Consider a scenario where a finance manager at a mid-sized company receives an urgent email from the CEO requesting a $50,000 wire transfer to a new vendor. The email looked legitimate—same signature, same writing style—but something felt off. A quick verification call to the CEO confirmed his suspicion: the email was fake. Hackers had forged the sender’s address to make it appear as if it came from the CEO.
This deceptive tactic, known as email spoofing, is a common method cybercriminals use to impersonate trusted senders, manipulate recipients, and launch phishing attacks. But how does it work, and how can you protect yourself? Let’s dive in.
Is Email Spoofing Always Bad?
Email spoofing has both harmful and legitimate use cases. While attackers often spoof domains to send phishing or spam emails, organizations may also use spoofing for valid business purposes.
Malicious Email Spoofing: Cybercriminals commonly use spoofing to impersonate trusted domains and trick users into revealing sensitive information, such as login credentials or credit card details. In addition, they have also exploited the Direct Send feature in Exchange Online to craft and send spoofed messages, increasing the overall security risk to organizations.
Legitimate Email Spoofing: Despite its risks, email spoofing is necessary for certain business operations. Microsoft 365 organizations may allow spoofing in the following scenarios:
✅ Spoofing Internal Domains:
- Third-party senders deliver bulk emails to employees from an accepted domain.
- External companies send product updates or marketing emails on behalf of the organization.
- Internal applications send automated email notifications.
✅ Spoofing External Domains:
- Mailing lists relay emails from original senders to all subscribers.
- Third-party services send automated reports or notifications on behalf of other companies.
Since both legitimate and malicious spoofing occur, it’s essential to distinguish between these two to ensure business operations run smoothly without compromising security.
What Actions Need to Be Taken?
Admins should ensure that legitimate emails are not blocked by spam filters at either the sending or receiving end. At the same time, malicious emails must be identified and blocked to protect users and organizational data. This is where Spoof Intelligence Insight in the Microsoft 365 Defender portal plays a critical role.
What is Spoof Intelligence Insight in Microsoft 365?
Spoof Intelligence Insights in Microsoft 365 Defender helps admins quickly identify and analyze unauthenticated spoofed emails—messages that fail email authentication (SPF, DKIM, and DMARC) checks. It allows organizations to take informed actions to manage spoofing securely.
License Requirements
To use Spoof Intelligence Insights, your organization must have the appropriate licenses:
- Default email protection for cloud mailboxes
- Microsoft Defender for Office 365 Plan 1 or Plan 2
- Microsoft Defender XDR
Permissions Requirements
Users must be assigned the proper roles to access and manage Spoof Intelligence Insights:
- Defender XDR Unified Role Based Access Control: Manage or read permissions under Email & collaboration > Defender for Office 365.
- Exchange Online roles: Organization Management, Security Administrator, or View-Only roles to allow/block spoofed senders; Global Reader or Security Reader for read-only access.
- Microsoft Entra roles: Global Administrator, Security Administrator, Global Reader, or Security Reader.
With Spoof Intelligence Insight, you can:
- Identify and review spoofed senders to determine if they are legitimate or malicious.
- Manually allow or block spoofed senders based on reputation, location, or other factors.
- Monitor allowed spoofed senders to ensure continued security and prevent potential threats.
How to View Spoof Intelligence Insights in Microsoft Defender?
Follow these steps to access Spoof Intelligence Insights in Microsoft Defender:
- Log in to the Microsoft Defender portal.
- Navigate to Email & collaboration > Policies & rules > Threat policies > Tenant Allow/Block Lists (under the Rules section).
- Select the “Spoofed senders” tab.
- Under this tab, you’ll find an insight stating “<number> of domains spoofed in the past 7 days” with a clickable link View spoofing activity to explore further details.
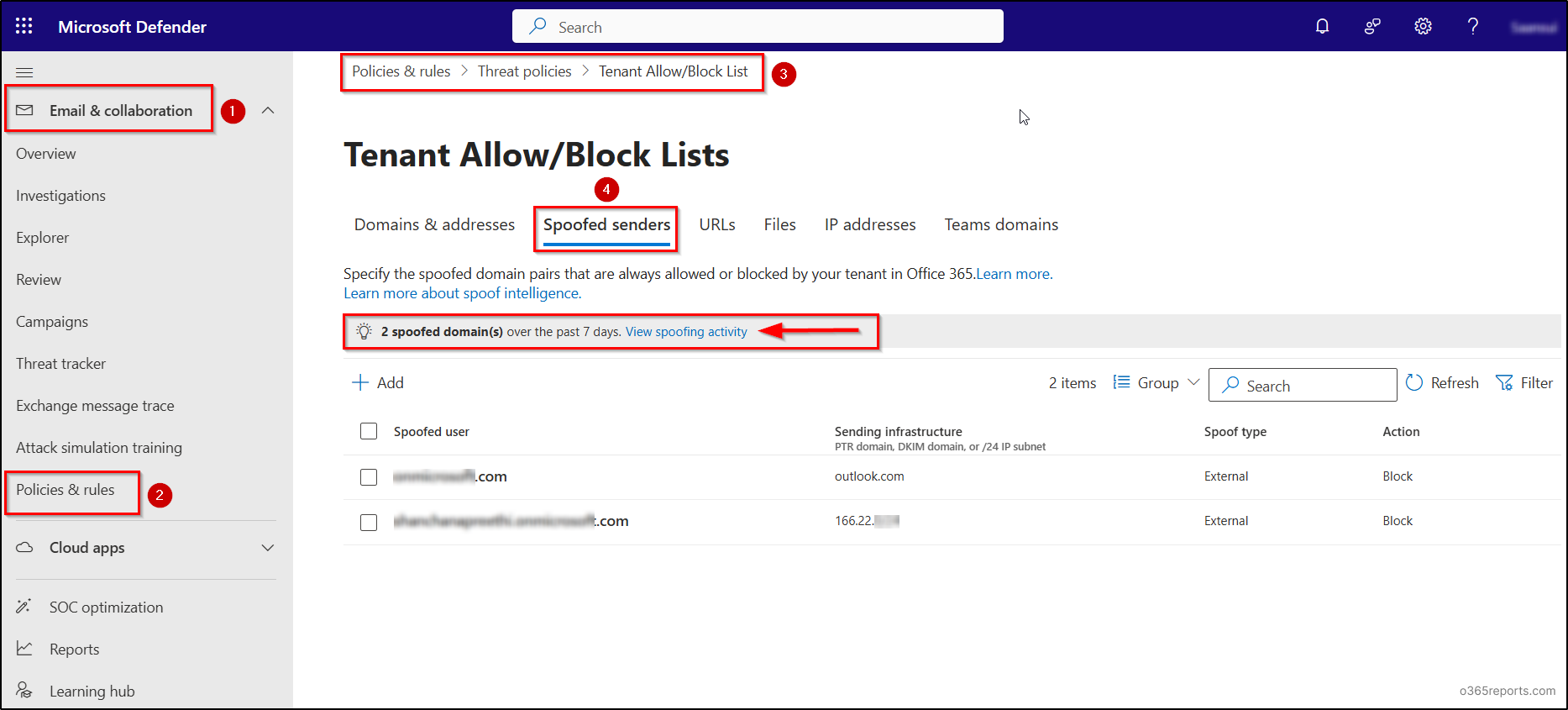
The insight operates in two modes depending on whether Spoof Intelligence is enabled:
- Insight Mode: If enabled, it shows how many messages were detected as spoofed in the last seven days.
- What If Mode: If disabled, it estimates how many messages would have been detected as spoofed in the last seven days.
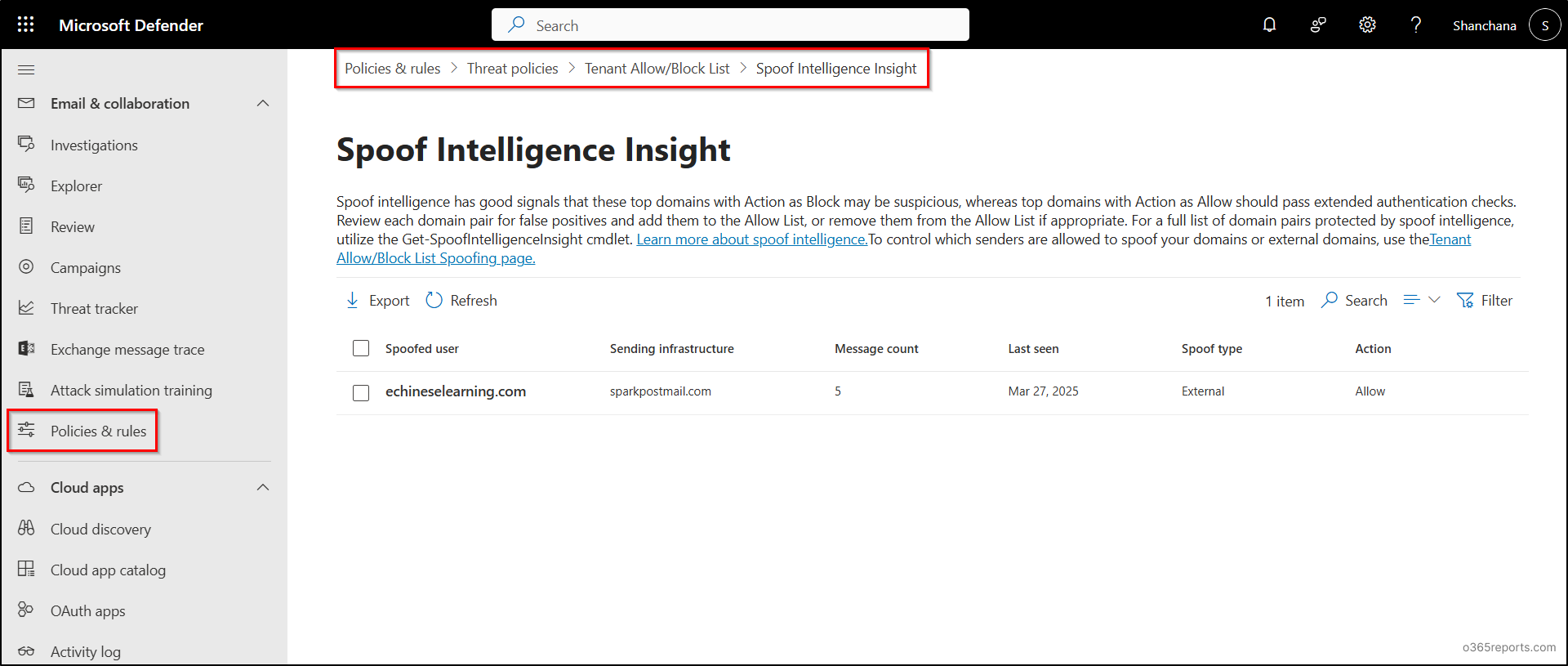
Microsoft 365 Spoof Intelligence Insights
On the Spoof Intelligence Insight page in the Microsoft 365 Defender, you can view and sort details about detected spoofing attempts using the following key columns.
| S.No | Column Name | Column Values |
| 1 | Spoofed user | Displays the domain of the spoofed sender shown in the “From” field of email clients (also known as the 5322.From address). |
| 2 | Sending infrastructure | Shows one of the following values based on the sending source:
|
| 3 | Message count | Total number of spoofed messages received from the spoofed domain in the last 7 days. |
| 4 | Last seen | The most recent date when a message was received from the spoofed domain. |
| 5 | Spoof type | Indicates whether the spoofed domain is:
– Internal: Belongs to your organization (an accepted domain). – External: Does not belong to your organization. |
| 6 | Action | Indicates whether the spoofed message was Allowed or Blocked:
– Allowed: Domain failed SPF/DKIM/DMARC but passed implicit (composite) authentication; no anti-spoofing action was taken. – Blocked: Marked as bad by spoof intelligence; action is enforced via preset security policies. |
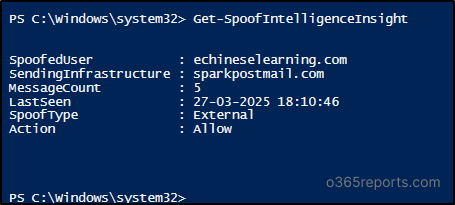
Get Microsoft 365 Spoof Intelligence Insight Using PowerShell
By default, Microsoft Defender provides Spoof Intelligence Insights for the past 7 days. However, you can use PowerShell to retrieve spoof analysis data for up to 30 days.
Before proceeding, ensure to connect to the Exchange Online PowerShell. Once connected, execute the Get-SpoofIntelligenceInsight cmdlet as shown below to retrieve spoof data.
|
1 |
Get-SpoofIntelligenceInsight |
How to See Spoofed Email Activity in Microsoft 365?
To view detailed spoofed email activity and analyze potential threats in your organization, you can use the Spoof Detections report in Microsoft 365 Defender or retrieve the data via PowerShell.
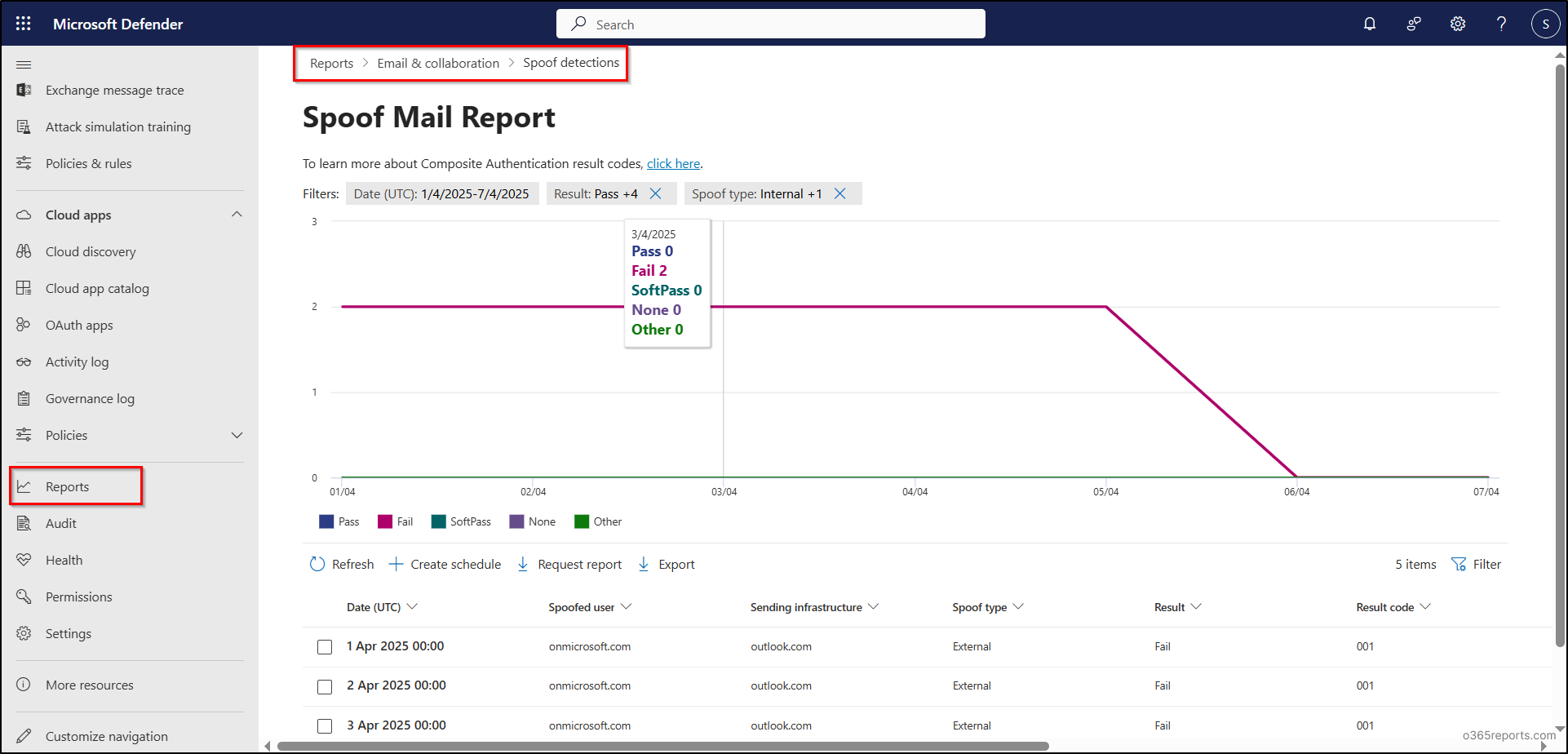
View Spoof Detections Report in Microsoft 365 Defender
- Go to the Email & collaboration reports page in the Microsoft Defender portal.
- Find the Spoof Detections card and click View details to open the report.
The report displays a list of spoofed emails detected within your Microsoft 365 environment. Both the chart and report views support filtering data for up to 90 days. Keep in mind that the latest data in the report may be delayed by 3 to 4 days.
Detect Spoofed Emails Using PowerShell
You can also export spoofed email activity using the ‘Get-MailDetailATPReport’ cmdlet in PowerShell. Before running the cmdlet, make sure to connect to the Exchange Online PowerShell.
|
1 |
Get-MailDetailATPReport -EventType "Spoof DMARC","Spoof intra-org","Spoof external domain" |
This cmdlet fetches details of emails flagged as spoofed based on DMARC failure, intra-org spoofing, or external domain spoofing.
By regularly monitoring email protection reports for spoofed email activity, you can enhance your security posture and take timely action against phishing or impersonation attacks.
Now that you understand what email spoofing is and how to identify spoofed emails in Microsoft 365, you might be wondering how to prevent such incidents from affecting your organization in the future. To combat email spoofing and protect your organization, Microsoft offers Anti-Spoofing Protection within Exchange Online Protection (EOP).
What is Anti-Spoofing Protection?
Anti-spoofing protection is a feature in EOP designed to detect and block emails that appear to originate from trusted domains but are actually sent from unauthorized or malicious sources. It analyzes incoming messages to identify and mitigate spoofing attempts, thereby preventing phishing attacks and unauthorized use of your domain.
In Exchange Online Protection (EOP), anti-spoofing protection technology focuses on detecting and preventing email spoofing by analyzing the ‘From’ header in email messages. This header represents the sender’s address displayed in email clients. When EOP determines with high confidence that the ‘From’ header has been forged, it classifies the message as spoofed and takes appropriate action to protect recipients.
In a nutshell, regularly monitor email spoofing reports to identify threats, take corrective actions, and strengthen your organization’s email security posture. By staying vigilant and making informed decisions, you can reduce the risk of spoofed emails reaching your users. We hope this blog has offered helpful insights into Microsoft 365 email spoofing and supports your efforts to prevent it.