Multi-factor Authentication (MFA) plays a vital role in securing user accounts. As the name suggests, it uses multiple methods to identify an authorized user.
You can get to know more about what is MFA, how it works and how to execute a PowerShell script with MFA enabled accounts.
MFA in Microsoft 365
To protect your Microsoft 365 environment, you need to configure MFA for both user and admin accounts. Before diving into setting up MFA in your organization, you should understand the various MFA configuration methods: Per-user MFA, Security Default, and Conditional Access Policy.
This blog focuses on the traditional per-user MFA method. There are three settings that a user account can be set to in per-user MFA:
- Disabled – MFA is not required to sign in. This is the default state for new users.
- Enabled – The user has been enrolled in multi-factor authentication but has not completed the registration process. They will be prompted to complete the process next time they log in.
- Enforced – The user has either completed the enrollment process or they have been administratively “Enforced” to use MFA. They must set up MFA to login Office 365 apps.
All users start out Disabled. When you enroll users in Azure MFA, their state changes to Enabled. When enabled users sign in and complete the registration process, their state changes to Enforced.
How to Check if MFA is Enabled in Microsoft 365 using PowerShell?
While Microsoft 365 Admin Center provides a list of users and their MFA status, it lacks essential details such as MFA activation status, registered MFA methods, MFA deployment source, MFA phone number, MFA email, license status, and admin roles, etc.
Note: If you want to view all the information with the Graphical User Interface(GUI), you can try Microsoft 365 Reporting tool by AdminDroid.
We have written a PowerShell script to export Office 365 users’ MFA status along with many useful information about the user account.
Download Script: GetMFAStatus.ps1
Update: Get MFA status report using Microsoft Graph PowerShell
Since ‘MsOnline’ and ‘AzureAD’ PowerShell modules were officially retired in Mar 2024, we have written a script to export MFA status reports using MS Graph PowerShell. With this advanced script, you can generate 7+ MFA reports with 10+ user/MFA properties. For more info, refer to: Export MFA status report using MS Graph PowerShell
Script Highlights:
- Generates reports based on MFA status.
- Result can be filtered based on Admin users.
- You can filter result to display Licensed users alone.
- You can filter result based on Sign-in Status (SignIn allowed/denied).
- The script produces different output files based on MFA status.
- The script can be executed with MFA enabled account.
- Exports result to CSV file.
-
Using the ‘Admin Roles’ column, you can find users with admin roles that are not protected with MFA. For example, you can find Global Admins without MFA.
- The script is scheduler friendly. i.e., credentials can be passed as parameter instead of saving inside the script.
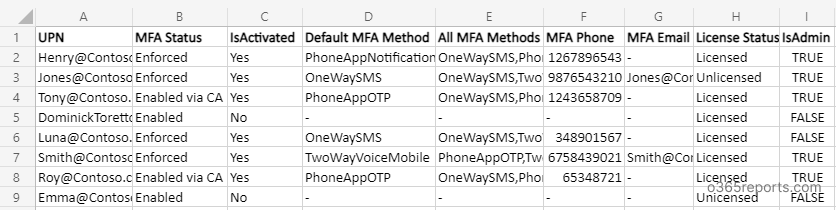
Export MFA Status Report – Sample Output:
The exported MFA status report will look similar to below screenshots.
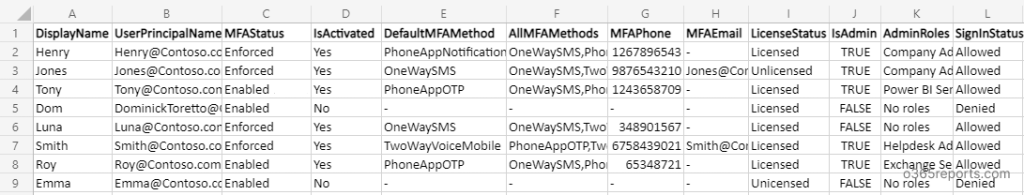
MFA enabled users report (for Enabled/Enforced users):
MFA enabled user report has the following attributes:
Display Name, User Principal Name, MFA Status, Activation Status, Default MFA Method, All MFA Methods, MFA Phone, MFA Email, License Status, IsAdmin, Admin Roles, Sign-in Status.
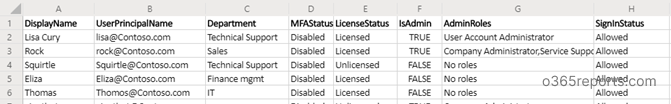
MFA disabled users Report:
MFA disabled user report has the following attributes: Display Name, User Principal Name, Department, MFA Status, License Status, Is Admin, Admin Roles, Sign-in Status.
How to Get MFA Status Report Using PowerShell?
This all-in-one PowerShell script helps you generate 10+ MFA status reports to assess your organization’s security.
|
1 |
./GetMFAStatus.ps1 |
The script will return MFA enabled and enforced users by default. If you want to list MFA disabled users, you need to use the –DisabledOnly param.
Note:
This script uses the MSOnline PowerShell module, which has been officially deprecated but will continue to work at least until July 2025. You can also use Microsoft Graph to get per-user MFA status, as Microsoft recently added support for this feature.
More Use Cases of our ‘MFA Report’
Our script supports built-in filtering capability to generate more granular MFA status report.
1. Get a Report on Users’ MFA Enabled Status:
As an Office 365 admin, often you ask ‘How to check if MFA is enabled in office 365’? The solution is here. By using –EnabledOnly param, you can export MFA enabled users to CSV file.
|
1 |
./GetMFAStatus.ps1 -EnabledOnly |
With this report, you can identify MFA enabled users and their registered authentication methods and MFA phone number.
Note: Microsoft recommends avoiding less secure authentication methods like Phone (SMS and Voice calls). If you’re looking to switch to more secure options, our pre-built PowerShell script can help you effortlessly remove Phone authentication from all users.
2. Export MFA Enforced Users Report to CSV:
Some users may enabled MFA but not enforced (registration process not completed) for MFA. You can get a list of MFA enforced users using -EnforcedOnly param.
|
1 |
./GetMFAStatus.ps1 -EnforcedOnly |
By using this report, you can identify users who have not completed the MFA registration process.
3. List Microsoft 365 Users Without MFA:
MFA provides an additional level of security to accounts. To view MFA disabled users, you can run this script with -DisabledOnly param.
|
1 |
./GetMFAStatus.ps1 -DisabledOnly |
By referring to this report, admins can enable MFA for a specific user(s) or all users. Additionally, you can use the multifactor authentication gaps workbook to spot users without MFA.
4. Export Microsoft 365 Admins Without MFA:
As admin accounts have more privileges, it requires special attention. According to a recent survey, 78% of Microsoft 365 admins don’t activate MFA for their accounts. To export all Microsoft 365 admins without multi-factor authentication, run the script using –AdminOnly param.
|
1 |
./GetMFAStatus.ps1 -AdminOnly -DisabledOnly |
The exported MFA report lists admin accounts(users) that are not protected with MFA. By referring to this report, you can enable MFA for admins to secure their accounts.
5. Export Licensed Users’ MFA Status Report
Instead of generating MFA status report for all the users, you can get MFA status for licensed users alone. You can use –LicensedUserOnly param to get licensed users’ MFA status
- To view MFA activation status for licensed users,
|
1 |
./GetMFAStatus.ps1 -LicensedUserOnly |
- To view all the licensed users who have not configured MFA,
|
1 |
./GetMFAStatus.ps1 -LicensedUserOnly -DisabledOnly |
6.Export Users’ MFA Status Based on Sign-In Status
Most organizations keep former employees’ accounts in a disabled state as part of the Microsoft 365 offboarding procedure. Therefore, we have the –SignInAllowed paramparameter to filter the MFA status report generation based on sign-in status.
- To view sign-in allowed users without MFA
|
1 |
./GetMFAStatus.ps1 -SignInAllowed $True -DisabledOnly |
- To list sign-in denied users with MFA,
|
1 |
./GetMFAStatus.ps1 -SignInAllowed $False |
Note: You can use multiple filters together to get a more granular MFA status report. For example,
- You can get a list of MFA disabled admin users whose sign-in status is allowed.
|
1 |
./GetMFAStatus.ps1 -DisabledOnly –AdminOnly –SignInAllowed $True |
7. How can I Schedule MFA Status Report?
You can scheduling the PowerShell script in the Task Scheduler to get the MFA status report periodically, . It can be achieved by explicitly mentioning the credential, as follows:
|
1 |
<Script Location>\.GetMFAStatus.ps1 -UserName <UserName> -Password <Password> |
This method will work only for non-MFA accounts. You can disable MFA for a specific account using a Conditional Access policy to make it work.
Additionally, just as you prioritize implementing MFA for users, it’s equally crucial to track the frequency of MFA prompts. Because, excessive prompting can hinder productivity and may even signal cyberattacks. Therefore, track it using the Authentication prompts analysis workbook in Entra ID.
Get More Detailed MFA Reports:
Are you tired of manually executing scripts and sending the result to email? If YES, I’d suggest you try AdminDroid Office 365 reporting tool.
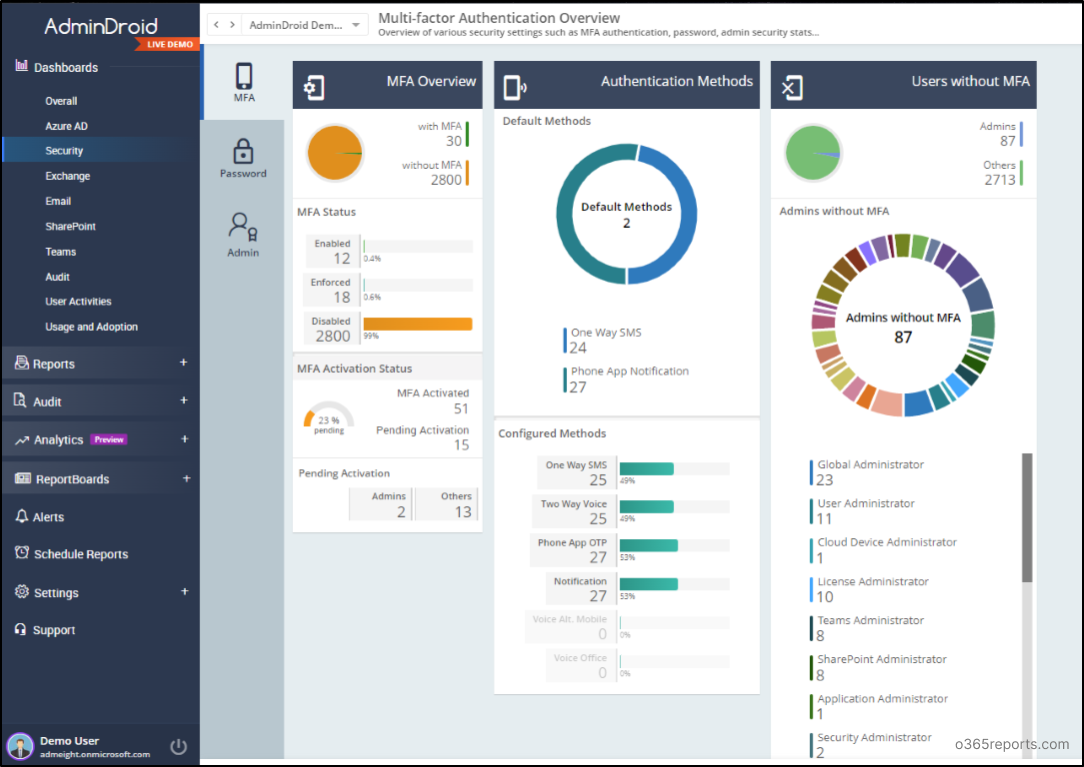
AdminDroid has a dedicated MFA dashboard and more detailed MFA reports. You can schedule these reports and send them to preferred email addresses. Additionally, you can apply filters on any columns to view only the required information. Some of the MFA report categories are:
- MFA Status
- MFA enabled users
- MFA enforced users
- MFA disabled users
- MFA Activation Status
- MFA activated users
- MFA non-activated users
- Detail of MFA authentication methods and device details
- MFA Auditing
- When MFA enabled to users
- When MFA disabled to users
- MFA Sign-in Auditing
- Sign-in attempts failed pass MFA challenge
- Sign-in successful using MFA
- Sign-in blocked by CA policy
- Sign-in allowed by CA policy
- And more
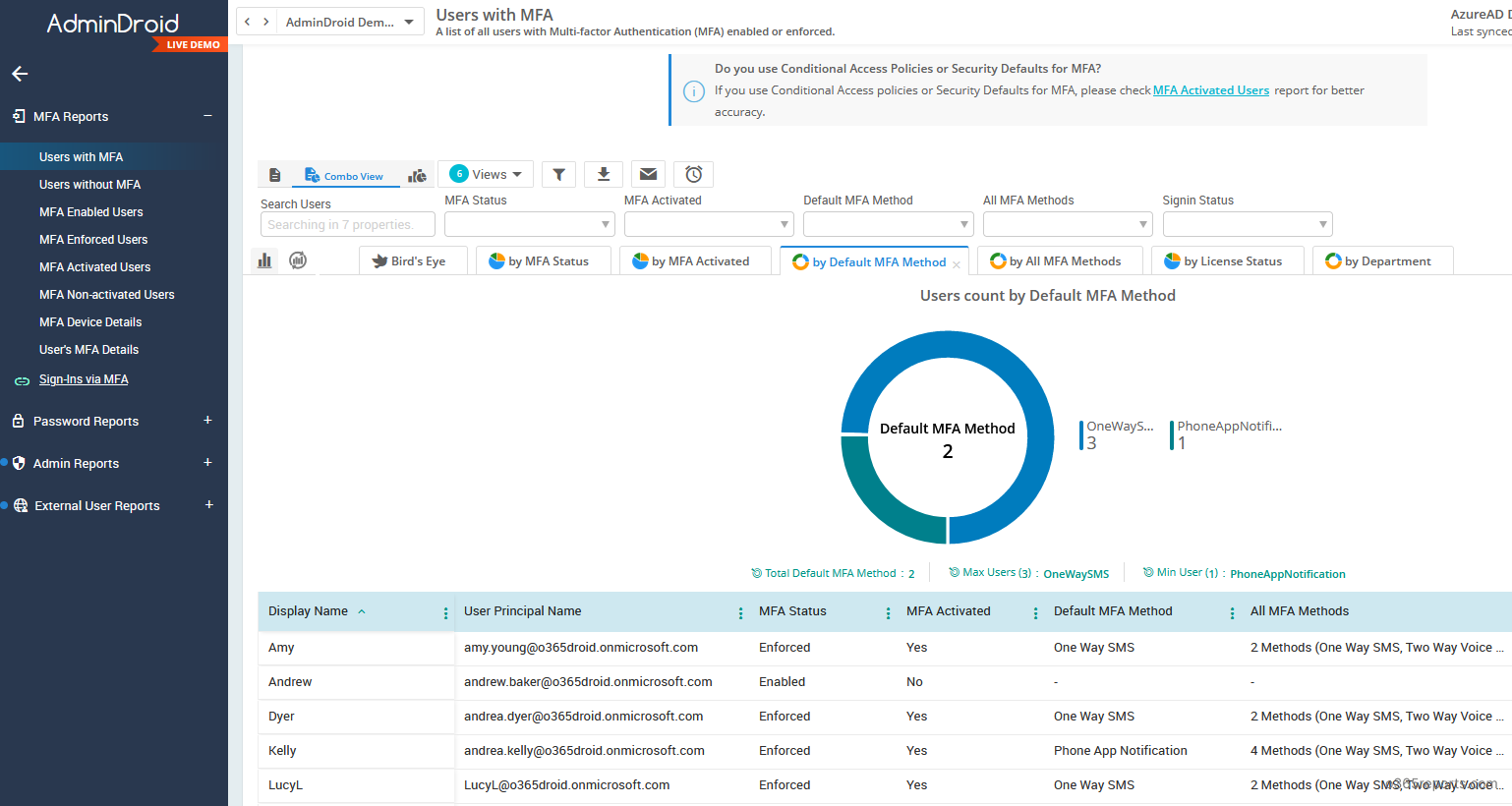
Besides, AdminDroid Offers over 120+ free reports and a handful of dashboards. It includes reports on Users, Licenses, Groups, Group Members, Devices, Login Activities, Password Changes, License Changes, and more. You can do customization, scheduling, and exporting. You can download Free Azure AD reporter and see how it helps you.
Additionally, AdminDroid provides 1800+ pre-built reports and 30+ dashboards on various Office 365 services like Azure AD, Exchange Online, SharePoint Online, Microsoft Teams, etc. For your Office 365 reporting and auditing needs, you can try Microsoft 365 reporting tool by AdminDroid and see how it helps for you.
Finally, we hope this post was helpful. If you modify the script and use it for other use cases, then please leave your idea in the comment section and help more admins.