Each organization registers applications in Microsoft Entra ID for various purposes, such as integrating third-party services, enabling Single Sign-On (SSO), or automating business processes. To ensure these applications function smoothly, they require credentials like client secrets or certificates, which are used to obtain access tokens and access organizational resources. These credentials are typically set to expire after a defined period. If left unnoticed, expired credentials can lead to application downtime, service disruptions, or even security vulnerabilities.
For instance, imagine an automation service that relies on a client secret for periodic access to Microsoft Graph. If the secret expires without notice, the automation will fail, potentially causing delays in critical business processes.
Therefore, it is essential to be proactive about app credential expiry and take timely action to renew or replace them. In this blog, let’s explore how to automate Entra app credential expiry notifications to users via email, so you can stay ahead of these issues.
How to Configure Email Reminders for App Credential Expiry Using PowerShell
While you can track Microsoft Entra apps with expiring credentials, there isn’t a direct way to automatically send expiry notifications to admins. This gap could lead to situations where users are caught off guard by expired credentials, risking app failures.
That’s why we developed a PowerShell script that automates the process of notifying users about apps with expiring credentials. The script tracks all app registrations with credentials and identifies the ones with expirations within the specified time. It then sends email alerts about the upcoming credential expirations, giving users the opportunity to take action before any issues arise.
Script highlights
- Sends Entra app credential expiry notifications to specific users.
- Sends notifications for expiring certificates alone, client secrets alone, or both.
- Exports a list of apps with expiring credentials within the specified days in CSV format.
- Allows sending emails on behalf of other users.
- Automatically installs the Microsoft Graph PowerShell module (if not installed already) upon your confirmation.
- The script can be executed with MFA and non-MFA accounts.
- It can be executed with certificate-based authentication (CBA) too.
- The script is scheduler-friendly.
Download Script: AppCertsAndSecretsExpiryNotification.ps1
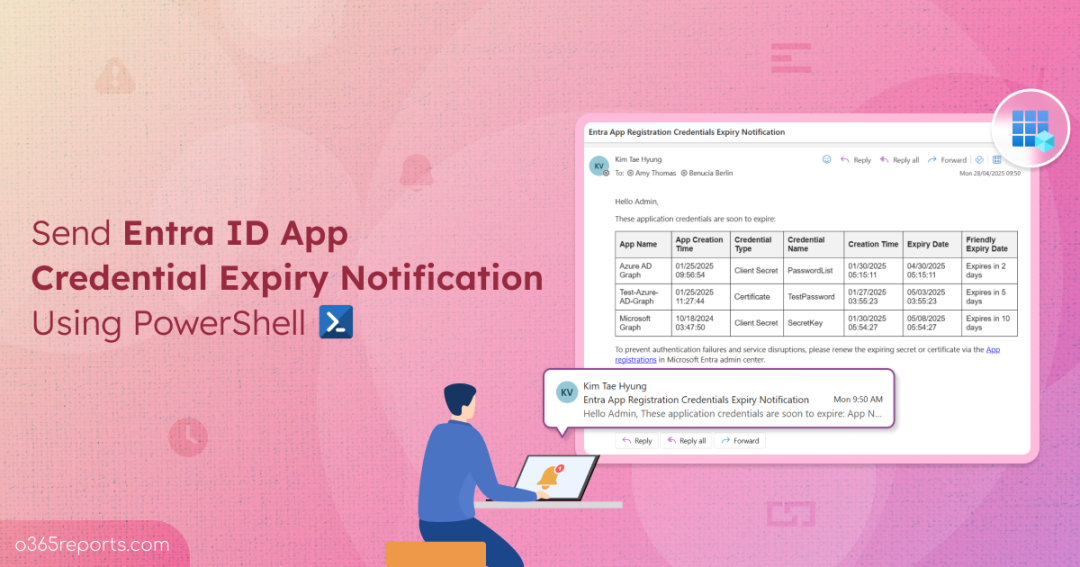
Entra App Credential Expiry Notification – Sample Output
The credential expiry notification email looks like the screenshot below.
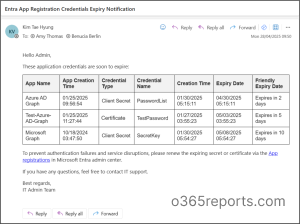
The user will receive an email, as shown above, detailing all applications with expiring credentials within the specified time frame. From the email, they can be redirected to the app registration page in the Microsoft Entra Admin Center, where they can remove the expiring app credential and create a new one.
Send App Credentials Expiry notifications in Microsoft 365 – Script Execution Steps
Follow the steps below to set up email alerts for expiring credentials of Entra ID-registered apps in Microsoft 365 using the PowerShell script.
- Download the script
- Start Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1:
Execute the script with an MFA or non-MFA account.
This script sends an email to the specified users with details of apps whose credentials will expire within the specified days.
|
1 |
.\AppCertsAndSecretsExpiryNotification.ps1 -SoonToExpireInDays 10 -Recipients 'amy@contoso.com, benucia@contoso.com' |
The above format sends email alerts to the mailboxes of Amy and Benucia. The email contains a list of application names whose credentials are set to expire within the next 10 days, along with details such as App Name, Credential Type (Client Secret or Certificate), Credential Name, Credential Creation Time, and Credential Expiry Date.
Note: The email notification is sent only when the script is executed, so you need to run it manually each time to notify users about upcoming credential expirations.
Method 2: Execute the script using certificate-based authentication.
To use certificate-based authentication, you must register an app in Entra ID, which helps you connect Microsoft Graph PowerShell. Depending on your needs, you can choose to use a certificate authority (CA) or create a self-signed certificate.
|
1 |
.\AppCertsAndSecretsExpiryNotification.ps1 -SoonToExpireInDays 10 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <CertificateThumbprint> -FromAddress jack@contoso.com -Recipients ‘amy@contoso.com’ |
This format sends a notification from the mailbox of “Jack” to the user “Amy.”
Note: The FromAddress parameter is mandatory when executing the script using certificate-based authentication.
Automate Sending Notifications for Client Secret/ Certificate Expiry
As mentioned earlier, this script only sends an email at the time of execution. To automate Entra app credential expiry notifications, you can schedule the script using Task Scheduler and alert admins periodically.
Follow the steps below to automate the execution of the PowerShell script with Task Scheduler:
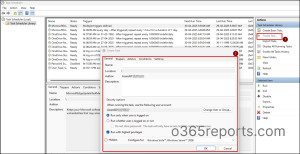
- Open Task Scheduler and click “Create Task…” under the Task Scheduler Library section in the Actions pane.
- Enter a task Name and Description in the respective fields.
- Set the following option in the Security options.
- Choose the user account under which the task should run.
- To run the task even when the user is not logged in, select Run whether user is logged on or not.
- To allow interactive execution, choose Run only when user is logged on.
- Check the Run with highest privileges option.
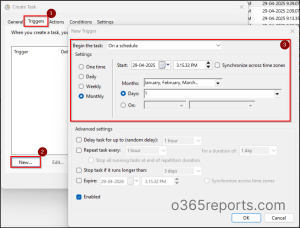
- Go to Triggers tab, click New…, and choose the following settings in the New Trigger window.
- Set “Begin the task” to On a schedule and choose Monthly under Settings.
- Choose <Select all months> from the Months drop-down and pick the 1st day from the Days drop-down.
- Set the Advanced Settings as per your requirements and click OK.
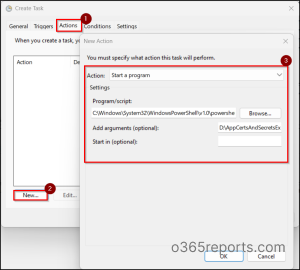
- Then, go to the Actions tab and click “New…” to open the New Action dialog.
- Select Start a Program in the Action field.
- In the “Program/script” field, click Browse and select the ‘PowerShell.exe’ from the following location.
1C:\Windows\System32\WindowsPowerShell\v1.0\PowerShell.exe - In the Add arguments(optional) text box, enter the following format to schedule the script using certificate-based authentication.
1<ScriptPath>\AppCertsAndSecretsExpiryNotification.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -SoonToExpireInDays 30 -FromAddress jack@contoso.com -Recipients ‘amy@contoso.com, benucia@contoso.com’
- Then, configure any other conditions in Task Scheduler based on your organization’s needs and click OK to finish the creation of the scheduled task.
Once scheduled, the above format will automatically run at the 1st of every month and send Entra app credential expiry notifications to recipients like Amy and Benucia, listing app with credentials expire in the month.
Handy Tip: You can also schedule the script using Azure Automation.
Tailor the Script to Fit Your Requirements
This script is developed with multiple filters to satisfy your specific requirements. Here are the specific use cases the script can handle.
- Send notifications for expiring certificates for Entra ID apps
- Send alerts on applications’ client secret expiry
- Export reports for apps with expiring credentials
- Send credential expiry notifications from a specific email address
1. Send Notifications for Expiring Certificates for Entra ID Apps Registration
If your organization relies heavily on certificate-based authentication and you want to send notifications only for expiring certificates, you can schedule the script with -CertificatesOnly parameter.
Schedule the script using the below format to setup email alerts notification for certificate expiry.
|
1 |
<ScriptPath>\AppCertsAndSecretsExpiryNotification.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -SoonToExpireInDays 7 -FromAddress jack@contoso.com -CertificatesOnly -Recipients ‘amy@contoso.com, benucia@contoso.com' |
This format automates the expiry email notification to the recipients Amy and Benucia, notifying them about the apps with certificates set to expire within the next 7 days. You can schedule the script to run on every Sunday to get all app registrations with certificate expire in the week.
2. Send Alerts on Applications’ Client Secret Expiry
Just like the previous scenario, if you want to notify users about only the apps with expiring client secrets, you can use the -ClientSecretsOnly parameter.
Use the below format to automate sending email notification for client secret expiry.
|
1 |
<ScriptPath>\AppCertsAndSecretsExpiryNotification.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -SoonToExpireInDays 30 -FromAddress jack@contoso.com -ClientSecretsOnly -Recipients ‘amy@contoso.com, benucia@contoso.com' |
This command sends an email to the specified users with details of the apps and their client secrets that are set to expire in 30 days. Schedule the script to run on first day of every month to identify the credential that expire within the month.
Tip: You can manage the client secrets of an application using the Microsoft Entra app management policies.
3. Export Reports for Apps with Expiring Credentials
While running the script, it only sends email about credential expiry to users and doesn’t export or store the respective report locally on your machine. You can run the script with the -StoreReportLocally parameter to export the apps with expiring credentials report locally.
|
1 |
<ScriptPath>\AppCertsAndSecretsExpiryNotification.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <Certthumbprint> -SoonToExpireInDays 20 -FromAddress jack@contoso.com -Recipients 'amy@contoso.com, benucia@contoso.com' -StoreReportLocally |

This format sends notifications for app registrations with credentials expiring in 20 days to the specified users and stores a report in the working directory. The exported app registered with expiring credentials report contains details such as App Name, App Owner, Credential Type, Credential Name, Credential ID, Expiry Date, Days To Expiry, App Creation Time, Credential Creation Time, and App ID.
4. Send Credential Expiry Notifications From a Specific Email Address
While running the script interactively, the script sends notifications from the user account that is logged into the Microsoft Graph module while running the script interactively. However, there may be situations where you need to send the emails from a different user’s mailbox.
Instead of providing credentials to the user running the PowerShell script, you can use the -FromAddress parameter and send the expiry notifications from another mailbox.
|
1 |
.\AppCertsAndSecretsExpiryNotification.ps1 -SoonToExpireInDays 30 -FromAddress jack@contoso.com -Recipients ‘amy@contoso.com, benucia@contoso.com' |
The above format sends the notifications from the mailbox “Jack” no matter who run the script.
Note: The user running the script must have “Send As” and “Full Access” permissions on the mailbox of the user from whom the email is being sent.
We hope this blog has provided you with valuable insights on setting up email notifications for Microsoft Entra app credential expirations. Feel free to drop your questions or share your thoughts about the script in the comments section below. We’re happy to help!