As we move into 2026, it’s the perfect time to look back at the Microsoft 365 admin blogs that created the most impact over the past year. This curated roundup brings together a diverse range of topics, from key Microsoft 365 security updates to in-depth explorations of newly released features.
Beyond feature announcements, it also highlights practical PowerShell scripts and proven admin best practices that help streamline daily operations and strengthen tenant management. Whether you’re a Microsoft 365 administrator or simply exploring what’s new in the ecosystem, these posts deliver valuable, actionable insights worth revisiting. 🎉
Top Microsoft 365 Admin Blogs of 2025
Explore a curated roundup of 2025’s most-read Microsoft 365 admin blogs from Office 365 Reports, grouped by topic for quick access.
- Best practices for Microsoft 365 admins
- PowerShell scripts for M365 monitoring and automation
- Top configurations admins shouldn’t miss
- Administrative issues and fixes
Best Practices for Microsoft 365 Admins
Effective security is a continuous process, not a one-time task. Microsoft 365 admins can use this practical guidance to maintain control, protect data, and keep environments consistent as they scale.
1. Best Practices to Manage Large Teams in Microsoft Teams
Managing large teams in Microsoft Teams is essential for scalable collaboration, but without the right governance controls, it can quickly become chaotic. As teams grow in size, issues like uncontrolled channel creations, excessive mentions, and inconsistent team structures can reduce productivity. By applying the right best practices, such as channel moderation, app control, and naming conventions, you can reduce chaos and improve collaboration.
Explore the best practices to manage large Teams environments efficiently without compromising productivity.
2. Effective Ways to Prevent Oversharing in Microsoft 365
Microsoft 365 makes file sharing quick and convenient, but in large organizations, that convenience can easily lead to oversharing. Files may end up being accessible to more users or guests than intended, increasing the risk of data exposure. By applying the right sharing controls, access restrictions, and security policies, admins can keep collaboration productive while protecting sensitive information.
Make use of the best practices to prevent oversharing across Microsoft 365. By applying these controls, admins can drastically cut down the risk of both accidental and intentional oversharing.
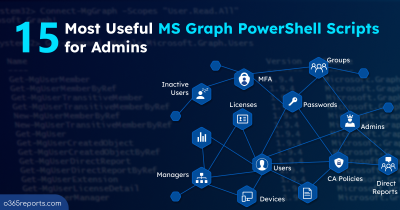
PowerShell Scripts for M365 Monitoring and Automation
Make use of our PowerShell scripts to simplify Microsoft 365 monitoring, automation, and proactive alerting.
- Security and resource optimization with timely alerts
- Identity and access monitoring
- File sharing exposure and usage governance
- Email service monitoring
Security and Resource Optimization with Timely Alerts
Reduce risk and operational overhead by automating alerts for critical security and resource events using PowerShell in Microsoft 365.
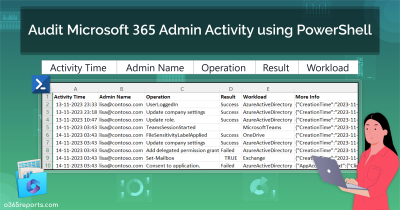
1. Send Password Expiry Notifications in Microsoft 365
Password expiration policies in Microsoft 365 help strengthen security, but they often result in unexpected user lockouts when passwords aren’t updated on time. With native Microsoft 365 solutions, there’s no simple method to get the password expiration date of the users, making timely password reminders difficult.
We’ve developed a PowerShell script that automatically sends password expiry email notifications to users until they update their passwords. The script retrieves password expiration details, notifies users in advance, and exports a detailed report.
2. Set Up Email Notifications for Application Credentials Expiry
Organizations rely on Microsoft Entra ID app registrations to support SSO, third-party integrations, and automation. These apps use client secrets and certificates for authentication, but when these credentials expire unnoticed, they can cause app failures, service disruptions, or security risks. Since there’s no built-in way to notify admins, it becomes difficult to find app registrations expiring certificates and secrets.
To make it easier, use a script that automates Entra app credentials expiry notifications to users, helping prevent outages before they occur.
3. Send Automated Microsoft 365 User Sign-in Summary Email
Monitoring user sign-ins is critical to protect privileged accounts and data in the Microsoft 365 environment. Without continuous sign-in monitoring, admins risk missing authorized access attempts, repeated failed sign-ins, etc. While the Entra admin center allows exporting raw sign-in logs, analyzing them manually can be time-consuming and overwhelming.
Instead of manually analyzing, use this script to automate daily sign-in summary emails with clear HTML insights and detailed CSV data. The reports provide key insights such as successful and failed sign-in attempts, MFA activity, and CA events, along with detailed data on external users and more.
4. Automate Alert for Break Glass Account Activity
Break glass accounts play a critical role in Microsoft 365 by providing emergency access when admins are locked out. However, because these accounts typically hold Global Administrator privileges, they are high-value targets for attackers. Relying on native monitoring options can be complex, license-dependent, or costly.
To address this, use this PS script that automates email alerts for break glass account activity. With timely alerts in place, admins can quickly detect suspicious activities and protect their most privileged accounts.
5. Audit PIM Role Activations in Microsoft Entra
In Microsoft 365, admins can temporarily elevate privileges using Privileged Identity Management (PIM). While this reduces risk, it also makes auditing role usage more important than ever. Monitoring who activates privileged roles and when they deactivate them ensures better control over sensitive access.
We’ve built a PowerShell script that automatically retrieves PIM role activation and deactivation events, exports detailed reports and delivers them straight to your inbox.
6. Find Unused Licenses in Microsoft 365
Managing Microsoft 365 licenses becomes increasingly complex as organizations grow. Licenses often remain assigned to inactive, disabled, or never-logged-in accounts, creating both cost inefficiencies and security concerns. With no native report to track unused licenses, admins are left with manual and time-consuming checks.
Check out the custom PowerShell script developed to export the unused license report in Microsoft 365. The report includes properties like number of license plans, directly assigned licenses, license assigned via groups, last successful sign-in date, inactive days, last interactive sign-in date, and more.
Identity and Access Monitoring
Gain deeper visibility into Microsoft Entra users and applications to strengthen identity security and governance.
1. Track Microsoft Entra Application Operations
Application registrations in Microsoft Entra can quietly become high-risk assets as their permissions and configurations change over time. Whether it’s granting new API permissions, updating credentials, or modifying service principals, every change can impact security if not properly tracked. While native audit logs provide essential visibility, retrieving specific operational changes often requires complex filtering and manual effort.
To get around these limitations, use the custom PowerShell script to monitor Entra app operations with ease. It also allows admins to track actions performed by specific users or actions performed on specific apps, helping pinpoint who made changes and when.
2. Get Entra User Details
Organizations with frequent onboarding and offboarding often struggle to maintain visibility over their Microsoft Entra user accounts. Without proper visibility, inactive, unmanaged, or risky users can easily go unnoticed, leading to security gaps and unnecessary license usage.
Make use of this user-friendly PowerShell script that will export 30+ Entra user reports based on various filters. These Entra user reports help streamline user lifecycle management, optimize licenses, and strengthen security by tracking guest users, sign-in status, and risky accounts.
File Sharing Exposure & Usage Governance
Microsoft 365 admins enable file sharing to support collaboration, remote work, and cross-team productivity. However, without proper monitoring, shared files can quickly become overexposed, accessed by unintended users, or remain shared long after their purpose is complete. Gain full visibility into file sharing and usage across Microsoft 365 services and maintain control over your data.
1. Remove Sharing Links in SharePoint Online
Sharing links in SharePoint Online enable collaboration, but unmanaged links, such as anonymous, never-expiring, or misconfigured shared links, create significant security risks. While the native method offers a simple way to remove shared links, it lacks scalability for larger environments.
To address the limitations of native tools, we created a PowerShell script that scans your entire SharePoint Online environment and exports all sharing link details into a CSV file. This allows admins to review and validate shared content before making any changes. After verification, the same script can be used with removal filters to bulk delete unwanted sharing links across SharePoint sites.
2. Export OneDrive Usage Report in Microsoft 365
Managing OneDrive for Business storage at scale can be challenging as the organization starts to grow. Some users accumulate large volumes of data, while others leave behind inactive OneDrive sites that continue to consume storage. Without proper monitoring, these scenarios can introduce compliance risks and operational inefficiencies.
To help administrators stay in control, use this script to export the OneDrive usage report for users in Microsoft 365. It provides detailed storage usage insights, enabling administrators to monitor utilization across all OneDrive sites without missing any data.
3. Auto-Archive Inactive Teams in Microsoft Teams
Every organization faces the challenge of managing inactive teams in Microsoft Teams once projects are completed. These unused teams in Microsoft Teams often continue to store sensitive files, conversations, and data, making effective lifecycle management essential for maintaining security and compliance. But manually tracking inactive teams and archiving them requires significant effort and is not scalable.
To simplify this process, this PS script helps to track and auto-archive inactive teams in bulk, enabling a well-governed Teams environment.
Email Service Monitoring
Improve email security and compliance by monitoring mailbox activity and external email flow. By tracking sent, received, and deleted messages, you can identify unusual patterns, detect potential phishing attempts, and prevent accidental data leaks.
1. Check Who Deleted Emails from Shared Mailbox
Shared mailboxes are widely used by teams to manage customer communications and internal collaboration. However, when multiple users can access and delete messages, it’s easy for emails to go missing. Although Microsoft Purview audit logs capture deletions, they don’t provide a way to filter specifically for shared mailbox activity, making it hard to trace who deleted what.
Use this PowerShell script to monitor shared mailbox email deletions in Microsoft 365, including soft deletes and hard deletes.
2. Identify and Block Sign-in for Shared Mailboxes in Microsoft 365
Although shared mailboxes in Microsoft 365 are created without the need for licenses or sign-in access, changes over time can unintentionally enable direct login. This often results in compliance gaps, licensing violations, and increased risk of unauthorized access.
To address this risk, execute this PowerShell script to detect sign-in enabled shared and resource mailboxes. It also covers disabling sign-in for shared mailboxes in bulk, reducing security exposure, and preventing policy violations.
3. Trace Emails Sent and Received from External Domains in Exchange Online
Email communication with external domains is unavoidable in Microsoft 365, whether it involves customers, vendors, or business partners. However, outbound and inbound emails can also become major security and compliance blind spots if they are not properly monitored. Outbound messages leaving the organization may expose sensitive data, while inbound emails from external domains are often the primary source of phishing and malware attacks
To eliminate these blind spots and strengthen email security, we have created the following dedicated PowerShell scripts to trace external email activity in Exchange Online.
Top Configurations Admins Shouldn’t Miss
Discover must-know Microsoft 365 configurations that help admins close security gaps and stay ahead of changes.
1. Restore Deleted Conditional Access Policy in Entra ID
Conditional Access policies are a core pillar of Microsoft Entra ID security, controlling access to applications based on identity, device, and risk conditions. However, accidental deletions of these policies can quickly create security gaps or disrupt user access across the organization. Until recently, such deletions were permanent and difficult to recover.
Microsoft has now brought the ability to restore Conditional Access policies in Microsoft Entra. Admins can safely retain the deleted CA policies using Entra admin center, Graph Explorer, or PowerShell within the first 30 days.
2. Create Prompt Policy to Protect GenAI Apps in Microsoft 365
As organizations increasingly rely on generative AI, securing AI interactions has become just as important as protecting identities and applications. However, this rapid adoption has introduced new attack vectors, with prompt injection emerging as one of the most critical risks to AI security. To defend against such threats, Microsoft introduced prompt policies in Entra ID.
Learn how to create a prompt policy to block malicious prompts in Gen AI apps. By implementing prompt policies, suspicious input can be filtered before it reaches the AI, reducing the risk of data leakage, manipulation, or misuse.
3. Set Up Email Addressing to Redirect Unlicensed Admin Emails
Many organizations keep Microsoft 365 administrative accounts unlicensed as a security best practice. However, this also means that those unlicensed accounts cannot receive emails, including critical alerts and system notifications. Plus Addressing offers a simple solution by allowing emails intended for unlicensed admin accounts to be dynamically routed to a licensed mailbox using tagged addresses (e.g., admin+alerts@domain.com).
Discover how to set up plus addressing in Exchange Online and why it’s ideal for unlicensed admin accounts.
Administrative Issues and Fixes
Managing Microsoft 365 comes with its fair share of challenges, as unexpected glitches, service disruptions, and security concerns can impact productivity and create extra work for admins. Address common Microsoft 365 issues with practical fixes, clear diagnostics, and step-by-step guidance to restore stability and reduce admin overhead.
1. Fix Teams Client Issues with the Client Health Dashboard
Many organizations face challenges with the Teams desktop client, including app crashes, failed launches, outdated versions, and performance inconsistencies. The Teams Client Health Dashboard in Microsoft Teams admin center addresses these issues by giving admins clear visibility into client version adoption, device health, and reported problems. With detailed insights, remote log collection, and actionable recommendations, admins can quickly identify the root cause of issues.
Get insights on how to fix Teams client issues with the client health dashboard, improving user experience, and reducing support requests.
2. Resolve Email Bounces in Microsoft 365
Email bounces in Microsoft 365 can disrupt communication and create confusion, especially when the underlying cause is not immediately apparent. Each bounce comes with a specific error code, which provides crucial clues about why a message failed to reach its intended recipient. Understanding these codes and the type of bounce, whether temporary or permanent, is essential for quickly resolving delivery issues.
To help administrators maintain smooth email operations, we have listed step-by-step guidance on how to resolve email bounces for specific error codes, addressing common bounces.
3. Remediate Illicit Grant Consent Attacks in Microsoft 365
An illicit consent grant attack happens when a user unknowingly approves an OAuth request from a malicious application. Even though no credentials are compromised, the app gains persistent access to Microsoft 365 data.
In such cases, admins must detect and remediate attacks by auditing user consent grants and monitoring suspicious activity. To help you with that, we have compiled actionable steps to remediate illicit consent grants and prevent them in the future.
As we wrap up our 2025 recap of Microsoft 365 admin blogs, these top insights highlight the strategies and learnings that will carry forward into 2026. Your support and feedback inspire us to keep delivering content that helps admins stay ahead.
Get ready for 2026 with updates on Microsoft 365 features, security enhancements, and practical guidance. Don’t forget to explore o365reports.com and share your thoughts in the comments.
🎈 Here’s to another year of collaboration and discovery. Thank you for being part of our journey!