Are you concerned about sensitive data leakages, suspicious file uploads, and permission changes in your O365 tenants? If so, Office 365 auditing is the solution you are looking for and Office 365 audit logs can assist you in keeping an eye on your employees’ activities, investigating security breaches, and meeting compliance standards.
What Does the O365 Unified Audit Log Do?
An O365 unified audit log is like a self-functioning notebook that records all the activities of the Office 365 tenant and notes down whenever a new event takes place.
With the help of the audit log search tool, you can search, view, and export audit records for the required events or activities. It records users’ and admins’ activities across various Microsoft 365 services and retains them based on the Audit’s retention period.
How to Enable Office 365 Auditing?
Auditing is enabled by default if your organization uses Microsoft 365 and Office 365 Enterprise subscriptions. If it is not enabled, follow the below ways to enable Microsoft 365 auditing.
- Using Microsoft Purview Compliance Portal.
- Using PowerShell.
1. Turn on Auditing Through Office 365 Compliance Portal:
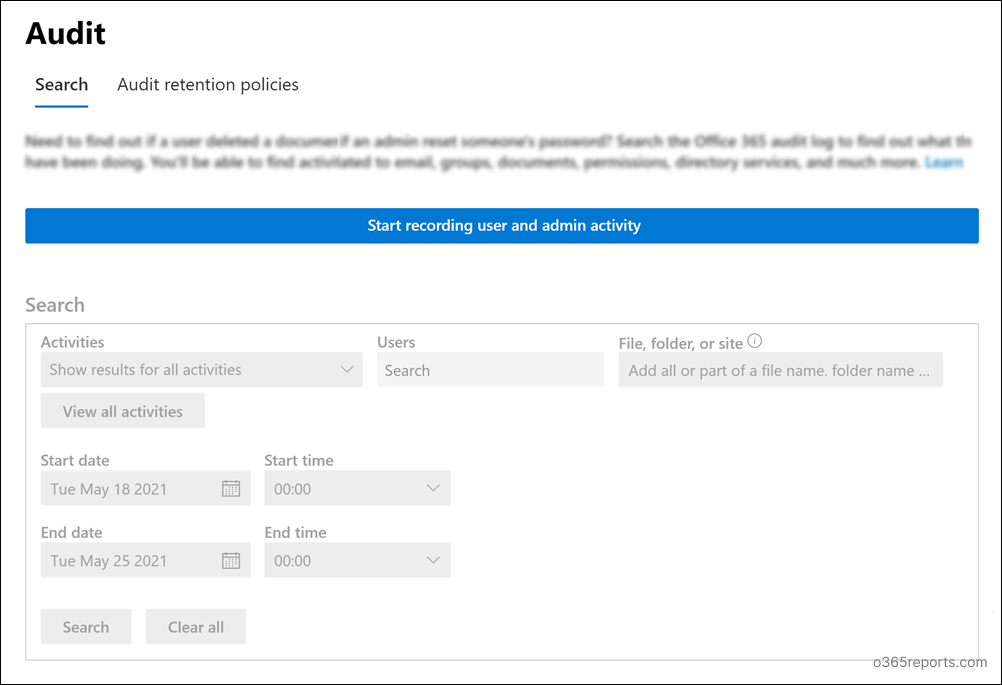
Step1: Go to Microsoft Purview Compliance Portal and then, click on “Audit” under “Solutions” from the left side of the portal.
Step2: Under the Search tab, press the “Start Recording User and admin activity” button.
2. Enable Auditing in Office 365 Using PowerShell:
You can also turn on auditing using PowerShell. This can be done as follows:
- Firstly, connect to Exchange Online PowerShell.
- Then run the following cmdlet to turn on auditing:
|
1 |
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true |
How to Search Office 365 Audit Logs?
You can search and view the Office 365 admins’ and users’ activities with the help of the audit log search using the below ways.
- Microsoft Purview Compliance Portal.
- PowerShell/Exchange Management Shell
- Office 365 Management Activity API
Method 1: Searching Office 365 Audit Logs using Compliance Center:
- Go to Microsoft Purview Compliance Portal. Then select ‘Audit’ under the ‘Solutions’ menu.
- Below the ‘Search’ tab, specify the required filters for searching unified audit logs such as date, time, users, and activity based on your requirements. Then press ‘Search’.
- If you wish, you can download the results in CSV format for documentation and other purposes.
It is very challenging for the administrators to analyze and manage the O365 environment as downloadable CSV files are burdensome and unfamiliar.
Method 2: Audit Log Search Using PowerShell:
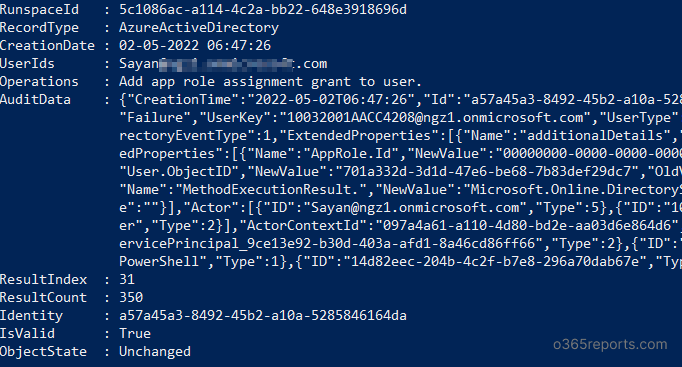
You can search Office 365 Audit logs using the Search-UnifiedAuditLog cmdlet in Exchange Online PowerShell.
This cmdlet will generate reports on activities across apps and services like Exchange Online, SharePoint, Teams, etc.
Example:
|
1 |
Search-UnifiedAuditLog -StartDate 4/27/2022 -EndDate 5/4/2022 |
It retrieves all the unified audit logs from the starting date (27th April 2022) to the ending date (4th May 2022).
Searching audit logs through PowerShell is more complex unless you have basic knowledge of PowerShell cmdlets. Also, complicated PowerShell scripts will eat up your time and peace of mind.
Method 3: Searching Audit Logs Using Office 365 Activity Management API:
Office 365 Management Activity API helps to fetch information about users, admin, system, and policy actions and events in Office 365 and Azure AD. Also, You can download all these reports in JSON format. In addition to that, admins can visualize the audit data and analyze the usage trends with the help of this tool.
The major drawback of using Office 365 Activity Management API is that it will get data only for the past 7 days while others retrieve the past 90 days of Office 365 audit data.
Limitations of Native Office 365 Audit Logs:
Although Native Office 365 Auditing provides records on all the Microsoft 365 activities, there are a few downsides of Office 365 Audit Logs. Some of them are:
- Complex to Analyze: Native audit logs are exceedingly difficult to understand for people who are unfamiliar with them. They are listed haphazardly.
- Search Filtering Options are Limited: Filtering options available for audit log search are limited. Hence, it is hard to find the relevant reports you are looking for. Also, the manual search for the desired data in the unified audit log consumes more time.
- Contains only a few Pre-Defined Reports: Admins should create the report with their desired requirements as there are only a few pre-defined reports. Also, it is not possible to create and save customized filters.
- Default Retention Period is low: By default, O365 audit data is reserved only for 90 days. To retain for a longer period, you must create Audit retention policies. Doing this is a big hassle as there are many categories of O365 activities. With expanded audit log capability, Microsoft Purview (Standard) customers can keep audit log for up to 180 days.
An Alternative to Native Office 365 Audit Logs:
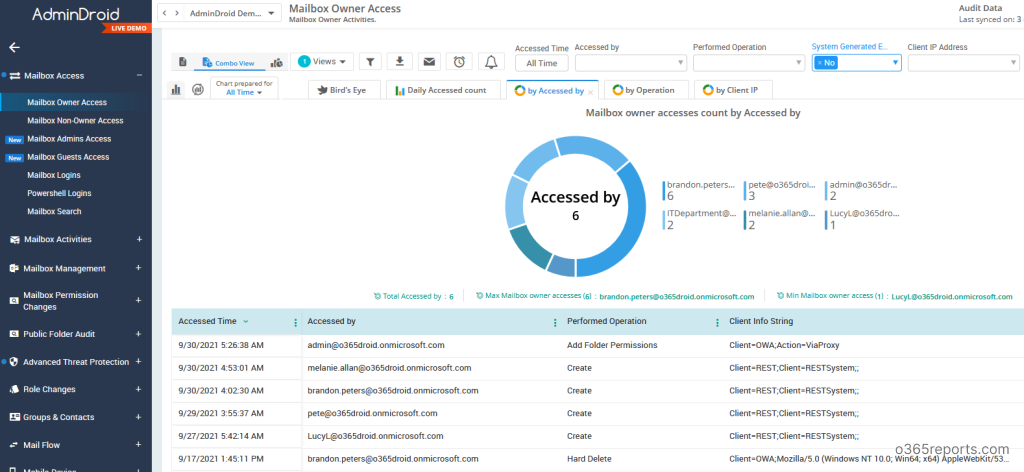
Native Office 365 auditing is becoming outdated. One of the best alternative tools for Office 365 auditing is the AdminDroid Office 365 Auditing Tool. It has 800+ pre-defined audit and analytics reports with advanced filtering options and views. AI-powered graphical analytics and Audit dashboards greatly help admins to visualize the O365 activities and gain powerful insights.
AdminDroid accumulates all the Office 365 audit data and stores it indefinitely. You can access the data anytime based on your desired time intervals.
Conclusion:
Despite its limitations, Office 365 auditing is an extremely useful feature which will help you monitor all the activities in your tenant and with the help of Office 365 audit logs, you can react accordingly to any suspicious activities in an efficient manner. You can say that it helps add a layer of transparency to your tenant and you get a proper picture of what is going on. So, if you want your Office 365 environment to be monitored properly, you can try using Office 365 auditing and audit logs.