Conditional Access policies play a vital role in securing your Microsoft 365 environment and are a key component of the zero-trust model. However, setting them up incorrectly can have serious consequences, like unintentionally compromising your entire Microsoft 365 security. It’s crucial to not only understand and configure these CA policies accurately but also to monitor them regularly. To make this easier, this blog introduces a PowerShell script to export Conditional Access policy reports. This helps secure your environment by providing CA policy insights and ensuring strong security.
How to View Conditional Access Policies in Microsoft 365?
There are two main ways to view CA policy configurations. They are,
Microsoft Entra admin center:
The “Policies” section of the Microsoft Entra Conditional Access page provides basic details like policy status, creation date, and last modified date for tracking CA policies. However, it doesn’t offer an export option and lacks customizable options. Additionally, checking each CA policy configuration requires clicking into each policy individually, which can be cumbersome and time-consuming.
PowerShell:
The “Get-MgBetaIdentityConditionalAccessPolicy” cmdlet allows you to retrieve Conditional Access policies within the organization. However, retrieving these policies isn’t as straightforward as it may seem. The cmdlet doesn’t directly list all configured properties, necessitating additional handling. Moreover, the returned values are in the form of object IDs, requiring further processing to present them as identifiable names. It can be challenging and require more time.
To address this, we introduce the ExportCApolicies PowerShell script designed to export Conditional Access policies into an Excel file. You can download the script from here and learn more about its functionality in the following sections.
Download Script: ExportCApolicies.ps1
Script Highlights
- The script generates 6 reports with 33 attributes for detailed CA policy analysis.
- The script exports all Conditional Access policies by default.
- It generates report on active CA policies.
- Finds all disabled CA policies.
- It also lists report-only mode CA policies.
- Identifies the recently created CA policies for review.
- Lists recently modified CA policies for tracking changes.
- The script can be executed with MFA-enabled accounts.
- It exports reports to CSV format.
- The script automatically installs the required Microsoft Graph Beta PowerShell module upon user confirmation.
- Supports certificate-based authentication for secure access.
- Includes scheduler-friendly functionality for automated reporting.
Conditional Access Policies Reports –Sample Output
The exported Conditional Access policy report will resemble the screenshot provided below.
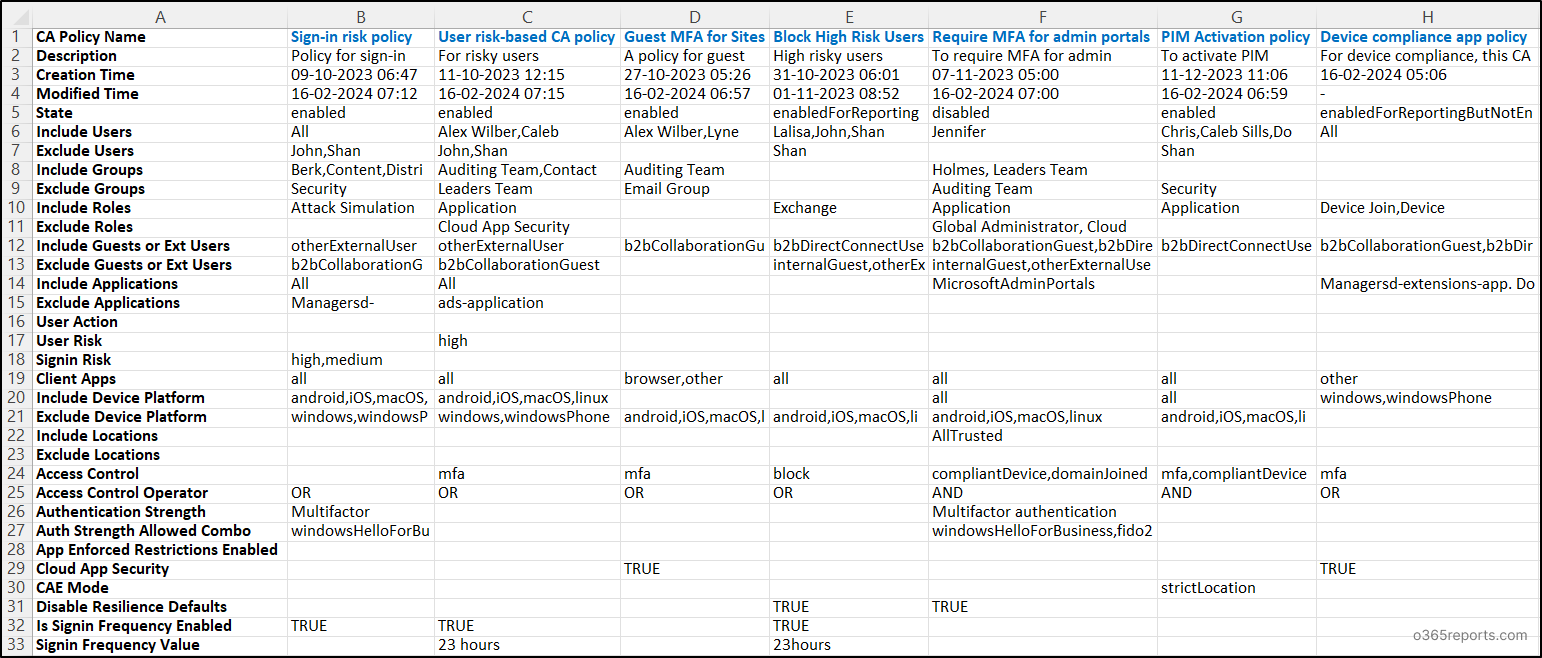
Note: The report data in the screenshot has been transposed to display all attributes.
How to Execute the Script?
Download the script provided above and open Windows PowerShell on your system. Execute the script using any of the methods listed below.
Method 1: You can execute the script using both MFA and non-MFA accounts.
|
1 |
./ExportCApolicies.ps1 |
The script exports all Conditional Access policies to CSV format.
Method 2: For an unattended approach, you can run the script using certificate-based authentication. You can also use this method to schedule the CA Policy report.
|
1 |
./ExportCApolicies.ps1 -TenantId <tenantId> -ClientId <ClientId> –CertificateThumbprint <Certthumbprint> |
You can use either a certificate authority or a self-signed certificate based on your preferences. However, ensure you register an app in Azure AD before using certificate-based authentication.
Export Conditional Access Policies Reports using PowerShell
With this PowerShell script, you can achieve the following:
- Export CA policies via PowerShell
- View active Conditional Access policies
- Find disabled CA Policies in Microsoft 365
- Identify report-only mode Conditional Access policies
- Detect the recently created CA policies
- Spot the recently modified CA policies
1. Monitor All Conditional Access Policies in Entra ID
By analyzing all Conditional Access (CA) policies in the organization, admins can gain an overview of the security measures implemented. This process ensures that the policies align with the organization’s security requirements and compliance standards. Therefore, admins should list all CA policies available in the organization and monitor them. To retrieve all Entra ID Conditional Access policies, use the script below.
|
1 |
./ExportCApolicies.ps1 |
The exported data displays all implemented Conditional Access policies in the organization.
2. View Enabled Conditional Access Policies in Microsoft 365
Admins should monitor enabled CA policies to verify that access controls are in place and users aren’t facing unexpected authentication challenges. Monitoring successful CA policy enforcement during sign-ins also helps detect suspicious activities, indicating a security breach or policy misconfiguration. This allows admins to take prompt actions to mitigate risks and maintain a secure environment. If a user’s access is unexpectedly blocked, admins can identify which CA policy is blocking sign-ins and take the necessary steps to resolve it.
To view all active CA policies, admins can execute the script with the “ActiveCAPoliciesOnly” parameter as shown below.
|
1 |
./ExportCApolicies.ps1 -ActiveCAPoliciesOnly |
The script exports all active Conditional Access policies, which means only the policies that are turned on or enabled.
If you notice too many Conditional Access policies applied on the same resources, use Custom Security Attributes in Entra ID to avoid policy sprawl. Dynamic Conditional Access will then apply policies automatically based on the assigned attributes.
3. Find Disabled Conditional Access Policies
Monitoring disabled Conditional Access (CA) policies is essential because they can still contain configurations or conditions that might affect user authentication or access control. Admins should monitor these disabled policies to prevent accidental impacts on user access or the organization’s security posture.
Use the script below with the“DisabledCAPoliciesOnly” parameter to find all disabled CA policies.
|
1 |
./ExportCApolicies.ps1 -DisabledCAPoliciesOnly |
The above format exports all disabled Conditional Access policies in the organization. By monitoring this report, admins can proactively address potential issues and ensure effective enforcement of their organization’s CA policies.
4. Identify Report-Only Conditional Access Policies
The report-only mode in Conditional Access allows admins to test CA policies before enforcing them. Admins should identify all CA policies in this mode to assess their impact and decide whether to enforce them. To export Conditional Access policies that are currently in report-only mode, use the following script with the “ReportOnlyMode” parameter.
|
1 |
./ExportCApolicies.ps1 -ReportOnlyMode |
The exported report contains only the CA policies that are in report-only mode.
5. Detect the Recently Created CA policies
It’s crucial to monitor recently created Conditional Access policies to ensure their correct configuration. For example, if a new policy inadvertently blocks legitimate users, it can disrupt the organization’s workflow. Thus, admins should analyze the recently created CA policies in Microsoft 365. This allows them to quickly review and validate these policies, avoiding disruptions to user access and ensuring they’re correctly configured.
Execute the script below with the “RecentlyCreatedCApolicies” parameter to identify all recently created policies. Additionally, ensure to specify the number of days before execution.
|
1 |
./ExportCApolicies.ps1 -RecentlyCreatedCAPolicies 30 |
The above format returns the CA policies that were recently created within the last 30 days.
6. Check Recently Modified Conditional Access Policies
In organizations with multiple Conditional Access (CA) administrators, regular reviews and updates are common. Small errors in these CA policies can lead to major security risks by affecting access to Microsoft 365 resources. Thus, regularly monitor CA policy changes for swift issue identification and resolution, ensuring ongoing protection for Microsoft 365.
To facilitate this, run the provided script with the “RecentlyModifiedCAPolicies” parameter with the number of days to pinpoint all recently modified CA policies.
|
1 |
./ExportCApolicies.ps1 -RecentlyModifiedCAPolicies 60 |
The example above exports all modified Conditional Access policies that were changed within the last 60 days. This proactive approach simplifies the process of auditing CA policy changes
Even though CA policies can now be exported, there is no straightforward way to determine which policies require MFA for each user. So granular!
Nevertheless, this PowerShell script identifies Conditional Access policies requiring MFA assigned to users so you can pinpoint the exact policy causing MFA lockouts.
Conditional Access Policy Components in the Exported Report:
Let’s briefly review the properties of Conditional Access policies exported in the report. The exported CA policy report includes the following attributes:
- CA Policy Name
- Description
- Creation Time
- Modified Time
- State
- Conditional Access Policy Assignments:
- Users & Groups in CA Policy: Include Users, Exclude Uses, Include Groups, Exclude Groups
- Directory Roles in CA Policy: Include Directory Roles, Exclude Directory Roles
- Guest or External users: Include Guests or Ext Users, Exclude Guests or Ext Users
- CA Policy Target Resources: Include Cloud Apps, Exclude Cloud Apps, User Action
- Conditions in Conditional Access Policy: User Risk, Sign-in Risk, Client Apps, Include Device Platform, Exclude Device Platform, Include Locations, Exclude Locations
- Access Control in CA Policy:
- Access Control – Grant Access or Block Access
- Access Control Operator for Multiple Controls
- Authentication Strength
- Auth Strength Allowed Combo
- Session Controls in CA Policy:
- Use App Enforced Restrictions Enabled
- Use Conditional Access App Control – Cloud App Security
- Customize Continuous Access Evaluation – CAE Mode
- Disable Resilience Defaults
- Is Sign-in Frequency Enabled
- Sign-in Frequency Value
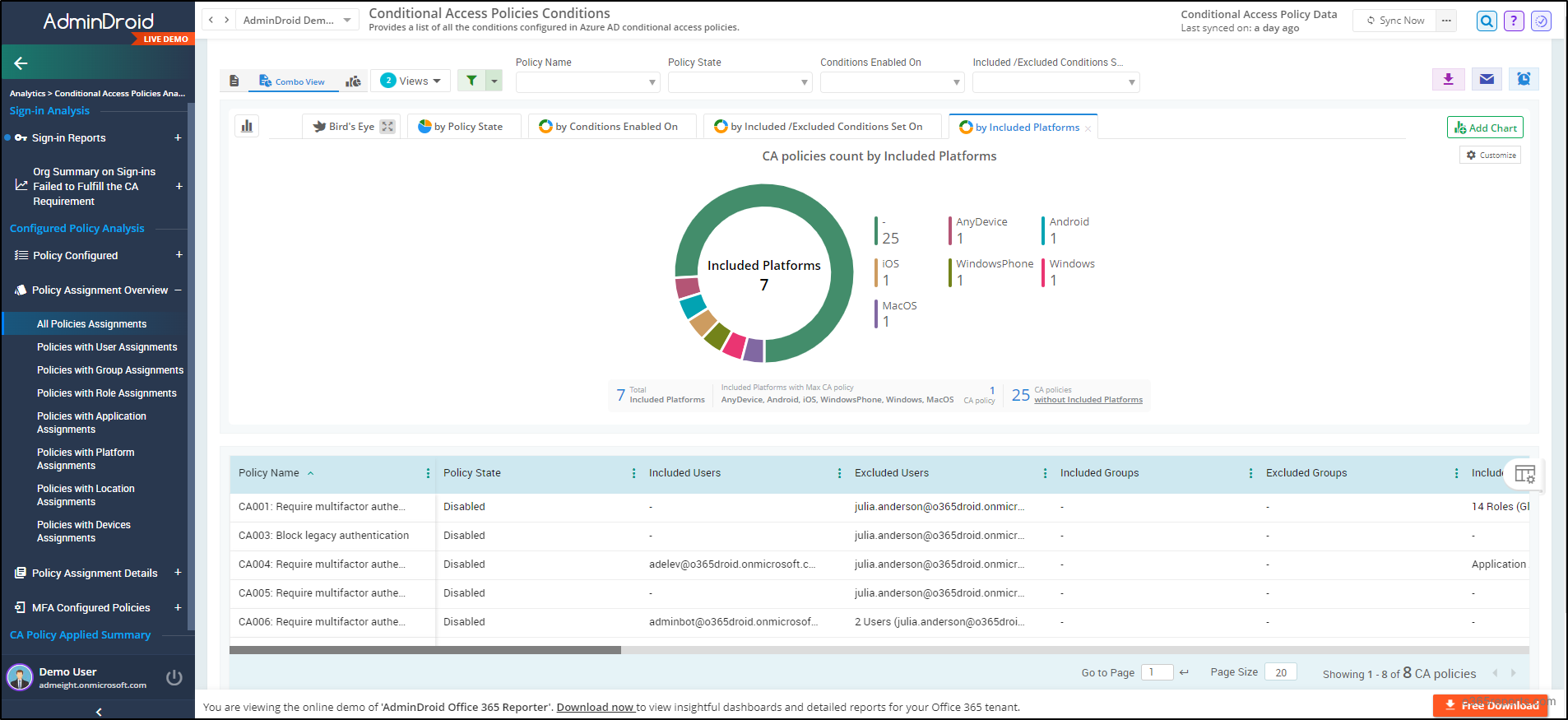
Unlock Comprehensive Conditional Access Reports with AdminDroid M365 Reporter!
Are you seeking deeper insights into your Conditional Access policies beyond basic reports? Then, look no further! AdminDroid Microsoft 365 Reporter offers a robust solution.
AdminDroid provides a wealth of reports on CA policy configurations, sign-ins based on CA policies, etc. It includes,
Sign-in Analysis based on CA policies
- Sign-ins passed by CA policy
- Sign-ins blocked by CA policy
- Users failed to fulfill CA policy requirements
- Sign-ins without any CA policy check
Users’ Sign-in Summary based on CA policy
- Overall count of the sign-ins by configured CA policies
- User sign-ins count satisfied by CA policy
- User sign-ins count blocked by CA policy
Configured CA policies
- All CA policies
- Recently modified CA policies
- Grant control details of CA policies
- Session control details of CA policies
CA Policies with MFA
- All CA policies with MFA
- MFA enabled CA policies assignments overview
- MFA enabled CA policies details
CA Policy Configuration Analysis
- User conditions in Azure AD CA policies
- Group conditions configured in CA policies
- App conditions configured in CA policies
- Role conditions in Azure AD CA policies
- Location conditions configured in CA policies
This is just a snapshot of what AdminDroid offers!
In addition, AdminDroid offers 120+ Azure AD reports and 10+ insightful dashboards, all completely free for your Azure AD management.
Furthermore, AdminDroid provides 1800+ detailed reports and 30+ sleek dashboards for MS Teams, SharePoint Online, OneDrive, Exchange Online, Stream, Power BI, and Viva Engage.
With features such as real-time alerting, quick scheduling, granular delegation, and advanced customization filters, AdminDroid simplifies your Microsoft 365 management.
Download AdminDroid now and enjoy a free 15-day trial – no credit card required! Streamline your admin tasks with AdminDroid today!
In summary, using PowerShell to export Conditional Access policies is a quick and effective way to manage and document security settings. We hope this blog has simplified the process of exporting Conditional Access insights and reporting using PowerShell. If you have any questions or need assistance, feel free to contact us in the comments section.