Do all the users in your Office 365 organization updated their sign-in methods? If not, then you must act faster and update it. Using legacy app clients holds less security than apps that supports modern authentication. Thus, it may lead to data leakage in your organization. To improve security, admins should avoid legacy app usage and stay updated. So, what should be updated to elevate security? You must check the users’ authentication methods, OS versions, browser versions, whether they use any deprecated client apps, etc. Microsoft helps you to monitor all the user details to secure your organization. Here, let’s see how to find out the usage of legacy client apps in your organization.
Microsoft 365 Authentication Methods?
Microsoft supports the following two types of authentications to connect to the server.
- Modern authentication
- Legacy (basic) authentication
Modern authentication is more secure than legacy authentication which requires no additional verification other than a username and password to access your tenant. When concerning data security, modern authentication is preferred. Now, Microsoft has deprecated legacy authentication to restrict its usage and improve security. So, users who use the older version no longer use the app without upgrading to modern authentication. To avoid this, admins need to monitor the client apps, Outlook versions, and browser versions used by the users and update them accordingly.
How to find the users who use deprecated client apps?
Admins should track the client apps used by the users to connect O365 to find out who still uses the deprecated client apps in the organization. Then, they should migrate to modern authentication. Admins can track the client apps in the following two ways.
- Microsoft 365 Admin Center
- Azure Active Directory Admin Center
Tracking app clients using Admin Center
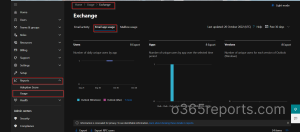
- Navigate to Microsoft 365 Admin Center.
- Click on Reports–> Usage.
- Under Email activity click View More.
- Select the Email app usage.
- You will get the list of client apps and versions of Outlook used by the users in your organization.
Tracking app clients using Azure Active Directory
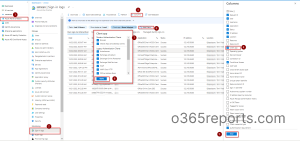
- Navigate to Azure Active Directory Admin Center.
- Select the Azure Active Directory. Select the sign-in logs.
- Use the Columns–>Client apps to add the client apps column.
- To filter deprecated protocols click Add filters–>Client App and select the deprecated protocols (Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, Exchange Web Services (EWS), Offline Address Book (OAB), Outlook for Windows, and Mac, SMTP).
- Click Apply.
You can also monitor the browser and OS versions used in the organization by clicking Columns and adding the Operating system and Device browser column.
How to restrict users from using deprecated client apps?
Though Microsoft has deprecated the basic authentication, admins can extend the deprecation period based on their organization’s requirements. You can also block legacy client apps in the following ways.
- Microsoft 365 Admin Center
- Conditional access policy
Blocking Legacy apps using Microsoft 365 Admin Center
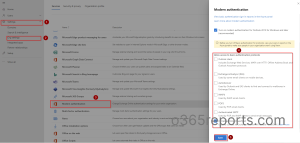
- Open the Microsoft 365 admin center.
- Select Setting –> Org settings.
- Under Services –> Morden authentication. A popup appears.
- Unselect all the basic authentication protocols and click Save.
Blocking Legacy apps using Conditional Access Policy:
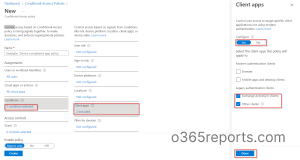
- Navigate to Azure Active Directory Admin Center.
- Browse to Azure Active directory–>Security–>Conditional Access.
- Select New policy.
- Set up a policy name. Under the Users or workload identities segment, select the users for whom you need to block legacy authentication.
- Under the Condition category, select Client apps. Set Configure to Yes and check the Exchange ActiveSync clients and Other clients checkboxes. Then, Select Done.
- Under Access controls–> Grant, select Block access
- After confirming your settings set Enable Policy to
- Click Create to enable the policy.
Proactively Monitor Legacy Client Apps in Office 365 with AdminDroid – A Basic Authentication Buster!
Basic authentication protocols can pose a significant risk to your organization’s security posture, as they are more vulnerable to hacking and cyber threats. Since the native Office 365 reports lack detailed statistics of client apps usage, it provides a loophole to the attackers in any way.
But fear not! AdminDroid offers detailed statistics on authentication methods that are used by your organization’s users to safeguard their client apps from malicious phishing attacks.
It provides 100+ sign-in reports under ‘Analytics’ based on the devices, OS, Authentication methods, and protocols that admins and users configured for their Office 365 tenants.
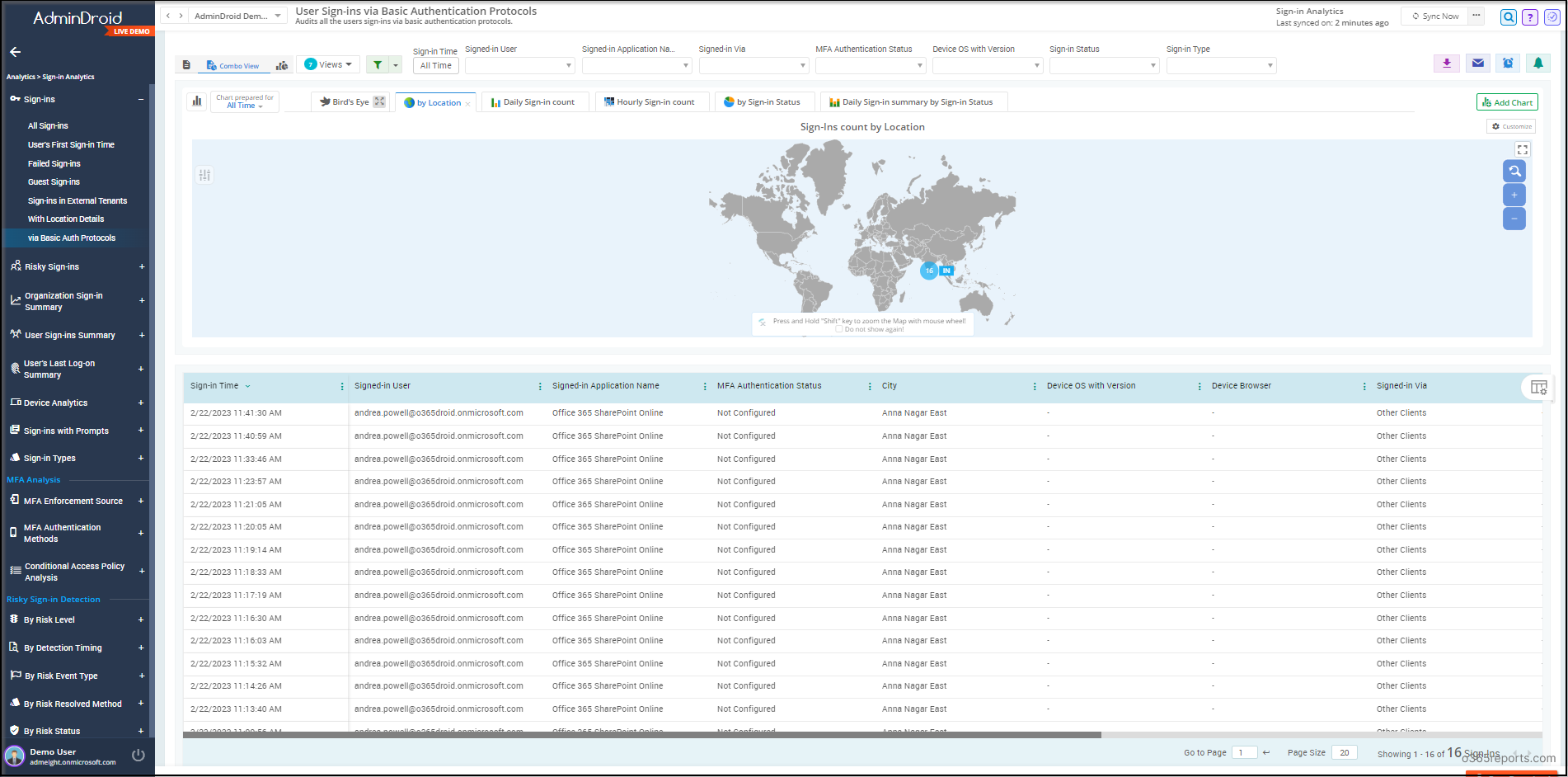
Get to Know the Users Who Are Signed-in Using Basic Auth Protocols:
With the help of AdminDroid, you can easily identify and track down users who are still using basic authentication for Office 365 resources.
- Our comprehensive report provides detailed information on the sign-in type, signed-in application, and MFA authentication status of each user, allowing you to take appropriate action to enhance your organization’s security posture.
- You can also check whether the user configured any second layer of protection in their Office 365 account with the help of authentication details such as authentication methods and MFA authentication status.
AdminDroid can also email you periodically if any user logs in using basic authentication protocols, so you can take swift action to prevent any potential security breaches.
Kick Away the Malicious Attackers by Tracking all the Office 365 Sign-ins!
And that’s not all! AdminDroid’s sign-in analytics provides valuable insights about conditional access checks on legacy authentication, offers clear-cut Office 365 risky sign-in details, detected sign-ins using risk levels, MFA analysis, and many more reports.
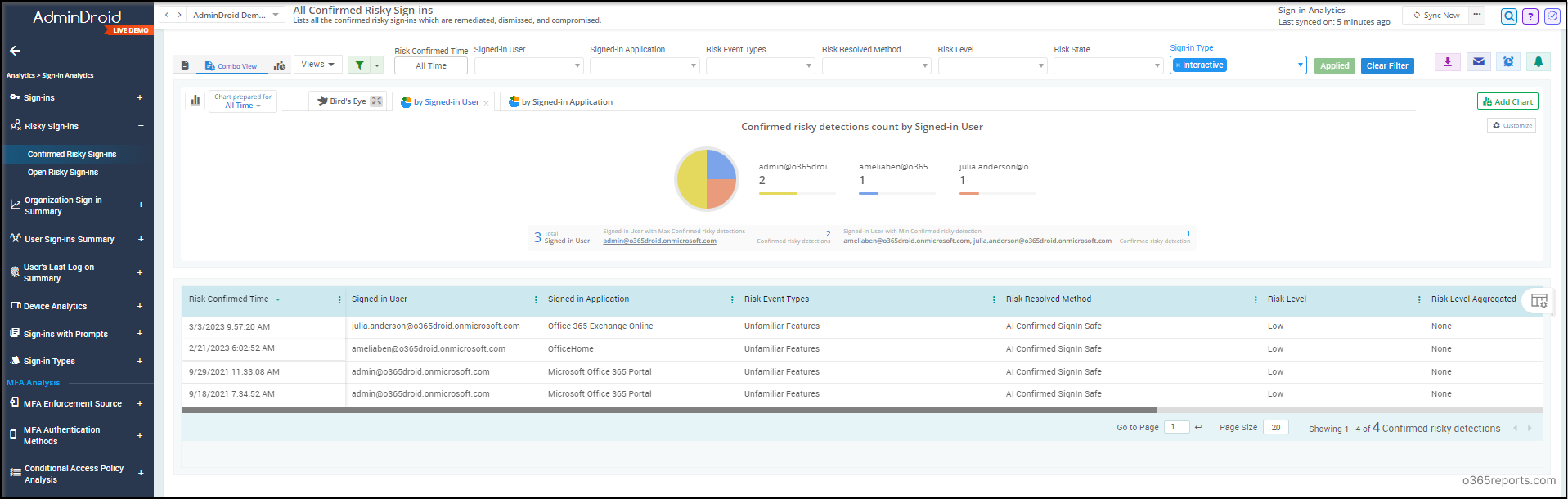
Microsoft is actively working to deprecate basic authentication protocols for all services, which makes it crucial to take action as soon as possible. Thus, with these reports, you can easily pinpoint users who have not enabled robust authentication methods and take appropriate measures to ensure the security of your organization’s data.
Additionally, AdminDroid has the capability of delivering the following must-have features such as detecting suspicious activities, automating the reports, and delegating granularly for efficient Office 365 management.
And that’s just the tip of the iceberg! With free Azure AD AdminDroid reporting, you can get 120+ free reports and will have a basic experience with a wide range of innovative features designed to make Office 365 reporting and auditing easier.
So why wait for the breach? Download AdminDroid today and take control of your Office 365 environment with confidence!
Hope we have fulfilled your requirements regarding the client apps. Feel free to reach us in the comment section. We would be glad to assist you!