Imagine spending your afternoon sifting through dozens of app registrations in Entra ID to determine which ones are still active, and which are relics from past projects. As an admin, you know that applications use certificates and secrets for app registrations to securely authenticate—but many of these credentials persist even after the apps they supported have been retired.
Over time, these certificates and secrets become more than just clutter—they turn into hidden liabilities. A single outdated certificate or secret could grant unintended access if exploited. In this blog, we’ll show you how to export Entra app registration certificates & secrets report to quickly identify and remove unused credentials, ultimately enhancing application security in Microsoft 365.
How to Get All Entra ID App Registrations with Certificates and Secrets?
To manage and track secrets and certificates of Entra ID apps, you can use the following approaches.
- View app registration certificates and secrets in Entra admin center
- Retrieve Entra ID app secrets and certificates via PowerShell
View Certificate and Secrets for App Registrations in Entra admin Center
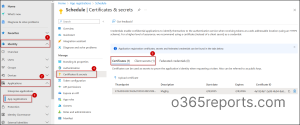
You can view all the Entra ID app registrations and their certificates and secrets in Microsoft Entra admin center by following the steps below.
- Login to the Microsoft Entra admin center.
- Navigate to All applications tab under Identity –> Applications –> App registrations.
- Click on any desired application and select the Certificates & secrets.
- Now, you can see the app’s certificates and secrets in the respective tabs.
Export App Registrations with Certificates and Secrets Using PowerShell
While manually checking every app in the Entra admin center for client secrets and certificates can be time-consuming. An alternative approach is to use the Get-MgApplication cmdlet from the Microsoft Graph PowerShell.
This cmdlet gathers details from all Entra ID apps, though you’ll still need to apply extra filters to extract the certificates and secrets. This led us to develop a PowerShell script where you can export certificates & secrets for all apps in no time and filters. This script not only simplifies the process but also provides additional insights, such as app owner name, expiry status, and days to expiry, all in one go.
Download Script: GetAppsCertificatesAndSecrets.ps1
Script Highlights:
- The script automatically verifies and installs the Microsoft Graph PowerShell SDK module (if not installed already) upon your confirmation.
- Exports certificates and secrets for all app registrations in Microsoft Entra.
- Generates a report that retrieves certificates from apps.
- Exports a report that retrieves client secrets from apps.
- Identifies applications with only active certificates or client secrets.
- Lists applications that have only expired certificates or client secrets.
- Allows to export the list of apps soon to expire client secrets and certificates (i.e., 30 days, 90 days, etc.)
- Exports the report result to CSV.
- The script can be executed with an MFA enabled account too.
- It can be executed with Certificate-based Authentication (CBA) too.
- The script is schedular-friendly.
Entra ID Application Registration Report – Sample Output
The exported ‘Apps certificates and secrets’ report looks like the screenshot below.
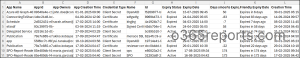
The script exports apps and their certificates & secrets along with the following attributes:
App Name, App Id, App Owners, App Creation Time, Credential Type, Certificate/Secret Name, Certificate/Secret Id, Certificate/Secret Expiry Status, Certificate/Secret Expiry Date, Days since/to Expiry, Friendly Expiry Date, Certificate/Secret Creation Time.
Entra ID Application Registration Report – Script Execution Methods
- Download the script.
- Start the Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1: Execute the script with MFA or non-MFA account
|
1 |
./GetAppsCertificatesAndSecrets.ps1 |
Executing this script generates a comprehensive report of all app registration certificates and secrets in your tenant.
Method 2: Execute the script using certificate-based authentication.
Before you can connect Microsoft Graph PowerShell with certificate authentication, you’ll need to register the app in Entra ID. Based on your flexibility, you can obtain one from a certificate authority (CA) or create a self-signed certificate.
|
1 |
./GetAppsCertificatesAndSecrets.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <CertificateThumbprint> |
You can also schedule this script using Task Scheduler or Azure Automation to periodically export Entra ID app registration report.
Get Entra Apps Certificates and Client secrets
The script provides granular Entra ID app credential reports with flexible filtering options. Let’s see the use cases that this PowerShell script solve effectively in detail.
- Get a list of Entra ID applications with certificates
- Identify all Entra ID apps with client secrets
- Export apps with expired certificates and client secrets
- Obtain apps with active certificates and client secrets
- Track down apps with certificates and secrets that are soon to expire
- Find all apps with soon to expire certificates
- Discover all apps with soon to expire client secrets
- Generate more granular app registration reports
1. Get a List of Entra ID Applications with Certificates
Certificates offer asymmetric authentication via public-key cryptography, reducing reliance on shared secrets. To retrieve a complete list of Entra ID applications that include certificates, run the script with the -CertificatesOnly parameter as shown below.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -CertificatesOnly |
This format exports details of apps that have certificates, allowing you to monitor and manage these credentials effectively.
2. Identify All Entra ID Apps with Client Secrets
Client secrets are often used in Entra apps because they’re easier to implement over certificates. If you want to retrieve details of the apps with client secrets, run the script with the -ClientSecretsOnly parameter as shown below.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ClientSecretsOnly |
The above format exports the apps’ client secrets along with their details in your Entra environment.
Tip:
You can use app management policies in Microsoft Entra to manage the client secrets of your organization’s applications. These policies include restricting password additions for applications, blocking custom passwords, restriction certificate and client secret lifetimes, and more.
3. Export Microsoft Entra Apps with Expired Certificates and Client Secrets
Failing to remove expired certificates & secrets on a regular basis can lead to an accumulation of outdated credentials, which complicates management. Therefore, run this script with the -ExpiredOnly parameter to export a report of apps with expired secrets and certificates in Entra.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ExpiredOnly |
The output will provide essential details for identifying outdated credentials and deleting expired certificates & secrets to maintain a clean environment.
4. Obtain Apps with Active Certificates and Client Secrets
App registrations with active certificates and client secrets indicate that the credentials are currently valid and in use. To filter for only those applications with active credentials, execute the script with the -ActiveOnly parameter as shown below.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ActiveOnly |
This format helps you quickly identify which certificates and client secrets are active, ensuring you focus on operational credentials.
5. Track Down Apps with Certificates and Secrets That Are Soon to Expire
Proactively monitoring credentials nearing expiration is key to preventing service interruptions and ensuring continuous operations. To identify Entra apps with expiring secrets and certificates, run the script with the –SoonToExpireInDays parameter along with the number of days.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -SoonToExpireInDays 30 |
This format exports a list of applications with certificates and
secrets expiring in 30 days, empowering you to create and add new credentials for apps to ensure seamless operations.
Handy Tip: To make it even better, you can automate Entra app credential expiry notifications that send emails to users with details of apps whose credentials will expire in n days.
6. Find All Apps with Soon to Expire Certificates
If you specifically want to focus on certificates that are approaching their expiration dates, you can run the script with both the -CertificatesOnly and –SoonToExpireInDays parameters.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -CertificatesOnly -SoonToExpireInDays 15 |
This cmdlet provides a targeted report of app registrations with
certificates expiring in 15 days, enabling you to proactively create new certificates and delete certificates nearing expiry date.
7. Discover All Apps with Soon to Expire Client Secrets
Similarly, to monitor client secrets that are nearing expiration, execute the script with the -ClientSecretsOnly and -SoonToExpireInDays parameters.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ClientSecretsOnly -SoonToExpireInDays 7 |
This cmdlet exports a detailed list of apps with
client secrets expiring in 7 days, helping you notify the owners of the app registrations in Entra. This enables them to create new client secrets and add them to the applications.
8. Generate more granular app registration reports
Apart from the above-mentioned use cases, you can also use multiple filters. Here are a few examples.
- View Entra apps with expired certificates to generate and assign new certificates to applications.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -CertificatesOnly –ExpiredOnly |
- Export apps with active certificates to plan the future renewal of the certificates.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -CertificatesOnly –ActiveOnly |
- Get Entra app registrations with expired client secrets to create a new secret as renewing client secret is currently not possible.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ClientSecretsOnly –ExpiredOnly |
- Manage client secret expiration with active client secrets report and prevent authentication failures.
|
1 |
.\GetAppsCertificatesAndSecrets.ps1 -ClientSecretsOnly –ActiveOnly |
Take Your Entra App Registration Management to the Next Level at No Cost!
We’ve explored how to manage app registrations using PowerShell scripts. But what if you could instantly get every Entra app changes with just a few clicks? AdminDroid’s free Entra ID auditing tool makes this possible – turning complex credential management into simple, with actionable insights.
This tool empowers you with detailed reports specifically designed for Microsoft Entra app and service principal management. Some of the essential app registration reports offered by AdminDroid include:
- Added Applications: Verify and validate newly registered apps in Azure AD.
- Updated Applications: Monitor modifications to existing Entra applications.
- Deleted Applications: Audit the removal of registered applications.
- Consent to Applications: Track consents granted to various applications.
- OAuth2 Permission Grants: Confirm the issuance of OAuth2 permission grants.
- App Role Assignments: Assess role assignments for users and service principals.
- Service Principal Changes: Stay updated on any changes to service principals.
- Credential Changes: Keep a record of updates to app credentials.
- Delegation Changes: Monitor shifts in authentication settings.
- All App Operations: Capture all operations performed on Entra applications.
And that’s not all— AdminDroid’s M365 management tool also offers over 1,900 ready-to-use reports and 30+ dashboards. These resources cover Microsoft 365 services such as Exchange Online, SharePoint Online, OneDrive, Teams, and more. This helps you keep your entire Microsoft 365 environment secure and compliant.
Elevate your Microsoft Entra app registration management today with AdminDroid. Download now and experience a more streamlined, secure approach to managing your Microsoft 365 environment!
We hope this blog helps you efficiently manage your Entra ID app registration credentials and prevent unexpected authentication failures. Implement it today to keep your certificates and secrets under control, and don’t hesitate to reach out in the comments if you need any clarification.