Break glass accounts in Microsoft 365 are used for emergency access when admin accounts get locked out. 🔒 But since they hold global admin privileges, they’re a prime target for attackers.
Imagine an attacker target one of these? If it happens, it can pose a serious risk like account compromise, phishing attack, MFA fatigue, and other potential security threats. 🚫
That’s why one of the best practices to safeguard break glass accounts is to regularly monitor their activities. While manual setup is an option, Microsoft Defender’s alert policies involve multiple configuration steps that make the process tedious, and they also require a ‘Defender for Endpoint Plan 1’ license. Azure Log Analytics could help as well, but it requires a subscription and comes with added costs.
So, we have written a PowerShell script for sending automated email alert on break glass account sign-in activities. It’s simple, cost-effective, and helps secure your most sensitive accounts without additional overhead.
How to Automate Alert for Break Glass Account Activity Using PowerShell:
To get started, download the script given below:
Download Script:BreakGlassAccountActivityAlert.ps1
Once you’ve downloaded the script, it’s time to automate the monitoring process using Windows Task Scheduler.
Let’s create a scheduled task that runs the script every 2 hours, automatically retrieving the latest break glass account sign-in activities and send alert to the specified recipient.
💡 Want to customize the schedule or time range? Just let us know. We’ll help you tweak the script as needed.
Send Sign-in Alert for Break Glass Account Activity using Task Scheduler
Before scheduling the task, make sure the following prerequisites are met to ensure successful execution.
Pre-requisites:
- First, you must need to register an application in Microsoft Entra ID for certificate-based authentication. This registration allows secure connection to Exchange Online using a certificate.
- Make sure to grant the following API permissions to the app:
- Microsoft Graph: Application.Read.All, Mail.Send.Shared, User.Read.All
- Office 365 Exchange Online: Exchange.ManageAsApp
- And then, depending on your organization’s policy, you can either use a self-signed certificate, or a certificate issued by a Certificate Authority (CA).
Once all these configurations are in place, you’re ready to schedule the task. Here’s how to do it:
- Create a new task in Task Scheduler
- Choose when the script should run
- Schedule the script with necessary parameters
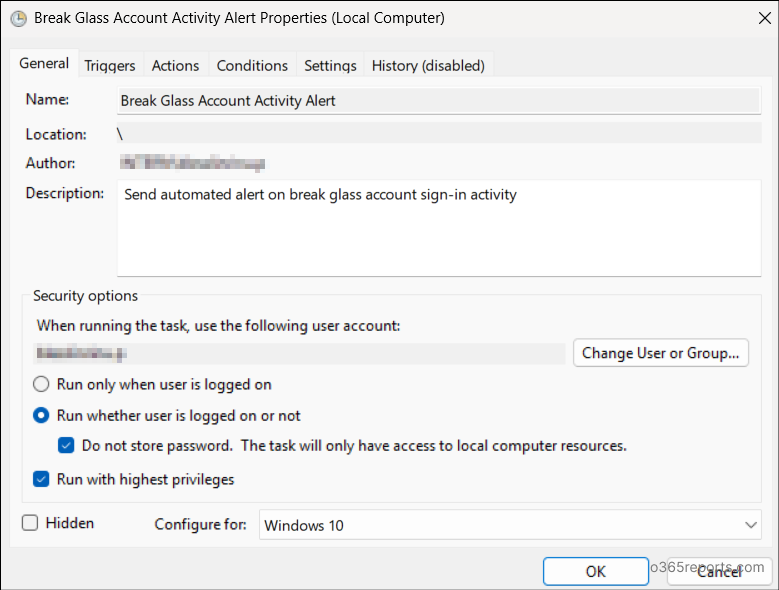
1. Create a New Task in Task Scheduler
- Open the Task Scheduler and click the Create Task. Enter a name and add description.
- Choose Run whether the user is logged on or not to run the script non-interactively. This executes the task in the background without requiring user login.
- Check Run with highest privileges to elevate the task’s priority.
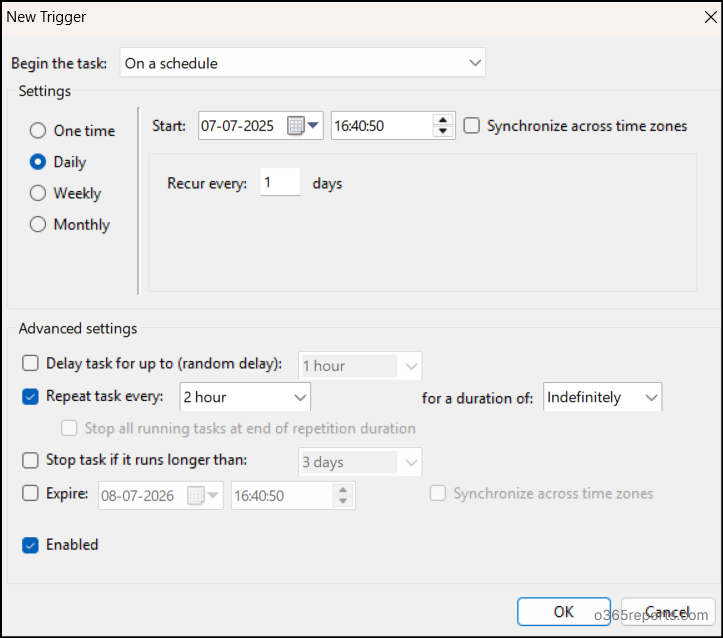
2. Choose When the Script Should Run
Once the task is created in the General tab, switch to the Triggers to define the conditions when the task should run.
- Set the trigger frequency to Daily, choose the Start date and time, and set it to Recur every 1 day.
- Under advanced settings, set Repeat task every to 2 hours and Duration to Indefinitely.
- Finally, Check the Enabled box, and click OK to save.
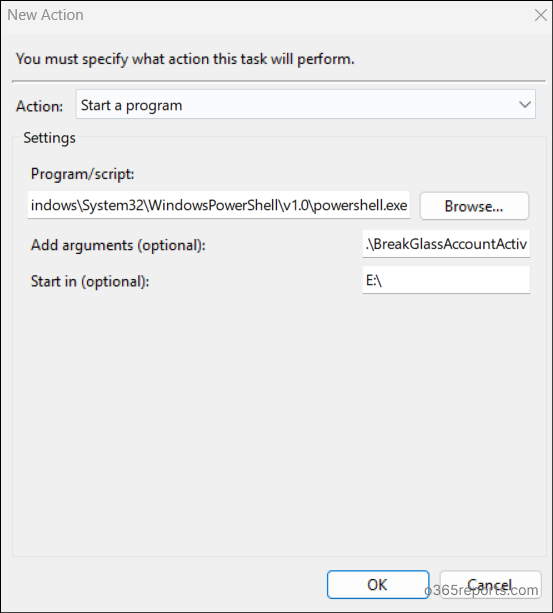
3. Schedule the Script with Necessary Parameters
Once the trigger of the break glass account activity is set, switch to the Actions tab to execute the script.
- In the Program/Script textbox, you can use the following path to locate to the PowerShell:
1C:\Windows\System32\WindowsPowerShell\v1.0\PowerShell.exe - To ensure the PowerShell script runs unattended, you need to add the required arguments in the Add arguments field. Here’s an example:
1<FolderPath>BreakGlassAccountActivity.ps1 -StartDate (get-date).addminutes(-120) -EndDate (Get-date) -bgAccountUPNs "abc@contoso.com,xyz@contoso.com" -Recipients "Admin@contoso.com,admin1@contoso.com" -$HideSummaryAtEnd -TenantId<TenanatId> -ClientId<ClientId> -CertificateThumbprint<CertificateThumbprint> -Organization<DomainName> -FronAddress<FromAddress>
Replace <FolderPath> with the actual path to your script to directly navigate to the correct directory. Here is the breakdown for the specified parameters:
- StartDate – Specifies the start time for collecting break glass account activity logs. In this example, it retrieves activity from the past 2 hours.
- EndDate – Defines the end time for the audit data collection. Here, it’s set to the current time when the script is run (i.e., the scheduled execution time).
- bgAccountUPNs – Provide one or more break glass account UPNs (comma-separated).
- Recipients – Specify one or more email addresses (comma-separated) to receive the break glass account sign-in activity alert.
- ClientId – The Application (Client) ID registered in Entra.
- CertificateThumbprint – Certificate thumbprint from the properties of the registered app.
- Organization – Your Microsoft 365 tenant name (e.g., contoso.com).
- FromAddress – Email address that will appear as the sender in the alert emails.
Ensure that the system remains powered on 24/7 and continuously connected to the internet to enable uninterrupted execution of the script.
Next, you can optionally make additional changes under the Settings tab. If no further changes are needed, simply click OK to complete the task scheduling process.
Handy Tip: You can also use Azure Automation to schedule the PowerShell script as an alternative method to create automated alerts for break glass account sign-in monitoring.
What You’ll Receive: Break Glass Account Activity Alert Email
Now that the script is scheduled, monitoring break glass account activities is fully automated.
As mentioned earlier, the script will run every 2 hours, monitor break glass account sign-in activities and send automated email alerts to the specified recipient. Note that, if there is no activity during a run, no email will be sent.
Below is a sample email alert generated for a break glass account with recent activity:
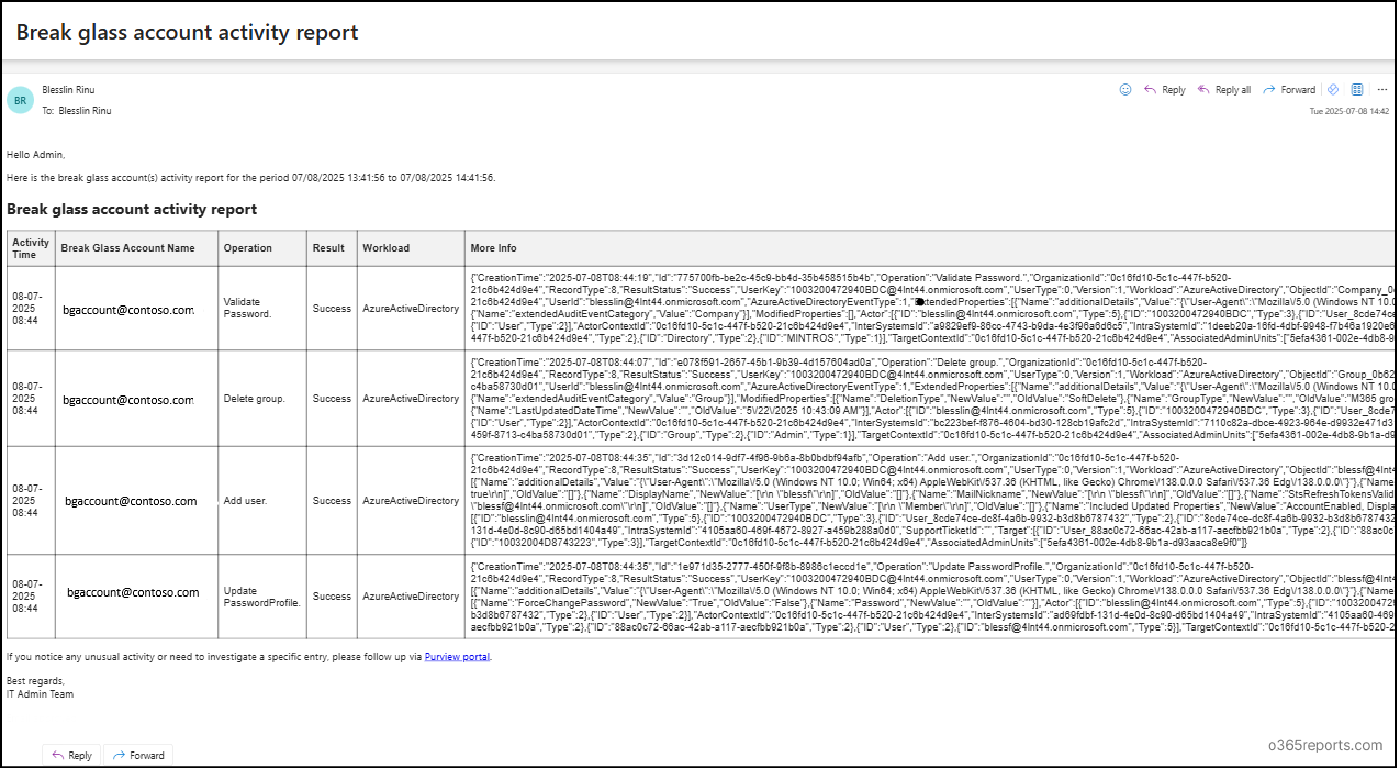
In addition to sending email alerts, the script also exports the output in both CSV and HTML formats and stores in the current working directory. This makes it easy to keep a record and regularly review break glass account activities.
It’s strongly recommended to test your break glass accounts at least every six months to verify they work as expected and can sign in without any disruptions.
To further enhance your safety net, consider creating a break glass application that serves as a reliable fallback when user-based recovery methods fail.
Automated Alerts Made Simple with AdminDroid!
Monitoring break glass account activities is critical to maintaining the integrity and security of your Microsoft 365 environment. With AdminDroid Microsoft 365 alerting tool, you can create automated alerts effortlessly. No PowerShell! No manual scheduling!
Use the ready-to-deploy alert policy templates to monitor break glass account sign-ins in a few clicks. Just pick the Break Glass Account Sign-ins template, enter the break glass account name, and you’re all set.
- You’ll receive an email whenever there’s activity from the break glass account.
- Need Teams alerts instead? You can configure that too.
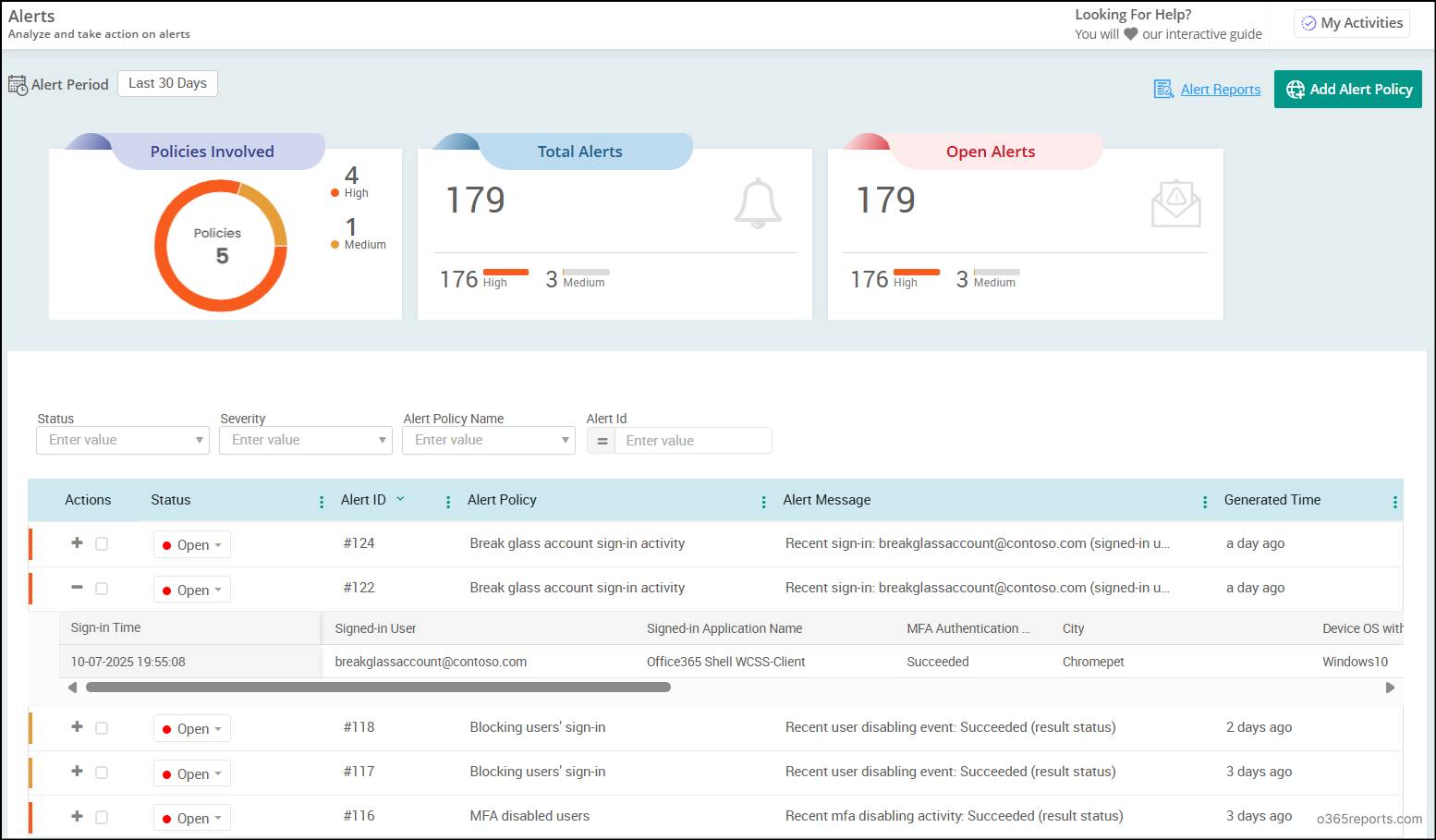
Additionally, AdminDroid provides 80+ ready-to-use alert policies and supports alerts on 1,400+ critical activities across your Microsoft 365 environment.
Download AdminDroid today to start receiving instant alerts on what truly matters.
Wrapping Up
With this blog, we hope you’re now better equipped to schedule and send automated email alerts for break glass account activity using Task Scheduler. If you have any questions or need further assistance, feel free to drop them in the comments section.
Stay tuned for more helpful PowerShell script blogs and security automation tips!