Failed sign-in attempts in Microsoft 365 are often overlooked, yet they serve as crucial indicators of potential security threats. Repeated login failures can hint unauthorized access attempts, compromised accounts, or misconfigurations putting sensitive data at risk. Ignoring these signs not only disrupts the security and productivity of your organization, but also complicates the process of diagnosing sign-in issues.
Monitoring failed login attempts enables early detection of suspicious activities, helping admins identify attack patterns before they escalate. It also enhances visibility into user sign-ins and service principal sign-ins, ensuring protection for both users and applications.
In this blog, we’ll explore how to track Microsoft 365 failed login attempts, empowering you to detect anomalies quickly and maintain seamless access for your users.
How to Get All Microsoft 365 Failed Login Events?
The following are the available methods to check unsuccessful login attempts in Microsoft 365.
Microsoft Entra Admin Center: Sign in to the Microsoft Entra admin center and navigate to Identity → Monitoring & Health → Sign-in logs → Appy status filter to Failure. Here you can find the list of unsuccessful interactive sign-in events. However, you need to download separate reports for non-interactive, service principal sign-in failure events.
Unified Audit Log Search: Using the Search-UnifiedAuditLog cmdlet, you can audit failed login attempts in Microsoft 365 for up to 180 days. However, it lacks crucial details such as whether the attempts were interactive or non-interactive, MFA status, and the associated sign-in risk level. This makes comprehensive analysis challenging.
Entra Sign-in Logs: You can use the Get-MgAuditLogSignIn cmdlet in Microsoft Graph PowerShell to retrieve failed sign-in attempts. However, you need to do complex filtering to get important details about the failed login events which is time consuming and prone to error.
To make your lives easy, we’ve developed a PowerShell script that exports all failed login attempts in your Microsoft 365 environment. This includes key information such as sign-in risk, conditional access, MFA, and more.
Download Script: GetEntraFailedSignIns.ps1
Script Highlights:
- The script automatically verifies and installs the Microsoft Graph PowerShell SDK module (if not installed already) upon your confirmation.
- Generates a report that retrieves all interactive failed sign-in attempts by default.
- Enables filtering of failed attempts from the following sign-in types.
- Non-interactive user sign-ins
- Service principal sign-ins
- Managed identity sign-ins
- All type of sign-in failure events
- Allows you to export a failed login attempts report for a custom period.
- View sign-in failure events based on error code.
- Helps export failed risky sign-ins alone.
- Exports a report on guest users’ sign-in failures.
- Segments failed sign-in attempts based on MFA enforced & not enforced.
- You can export the report to choose either All users or Specific user(s).
- The script can be executed with an MFA-enabled account too.
- Exports report results as a CSV file.
- The script is scheduler friendly.
- It can be executed with certificate-based authentication (CBA) too.
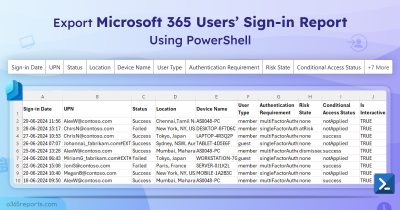
Microsoft 365 Failed Login Attempts Report – Sample Output
The exported ‘Failed Login Events Report’ looks like the screenshot below.

The script exports all failed login events in Microsoft 365 along with the following attributes:
Sign-in Date, UPN, UserName, Application Name, Resource Name, Status, Error Code, Failure Reason, User type, Ip Address, Location, Device Name, Browser, Operating System, Authentication Requirement, Conditional access status, Applied Conditional Access Policies, Risk detail, Risk state, Sign-in Id, Flagged for Review, Is Interactive, Additional Details.
Microsoft 365 Sign-in Failure Report – Script Execution Steps
- Download the script.
- Start the Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1:
Execute the script with MFA or non-MFA account.
|
1 |
./GetEntraFailedSignIns.ps1 |
Executing this script generates a comprehensive report of all interactive sign-in failure events in your Microsoft 365 tenant.
Method 2: Execute the script using certificate-based authentication.
Before you can connect Microsoft Graph PowerShell with certificate authentication, you’ll need to register the app in Entra ID. Based on your flexibility, you can obtain one from a certificate authority (CA) or create a self-signed certificate.
|
1 |
./GetEntraFailedSignIns.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <CertificateThumbprint> |
To retain data beyond the 30-day retention of Entra sign-in logs, you can schedule this script using Task Scheduler or Azure Automation to retain audit logs for a longer period.
Get Entra Sign-In Failure Report – More Use Cases
The script provides a granular Microsoft 365 login failure report with flexible filtering options. Let’s look at the scenarios where this script proves most effective.
- Export failed login events for a custom period
- Filter failed sign-ins across different sign-in types
- Identify failed risky sign-in attempts
- Track guest users’ login failures
- Retrieve MFA-failed sign-ins
- List login failures of non-MFA users
- Get failed login attempts for specific users
- Pull failed login events using error code
- Get more granular Entra login failure report
1. Export Microsoft 365 Login Failures for a Custom Period
By default, the script can retrieve data from the past 30 days. However, you can change the date range using –StartDate and –EndDate parameters.
|
1 |
./GetEntraFailedSignIns.ps1 -StartDate 2025/05/01 -EndDate 2025/05/12 |
The above script will export all users’ failed login attempts from May 01, 2025, to May 12, 2025.
Note: Date should follow the format of YYYY/MM/DD.
2. Filter Entra ID Failed Sign-Ins Across Different Sign-in Types
Entra ID supports various sign-in types, each representing a different authentication method. These include direct user access, certificate-based logins, and automated Azure resource authentications.
Monitoring failed sign-in attempts across these categories is crucial for identifying access issues. For example, frequent interactive sign-in failures might indicate user password issues, while failed service principal sign-ins could signal expired client secrets and certificates in app registration.
To filter failed sign-in events, you can use the –SignInEventType parameter.
|
1 |
./GetEntraFailedSignIns.ps1 -SignInEventType ServicePrincipalSignIns |
The above example will return all failed service principal sign-in attempts in your Microsoft 365. Here are the other supported values for –SignInEventType parameter.
- NonInteractiveSignIns → For app-based authentications without user interaction.
- ManagedIdentitySignIns → For Azure resource-linked managed identities.
- AllSignIns → For all types of sign-in failures.
3. Identify Failed Risky Sign-In Attempts in Microsoft 365
Risky sign-ins in Entra ID are login attempt flagged as suspicious due to indicators such as multiple failed logins, unfamiliar locations, impossible travel between sign-ins and more. These events indicate potential account compromises, emphasizing the importance of monitoring risky sign-in activities to detect threats early as possible.
To find these failed risky sign-in attempts, use the -RiskySignInsOnly parameter.
|
1 |
./GetEntraFailedSignIns.ps1 -RiskySignInsOnly |
This retrieves a report of all failed sign-in events that were identified as risky sign-in attempts.
4. Track Guest Users’ Login Failures in Microsoft 365
By tracking failed sign-in attempts from guest user accounts in Microsoft 365, you can identify unauthorized attempts from external collaborators or partners. It also hints at the misuse of inactive guest user accounts, helping you safeguard sensitive information.
By using the script with –GuestUserSignInsOnly parameter, you can retrieve failed sign-in attempts of guest users.
|
1 |
./GetEntraFailedSignIns.ps1 -GuestUserSignInsOnly |
The format will export all login failure events from the external users, and helps you find whether the account is blocked, attempted for brute-force or password spray attacks.
5. Retrieve MFA-Applied Sign-Ins in Entra ID
Identifying failed sign-ins from MFA-enforced users helps ensure that multi-factor authentication policies are effectively protecting your Microsoft 365 environment. Also, frequent failed attempts may indicate issues with authentication method reliability or incorrect configurations.
You can retrieve failed sign-ins from users with MFA enforced by running script with the –MFASignInsOnly parameter.
|
1 |
./GetEntraFailedSignIns.ps1 -MFASignInsOnly |
The output report helps you assess any recurring sign-in failures caused by the current MFA configuration. It enables you to plan policy adjustments to enhance security.
6. List Login Failures of Non-MFA Users in Microsoft 365
Monitoring failed sign-in attempts from users who are not protected by MFA is crucial for identifying high-risk accounts that lack an additional layer of security. These failed attempts could expose vulnerabilities, making it important to secure those accounts promptly.
Use the –NonMFASignInsOnly parameter in the script to fetch failed sign-in attempts from users without MFA.
|
1 |
./GetEntraFailedSignIns.ps1 -NonMFASignInsOnly |
This will return the failed login events of users without MFA, help you identify vulnerable users and enforce users to complete MFA to enhance security.
7. Get Failed Login Attempts for Specific Users in Entra ID
If you want to get failed sign-in attempts of multiple users, you can pass UPNs using the –UserPrincipalName parameter as comma-separated values.
|
1 |
./GetEntraFailedSignIns.ps1 -UserPrincipalName "john@contoso.com", "jones@contoso.com" |
The exported report contains login failure history of ‘john’ and ‘jones’ user.
8. Pull Failed Login Events Using Error Codes in Microsoft 365
Every failed login attempt in Microsoft 365 generates a unique error code that signifies the reason behind the failure—whether it’s due to incorrect credentials, account lockouts, or policy restrictions. Analyzing these error codes enables quicker troubleshooting and better visibility into authentication issues.
The script provides an –ErrorCode parameter that lets you specifically filter failed login events by their error code.
For example, if you want to identify all failed logins due to invalid username or password (error code 50126), you can use the format below.
|
1 |
./GetEntraFailedSignIns.ps1 -ErrorCode 50126 |
This makes isolating specific failures, detecting recurring issues, and streamlining troubleshooting easier.
9. Get More Granular Entra Login Failure Report
By default, this PowerShell script supports multiple advanced filtering options. You can use combinations of one or more filters. I have listed some use-cases here.
- To export specific user’s failed login attempts from last week, you can execute the script as follows.
1./GetEntraFailedSignIns.ps1 -StartDate 2025/05/04 -EndDate 2025/05/10 -UserPrincipalName "john@contoso.com" - To export all failed login attempts caused by sign-in attempts to sign-in blocked accounts from the past week, use the format below.
1./GetEntraFailedSignIns.ps1 -StartDate 2025/05/04 -EndDate 2025/05/10 -ErrorCode 50057
We hope this blog is useful in analyzing Microsoft 365 sign-in failure activities. If you have any queries, feel free to share them with us through the comment section.