As everything is being moved to the cloud environment these days, security becomes a definite question mark! That too when automated tools and applications are given extensive permissions, leaving an organization vulnerable to cyberattacks and other security breaches. Yes! The protection layer of your organization will look fragile with the most inclusive permissions for the applications.
Therefore, Microsoft introduced service principal sign-ins in Azure AD to simplify access management, enhance security and enable easier automation of workflows. The service principal is an identity that allows applications and services to authenticate and access resources.
Moreover, monitoring service principal sign-ins becomes mandatory as it acts as a key to the locker with which anybody can easily access your data! Therefore, constantly monitoring the service principal sign-ins with eyes wide open becomes essential to prevent security threats. So, without further ado, let’s learn more about service principals and how to monitor them here.
What is Service Principal in Azure?
A service principal in Azure AD is a type of identity created for applications, hosted services, and automated tools for the purpose of the utilization of resources and accomplishment of tasks within the Office 365 environment.
Real time Use Case of Service Principal in Microsoft 365
For example, say you want to register an app to access the Microsoft Graph for some automation purposes. Then, that’s where service principals come into play! A service principal is created as an identity, that allows the application to access the required resources without requiring user interaction or exposing user credentials.
Each service principal is assigned a unique identifier and login credentials upon creation. Later, this can be used during the process of authentication and authorization to verify the identity of the registered application.
- This set of credentials can include certificates or secrets for the apps, which are securely stored and used to obtain access tokens that allow the service principal to perform actions on behalf of the organization.
Note:
You can follow the security guidelines for registering an application in Azure AD to better align with the best practices of the applications in Microsoft 365.
How to Create a Service Principal in Azure AD?
Create service principal easily while registering an app by following the below steps.
Microsoft Entra admin center 🡢 Applications 🡢 App registration 🡢 New registration
- Give a ‘Name’ to your app and select ‘Accounts in this organizational directory only’ under Supported account types.
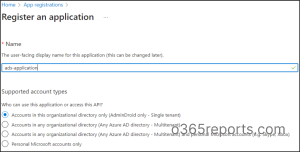
- After registering your application, copy the Application (client) Id which will be required later.
- Now, click ‘Add a certificate or secret’ under Client credentials.
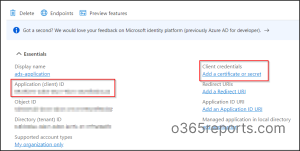
- Next select ‘New client secret’, then add a description and expiry date to the client secret.
- Then copy the Secret Value which will not be displayed later. For security reasons and to protect them from falling into the wrong hands, the secret value, also known as the application password, is not displayed later.
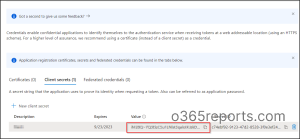
Eventually, the application ID and secret key value will be used as a login credential at the time of signing into the client application. As we are now clear about creating service principals in Azure, let us see how to view the service principal sign-in reports in the Azure portal.
Note: Azure AD Graph API is now deprecated, and future investments will focus exclusively on Microsoft Graph. To ensure continued support and leverage modern features, Microsoft advises you to migrate service principals to Microsoft Graph API.
The Need to Monitor Service Principal Sign-ins in Azure AD?
Keeping an eye on service principal sign-ins and monitoring consistently can highly help admins to stay ahead of potential threats and keep the data secure. Therefore, let’s see some of the potential issues that will give reasons to start monitoring service principal sign-ins strictly!
Be aware of exploitation -Cybercriminals can exploit the credentials associated with the service principal to gain access to sensitive data or perform malicious activities that go undetected for extended periods. So, monitoring service principal sign-ins can help to avoid such malicious attacks!
Resource utilization – It is highly essential for admins to monitor service principal sign-ins to know the daily use of the application and how the resources have been accessed in your organization. Therefore, just be watchful of the regular patterns in order to spot unusual activity in your Microsoft 365 environment.
Risk minimization – Tracking service principal sign-ins is way more important in the process of reducing the unwanted risks of misusing applications in your Azure AD tenant. If you detect unusual patterns in application usage, it’s essential to quickly revoke access to applications & prevent further data loss.
Identify certificate and secret users – Through this monitoring, you can detect who uses the secret values and who uses certificates for sign-in activity in your organizational setup.
Supervise service principal sign-in with conditional access – Sometimes it is hard to manage service principals with conditional access used for purposes like blocking service principals from unknown locations. Therefore, do check these reports continuously to manage the service principal sign-ins deployed with conditional access.
How to Monitor Service Principal Sign-ins in Azure AD?
You can monitor service principal sign-in activity in two different places within Azure AD.
- Service principal sign-ins in Azure AD sign-in logs.
- Service principal sign-in activity in Usage and Insights.
Monitor Service Principal Sign-ins in Azure AD Sign-in Logs
You can follow the path below to view the service principal sign-in reports.
Microsoft Entra admin center 🡢Monitoring & health 🡢 Sign-in logs 🡢 Service Principal sign-ins.
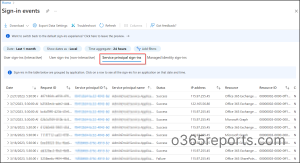
This report contains the Date, Request ID, Service principal ID, Service principal name, Status, IP address, Resource, Resource ID, Conditional access, and Sign-ins.
- Date – The date column displays the last sign-in date & time of the respective sign-in activity.
- Request ID – It is the request identifier of the sign-in activity associated with request detection.
- Service principal ID – The service principal ID is the unique ID of the service principal object associated with the application.
- Service principal name – It displays the service principal name from where the sign-in was initiated.
- IP address – The IP address of the location in which the client used to sign-in.
- Resource – The type of resource in which the service principal is signed is displayed here.
- Resource ID – The ID of resources like Microsoft graph, Office 365 Exchange Online, Windows Azure Active Directory, and many more resources into which the service principal is signed are recorded here.
- Conditional access – A list of all conditional access policies applied for the sign-in can be seen here.
Primarily, this report doesn’t support the customization of columns, instead allows you to filter based on specific fields. Thus, to make the sign-in data an easily accessible and digestible model, Microsoft aggregates the sign-in events into a single entity when the following data types are the same.
- Service principal ID
- Service principal name
- Status
- IP address
- Resource
- Resource ID
Audit the Service Principal Sign-in Activity in Usage & Insights
Lately, Microsoft has introduced a new report experience for ‘service principal sign-ins’ in the Usage & insights section. Navigate to the path below to view the new experience!
Microsoft Entra admin center 🡢 Monitoring & health 🡢 Usage & Insights 🡢 Service principal sign-in activity (Preview)
Here, you can notice that ‘Service principal sign-in activity is available in preview’ along with 3 different preview reports. And the following are the 5 different reports provided by the ‘Usage and insights reporting section’ on different sign-in activities.
- Azure AD application activity report (Preview)
- AD FS application activity report
- Authentication methods activity
- Service principal sign-in activity (Preview)
- Application credential activity (Preview)
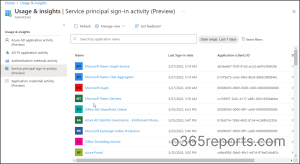
With the new ‘service principal sign-ins report in the usage and insights’ section, admins can quickly generate reports based on the sign-in data of specific applications. Also, you can optimize reports for a specific period based on the default options available in the drop-down list of the date range.
The “usage & insights” section provides a convenient way for admins to obtain an overview of the sign-in activity of a specific application by service principals along with application details. But, whereas in the sign-in logs, all the sign-in activities are grouped and listed based on the time frame.
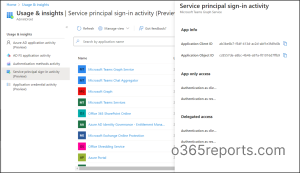
Basically, this service principal sign-in report lists the application name, last sign-in date, application (client) id, and details. Click on ‘View more details’ to know more details about the specific application.
- The details tab elaborates on the app-only access and delegated access of the applications. The apparent details of frequent usage of applications and inactive applications can be inferred explicitly from the column of ‘last sign-in date’ in these reports.
Pre-requisites to View Usage and Insights
- To access the Usage and Insights, users must be assigned with any one of the following roles.
- Global administrator
- Security administrator
- Security reader
- Report reader
- The Azure AD Premium (P1/ P2) subscription is required.
Although you can monitor service principal sign-in activity in the native admin center, visualizing every nook and corner of its changes is not possible with the admin center! And in the case of PowerShell, you need to loop multiple cmdlets to generate desired error-free reports. However, no more hassle in monitoring service principal sign-in activity because AdminDroid Microsoft 365 Reporter is at your rescue!
Enjoy Free Service Principal Sign-in Activity Reports with AdminDroid!
Now look through all the crystal-clear stats of service principal sign-in activity and every change with the AdminDroid service principal sign-in reports. Free Azure AD reporting tool by AdminDroid, offers more robust and dedicated reports on sign-in activities, risky sign-ins, password reset activity reports, MFA usage reports, group activity reports, etc., of your Microsoft 365 environment. Along with the column customization ability, it allows you to tweak a lot of desired reports.
Moreover, the AdminDroid service principal changes report helps to thoroughly monitor and analyze every minor change in service principals, such as new service principals added, updated, or removed within your organization. And the granular report dives deep into service principal sign-in activities comprising details like sign-in time, signed-in application name, sign-in status, sign-in location, and many more.
On top of this, the spectacular AdminDroid Azure AD auditing tool helps you to carry out user auditing, group auditing, user logins auditing, admin role changes auditing, application auditing, and setting change auditing for better insights and administration.
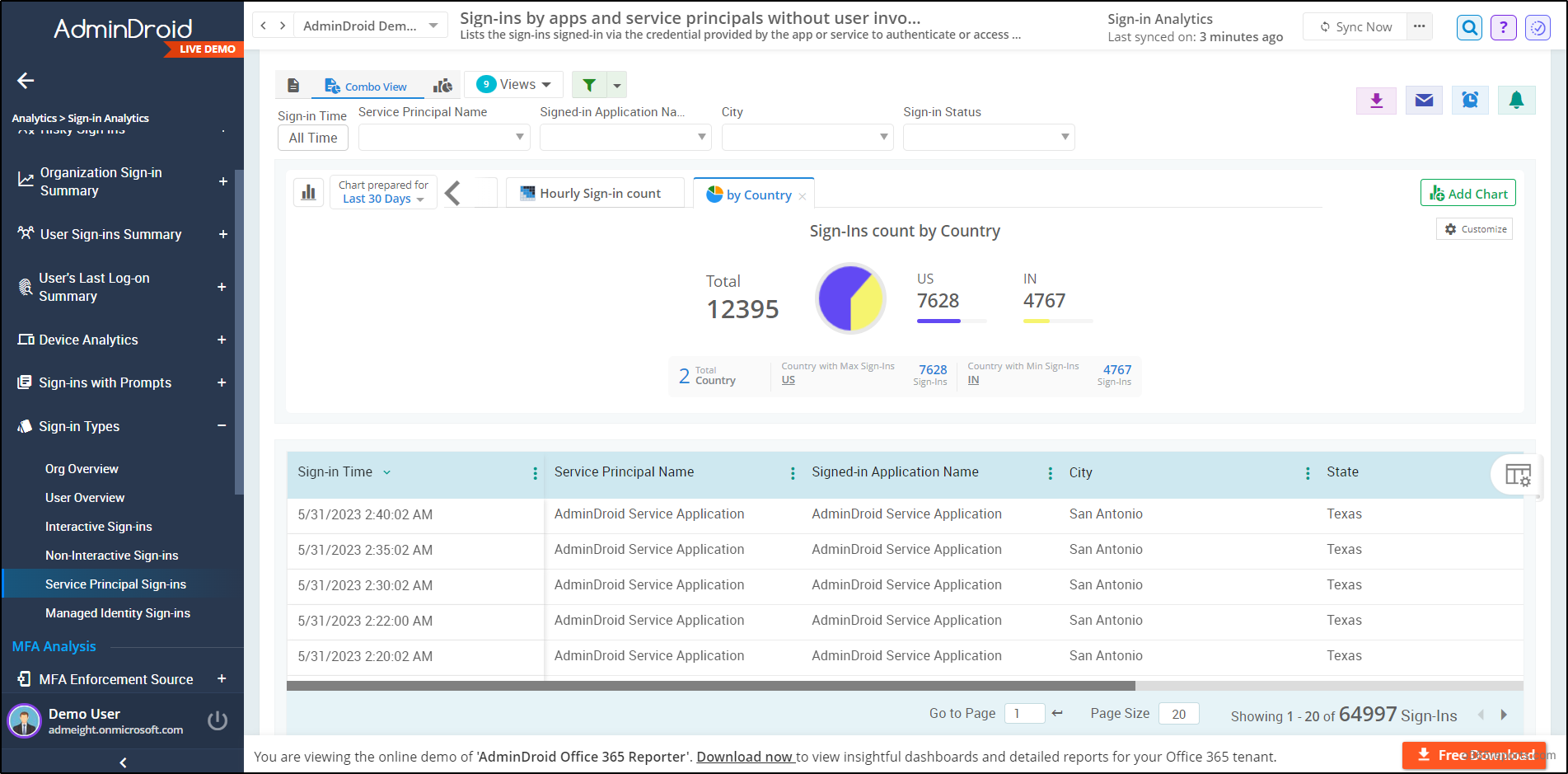
AdminDroid provides 190+ free reports and 10+ smart dashboards on user login activities, MFA changes, password changes, license & expiration changes, and more. So, get started now and enjoy a free reporting experience with the AdminDroid Azure AD management tool
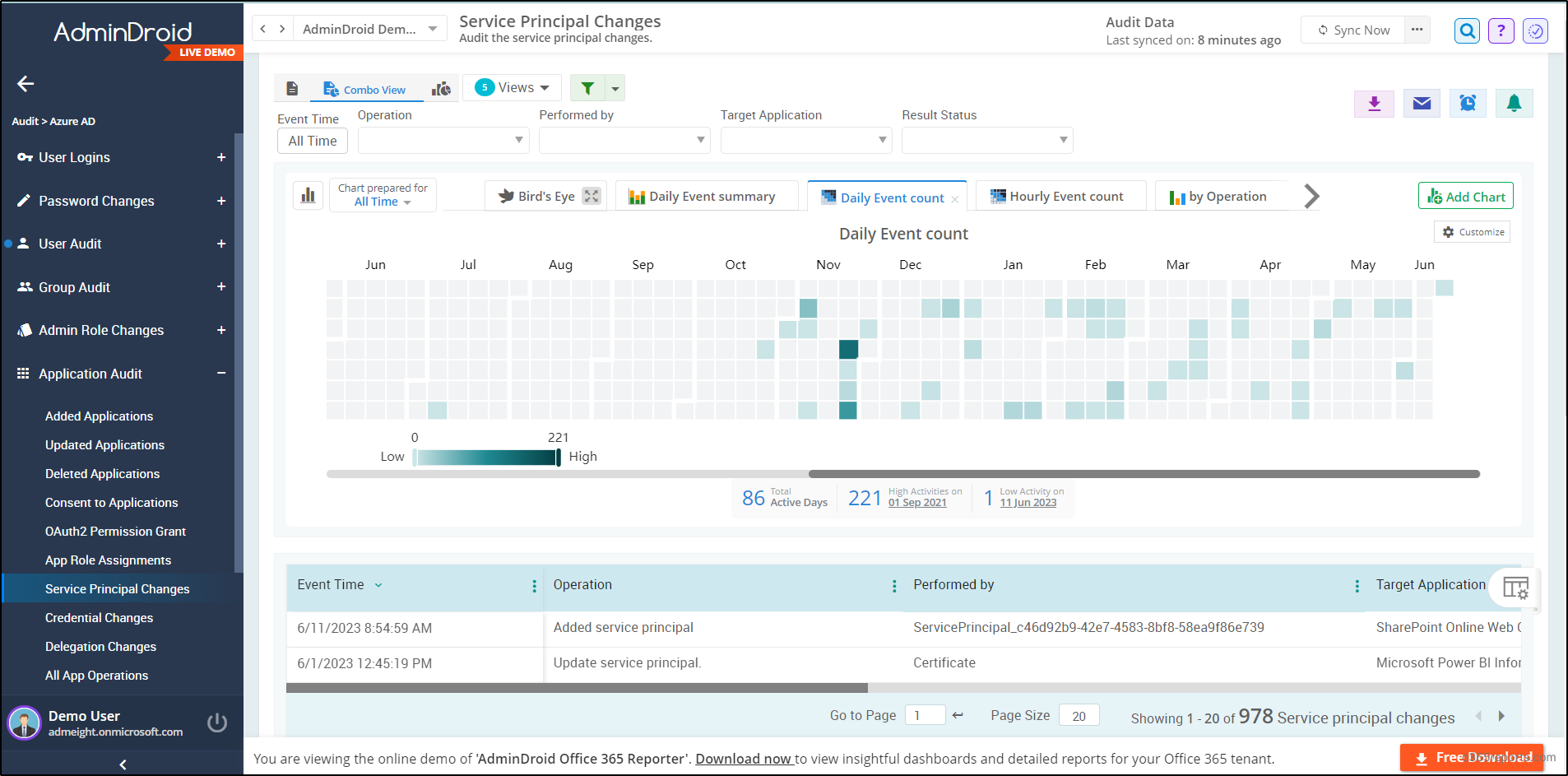
Don’t confine yourself to service principal sign-in & changes monitoring, now start exploring the
AdminDroid Microsoft 365 Reporting tool for a highly advanced reporting experience. You can carry out hassle-free administration with 1800+ pre-built reports by AdminDroid for every Microsoft 365 service.
“Comfortably visualize your Microsoft 365 space from AdminDroid 30+ sleek & smart dashboards for enhanced Office management!”
With its highly advanced features and user-friendly interface, AdminDroid leaves you no choice for Microsoft 365 reporting and monitoring! Download AdminDroid now to enjoy facile Office 365 administrating capabilities.
As a wrap up, we recommend you to monitor every step of service principal sign-ins to be aware of unauthorized access and strictly restrict the permissions for the backdoor access of resources. Organizations can enhance their cybersecurity posture and safeguard against various threats by taking the appropriate safety measures to secure the sign-in process.
Hope this blog made you familiar with service principal and its characteristics. Drop your thoughts in the comments section.