As remote work culture gained momentum, Microsoft Teams evolved into a crucial communication platform, bridging connections within organizations. However, with its widespread adoption, security concerns have also escalated. The increased user base has provided hackers with a broader array of potential targets.
Thus, Microsoft introduces a range of security measures like reporting suspicious messages, blocking anonymous user access, etc., to ensure the safety of Teams users. Then, here comes the Zero-hour auto purge (ZAP) in Microsoft Teams next for your rescue!
Without further delay, let’s dive into knowing this ZAP feature and its configurations under this blog.
What is Zero-hour Auto Purge in Microsoft Defender?
Zero-hour auto purge (ZAP) is an email protection feature in Exchange Online Protection (EOP), providing an additional layer of security. The Zero-hour auto purge in Exchange Online actively monitors your mailbox, isolating spam, phishing, and malware emails that have infiltrated your inbox.
Zero-hour Auto Purge for Microsoft Teams
Within Microsoft Teams, Zero-hour Auto Purge (ZAP) scans your Teams environment to identify any malicious messages that have infiltrated your workspace. Once detected, these messages are promptly blocked for both the sender and recipients. Please note that although the initial block happens immediately after delivery, the ZAP occurs up to 48 hours from the message’s delivery time.
License Required for Zero-hour Auto Purge in MS Teams
The license requirements for Zero-hour auto purge for Microsoft Teams are listed below.
- Microsoft 365 E5
- Microsoft Defender for Office 365 Plan 2
Most importantly, ZAP in Microsoft Teams supports only internal messages and does not support external messages. Then, Microsoft Zero-hour auto purge extends its support only for Teams chat, shared channels, and standard channels.
Configure Zero-hour Auto Purge for MS Teams in Microsoft Defender
Microsoft states that after August 2023, the Teams protection features, including Zero-hour auto purge, will be turned ‘On’ by default for eligible customers as per MC661823. If not, you can use the steps below to manually enable Zero-hour auto purge (ZAP) for Teams protection.
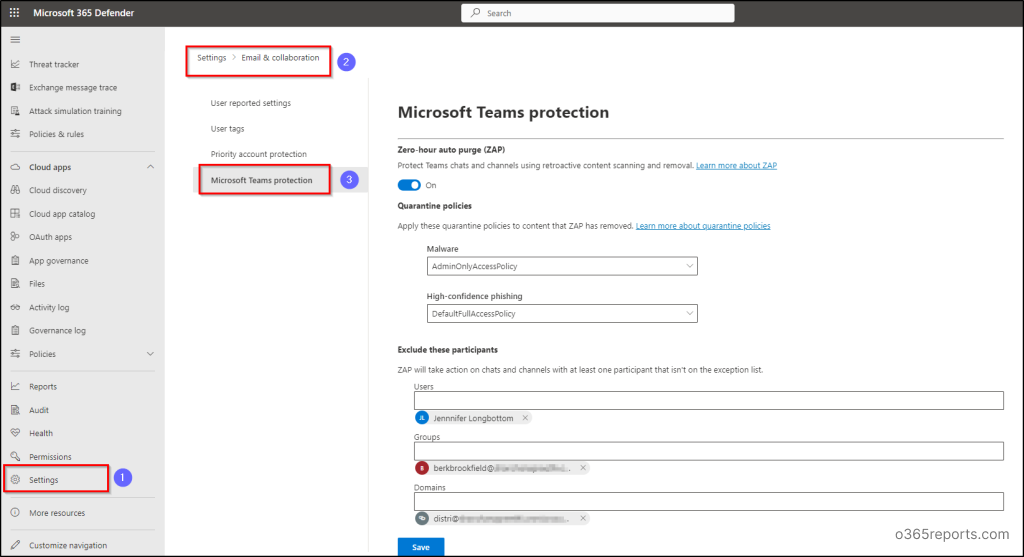
1.Navigate using the path below to configure ZAP for Teams protection.
Microsoft 365 Defender 🡢 Settings 🡢 Email & collaboration 🡢 Microsoft Teams protection
2. Now verify whether the Zero-hour auto purge toggle is On/Off to create Zero-hour auto purge policies for spam and malware messages. If the toggle is Off, set it to On.
3. Next, assign quarantine policies to control user capabilities and notifications for messages removed by ZAP, like malware or high-confidence phishing.
The default quarantine policies are outlined to specify the actions users can take on quarantined messages.
-
- AdminOnlyAccessPolicy – Administrators can use this policy to impose complete restrictions on user access to quarantined messages. Also, users won’t receive any notifications about the quarantined messages.
- DefaultFullAccessPolicy – This option provides full access to users on quarantined messages, but notifications are not enabled. Actually, this option is equipped for less harmful content, aiding users to directly block sender, delete, and preview depending upon the situation.
- DefaultFullAccessWithNotificationPolicy – Choose this alternative to provide full access with quarantine notifications enabled.
- NotificationEnabledPolicy – This option is only available to certain organizations that have activated end-user spam notifications. Organizations that are either newer or older and have never enabled end-user spam notifications do not possess this NotificationEnabledPolicy. This option grants users full access to quarantined messages with enabled quarantined notifications.
4. Then, you can remove ZAP protection feature for some recipients using ‘Exclude these participants’ option. So, mention the users, groups or domains that you want to exclude from ZAP for Microsoft 365 Teams protection.
- It’s significant to note that these exclusions for ZAP in Teams protections primarily target message recipients rather than message senders. Consider the following situations to understand how the ZAP protection feature is applicable with exclusions in group chats.
Imagine a group chat with four recipients namely A, B, C, and D.
-
- Case1: Recipients A, B, C, and D are excluded from ZAP for Teams protection
Outcome: Microsoft Zero-hour auto purge will not block messages sent to this group chat - Case 2: Only recipients A, B, and C are excluded from ZAP for Teams protection.
Outcome: Zero-hour auto purge in Microsoft 365 will block messages sent to this group chat for all recipients. (even the recipients excluded from ZAP) - Case 3: Recipients A, B, C, and D are not excluded from ZAP for Teams Protection. Instead, Sender X is excluded from ZAP for Teams protection.
Outcome: ZAP will block messages sent to this group chat for all recipients.
- Case1: Recipients A, B, C, and D are excluded from ZAP for Teams protection
5. After configuring the ZAP settings, hit the Save button to save your configuration for ZAP in Microsoft Teams.
Configure ZAP for Teams Protection Using PowerShell
Apart from defender portal, Microsoft also paves the way for configuring Zero-hour auto purge in MS Teams using Exchange Online PowerShell. Before diving deep into this topic, make sure to connect to the Exchange Online PowerShell module. Majorly two cmdlets are involved for configuring ZAP using PowerShell. They are,
- Teams Protection Policy – This cmdlet is used for turning ZAP on and for framing the quarantine policies to take corresponding actions based on the malware or high confidence phishing detections.
- Teams Protection Policy Rule – It is used to identify the Teams protection policy and mention the exclusions for ZAP for Teams protection including users, groups, or domains.
By using Exchange Online PowerShell, we can perform the following operations on Zero-hour auto purge in Microsoft Teams.
- Get Teams Protection Policy
- Get Teams Protection Policy Rule
- Modify Teams Protection Policy
- Create Teams Protection Policy Rule
- Modify Teams Protection Policy Rule
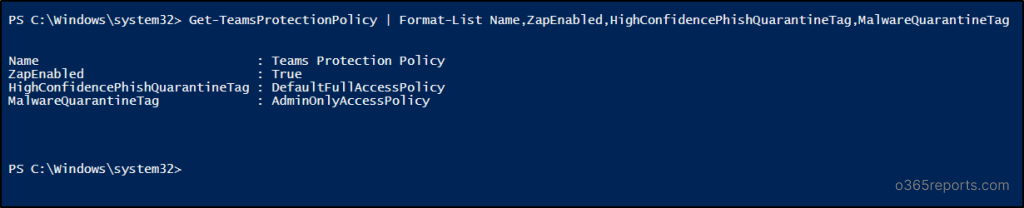
1. Get Teams Protection Policy
Use the “Get-TeamsProtectionPolicy” cmdlet to check whether ZAP is enabled and to retrieve its important values in Teams protection policy.
|
1 |
Get-TeamsProtectionPolicy | Format-List Name,ZapEnabled,HighConfidencePhishQuarantineTag,MalwareQuarantineTag |
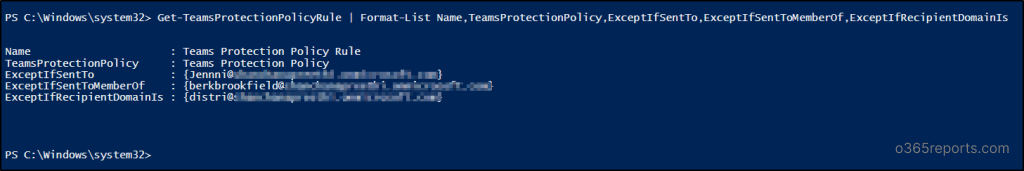
2. Get Teams Protection Policy Rule
Run the following “Get-TeamsProtectionPolicyRule” cmdlet to get detailed information on exclusions such as users, groups or domains excluded from ZAP for Teams protection.
|
1 |
Get-TeamsProtectionPolicyRule | Format-List Name,TeamsProtectionPolicy,ExceptIfSentTo,ExceptIfSentToMemberOf,ExceptIfRecipientDomainIs |
3. Modify Teams Protection Policy
You can utilize the “Set-TeamsProtectionPolicy” cmdlet to customize your organization’s Teams protection policy. This allows you to enable features like Zero-hour auto purge and assign quarantine policies to handle malware or highly confident phishing detections.
|
1 |
Set-TeamsProtectionPolicy -Identity "Teams Protection Policy" [-ZapEnabled <$true | $false>] [-HighConfidencePhishQuarantineTag "<QuarantinePolicyName>"] [-MalwareQuarantineTag "<QuarantinePolicyName>"] |
In this example, we enable Zero-hour auto purge and set the quarantine policy as AdminOnlyAccessPolicy for high confidence phishing detections.
|
1 |
Set-TeamsProtectionPolicy -Identity "Teams Protection Policy" -ZapEnabled $true -HighConfidencePhishQuarantineTag AdminOnlyAccessPolicy |
![]()
4. Create Teams Protection Policy Rule
There is no default Teams protection policy rule since there are no default exclusions for ZAP feature. So, you can use the “New-TeamProtectionPolicyRule” cmdlet mentioned below to create Teams protection policy rule defining the exceptions.
|
1 |
New-TeamsProtectionPolicyRule -Name "Teams Protection Policy Rule" -TeamsProtectionPolicy "Teams Protection Policy" [-ExceptIfSentTo <UserEmail1,UserEmail2,...UserEmailN>] [-ExceptIfSentToMemberOf <GroupEmail1,GroupEmail2,...GroupEmailN>] [-ExceptIfRecipientDomainIs <Domain1,Domain2,...DomainN>] |
The below example creates a Teams protection policy rule excluding the members of distribution list with “ExceptIfSentToMemberOf” parameter.
|
1 |
New-TeamsProtectionPolicyRule -Name "Teams Protection Policy Rule" -TeamsProtectionPolicy "Teams Protection Policy" -ExceptIfSentToMemberOf research@contoso.onmicrosoft.com |
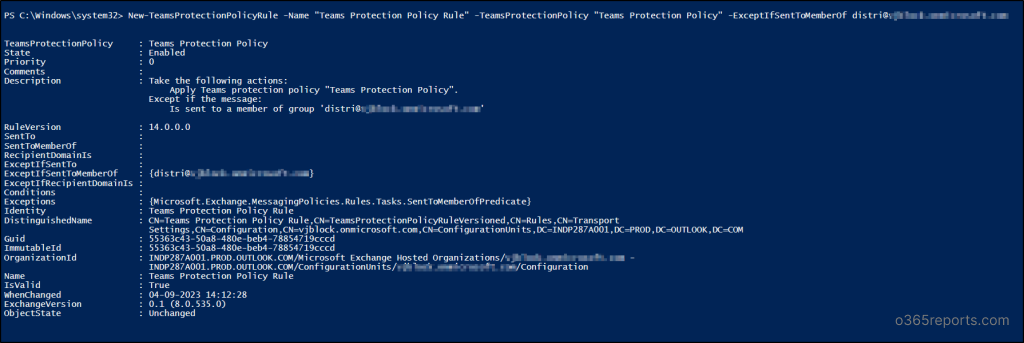
5. Modify Teams Protection Policy Rule
You can modify the existing Teams protection policy rule using the “Set-TeamsProtectionPolicyRule” cmdlet mentioned below.
|
1 |
Set-TeamsProtectionPolicyRule -Identity "Teams Protection Policy Rule" [-ExceptIfSentTo <UserEmailAddresses | $null>] [-ExceptIfSentToMemberOf <GroupEmailAddresses | $null>] [-ExceptIfRecipientDomainIs <Domains | $null>] |
Using the example below, you can modify your existing Teams Protection policy rule and exclude members from particular domain with the “ExceptIfRecipientDomainIs” parameter.
|
1 |
Set-TeamsProtectionPolicyRule -Identity "Teams Protection Policy Rule" -ExceptIfRecipientDomainIs research.contoso.com,research.contoso.net |
![]()
NOTE: Use ‘$null’ value in ExceptIfSentTo, ExceptIfSentToMemberOf, or ExceptIfRecipientDomainIs parameters to avoid exclusions from ZAP for Teams protection.
Things to be Noted…
- Only one Teams protection policy for an organization exists, where it is designated as the “Teams Protection Policy” by default.
- Use the “New-TeamsProtectionPolicy” cmdlet to create a Teams protection policy. Please be aware that the policy will only be established if no Teams protection policy already exists in your organization. Running the cmdlet may not result in errors, but its execution leads to policy creation solely when no prior policy exists.
- It is not possible to remove or delete the Teams Protection policy or Teams Protection policy rule.
- Finally, there is no Teams protection policy rule by default in Microsoft 365. Configuring quarantine policies and adding exclusions for ZAP for Teams protection creates Teams protection policy rule automatically. You can configure them in the Defender portal or using the “New-TeamsProtectionPolicyRule” cmdlet in PowerShell.
View MS Teams Quarantined Messages in Microsoft Defender
Quarantining harmful malicious or phishing messages is a vital initial precaution, but it’s not the only defense against intrusions and malicious attacks in your organization. As an administrator, you have the capability to get Zero-hour auto purge reports and review the harmful content that ZAP has removed through the Microsoft Defender portal. Using the Microsoft Defender portal, manage MS Teams quarantined messages in your organization.
Follow the path below for monitoring zapped messages that are ZAP removed and quarantined Teams messages.
Microsoft 365 Defender 🡢 Email & collaboration 🡢 Review 🡢 Quarantine 🡢 Teams messages
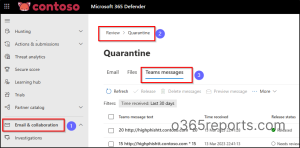
Zero-hour auto purge alone cannot completely eliminate data theft! Instead, it serves as an additional layer of defense, mitigating potential risks reaching your Teams chats and meetings. Therefore, it remains crucial for administrators to actively identify and address potential vulnerabilities within the Microsoft Teams to prevent data breaches.
Here comes the AdminDroid Microsoft 365 Reporter, a valuable tool designed to assist in analyzing your Microsoft 365 environment. It provides detailed reports on your entire Teams to monitor & safeguard against cyber threats.
Empower Microsoft Teams Data Security with AdminDroid
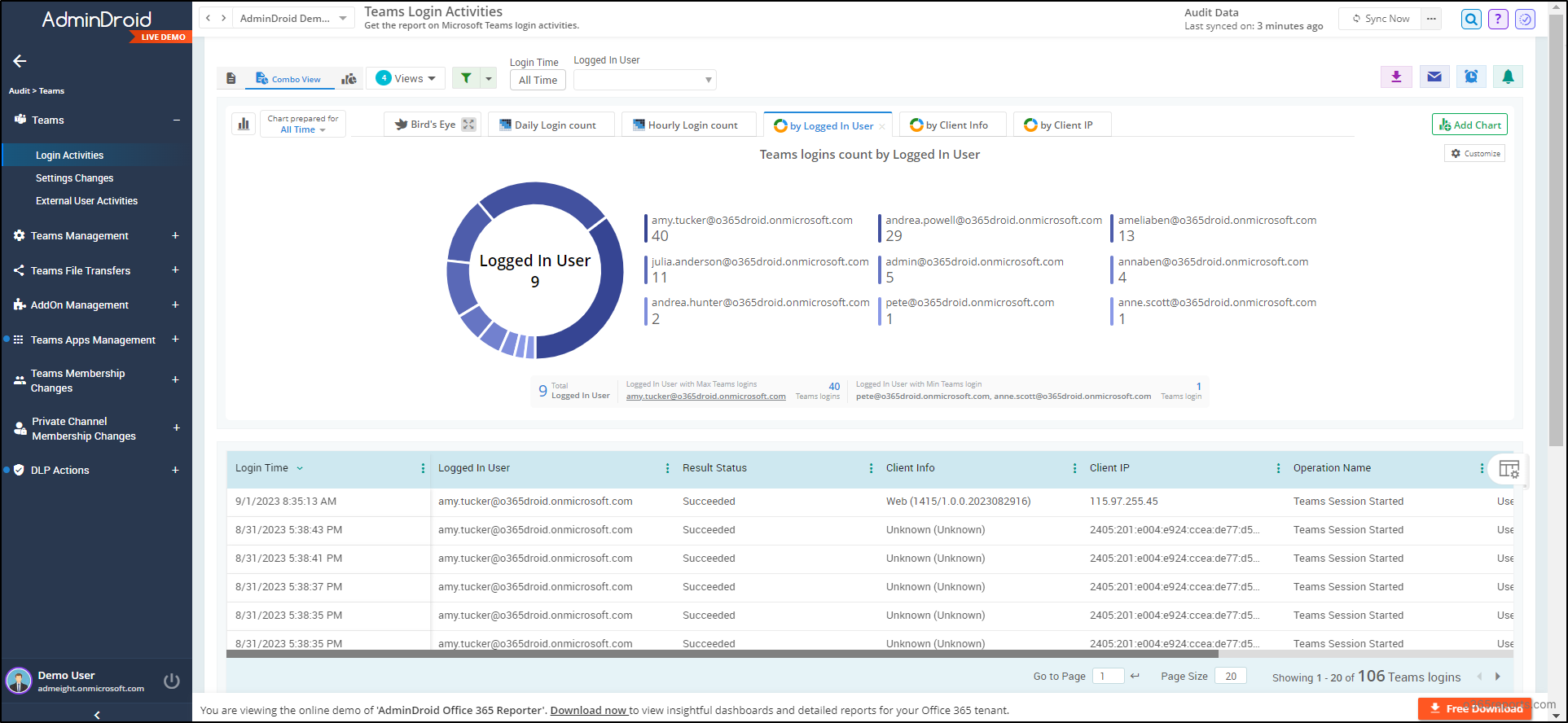
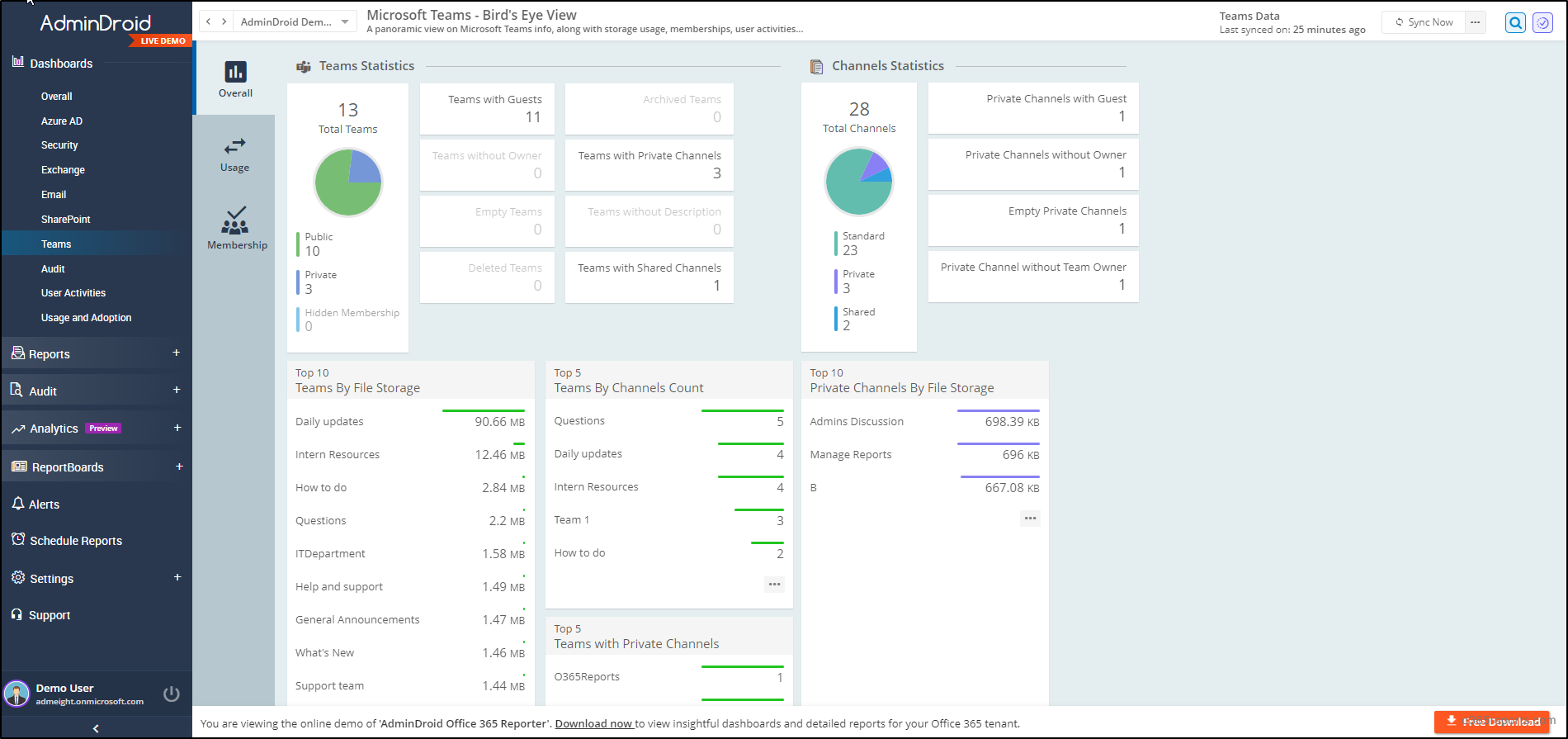
With AdminDroid, audit MS Teams activities like membership changes, external user login, DLP actions, user activities, file access, and sharing events to be ahead of the cyber threats in all possible ways. Have a complete overview of your Teams environment covering every minor detail to massive changes with Microsoft Teams dashboards in hand!
Furthermore, you can stay vigilant over all activities like Teams settings, standard & private channels, ownerships, memberships, permissions, Teams inactive users, device usages, etc., with AdminDroid Microsoft Teams reporting tool.
Don’t confine yourself to MS Teams management alone! There is much more in AdminDroid! Yes, AdminDroid is an all-in-one Microsoft 365 reporting and auditing tool. It offers almost 1800+ comprehensive reports and 30+ sleeking dashboards including various services like Microsoft Entra ID, Exchange Online, MS Teams, SharePoint Online, OneDrive, Power BI, Stream, and Viva Engage.
Moreover, it eases your Office 365 administration with splendid features like AdminDroid alerting, scheduling, granular access delegation and advanced customization filters.
Download AdminDroid now with a 15-day trial to have a trailblazing experience for effortless Microsoft 365 management.
Overall, there’s no need to be overly concerned if the occasional message manages to slip through your security defenses and make its way into Microsoft Teams. Enabling ZAP in Microsoft Teams helps swiftly intercept and block potentially harmful messages, ensuring your organization’s safety from potential threats.
Zero-hour auto purge (ZAP), as part of these protective features, plays a crucial role in maintaining the integrity and security of your new Microsoft Teams environment. So, ensure you follow the Microsoft Teams security best practices and take proactive steps today to fortify your Teams communication and keep your organization safe from emerging threats.
We hope this blog has provided you with a clear understanding of Zero-hour auto purge in Microsoft Teams. Please feel free to share your thoughts and any questions you may have in the comments section.