Microsoft 365 accounts are among the most common targets for attackers. Just one compromised identity can expose access to sensitive emails, files, Teams chats, SharePoint content, and much more.
As attack methods grow more sophisticated, including phishing, password spray attacks, token theft, and MFA fatigue, it’s critical to respond quickly before the damage spreads.
In this blog, we’ll look at the key practices to remediate compromised accounts in Microsoft 365. We’ll also explore methods to help you respond effectively and protect your environment.
Best Practices to Remediate a Compromised Account in Microsoft 365:
Trace Session ID–based user activity to map every action performed during the compromise. This investigation provides full visibility into what the attacker did. Based on your findings, follow the best practices to contain the breach, secure the account, and prevent further spread across Microsoft 365:
- Disable the user account
- Force sign-out from all active sessions
- Reset the password
- Review configured MFA methods
- Disable inbox rules
- Review email forwarding configuration
- Remove unauthorized email forwarding
- Monitor compromised user activities for last N days
How to Automate Compromised Account Remediation in Microsoft 365?
Explore the full range of actions that can be implemented to restrict access to compromised user accounts below:
- Recover compromised accounts using admin centers (Manual Method)
- Automate Microsoft 365 compromised account remediation using PowerShell (Recommended)
1. Recover Compromised Accounts Using Admin Centers:
Once a compromised Entra account is identified, the next step is to take immediate action to block unauthorized access and limit potential damage.
As a Global Administrator, you can use the Microsoft Entra Admin Center to disable the user account, revoke all active sessions, and reset the password. These actions ensure that the attacker is blocked from performing further malicious activities through the compromised account.
In addition, it’s important to investigate signs of mailbox abuse, such as unauthorized inbox rules or automatic forwarding configurations, which could lead to data exfiltration.
It’s also essential to monitor the actions performed by the compromised account. This helps assess the extent of the damage and provides insight into what the attacker attempted or accomplished.
You can follow the manual process described above to secure compromised accounts. However, it often involves switching between multiple portals such as Microsoft Entra Admin Center, Exchange Admin Center, and Microsoft Purview, which can be time-consuming and error prone.
To simplify the response, we’ve created a PowerShell script that automates key steps in compromised account remediation.
2. Automate Microsoft 365 Compromised Account Remediation Using PowerShell
The PowerShell script automates 8 essential best practices for remediating a compromised Microsoft 365 account, helping you respond quickly and consistently.
Download Script: AutomateCompromisedAccountRemediation.ps1
Script Highlights
- Automates 8 best practices of compromised user remediation.
- Automatically installs required PowerShell modules MS Graph and Exchange Online PowerShell (if not installed already) upon your confirmation.
- Export the detailed log file on actions performed and their status (success or failure).
- Supports certificate-based authentication (CBA) too.
Microsoft Entra Compromised Account Remediation – Script Execution Steps
- Download the script.
- Start Windows PowerShell.
- Select any of the methods below to execute the script.
Method 1: Execute the script with an MFA or non-MFA account.
|
1 |
.\AutomateCompromisedAccountRemediation.ps1 |
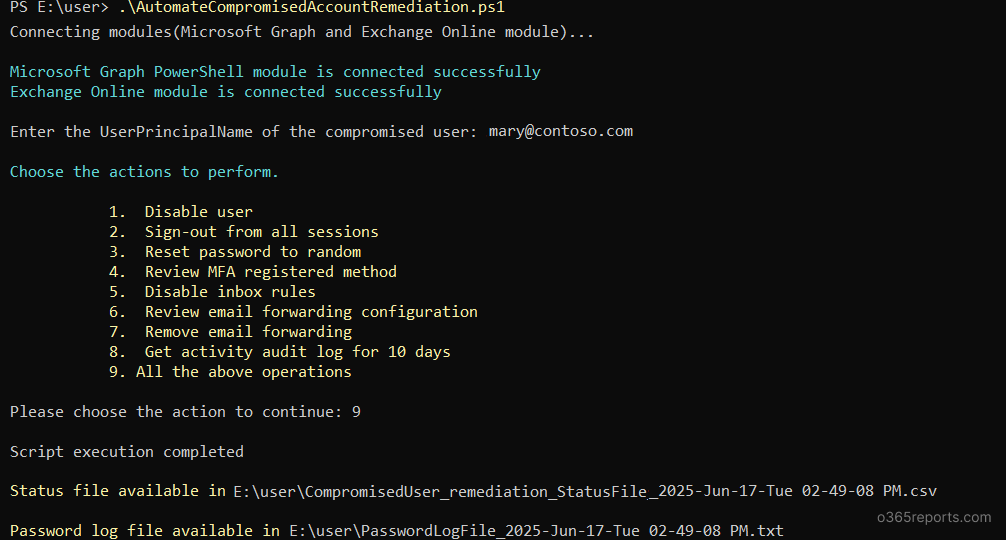
Once connected, you’ll be prompted to enter the User Principal Name(s) of the compromised account(s). You can enter one or multiple users as needed.
Next, the script will prompt you to select the specific remediation actions to perform by entering the corresponding action numbers. Upon selection, the script executes the chosen steps and generates a detailed log file.
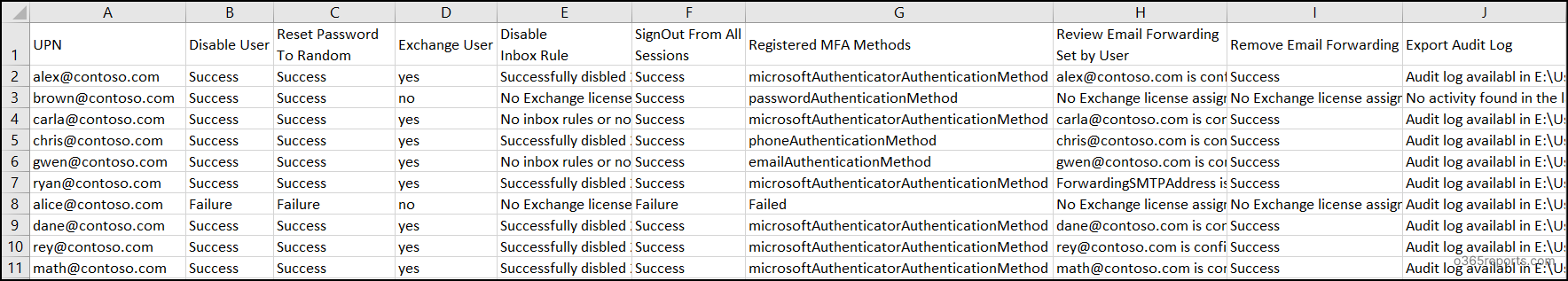
In addition, the script creates four optional output files based on the scenario:
- Password Log File – Lists users whose passwords were reset, along with the newly generated passwords.
- Invalid User Log File – Displays the usernames that were found to be invalid or not present in the tenant.
- Errors Log File – Provides the errors generated along with their code and details.
- Status File – Captures the last 10 days of activity performed by the compromised account to help assess the extent of potential damage. You can also use the dedicated script to audit compromised user activities for last 180 days.
The sample log file provides the status of all the remediation actions performed. Here’s a sample output given:
Method 2: Execute the script using certificate-based authentication.
To use certificate-based authentication, you must register an app in Entra ID, which helps you connect to Microsoft Graph PowerShell and Exchange Online PowerShell.
|
1 |
.\AutomateCompromisedAccountRemediation.ps1 -TenantId <TenantId> -ClientId <ApplicationId> -CertificateThumbprint <CertThumbPrint> -Organization <DomainName> |
Depending on your needs, you can choose to use a certificate authority (CA) or create a self-signed certificate.
Uncover Full Potential of the Script: Automate Compromised User Remediation
The script includes built-in capabilities and parameters that make the automation process easier to handle and more efficient which include:
- Custom compromised account remediation execution
- Enable remediation actions on multiple users
- Execute remediation for multiple compromised accounts via CSV file
1. Customize Compromised Account Remediation Execution
While all the 8 actions are considered best practices, the remediation steps needed can vary based on the situation or the organization’s policies. That’s why this script offers flexibility of choosing only the necessary actions to perform, instead of executing all steps by default. This could be done by simply enter the corresponding numbers of the actions you wish to run when prompted with ‘Please choose the action to continue:’ Here’s a sample action for you:
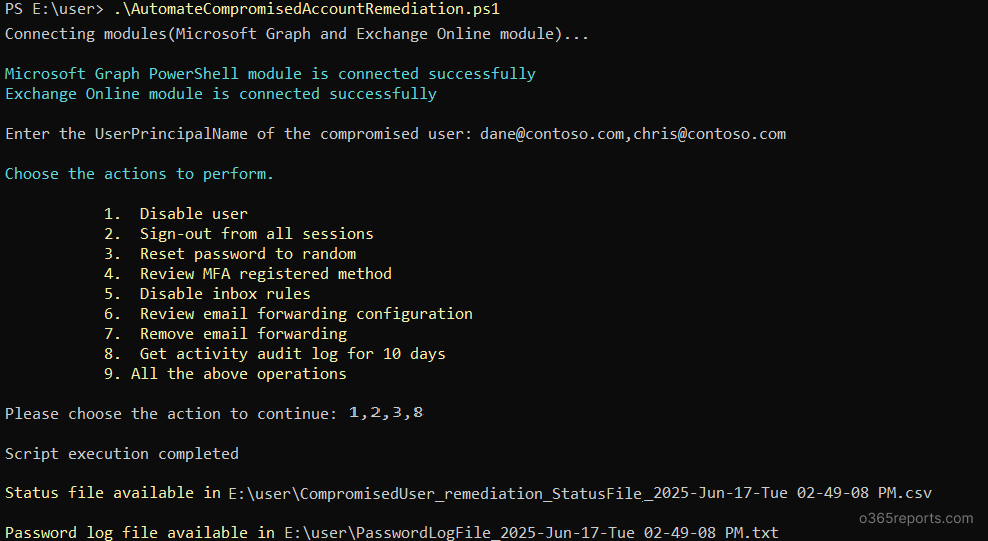
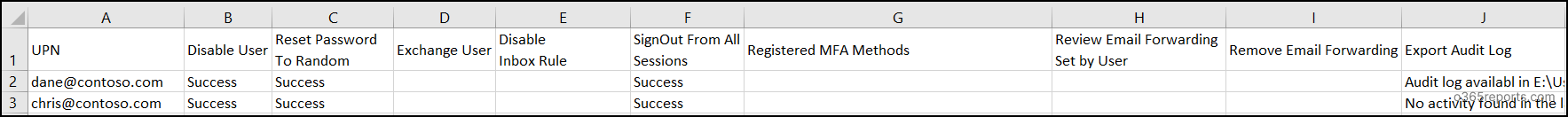
This allows you to customize the remediation process response based on the severity of the incident, the user’s role, or organizational policies to ensure efficient and controlled remediation.
2. Enable Remediation Actions on Multiple Users
Managing compromised accounts individually can be time-consuming, especially in large environments. This script simplifies remediation actions on one or multiple users at once. This flexibility not only saves time but also ensures consistency across your remediation efforts, making your incident response process both faster and more reliable.
Pass multiple users via UPNs parameter while executing and the script will handle the rest.
|
1 |
.\AutomateCompromisedAccountRemediation.ps1 -UPNs <UserPrincipalName> |
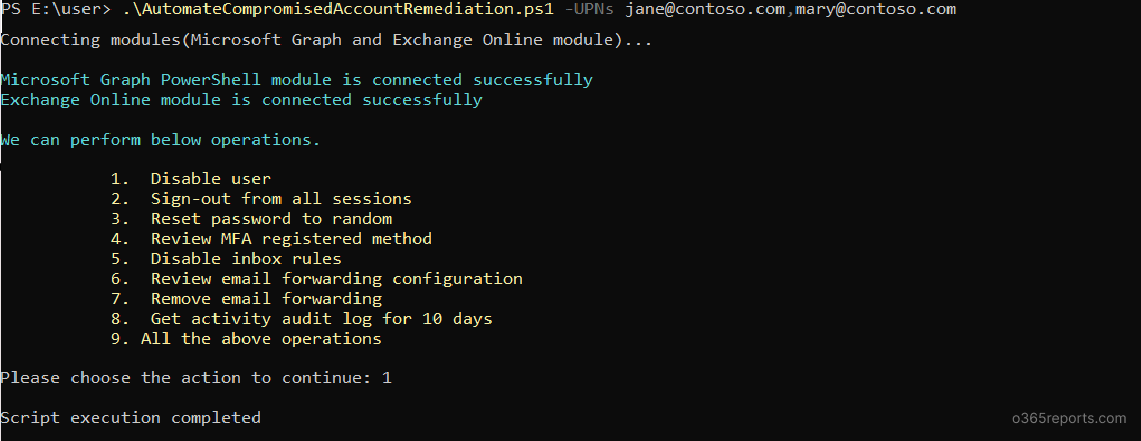
3. Execute Remediation for Multiple Compromised Accounts via input CSV
Another way to deal with multiple accounts is to simply import a CSV file containing the list of user principal names, formatted as shown below:
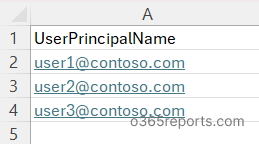
Now, execute the script with the –CSVFilePath param as shown below:
|
1 |
.\AutomateCompromisedAccountRemediation.ps1 -CSVFilePath <CSVFilePath> |
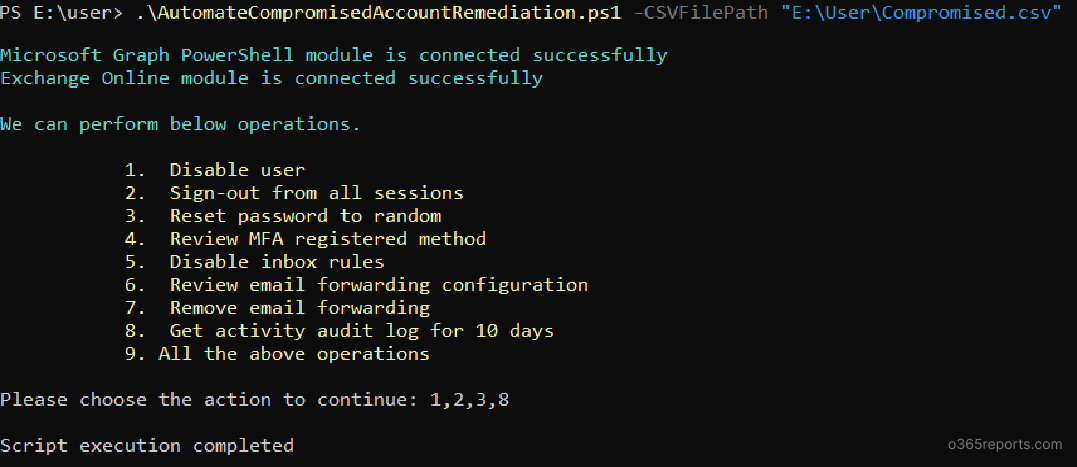
This approach allows you to scale your remediation efforts quickly and efficiently across your environment.
While acting quickly during an account compromise is crucial, it’s even wiser to prevent account compromises in the first place. Take proactive steps and implement the right security measures to reduce risk and stay ahead of potential threats.
AdminDroid Makes Compromised Account Remediation Easy!
Even though the PowerShell script is as simple as it gets, what if you could turn it into a one-click workflow to remediate compromised accounts effortlessly? 💡 That’s exactly what AdminDroid helps you do!
With AdminDroid’s Microsoft 365 Automation Tool, you can build a custom flow agent that performs key compromised account remediation actions like blocking sign-in, resetting a password and much more. Just drag and drop the steps. No coding required!
✅ Need to handle sensitive accounts differently? Add a condition to customize remediation actions based on admin role, department, or other attributes.
✅ Needed a confirmation whether to keep the user disabled or re-enable them? Insert an approval step to let your security team review and decide.
Here’s a sample flow that shows how a compromised account can be remediated using AdminDroid.
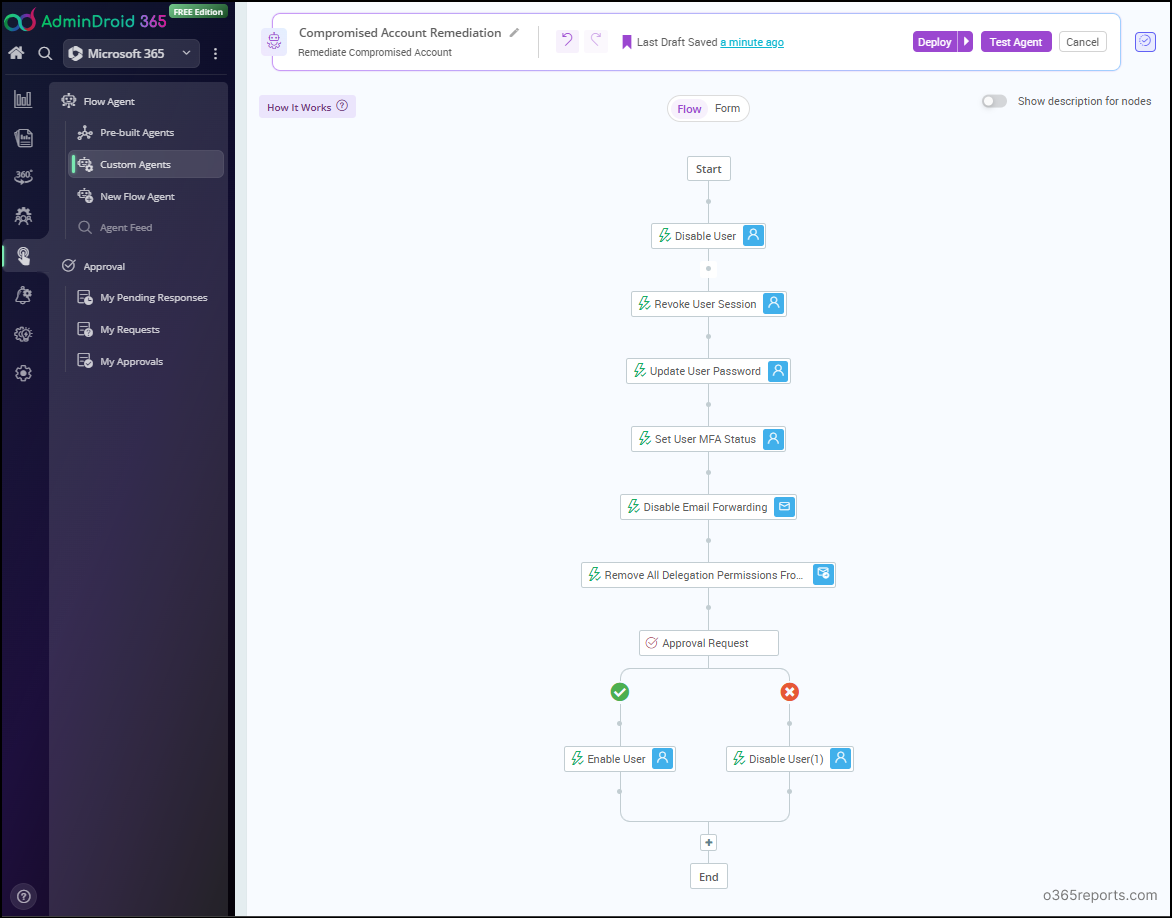
What’s more? AdminDroid offers 10+ pre-built flow agents including user onboarding, offboarding, each packed with expert-picked actions. Whether you’re a beginner or an experienced admin, these ready-to-use automations save hours of manual work and help you respond to threats faster.
Try AdminDroid now and experience one-click account remediation! Simplify your work. Save time! Stay secure!
Wrapping Up
With this blog, we hope you’re better equipped to manage compromised user accounts through automated remediation using PowerShell. In case of any queries, feel free to reach out to us through the comments section. Stay tuned for more PowerShell script blogs!