In today’s world, everyone in the organization prefers using Multi-factor Authentication (MFA) as an extra level of security beyond traditional credentials. MFA has the advantage of requiring additional verification methods other than the username and password when logging in to the Microsoft portal. For a secure experience, it is important to verify whether all users in the organization comply with the MFA configuration.
As Microsoft continues to enhance MFA standards, administrators must monitor which users have registered for MFA, and which have not, how MFA was enabled for each user, and who enabled MFA for those users. Let’s take a look at how admins can manage MFA configurations in Azure AD.
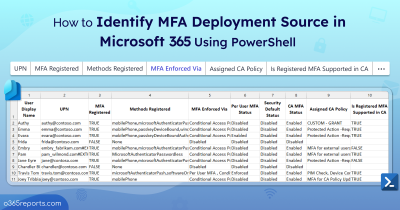
Users Who Registered for MFA
Registering for Multifactor authentication is important in an organization as it adds an extra layer of authentication that prevent hackers from logging into your system. Users’ MFA registration can be tracked using user registration details report and MFA status report where admins can ensure 100% compliance across your organization. Under this report, info like users who are capable of MFA, MFA registered methods by users, and so on can be obtained. MFA capable users are those who got registered and enabled for strong authentication methods.
Step:1 Log in to the Microsoft Azure Portal
Step:2 Navigate to Azure Active Directory –> Security –> Authentication Methods –> User Registration details.
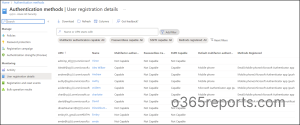
As an admin, verifying registered authentication methods is crucial for assessing how well accounts can withstand MFA attacks. If you discover any vulnerable methods, you can reset MFA to encourage users to re-register with stronger authentication options.
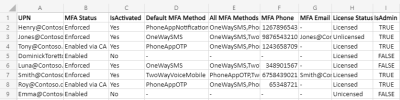
Users Who signed-in using MFA
Since native sign-in methods of using a username and a password are vulnerable to brute force attacks, it is important to monitor the sign-ins done with and without MFA. Wondering how? Using Azure AD sign-in logs, admins can easily track the logins made using authentication methods along with details like status, date, time, application, IP address, location, etc.
Step:1 Log into the Microsoft Azure Portal.
Step:2 Navigate to Azure Active Directory –> Sign-in logs
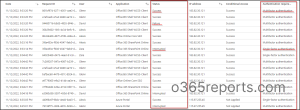
Further, by using sign-in logs, admins can obtain information about conditional access policies settings.
Reason Why MFA Configuration Got Failed
While configuring Multifactor authentication, sometimes the registration may get failed. It would be better if admins are aware of why the registration got failed. The reason for the MFA failure can be obtained from the Registration and reset events report. Further, this report also provides activity date, time, authentication methods used, etc., for better visibility.
Step:1 Log in to the Microsoft Azure Portal.
Step:2 Navigate to Azure Active Directory –> Security –> Authentication Methods –> Registration and reset events.
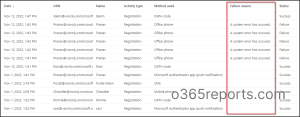
Never ignore to configure Multifactor authentication, as it acts as a crucial indicator that keeps bad actors away from your valuable data.
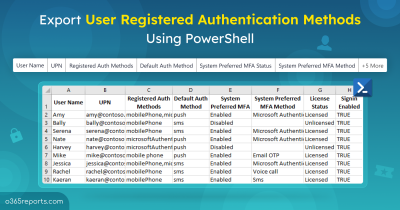
Find Out MFA Configuration for a Specific User
Adopting MFA is a key initiative for any company regardless of size and can be one of the easiest and simplest ways to keep user accounts protected. Using Azure, it is also possible to keep track of admins who turned on MFA for specific users. During investigations, admins can gain details on users who made suspicious MFA registration using Azure audit logs.
Step:1 Log into the Microsoft Azure Portal.
Step:2 Navigate to Azure Active Directory –> Audit Logs.
Step:3 Specify ‘Authentication Methods’ under the Service filter.
Step:4 Customize the date range based on requirement and then select apply.
Step 5: ‘Initiated by’ column will retrieve the user who turned on MFA for a specific user.
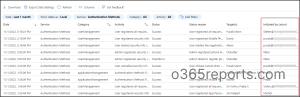
With the results obtained, admins can select any row in specific to view the complete audit and the details of who initiated the registration for MFA.
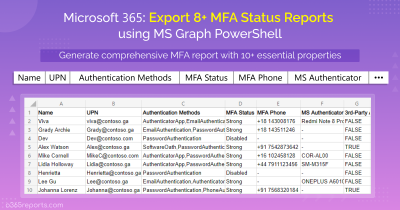
Unlock Powerful Insights for MFA Security with AdminDroid’s Reports and Dashboards
As we all know, native Microsoft 365 auditing is complex, particularly when an organization has large number of users, devices, and applications using MFA. Configuring and managing the MFA configurations can be time-consuming and require specialized knowledge.
There comes AdminDroid!
AdminDroid includes a wide range of MFA reports including a suite of reports specifically focused on MFA configured Conditional Access Policies.
- MFA Activated Users – Lists all users who have activated MFA on their accounts.
- Users with MFA – Lists all users who have MFA enabled on their accounts
- Users without MFA – Lists all users who do not have MFA enabled on their accounts.
- MFA Enabled Users – Lists all users who have MFA enabled on their accounts
- MFA Enforced Users – Lists all users who have MFA enforced on their accounts.
- MFA Non-Activated Users – Lists users who have MFA enabled but have not yet activated.
- MFA Device Details – Lists device details that users have used to authenticate with MFA.
- MFA User Details – Provides information about individual users’ MFA settings.
- Conditional Access policies with MFA – Lists the MFA configured CA policies.
- MFA enabled CA policies – condition details – Provides an overview of conditions that are associated with MFA-enabled CA policies.
- MFA included/excluded users based on CA policies – Provides detailed information on MFA included and excluded users based on CA policies.
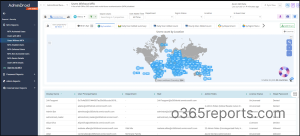
Some other important MFA reports offered by AdminDroid Azure AD reporting tool offers reports that you don’t want to miss.
- Organization Sign-Ins based on Authentication Method
- User’s Sign-Ins based on Authentication Method
- Successful User Sign-Ins via Muti-Factor Authentication
- User’s MFA Failures with Details
- MFA User sign-ins verified via Text message
- MFA User sign-ins verified via Mobile App notification
- MFA User sign-ins verified via mobile app verification code
- MFA User sign-ins verified via phone call
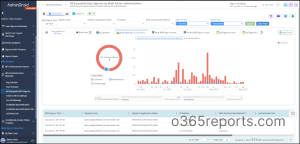
Microsoft 365 MFA Dashboard
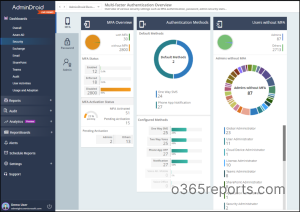
Apart from reports, AdminDroid has a dedicated MFA dashboard that provides an overview of:
- Users’ MFA status (including their activation and authentication status)
- Authentication methods they use (both default and alternate methods)
- Admins who do not have MFA enabled.
This customizable dashboard allows you to tailor your security monitoring to your organization’s specific needs!
AdminDroid revolutionizes your Azure AD reporting and auditing experience by offering much more than just MFA reports. With over 1800 pre-built reports for various Office 365 services such as Azure AD, Exchange Online, SharePoint Online, and Microsoft Teams, you can gain a comprehensive understanding of your organization’s performance.
AdminDroid’s user-friendly interface allows you to experience the power of data-driven insights. Indeed, your Office 365 auditing and reporting needs will be met with AdminDroid.
Get a free trial of AdminDroid – An Office 365 reporting tool.
I hope this blog has helped you in knowing where to find MFA enrollment and additional details in the Azure Active Directory. Feel free to drop the comments for further assistance!