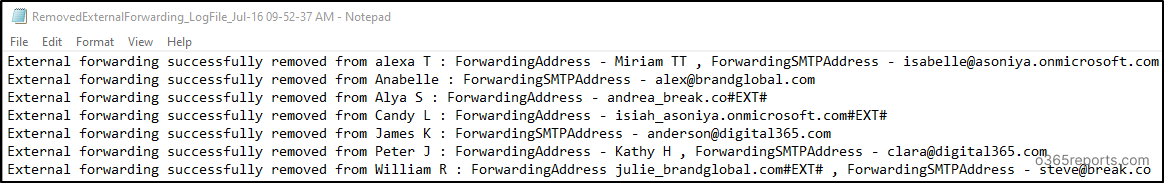
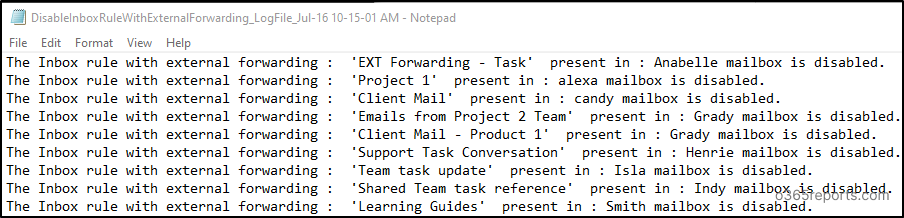
- Provides the detailed log file after removing the external forwarding configuration and disabling the inbox rules with external forwarding.
- The script can be executed with an MFA-enabled account too.
- The script supports Certificate-based authentication (CBA).
Download Script: BlockExternalEmailForwarding.ps1
Sample Output
The script analyses and exports two reports, ‘External email forwarding report’ and ‘Inbox rules with external forwarding report’.
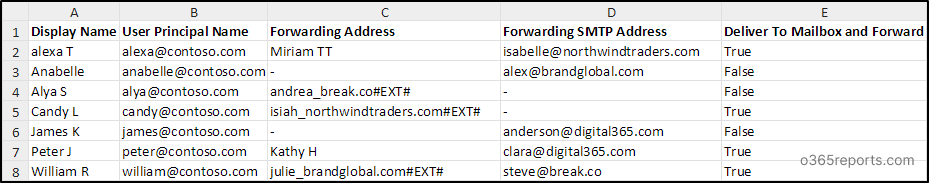
Export External Email Forwarding Configuration Report
The script exports this report with the following attributes:
- Display Name
- User Principal Name
- Forwarding Address
- Forwarding SMTP Address
- Deliver to Mailbox and Forward
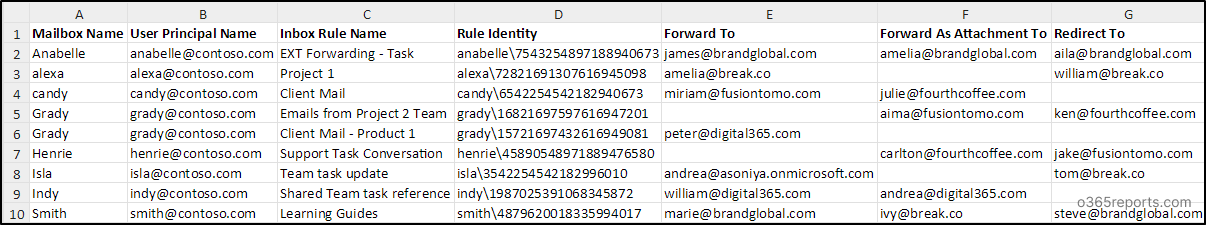
Export Inbox Rules with External Email Forwarding Configuration Report
The script exports this report with the following attributes:
- Mailbox Name
- User Principal Name
- Inbox Rule Name
- Rule Identity
- Forward To
- Forward As Attachment To
- Redirect To
Once the report is generated, you can enter ‘Y’ as the confirmation to block the external email forwarding and the inbox rules available in the output file as shown below.
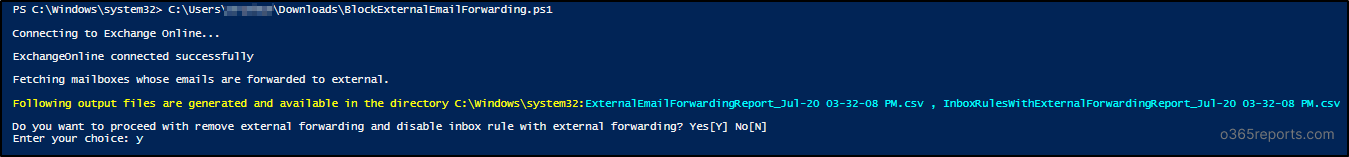
Once external forwarding is blocked, you will get a txt log file for both outputs as below.
Block External Email Forwarding in Microsoft 365 Using PowerShell – Script Execution Methods
- Download the script.
- Start the Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1: You can run the script with MFA and non-MFA accounts.
|
1 |
./BlockExternalEmailForwarding.ps1 |
The above example lets you export the email forwarding configuration report and the inbox rules with external forwarding report into a CSV file.
Method 2: You can explicitly pass credentials (username and password) and execute the script.
|
1 |
./BlockExternalEmailForwarding.ps1 -UserName <UPN> -Password <Password> |
The above method is applicable only for non-MFA admin accounts. You can disable MFA for a user via Conditional Access policy.
Method 3: You can also use certificate-based authentication to run the script. To do this, you must register the app in Azure AD and the app allows you to connect to EXO with certificate-based authentication.
|
1 |
./BlockExternalEmailForwarding.ps1 -Organization <Domain> -AppId <ClientId> -CertificateThumbPrint <CertThumbPrint> |
You can use either a certificate issued by a recognized certificate authority (CA) or create a self-signed SSL certificate.
Identify and Block External Email Forwarding Configuration in Exchange Online
Utilize the PowerShell script and identify all the external forwarding configurations and block them to have improved security. Explore more use cases you can achieve using the script below.
- Report and block all external forwarding configurations in Office 365
- Find and restrict external email forwarding for specific users
- Find and block external email forwarding excluding guest users
- Verify and block external email forwarding excluding internal guests
- Block suspicious external forwarding SMTP address (Input CSV)
- Disable inbox rules with external forwarding configuration
1. Report and Block all External Forwarding Configurations in Office 365
Identifying all the external email forwarding configuration, including inbox rules for all mailboxes is essential to detect suspicious forwarding and prevent data loss. You can verify the exported report, and you can decide whether to block all the external forwarding and disable all the inbox rules shown in the output based on your requirements.
Run the below cmdlet to identify and block external email forwarding for all mailboxes.
|
1 |
./BlockExternalEmailForwarding.ps1 |
Admins can get two reports, as said before, along with forwarding details. If you confirm to block all the configurations, the script will block all the email forwarding configurations in the output and send you the log file with blocked configuration details.
Note: If auto-email forwarding configuration is enabled, it might lead to severe security concerns if left unmonitored. You can block automatic email forwarding to external domain and protect your resources effectively.
2. Find and Restrict External Email Forwarding for Specific Users
If admins want to review the external forwarding configuration only for specific mailboxes, such as users working on a crucial project, they can prepare and include the CSV file with a list of required user addresses.
To find external email forwarding details for multiple users, you can include the CSV file path in the ‘MailboxNames’ parameter, as shown below.
|
1 |
./BlockExternalEmailForwarding.ps1 -MailboxNames <file path> |
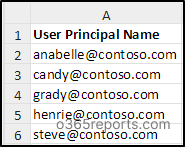
Replace the <file path> with the path of your created CSV file. You can also find external forwarding configuration in shared mailboxes and block them by including the desired mailbox address. Remember that the column name containing the users’ UPN should be ‘User Principal Name’ as shown in the image below.
Sample Input:
3. Find and Block External Email Forwarding Excluding Guest Users
Users can collaborate with external guest users for various purposes like project collaboration, etc. So, forwarding emails to them will be legitimate in these scenarios. If admins want to get the external forwarding configurations excluding the external guest users in their organization, you can use the ‘-ExcludeGuests’ parameter while running the script, as shown below.
|
1 |
./BlockExternalEmailForwarding.ps1 -ExcludeGuests |
The above script execution returns the emails forwarded to external users other than the guest users in the organization. It helps to easily narrow down to the desired result and block suspicious forwarding settings.
Note: Remember that the script considers the below as Guest users and excludes them from blocking.
- External Guests – Users added as guests (having #EXT in their SMTP address and authorizes using your organization credentials) and invited as guest users (using their own credentials to login) in the organization.
- Internal Guests – Your organizational users whose user type has changed to ‘Guest’ in Microsoft Entra ID.
4. Verify and Block External Email Forwarding Excluding Internal Guests
Before using B2B collaboration, organizations usually invite guest users and allow them to authorize by setting the internal credentials for them. They are added for working on projects, tasks, etc. Admins might want to exclude these internal guests in the external forwarding configuration report to drill down directly to desired results.
To achieve this, you can run the script by adding the ‘-ExcludeInternalGuests’ parameter.
|
1 |
./BlockExternalEmailForwarding.ps1 -ExcludeInternalGuests. |
Thus, forwarding to internal guest users (organizational users converted as guests) will be excluded from the output.
5. Block Suspicious External Forwarding SMTP Address (Input CSV)
As mentioned before, after executing the script, two reports will be generated: External email forwarding configuration report and Inbox rules with external forwarding report. After the reports are created, the script will prompt for confirmation to block all email forwarding settings displayed. If an admin identifies any forwarding settings that are legitimate and should not be blocked, they can choose ‘No’ when prompted.
Then, they should manually edit the output report by removing these legitimate entries from the output file. Once done, re-run the script with the ‘RemoveEmailForwardingFromCSV’ parameter.
|
1 |
./BlockExternalEmailForwarding.ps1 -RemoveEmailForwardingFromCSV <file path> |
Replace the file path with the path of the edited output file. So that instead of blocking all the forwarding settings, you can block only necessary configurations, excluding legitimate forwarding.
6. Disable Inbox Rules with External Forwarding Configurations
Like the above case, if admins don’t want to disable all the inbox rules shown in the output CSV file, admins can edit the file by removing inbox rules that shouldn’t be disabled in the organization. Then, run the script with the ‘-DisableInboxRuleFromCSV’ parameter as shown below.
|
1 |
./BlockExternalEmailForwarding.ps1 -DisableInboxRuleFromCSV <file path> |
Replace the <file path> with the edited output file path. After confirmation, all the inbox rules included in the CSV file will be disabled in your organization.
Efficiently Monitor External Email Forwarding in Exchange Online with AdminDroid
AdminDroid’s external forwarding configuration report lets you view all the external email configuration with precise details, such as external domain, username who configured forwarding, count of forwarding users, external recipients, and more.
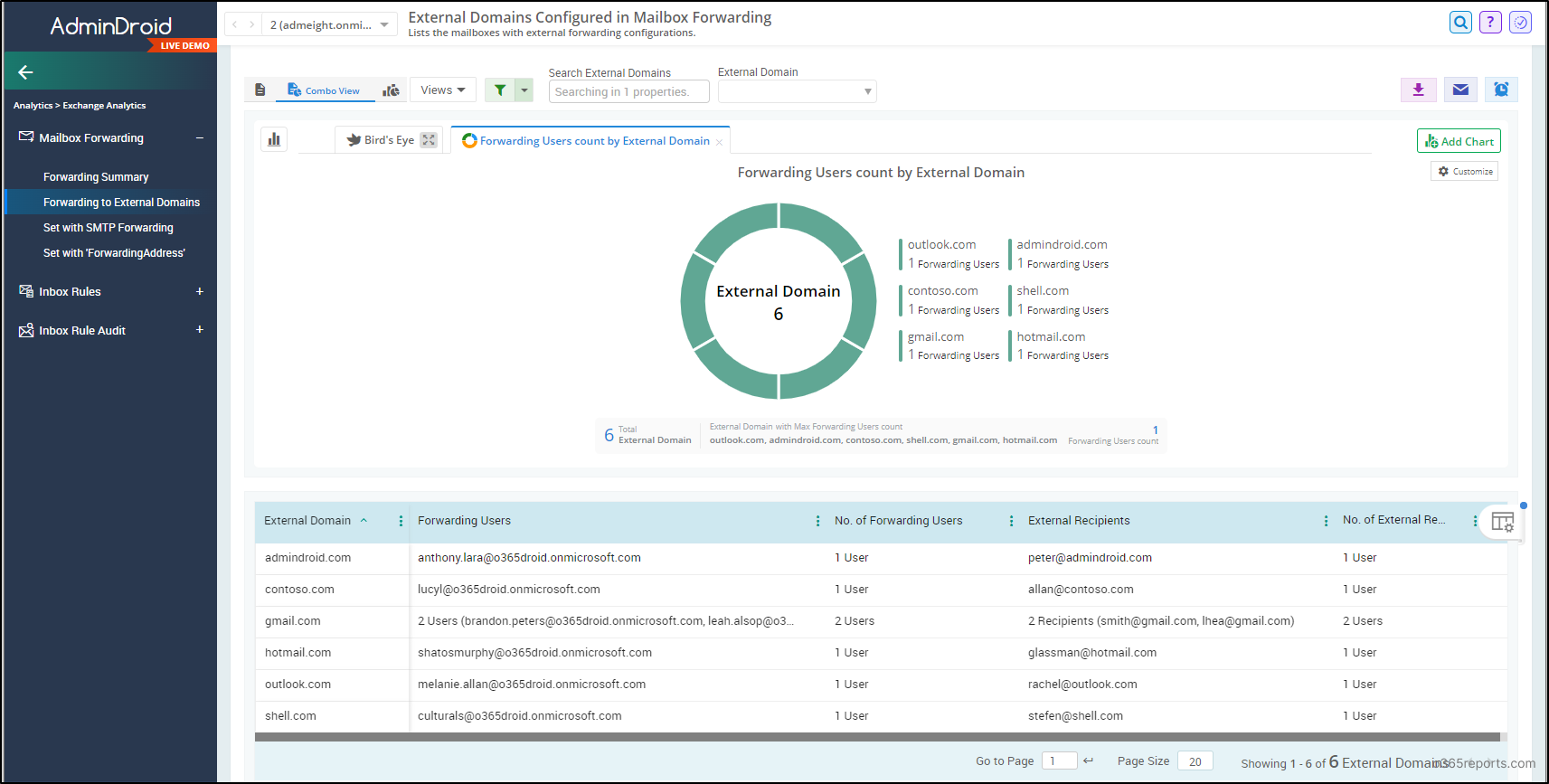
It helps to easily get the list of external domains to which emails are forwarded in your organization. Thus, you can easily decide and block suspicious domains effectively.
Moreover, the ‘mailbox with external forwarding inbox rules’ report displays all the inbox rules configured with external forwarding for each mailbox separately. It contains additional details like mailbox name, mailbox UPN, external address configured for forwarding as attachment to, forward to, redirect to, inbox rule condition details, rule processing status, and more. Also, you can get mailbox permission changes, user sign-in stats, and other crucial details.
Also, you can audit configuration changes made on external forwarding rules using the ‘Inbox Rules Configuration Changes with External Forwarding’ report. It helps to precisely identify any suspicious changes made to external forwarding inbox rules and revert them.
I hope this blog helps you to identify the external forwarding configuration and block unwanted settings in your configuration. Utilize the script to find suspicious forwarding easily. Drop your queries in the comment section. Happy securing!