When applications are registered in Microsoft Entra, they are granted with surprising number of privileges like accessing sensitive data to acting on behalf of users. But these permissions aren’t static. Once an app is registered, its configuration can evolve over time through various operational changes.
Admins may include additional permissions, remove unused credentials, or update role assignments to meet the ever-changing needs of the organization. While these actions are often necessary, they also introduce security risks, especially when performed without oversight.
That’s why auditing Entra app operations is important to drastically improve your applications security in Microsoft 365. In this blog, we’ll walk you through how to audit Microsoft Entra app operations. It helps you see who made changes, when they occurred, and prevent the misuse of critical apps.
How to View All Operations Performed on Entra ID App Registrations?
To list the changes made on the Entra ID apps, you can use the following approaches.
- Monitor app change activities in Entra admin center
- View Azure AD app activities with Microsoft Purview audit search
- Audit Entra app operations through PowerShell (Recommended)
1. Monitor App Change Activities in Entra Admin Center
You can check actions performed on the Entra ID app registrations in the Microsoft Entra admin center by following the steps below.
- Log in to the Microsoft Entra admin center.
- Navigate to Audit logs under Identity → Show more → Monitoring & health.
- Use the Date range filter to select a time range.
- Select the Category filter and choose ApplicationManagement from the drop-down list, then click Apply.
- Now, it will display all the operations performed on Entra ID applications.
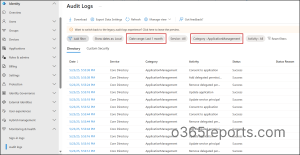
However, Entra audit logs retains app management activity records for a maximum of 30 days.
2. View Azure AD app Activities with Microsoft Purview Audit Search
To track all Entra ID app operations from Microsoft Purview portal, follow the steps mentioned below.
- Navigate to Search under Solutions → Audit in the Microsoft Purview portal.
- Customize the Start and End date based on requirements.
- Select all the Azure AD app operations under ‘Application administration activities’ in the Activities – friendly names dropdown.
- Click Search. Once the search is completed, you can view the results of all Azure AD app activities.

While Purview audit search can provide 180 days of audit records, it lacks granularity in filtering and exporting results.
3. Audit Entra App Operations Through PowerShell
As an alternative to the methods above, you can use the Search-UnifiedAuditLog cmdlet from Exchange Online PowerShell.
This cmdlet gathers data from all Entra ID apps, though you’ll still need to apply complex filters to retrieve specific operational changes. That’s why we built a PowerShell script that allows you to export all Entra app management activities quickly. The script streamlines auditing by providing essential details like app name, operation, and responsible user all in one go.
Download Script: AuditEntraAppOperations.ps1
Script Highlights:
- Tracks all Entra app operations for the past 180 days.
- Allows to track app operations for a custom date range.
- The script automatically verifies and installs the Exchange Online PowerShell V3 module (if not installed already) upon your confirmation.
- Enables filtering of app operations from the following categories.
- Added Applications
- Updated Applications
- Deleted Applications
- Consent to Applications
- OAuth2 Permission Grants
- App Role Assignments
- Service Principal Changes
- Credential Changes
- Delegation Changes
- Tracks app operations performed on the specific application.
- Generates a report that retrieves successful operations alone.
- Helps export failed operations alone.
- Audit app operations performed by a specific user.
- The script can be executed with an MFA-enabled account too.
- Exports report results as a CSV file.
- The script is scheduler friendly.
- It can be executed with certificate-based authentication (CBA) too.
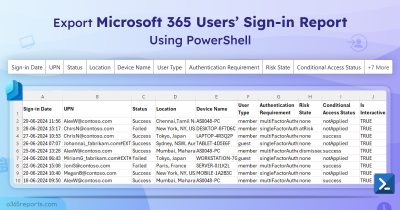
Entra App Operation Audit Report – Sample Output
The exported ‘App operations’ report looks like the screenshot below.
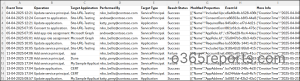
The exported report contains Event Time, Operation, Target Application, Performed By, Target Type, Result Status, Modified Properties, Event Id, and More Info.
Entra App Operation Audit Report – Script Execution Methods
- Download the script.
- Start the Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1:
Execute the script with MFA or non-MFA account.
|
1 |
./AuditEntraAppOperations.ps1 |
Running the script will export audit report of all app operation activities over the past 180 days.
Method 2: Execute the script by explicitly mentioning credentials.
|
1 |
./AuditEntraAppOperations.ps1 -Username admin@contoso.com -Password XXX |
The above method supports only non-MFA accounts. If the admin account has MFA, you need to disable MFA using CA policy make this method to work.
Method 3: Execute the script using certificate-based authentication.
To use certificate-based authentication, you must register the app in Entra ID which helps you to connect Exchange Online using certificate.
|
1 |
./AuditEntraAppOperations.ps1 -Organization <Domain> -ClientId <AppId> -CertificateThumbprint <CertThumbPrint> |
Depending on the requirement, you can use either CA certificates or create self-signed certificates.
You can also schedule this script using Task Scheduler or Azure Automation to periodically export list of operations performed on the Entra applications.
Audit Azure AD App Operation Activities – More Use Cases
The script provides granular app registration operation report with flexible filtering options, allowing you to analyze various scenarios effectively, such as:
- Audit app operations for custom period
- Track app operations performed by a specific user
- Get successfully completed app activities
- Identify failed Entra app operations
- Get operations performed on specific app registration
- Filter Entra ID app operations by action type
- Monitor app management activities more granularly
1. Get All Entra App Operations Performed Within a Specific Timeframe
By default, this script retrieves all app management activities in Microsoft Entra for the last 180 days. However, if you suspect app modifications occurred over the specific time, auditing only that period reduces noise.
In such cases, you can run the script with -StartDate and -EndDate parameters to reduce the script execution time and narrow down the search results.
|
1 |
./AuditEntraAppOperations.ps1 -StartDate 04/01/2025 -EndDate 04/30/2025 |
The above command retrieves all activities performed on the apps and service principals between April 01, 2025, and April 30, 2025.
2. Track Changes Made by a Specific User in Entra ID Apps
Reviewing operations performed by a specific user helps maintain clarity around their role and responsibilities. For instance, if a user is suspected of granting unnecessary app consents, you can easily filter operations they performed using -PerformedBy parameter.
|
1 |
./AuditEntraAppOperations.ps1 -PerformedBy gennady_golovkin@contoso.com |
Running this action helps to track changes made by the ‘Gennady Golovkin’ in Azure AD applications.
3. Audit Successfully Performed App Operations in Entra
Filtering only successful operations helps streamline compliance audits by confirming which changes were actually implemented. For example, you can verify that apps with expired secrets or certificates have been properly updated with new credentials.
To filter successfully completed app management operations, execute the script with the –SucceedOnly parameter as shown below.
|
1 |
./AuditEntraAppOperations.ps1 -SucceedOnly |
This script execution will return all successfully performed Entra app operations.
4. Identify Failed App Operations in Microsoft Entra
Failed operations can indicate misconfigurations or unauthorized attempts to modify Entra applications. Use the -FailedOnly param to find and review those unsuccessful changes.
|
1 |
./AuditEntraAppOperations.ps1 -FailedOnly |
This format will export all failed app operations; help you fix errors quickly and improve operational resilience.
5. Find Activities Performed on the Specific Entra Application
When monitoring sensitive or high-risk apps like emergency access application, narrowing the audit to a specific app can uncover misuse. However, apps in the Entra can have the same names, so it’s efficient to filter the app with its id.
To get changes applied on the specific application in Entra, use –AppId param along application’s id like below.
|
1 |
./AuditEntraAppOperations.ps1 -AppId abcd1234-5678-efgh-9876-ijkl9012mnop |
The exported report contains all activities done on the application with id ‘abcd1234-5678-efgh-9876-ijkl9012mnop’.
6. Filter Entra ID App Operations by Action Type in Entra ID
Focusing on specific operations helps streamline investigations and identify unusual changes in Entra apps and service principals. For example, you can track permissions consented to application by filtering the ‘Consent to application’ operation. This helps quickly identify illicit consent attacks or other risky permission grants.
To filter specific app operations, you can use the –Operations parameter like below.
|
1 |
./AuditEntraAppOperations.ps1 -Operations 'Consent to application' |
Tracking this action assists in confirming and remediating illicit consent grants given to third-party apps in Microsoft 365.
Similarly, to trace changes like credential updates or app role assignments, adjust the operation filter accordingly. Filtering these actions often expose lateral movement or privilege escalation attempts in your Microsoft 365 environment.
|
1 |
./AuditEntraAppOperations.ps1 -Operations 'Credential Changes','App Role Assignments' |
By narrowing down to relevant activity types, you can reduce noise and make your investigation more effective.
7. Audit App Operations More Granularly in Microsoft Entra
By default, this PowerShell script supports multiple advanced filtering options. In addition to this, you can combine one or more filters to get tailored reports for your specific needs. I have listed some examples here.
- To export failed delegate changes activities, you can execute the script as follows.
1./AuditEntraAppOperations.ps1 -Operations 'Delegation changes' -FailedOnly - To audit service principal changes of the specific app registration, use the format below.
1./AuditEntraAppOperations.ps1 -Operations 'Service Principal Changes' -AppId abcd1234-5678-efgh-9876-ijkl9012mnop - To find apps deleted with specific time range, you can run the script like below.
1./AuditEntraAppOperations.ps1 -StartDate 04/01/2025 -EndDate 04/30/2025 -Operations 'Deleted Applications'
Get a Complete Picture of Entra App Operations for Free with AdminDroid!
You’ve seen how easy it is to run our PowerShell script and get Entra app activity. But what if you could receive a detailed report of every app change directly in your inbox? just clear, ready-to-use insights delivered for quick access!
Yes, that’s exactly what AdminDroid’s free Microsoft 365 reporting tool offers! It turns complex Entra app operation details into actionable insights and allows you to schedule reports to be sent straight to your inbox automatically.
Stay on top of critical app changes with ready-made reports, including:
Entra App Change Auditing Reports
- All App Operations
- Added / Updated / Deleted Applications
- Consent to Applications
- OAuth2 Permission Grants
- App Role Assignments
- Service Principal Changes
- Credential Changes
- Delegation Changes
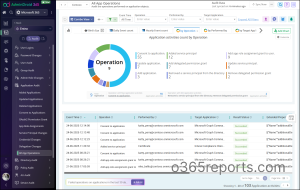
Apart from this, AdminDroid’s free Entra reporting tool offers 120+ reports and 10+ dashboards at no cost. It includes key Entra reports like users, licenses, groups, group members, login activities, password changes, license changes, and more.
And that’s not all! AdminDroid’s M365 management tool offers over 3000+ prebuilt reports and 100+ engaging dashboards, that let you audit and manage all important Microsoft 365 services. You also get full access to report customization, alerting, and exporting capabilities.
Download AdminDroid today and experience hassle-free Microsoft 365 reporting and management!
I hope this blog has been helpful in equipping you with the PowerShell script to audit Entra app operations effectively. Auditing app operations gives you control and safeguards your apps from hidden risks. For any further questions, feel free to reach out in the comments section.