Microsoft 365 suite comes with a large set of apps and services, with most of them having a user-friendly interface. However, Microsoft 365 suite is very vast and includes an extensive list of audit logs of all actions performed in an organization. Thus, it has become difficult and time-consuming for the administrators to monitor the suspicious activities and unauthorized actions that are taking place. This is where Microsoft 365 Alert Policies come in.
Using the Alert Policies feature available in the Compliance Center and Microsoft 365 Defender/Security admin center, you can combat this problem. With the help of alert policies, you can monitor user activities and security incidents, such as phishing, unusual external user activities, suspicious massive file or folder deletions, and more.
Contents:
- Requirements for Using Microsoft 365 Alert Policies
- How Alert Policies Work
- Default Microsoft 365 Alert Policies
- How to Create Alert Policies in Microsoft 365
- How To View Alerts and Alert Policies in Microsoft 365
- Disadvantages of Native Alert Policies
- How AdminDroid Simplifies Microsoft 365 Alerting
Requirements for Using Microsoft 365 Alert Policies:
For using Office 365 alert policies, you need to have an E5 license, or an E1 or E3 license with a Microsoft Defender for Office 365 P2, Microsoft 365 E5 Compliance, or Microsoft 365 eDiscovery and Audit add-on subscription. With these licenses, you can set alert policies depending on unusual activities and also provide the threshold.
In case your organization only has an E1 or E3 subscription, you will only be able to create alert policies that will trigger alerts only when an activity occurs.
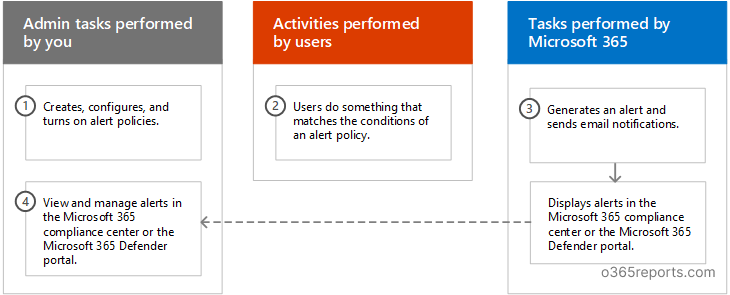
How Alert Policies Work:
There are three components related to the functioning of an alert policy. They are:
-
Alert policy creation:
An administrator can create an alert policy in the Microsoft 365 compliance center or the Microsoft 365 Defender portal. There is also an option of creating alert policies by using the PowerShell cmdlet New-ProtectionAlert. You can configure different alert settings, such as the alert severity, alert category, alert triggering activity, and more.
-
Alert triggering action:
The user then performs an action that corresponds with the conditions of the alert policy. Microsoft 365 then detects the action performed and sends out an alert which can be seen in the Alerts Page of the Compliance Center or Defender Portal. The alert will be triggered based on the configurations of the alert policy and will depend on settings such as the alert severity, alert category, and more. Then, alert notifications are sent out to the list of respective recipients as configured.
-
Alert report:
Alerts can be viewed in the Alerts section in the compliance center with statistics such as alert name, alert severity, alert status, etc.
Configurations of Alert Policies:
The following are the different configurations for alert policies:
- Alert Severity: There are three levels of severity-Low, Medium, and High. You can set the severity as per your preference. Later while resolving the Alerts, you can filter out by prioritizing the severe type of alerts.
- Alert Category: Alert policies can be classified into five categories based on the type of alert they will deal with:
- Threat Management
- Information Governance
- Permissions Mail Flow
- Mail Flow
- Others
- Alert triggering activity: You can create alert policies for activities you want to keep track of. These include activities like detected malware in files, externally shared files, deleted files, and more.
- Alert Conditions: You can set the action that will trigger an alert. You can specify the IP addresses, the user, or the file that triggers the alert.
- When to trigger alert: You can set the threshold on how many times an event should occur before an alert is triggered.
- Email Notifications: You can specify recipients who will receive an email alert once an alert is triggered.
Default Microsoft 365 Alert Policies:
Microsoft 365 includes several in-built templates for alert policies by default, that can track malware and phishing activities, external user actions, unusual file-sharing activity, etc. These are the alert policies that are of the “System” alert type and can be toggled on and off. You can modify the default alert policy configurations on whether to send email notifications, set the notification recipients, and the daily notification limit. A few examples of default alert policies are:
- Email sending limit exceeded: Admins can use this policy to generate alerts when users are sending more emails than the allowable limit. Using this policy, you can control the flow of outbound emails that can be sent by the users of an organization. This alert policy is used when you want to refrain users from sending unnecessary/junk mail. This policy has a medium severity setting.
- Malware campaign detected and blocked: Admins can use this policy for generating alerts when someone tries to send several email messages containing malware in your organization. This policy has a low severity setting.
- Unusual external user file activity: Admins can use this policy for keeping a check on the actions performed by external users on files exclusive to the organization. An alert is triggered when an extremely large number of actions are performed on SharePoint or OneDrive files, by users who are not a part of your organization. This policy has a high severity setting.
How to Create Alert Policies in Microsoft 365:
You can create alert policies from
- Microsoft Compliance Center
- Microsoft Defender portal
Both portals provides same steps to create alert policies but the navigation differs. You can choose the required portal and then create the alert policy.
Method 1: Creating an Alert Policy Using Compliance Admin Center:
- Go to the Compliance admin center and click on Policies from the menu on the left.
- From the Alert dropdown menu, select Alert policies. This will show the list of all the alert policies currently available and have the option of creating a new alert policy.
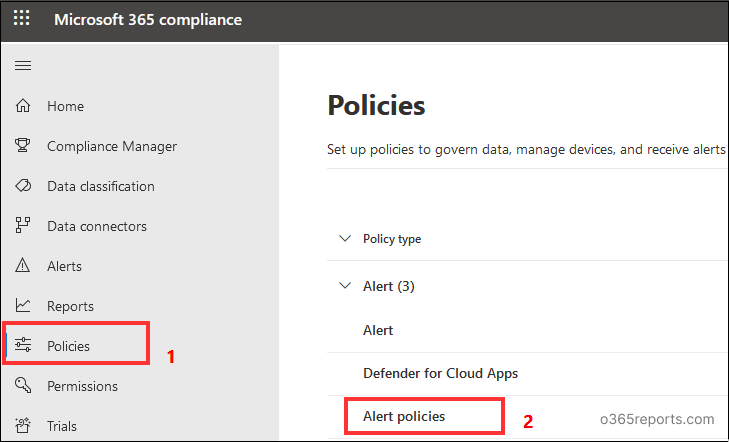
- Click on New Alert Policy. This will open a window that will guide you through the creation of a new Alert policy.
- Now, enter the name and description of the policy. Then select the severity and category of the alert policy.
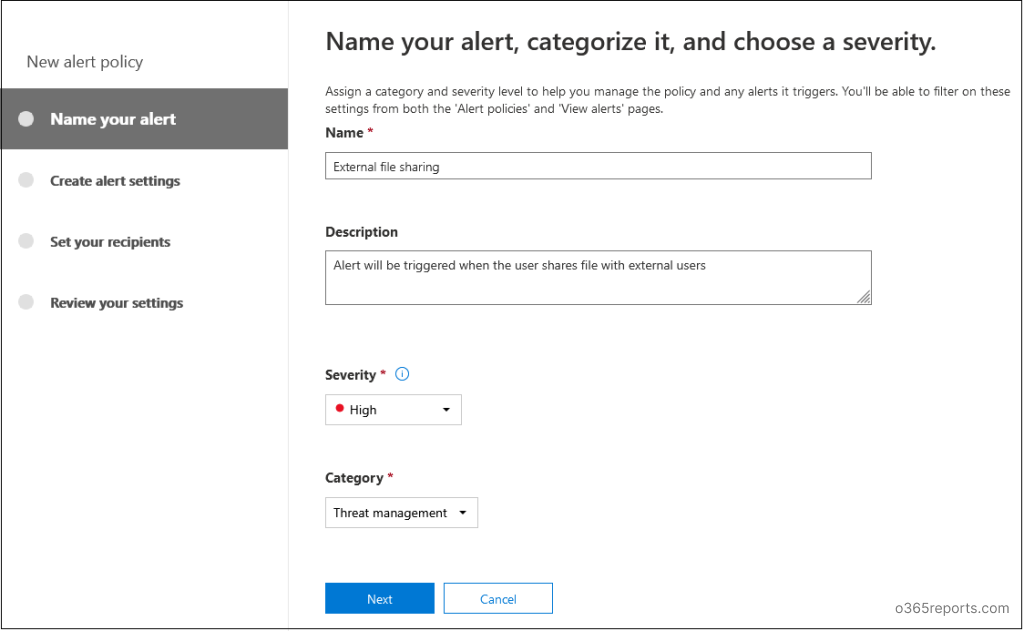
- Select the activity for which the alert is triggered (for example: for specific users or specific IP addresses) and provide additional conditions for when to trigger the alert. Select the threshold on how many times an event should occur before implementing an alert policy.
- Next, specify the recipients to whom the email notification will be sent out in case an alert is triggered. You can also set the daily notification limit for a single alert.
- Review the policy and select whether you want to turn it on immediately or some other time.
- Select Finish to deploy the alert policy.
Method 2: Creating an Alert Policy Using Microsoft 365 Defender Portal:
- Go to the Microsoft 365 Defender portal.
- Select Policies & Rules from the menu on the left under Email and Collaboration and then select Alert Policy. This will show the list of all the alert policies, and you can also create a new alert policy.
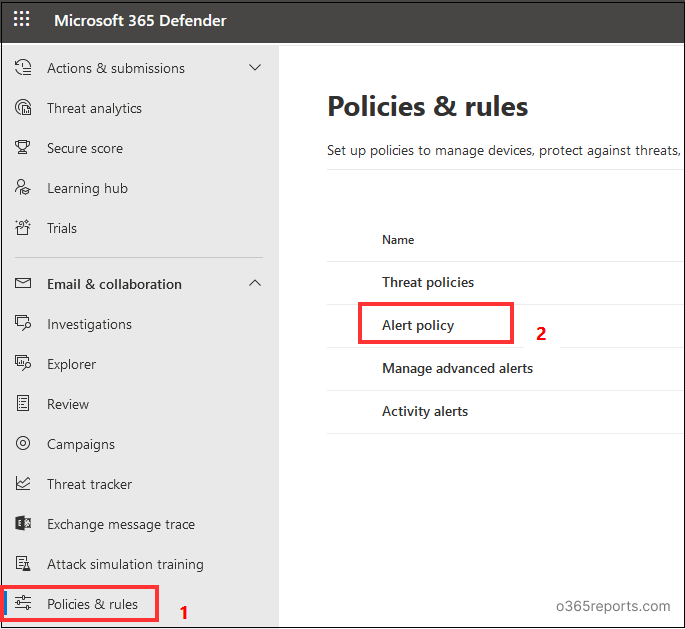
- Click on New Alert Policy. A new window will open to guide you through the process of creating alert policies.
- You can follow the same steps from 4 to 8 given in the ‘Creating alert policies using Compliance center’.
How To View Alerts and Alert Policies in Microsoft 365:
When the users’ activity matches the settings configured in the alert policy, an alert is generated. To view Alerts and configured Alert Policies, you can use the following portals.
Method 1: View Alerts Using Compliance Admin Center:
Click on Alerts in the Compliance center to view the list of triggered Alerts with their details.
Select Policies>Alert Policies from the menu on the left to view the alert policies. All the
alert policies with their details will be listed.
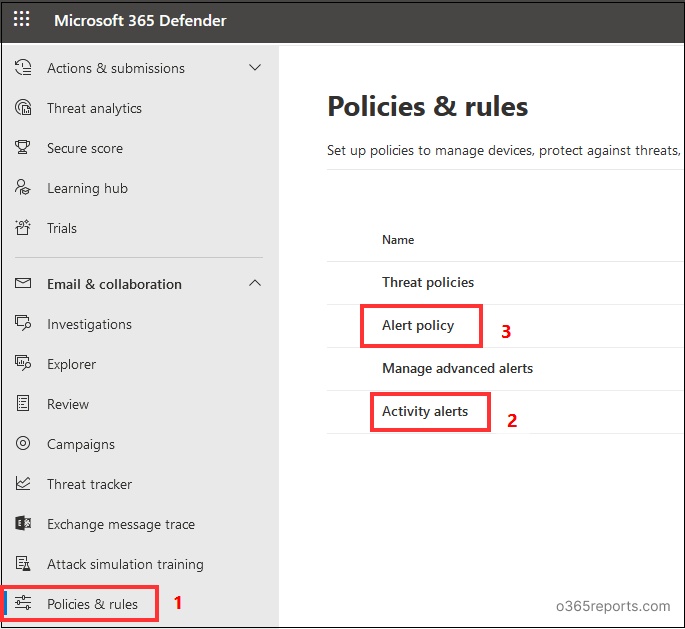
Method 2: View Triggered Alerts Using Microsoft 365 Defender Portal:
Select Policies & Rules>Activity alerts. All the alerts are listed with their corresponding details. This alert queue may contain false positives, low severity, and also some exceptional alerts. To avoid spending time on these low-priority accounts, create alert tuning policies and ensure effective alert management
To view the alert policies, select Policies & Rules>Alert policy. All the alert policies with their corresponding details are listed.
Disadvantages of Native Alert Policies:
- Licensing costs: The number of features you can avail of alert policies depends on the type of license you have. Accessing features such as advanced alerting and additional default alert policies would require you to have a Microsoft 365 E5 plan or other add-on plans. This would result in a higher cost per subscription and thus, it is not very cost-efficient.
- A Limited number of activities available for tracking: The audit log has a list of all the activities performed in the organization. There are only a few pre-defined alert policies available. Also, you can create custom alert policies on only a small number of activities. This is a problem as there will be certain suspicious activities that will not be available for tracking. Hence, automating audit monitoring with Alert policies is not a very good idea.
- Few pre-defined alert categories only available: There are only four pre-defined alert categories available- Threat Management, Information Governance, Permissions, and Mail Flow. The rest of the alerts will come under the other category. As such, it is a big problem as there is no option of creating custom labels as well.
These are some of the main reasons why organizations are shifting from native alerting to third-party alerting tools.
How AdminDroid Simplifies Microsoft 365 Alerting:
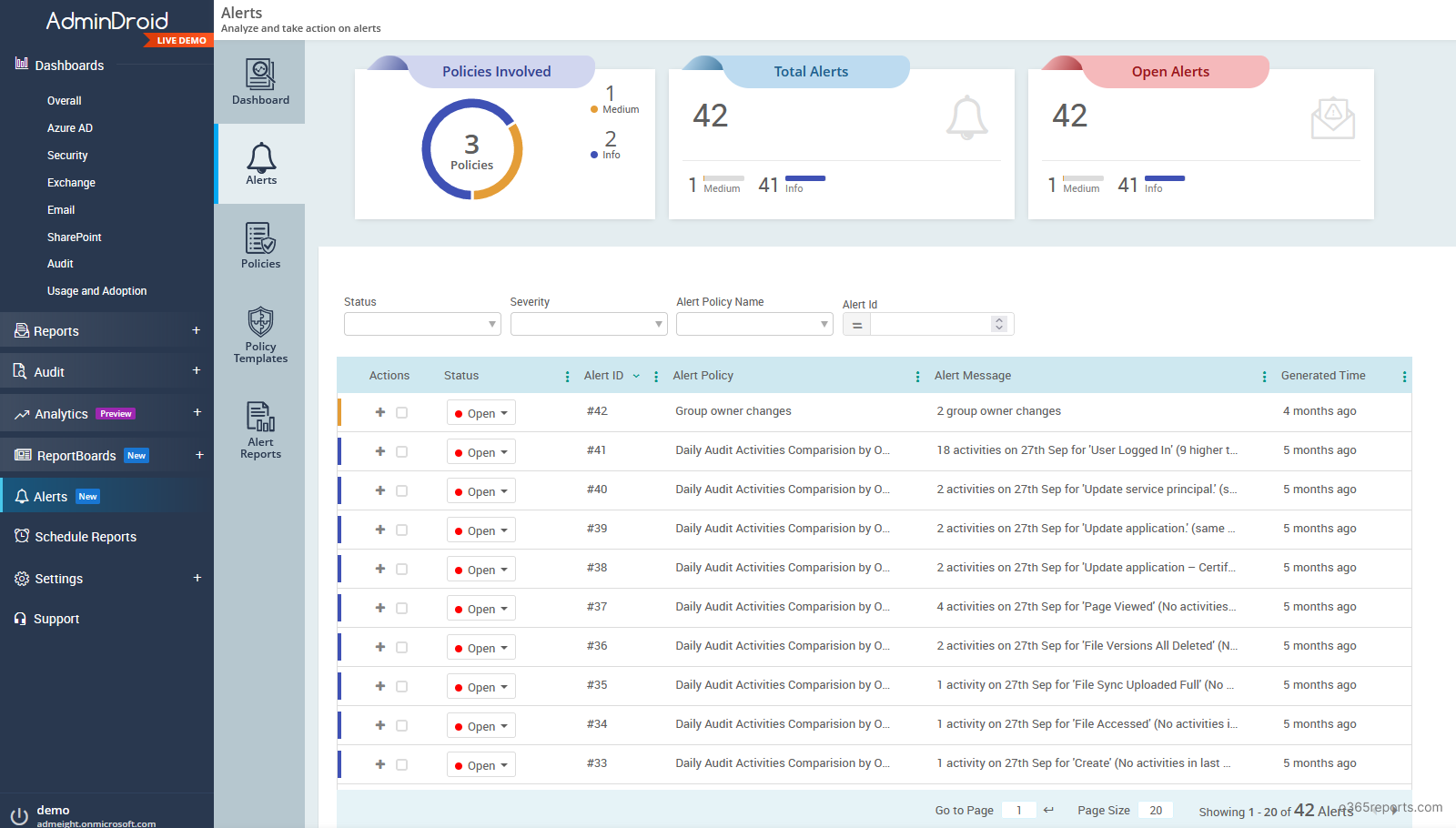
To combat these drawbacks, you can use the AdminDroid Office 365 Alerting tool, which comes with Advanced Alerting capability. It is a very powerful application that will help you view, create and manage alerts in a very easy way. The best part about this tool is that you do not need to have an E5 or equivalent license for the alerting to work, thereby cutting down the licensing cost. The whole application has a very user-friendly interface.
Glimpse of AdminDroid Microsoft 365 alerting tool:
- Assists in identifying new risks and unusual activities by comparing activity trends.
- Monitors 1400+ Microsoft 365 activities.
- Provides option of creating custom labels for alert categories, so you can categorize your alerts in a better manner.
- Gives 48 ready to deploy default templates that are recommended for all organizations.
- Alerts are reported with great detail so that you can react to them swiftly.
- Visualize the alerts, status, and trends quickly in the alert’s dashboard.
- Take immediate action on alerts and mark them as closed or investigating.
- Allows downloading the alerts reports and the alert policy reports.
Be cautious about all malware attacks, risky sign-ins, and unusual activities in your Microsoft 365 environment. Download AdminDroid Microsoft 365 alerting tool and see how it helps you detect risks and cyber-attacks.
Conclusion:
Alert policies are a very useful and highly recommended feature in Office 365, that will help you monitor your Microsoft 365 environment efficiently and help in keeping your organization up to date with any unusual activity going on in your organization’s tenant. As such, it adds a layer of security to your Microsoft 365 tenant.