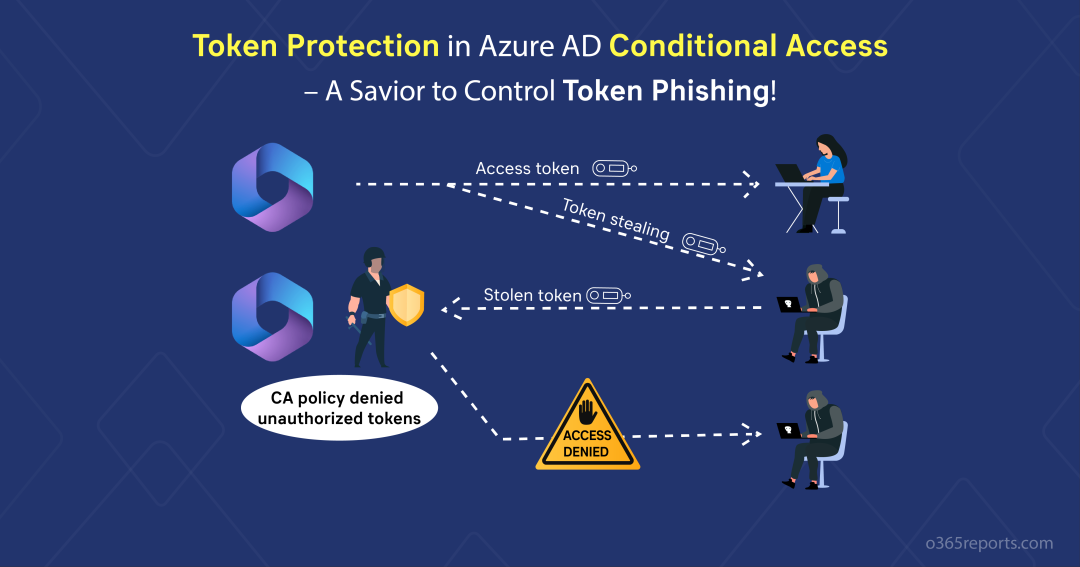
Token stealing is a serious threat in this hybrid work environment. Attackers use various technologies to steal tokens instead of passwords. With those stolen tokens, they will access critical resources and perform malicious activities in your Office365 environment. So, every organization should have a proper defense mechanism to overcome these token phishing attacks. To help you with this, Microsoft deployed the Token protection in Azure AD Conditional Access policy in addition to the CAE’s strictly enforced location policies that will protect your Office 365 resources from malicious attackers who try to compromise your organization’s security.
Therefore, let’s dive deeper to examine token protection (token binding) in detail and also learn to configure Conditional Access policies with token protection to safeguard your resources from attackers!
Token Protection in Azure AD Conditional Access
Office365 access tokens act as entry cards given to every user in an organization. And these tokens contain users’ identities which are used to access organization resources. Since users login to the resources using unmanaged devices, it becomes a loophole for the attackers to steal their Office365 access tokens.
After stealing the token, the attacker may perform activities like sending phishing messages to other users, changing user account settings, and stealing sensitive Office 365 data. Thus, it lets admins allow only authenticated access tokens created while users sign-in to the Office 365 resources.
Token protection creates a tight knot between the token and the intended device (client’s secret).
As quoted above, you can ensure that your users access resources using valid Office access tokens. From now on, you can create a Conditional Access Policy to enforce token protection in Azure AD. Undoubtedly, this policy will act as a first-line defense against unauthorized token access by attackers.
Checklist to Configure Conditional Access Policy with Token Protection
Below are the prerequisites that are taken into consideration before configuring the Conditional Access policy with token protection,
- First, you should have devices with Windows 10 or newer devices that are Azure AD joined, hybrid Azure AD joined, or Azure AD registered.
- Make sure to have the following versions for OneDrive and Microsoft Teams client,
-
-
- OneDrive-version 22.217 or later.
-
-
-
- Teams client-version 1.6.00.1331 or later.
-
Limitations in Creating Conditional Access Policy Using Token Protection
Besides prerequisites, there are some limitations in configuring the token protection in Azure AD Conditional Access. They are,
- Firstly, external users invited via Azure AD B2B are not supported, and it is advised not to include them in the policy.
- The windows client devices such as Windows Server and Surface Hub are not supported.
- Some applications don’t support signing in using the protected tokens. They are,
-
-
- Power BI Desktop client.
- PowerShell modules accessing Exchange, SharePoint, or Microsoft Graph scopes that are served by Exchange or SharePoint.
- PowerQuery extension for Excel.
- Extensions to Visual Studio Code which access Exchange or SharePoint.
- Visual Studio.
-
Create a Conditional Access Policy Using Token Protection (Preview)
A Conditional Access policy with token protection reduces the risky sign-ins using stolen tokens, since it allows only authorized users to access the organization’s sensitive information.
Important: Sign-in using token protection in the Conditional Access policy is only available for desktop applications that access Exchange Online and SharePoint Online on Windows devices.
To create a Conditional Access policy, follow the steps below.
- To begin with, sign in to the Microsoft Entra admin center as Conditional Access Administrator, Security Administrator, or Global Administrator.
- Then, click the Azure Active Directory from the left side tab and select ‘Conditional Access’ under Protect & secure option.
- After that, click + New policy to create a Conditional Access policy.
- Then, you can give a suitable name to your policy.
- Now, under the Assignments blade, from the Users option, you can choose all the users or specific users/groups whom you want to enable this policy.
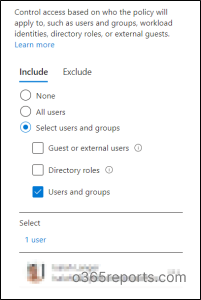
6. Then, under Cloud apps or action blade, select the cloud apps Office 365 Exchange Online, and Office 365 SharePoint Online.
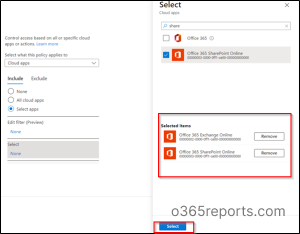
7. Now, under the conditions blade, click 0 conditions selected.
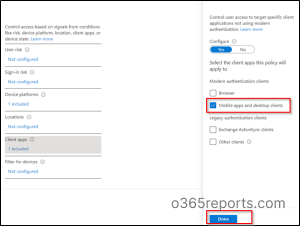
→ Now, you can configure Device platforms as Windows by toggling the configure option to ‘Yes’ and then click Done.
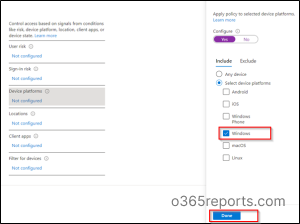
→ And then, you can configure Client apps as per your requirement by toggling the configure option to ‘Yes’ and then click Done.
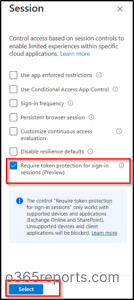
8. Finally, under Access controls > Session, select ‘Require token protection for sign-in sessions’ and click Select.
9. Finally, enable the policy to ‘Report-only’ or ‘On’ mode.
Once you have successfully created a policy, users with protected tokens are granted permission to access SharePoint Online and Exchange Online after successfully satisfying the conditions of the Conditional Access policy.
Monitor Risky Sign-ins Using Azure AD Sign-in Logs
Once the policy has been applied to the assigned users, you can view the policy enforcement status using Azure AD sign-in logs. You can ensure that no suspicious login attempts took place using access tokens through these logs.
You can view the sign-in logs in Azure Active Directory by the steps below.
- First, navigate to Conditional Access under Protect & secure option using the above-mentioned admin roles.
- Now, click Sign-in logs from the left side tab.
- Then, select the specific sign-in request to check whether the policy is accurately applied or not.
- Click the Conditional Access or Report-only mode pane based on its state and then select the policy that enforced token protection.
- Finally, under Session controls, you can view whether the policy requirements were satisfied or not.
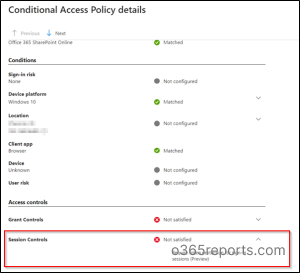
Note: You can also be able to use the log analytics to query the sign-in logs for allowed/blocked login requests for which the token protection policy is applied.
Wipe Out Token Stealing!
Even though token stealing by attackers occurs rare, its impact will hit us hard. Fortunately, the Token protection in Conditional Access policy came into existence that significantly reduces the risk of attackers gaining access to sensitive information. Thus, eliminate attackers intruding on your resources by creating a Conditional Access policy using token protection!
“At the end of the day, the goals are simple: Safety and Security”
-JODI RELL
We hope this blog helps you to gain information about Token protection in Azure AD Conditional Access policy. Furthermore, if you have any suggestions or ideas on policy creation using token protection, we welcome you to share them in the comments section.