In the fast-paced digital world, even the smallest sign-in risks are quickly spiraling into major cyber security threats. Shockingly, a recent report by Barracuda Networks found that every one in five organizations had an account compromise in 2021 alone!
Thankfully, Microsoft has introduced multi-factor authentication to secure user accounts from sign-in risks and provides an extra layer of protection against potential breaches. Thereby admins started to configure multi-factor authentication in their Office 365 environment to defend against attacks.
Although it protects organizations from sign-in risks to an extent, cybercriminals are always finding ways to bypass them anonymously. Thus, to stop hackers from invading organizations through user accounts, Microsoft brought the concept of multi-factor authentication fraud alerts. MFA fraud alert is a feature for alerting admins when users face unfamiliar MFA requests in their accounts. So, without any further delay, let us dive deep into the concept of MFA fraud alerts and their configuration.
What is a Multi-Factor Authentication Fraud Alert?
MFA fraud alerts are used to alert the admins when the multi-factor authentication request is initiated without the users’ concern. In MFA fraud alerting, the users notify the admins by reporting fraudulent activity that occurred in their accounts.
The users can report the fraudulent activity at the time of denying the MFA request in the authenticator app or by entering the fraud code in an automated telephone system.
What is the Purpose of MFA Fraud Alerts?
Now you might be wondering what the exact purpose of this MFA fraud alert is and what they do. So, let’s get to see the purpose of MFA fraud alerts.
- The main purpose of this MFA fraud alert is to notify the admin that a suspicious MFA request has been initiated for a user. Though these alert notifications do not solve the problem directly, it makes you get informed and well-prepared to face it!
- Most importantly, MFA fraud alerts reduce the potential risk of MFA fatigue attacks, also known as MFA Bombing. One such technique that recently attacked the giant company Uber in September last year.
-
- MFA fatigue attack is a social engineering technique that uses human error to gain information. In detail, attackers steal the user’s credentials by brute force or password spray attacks. Then, they send continuous MFA requests to prompt the user to accept one accidentally. Once the user accepts an MFA request, the hacker easily gets into the user account and tends to exploit it.
Therefore, avoid MFA fatigue at the initial stage using MFA fraud alerts! It allows you to investigate and take necessary security measures against fraudulent activity. So, now let us see how to configure MFA fraud alerts in Microsoft 365.
How to Configure MFA Fraud Alerts in Azure AD?
With just a few clicks, you can set up MFA fraud alerts for your organization and protect against fraudulent activity. To enable the settings, navigate through the following path.
- Microsoft Entra admin center 🡢 Protect and Secure 🡢 Security Center (Click ‘Show more’) 🡢 Manage 🡢 Multi-factor Authentication.
- Now on getting into the ‘multi-factor authentication’ page, select Fraud alert among the security settings.
- Then, you can configure the fraud alert settings below.
- Allow users to submit fraud alerts – Enable this setting to allow users to submit a report when an MFA request is initiated that they did not request. As a result, you’ll be able to identify the user accounts targeted by unknown MFA requests and take measures to safeguard your organization against future emerging threats such as phishing scams.
- Automatically block users who report fraud –To immediately block the targeted user accounts that have been attempted for compromise, push this toggle button to the ‘On’ condition.
PROS and CONS of the Block Users Option:
-
- If this block option is turned off, the user will not be blocked immediately. Therefore, as an alternative option, admins can configure to send email alert notifications to specific users about the suspicious MFA request. Then, they should investigate the situation and decide which response action to take.
- While enabling this option has both advantages and disadvantages! One of the greatest advantages of enabling this setting is that it immediately blocks further requests from hackers.
- But sadly, if a user reports a suspicious MFA request, the user account will be blocked until the admin unblocks the account. Eventually, blocking the user account will cause trouble for the user productivity. So ultimately, the admin has to decide whether to enable this setting or not based on their organization’s security posture.
- If this block option is turned off, the user will not be blocked immediately. Therefore, as an alternative option, admins can configure to send email alert notifications to specific users about the suspicious MFA request. Then, they should investigate the situation and decide which response action to take.
- Code to report fraud during initial greeting – By default, users can report suspicious MFA requests by entering the code 0. Now, with this setting, admins can customize the code number to report a fraudulent MFA request.
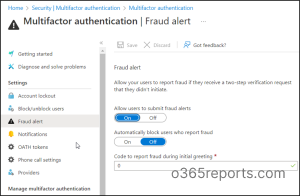
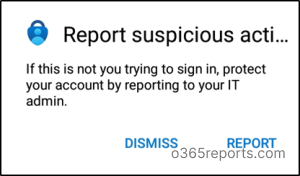
4. After finishing the configuration, store them using the Save option. Hereafter, your users will be able to report any suspicious multi-factor authentication requests in the Microsoft Authenticator app while denying the request. A sample of the report option is given below.
As we are now clear in configuring the multi-factor authentication fraud alerts, let us see how to turn on notifications for the admin or security team.
Turn On Notifications about MFA Fraud Alerts
Instead of viewing the reports every time to know about the suspicious activities happening around the organization, admins can get notified in real-time about every unusual behavior. In order to receive notifications via email when a user reports a fraud alert via the authenticator app or automated telephone system, admins should follow the steps below and configure email alert notifications for specific users.
Microsoft Entra admin center 🡢 Protect and Secure 🡢 Security center 🡢 Multi-Factor Authentication 🡢 Notifications.
On the notification page, you can add the email address of the people you want to receive notifications of unknown MFA requests. Do not forget to save them once you add all the recipients. Look at the screenshot below for the notification page and email of MFA fraud alert.
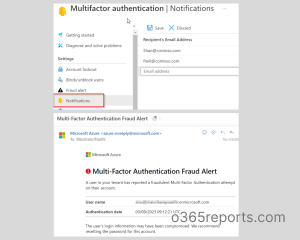
View Suspicious Activities Reports in Azure AD Audit Logs
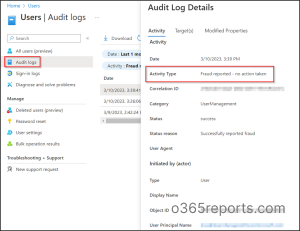
When a user reports an unfamiliar MFA request, it gets logged in the Azure AD audit logs as the user has been blocked for MFA. Admins can use this report to identify and disable the impacted users. Thereby, view the reports by navigating to the below path:
Microsoft Entra admin center 🡢 Users 🡢 All Users 🡢 Audit logs.
The report for fraud activity in Audit logs is present under activity type as Fraud reported – user is blocked for MFA, and Fraud reported – no action taken.
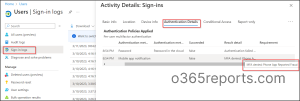
MFA Fraud Reports in Azure AD Sign-in logs
When a user reports an unknown MFA request, the event is logged in the sign-in logs as sign-in request was rejected. MFA fraud report appears in result detail as part of the standard Azure AD sign-ins report. MFA fraud report is indicated as MFA denied: Phone App Reported Fraud in the result detail column.
You can also view the suspicious events in the Sign-ins report using the following path.
Microsoft Entra admin center 🡢 Users 🡢 All Users 🡢 Sign-in logs 🡢 Authentication details.
Therefore, implement multi-factor authentication fraud alerts in your tenant to protect your organization from cyber security threats like MFA bombing.
Recommended Security Measures For Fraud Alert Reporting:
- In the first instance, when admins observe continuous user reporting activity, they can manually block the specific user sign-in if they consider the risks too high.
- Otherwise, they can reset the password of the targeted user as that user account doesn’t impose much threat to the organization.
The New ‘Report Suspicious Activity’ in Azure AD
Report Suspicious Activity feature is the new updated version of the MFA fraud alerts. This feature is now available in the public preview, where MFA fraud alerts operate in parallel with this report of suspicious activity.
What’s New in Report Suspicious Activity feature in Azure AD
- This new feature sets the user’s risk high when a suspicious MFA request has been initiated.
- Also, admins can use risk-based policies or enable self-service password reset options for immediate remediation.
Reporting suspicious activity alone is not sufficient for security. Instead, reporting & monitoring all MFA events is crucial for the utmost Microsoft 365 security. Ending up with native methods as a solution to monitor MFA is not a bad thing. But how long will you say monitoring them through the admin center or PowerShell suffice and do all the hard work? 😥
Could not find a perfect replacement? Then here comes the AdminDroid Microsoft 365 reporter to do all the hard work for you! Let’s dive into the spectacular features of AdminDroid. 🏹
Acquire AdminDroid Free MFA Reports to Defend against MFA Attacks!
No harm shall touch your Microsoft 365 with the binoculars of AdminDroid!
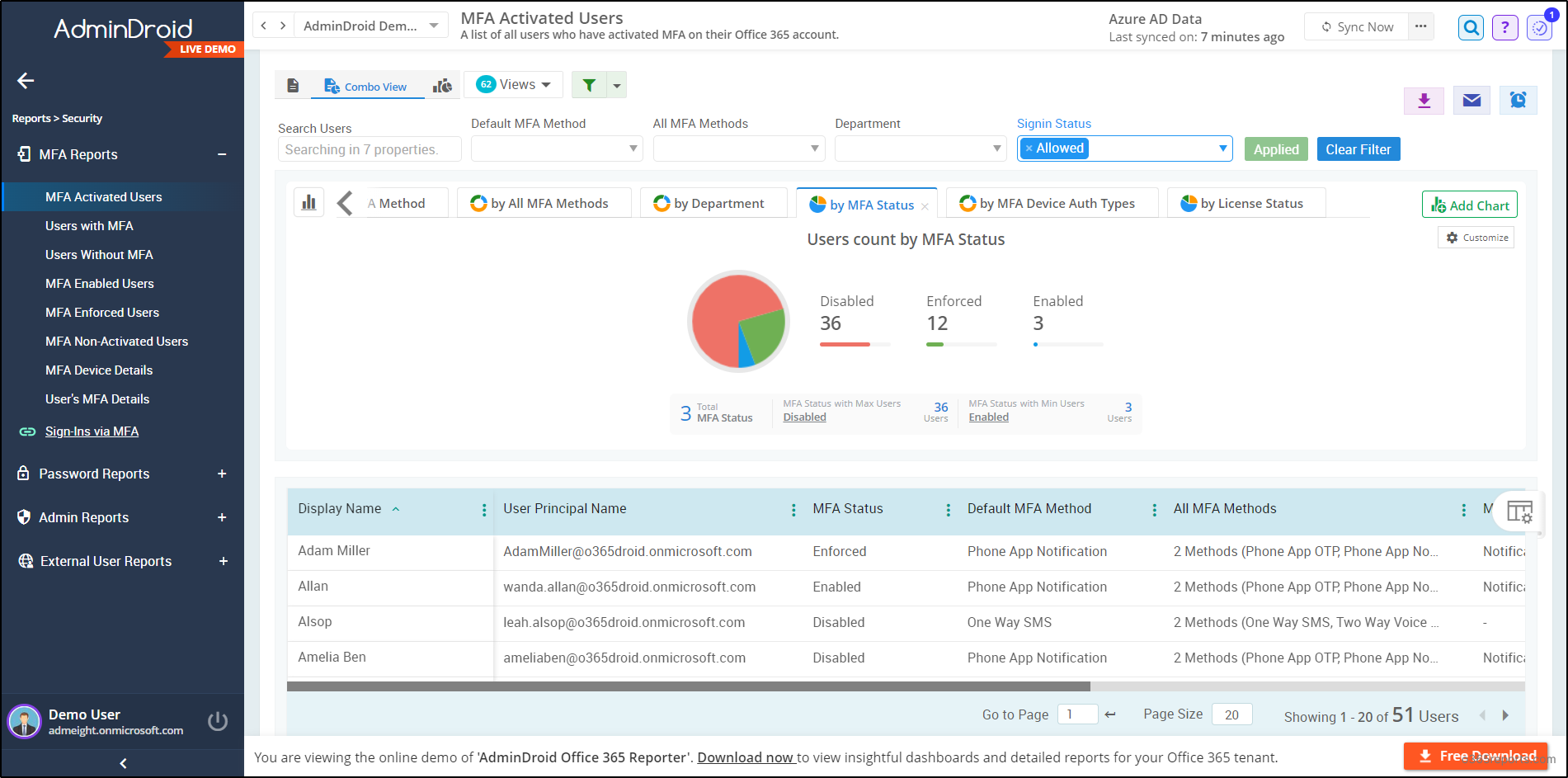
Have a stereoscopic view of every auth method in multi-factor authentication reports up to date for foreseeing issues with the past trend data. 📉 AdminDroid MFA reports offer the following detailed reports.
- Users with and without MFA
- Admins without MFA
- MFA enabled users
- MFA enforced users
- MFA-activated and non-activated users
- MFA device details
Additionally, enjoy the Free Azure AD reporting tool of AdminDroid that offers 190+ granular reports 📊 on Microsoft 365 users, groups, admins, password changes, licenses, external users, etc., to ultimately monitor your Azure AD environment.
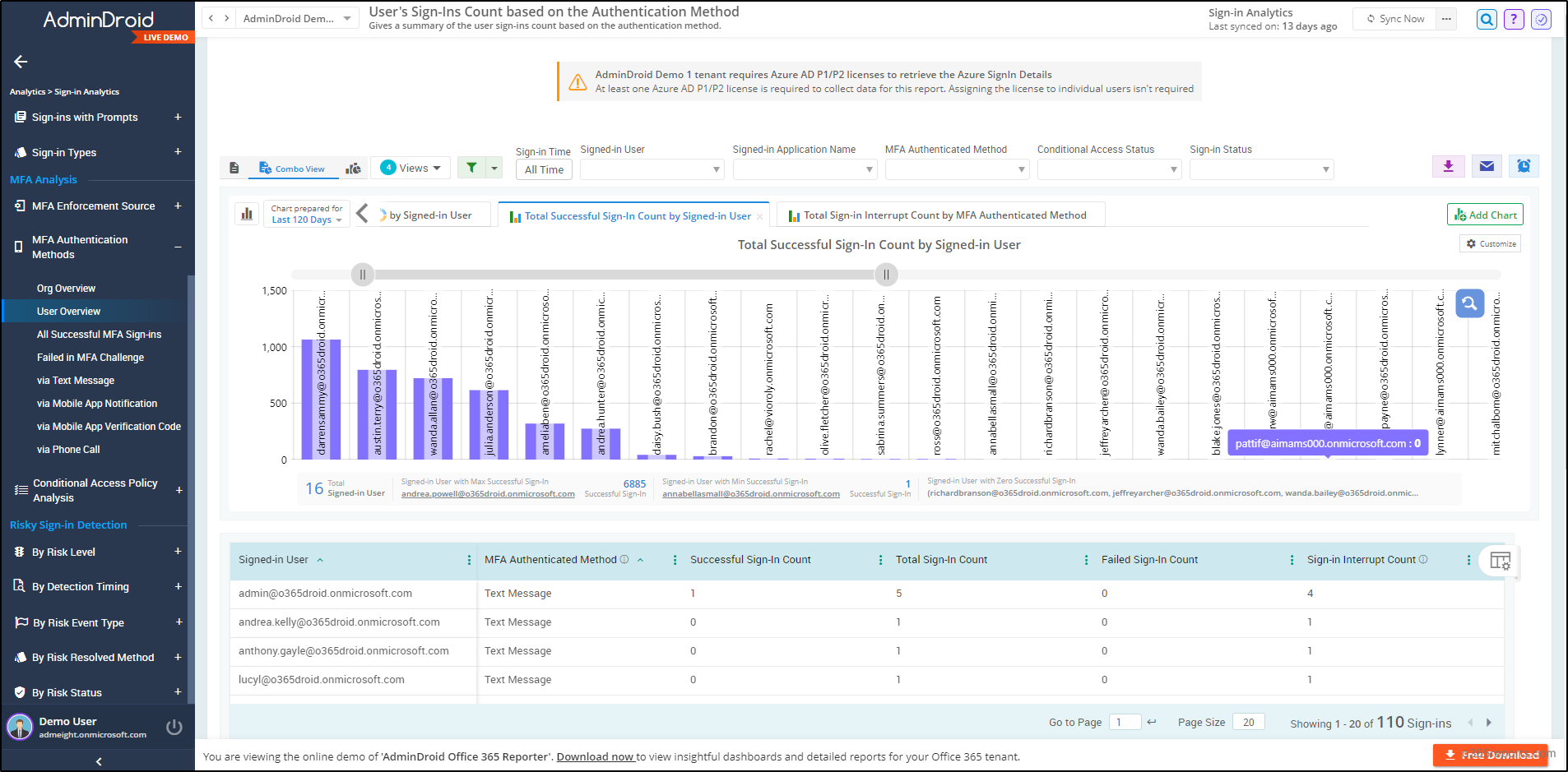
Apart from these reports, you can also perform in-depth MFA analysis with AdminDroid analytics. By closely analyzing every MFA event with AdminDroid, strengthen and secure your Microsoft 365 space. 🔐 With the below-detailed MFA reports, admins can effectively assess the implementation and effectiveness of MFA measures within your Microsoft 365 environment, ensuring a higher level of security and safeguarding against potential threats. The AdminDroid MFA Analysis report includes,
- MFA enforcement by CA policy
- MFA enforcement by user level
- MFA auth methods organizational & user-level overview
- Successful MFA sign-ins
- Failed in MFA challenges
- MFA auth via Text message
- MFA auth via Mobile App notification
- MFA auth via Mobile verification code
- MFA auth via Phone call
Now visualize your entire Azure Active Directory with comprehensive reports and AI-powered dashboards under the AdminDroid Azure AD management tool. Also, get 1800+ in-depth reports and 30+ sleek dashboards from AdminDroid on various services like Exchange Online, OneDrive, SharePoint Online, Microsoft Teams, Yammer, etc., to monitor your complete Microsoft 365.
Look no further! Now find everything that matters to your Microsoft 365 with AdminDroid. 💯 With its user-friendly interface and ingenious features of alerting, scheduling, filtering & granular access delegation, say bye to your conventional methods.
Try using AdminDroid now with a 15-day trial to have trailblazing field experience on Microsoft 365 reporting and monitoring. ✨
Overall, get started on enhancing your organization’s security posture by enabling MFA fraud alerts and reporting suspicious activity. Don’t let hackers intrude into your organization! Along with these measures, make use of features like remember MFA on trusted devices, MFA number matching, and more to further strengthen security. Configure these advanced settings to defend against unauthorized access and safeguard your environment effectively.
Hope this blog made you clear about the multi-factor authentication fraud alerts. Drop your thoughts in the comments section.