Cyber-attacks have become very common nowadays. People are becoming prey to these attacks very often. Also, it is trouble in larger organizations where the employees are falling victim to such attacks. Phishing and malware attacks are two of the most infamous types of cyber-attacks. Phishing, in particular, has become very much prevalent and new phishing techniques coming up as time passes on. So, the employees should know about these attacks to avoid this obstacle. Here’s where Office 365 Attack Simulation Training comes in.
What Is Attack Simulation Training?
Attack Simulation Training (formerly known as Office 365 Attack Simulator) is a phish simulation tool that lets you run realistic attack scenarios in your organization. As a result, you can identify which users are vulnerable to phishing and other malicious cyberattacks. Thus, you can prevent users from new phishing attacks in your Office 365 environment.
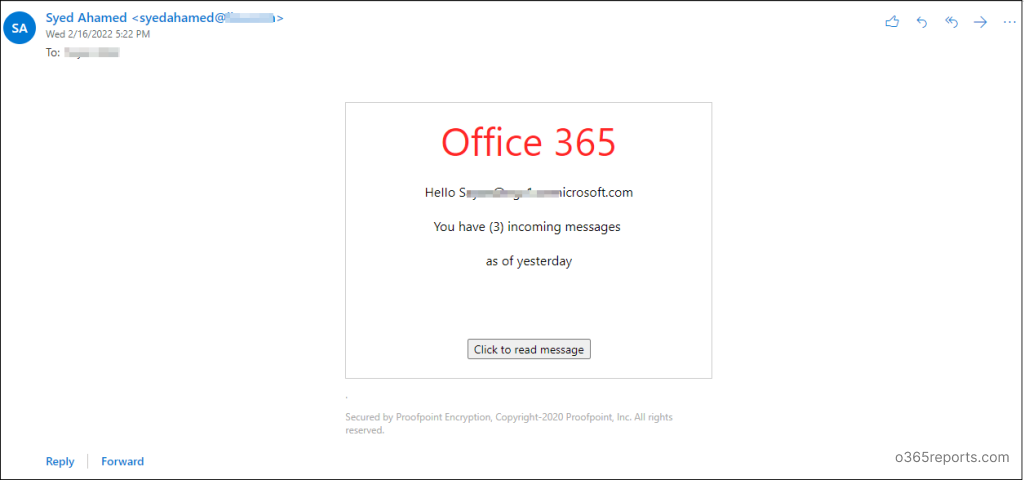
When an attack simulation is launched, the targeted users will receive an email. The email mimics a real phishing attack. There are several options available on what type of attack you want to launch.
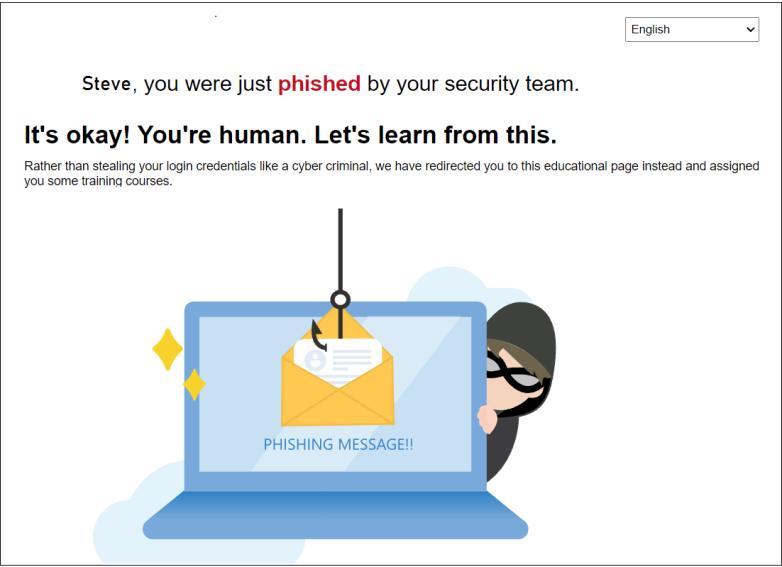
The user, on clicking the link, will get redirected to a landing page that will alert them to be aware of such attacks in the future. Then they will receive a notification email asking them to undergo training.
Requirements For Attack Simulation Training:
The following are the license and privilege requirements for running attack simulation training:
- You need to be a member of any of the following roles:
-
- Organization Management
- Security Administrator
- Your organization must have the Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2 license.
Attack Simulation Techniques:
Five social engineering/phishing techniques can be used with this simulation, based on the MITRE Attack framework. Let’s find out more about the phishing techniques below.
- Credential Harvest: In this technique, the attacker will generate a message with a URL and email it to the target recipients. When they click on it, they will be redirected to a website that asks for their personal information.
- Malware Attachment: In this case, the attacker will send a message containing a malicious attachment (which may be a pdf, word document, etc.) is sent to the recipient’s email address. In case of a real cyberattack, the attachment would contain malware that would install itself on the recipient’s device when clicked.
- Link in attachment: This is basically like a fusion of the first two methods. The attacker will send a message containing an attachment, with the malicious URL embedded inside it. The URL will then redirect the end-user to a website, similar to the one in credential harvest, which is insistent on personal information.
- Link to Malware: In this technique, the attacker creates a message, containing a malicious link to an attachment, which might be hosted on a website such as SharePoint or Dropbox. When the user clicks on the link, some arbitrary code such as a macro will execute to help the attacker install additional code on a target’s device, which might lead to the installation of malware on the device.
- Drive-by URL: The attacker sends the end-user/recipient a URL that redirects to a well-known/trustworthy website. However, the website is a clone or a compromised version of the original website.
Payload Types and Customization:
In Attack simulation training, a payload is the type of email message containing phishing messages and malicious URLs sent to users. There are different types of pre-defined payloads, with different attributes depending on the type of attack simulation technique selected. You can also create custom payloads with different attributes, such as theme, brand, event, etc. You can configure custom payloads by adding sender details, subject, and URL as per the need. Here are a few examples of pre-defined payloads:
- Facebook Password Reset
- Zoom Video Conference Invitation
- DHL shipment confirmation
- Missed mobile call
Simulation and Payload Automations:
Payload automations are used for collecting data from real phishing attacks that have taken place in your organization. You can specify the conditions to look for in these real cyberattacks like sender domain, phish technique type, specific sender name or email, etc. The attack simulation will be launched to the targeted users after the specified conditions are met.
Simulation automation work in the same way as a normal attack simulation the only difference is that you can set a schedule on when and how often you want to launch the simulation.
You can create simulation automation and payload automation using the respective tabs in the security admin center.
Steps for launching attack simulation:
- Go to the security admin center and select Attack Simulation Training from the left panel and then click launch simulation from the simulations tab.
- Select any of the available social engineering/phishing techniques.
- Name your simulation, and you may describe it if required.
- Use any of the predefined payloads or create customized payloads for attack simulation training based on your requirements.
- Select the specific users or groups or all the users for whom you wish to assign training.
- You can assign either pre-defined training given by Microsoft or your customized training plan. Set the due date for the training.
- Choose the required landing page from the given options.
- Select the preferences for the end-user notifications.
- Configure simulation launching details and ending duration.
- You can preview the simulation and check it by receiving a test email to your account.
- Launch the simulation. After launching, the respective user(s) will receive a phishing mail.
- The user, on clicking the link, will get redirected to a landing page that will alert them to be aware of such attacks in the future. Then they will receive a notification email asking them to undergo training.
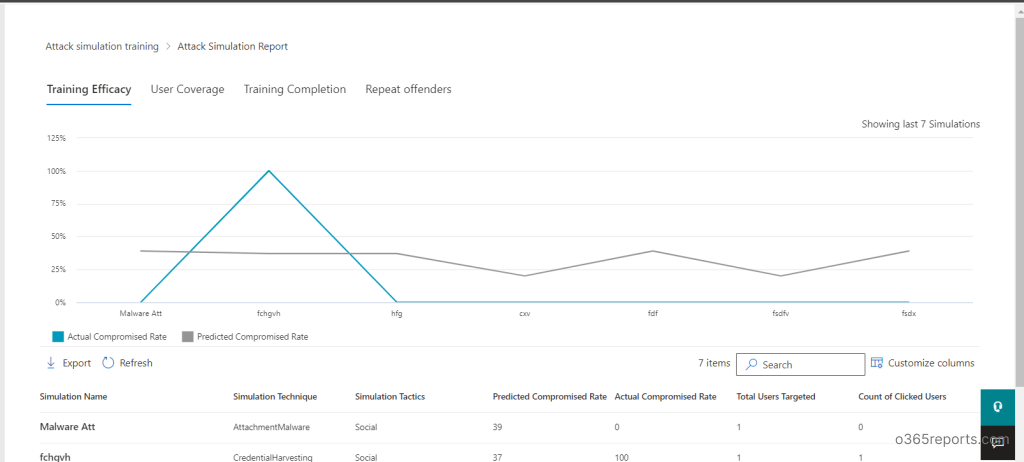
Attack Simulation Reports:
Reports provide a graphical representation of data with details like the simulation coverage, the repeat offenders, the training completion rate, and the effectiveness of the training.
Create Targeted Attack Simulation Training with Dynamic Groups
Attack Simulation Training is more effective when it’s tailored to specific user groups. Manually adding users and assigning training each time is time-consuming and inefficient. Instead, using dynamic groups allows users to be automatically added based on specific attributes, making it easier to assign relevant training.
This approach is ideal for targeting employees from different departments who face different types of threats. For example, HR might receive phishing emails with fake resumes, while support teams might receive suspicious links. Customized training helps each group handle the threats most relevant to them.
By creating targeted attack simulation training with dynamic groups, admins can automate training assignments, ensure timely delivery, and eliminate repetitive manual tasks. This hands-free, intelligent method significantly strengthens Microsoft 365 security.
Final Thoughts:
Phishing attacks have become prevalent. Hence, it is prominent for organizations to keep their employees trained regarding potential cyber-attacks. Thus, attack simulation training provides a way for organizations to set up regular drills and security checks to update their employees about these attacks and train them not to fall prey to such attacks in the future. Admins can add an external email warning tag to alert users when they receive email from an external domain. To further strengthen your defenses and fine-tune your phishing protection, follow Microsoft Secure Score recommendations for phishing.