In Microsoft 365, enabling or disabling a user account isn’t just a routine admin task; it’s a critical security event. Every change to a user account’s status can affect both access to sensitive data and the organization’s overall productivity. A compromised account, for example, can disrupt workflows and create security risks across the organization.
That’s why it’s essential to know who performed the action, when it happened, whether it succeeded or failed, and where it originated from. Without a clear audit trail of these events, organizations risk unauthorized access, compliance violations, and operational confusion. Tracking account enable/disable activities in detail helps maintain security, prove compliance, and ensure accountability in your M365 environment.
How to Track User Account Enable/Disable Events in Microsoft 365?
Here are a few ways to track account status changes in Microsoft 365:
Audit log search: You can search the audit logs using the “Updated user” activity to see when user accounts are enabled/disabled. However, this method shows all user property updates, and there’s no built-in filter to view only enable or disable actions.
PowerShell: Using the Search-UnifiedAuditLog with the -Operations “Update user” parameter lets you retrieve details about updated user properties. But, similar to the audit log, filtering specifically for enable/disable events is not straightforward. The logs record every user property change, from display name updates to license assignments. Isolating just account activation or deactivation therefore requires extra filtering or parsing, which is time-consuming and often demands custom PowerShell scripting.
To simplify this process, we’ve created a PowerShell script that audits account changes, highlights user enable/disable events, and generates clear, easy-to-read reports.
Download Script: AuditUserAccountStatusChanges.ps1
Script Highlights:
- The script automatically verifies and installs the Exchange Online PowerShell module (if not installed already) upon your confirmation.
- Tracks all Microsoft 365 user account status change events for the past 180 days.
- Allows you to retrieve enabled and disabled account activities for a custom date range.
- Generates a report of successfully completed account enable or disable actions.
- Exports only the failed account enable/disable events.
- Captures account status change events specific to guest users.
- Audits account status change events specific to internal users.
- The script can be executed with MFA-enabled account too.
- It exports the report result to CSV format.
- It can be executed with Certificate-based Authentication (CBA) too.
- The script is scheduler-friendly.
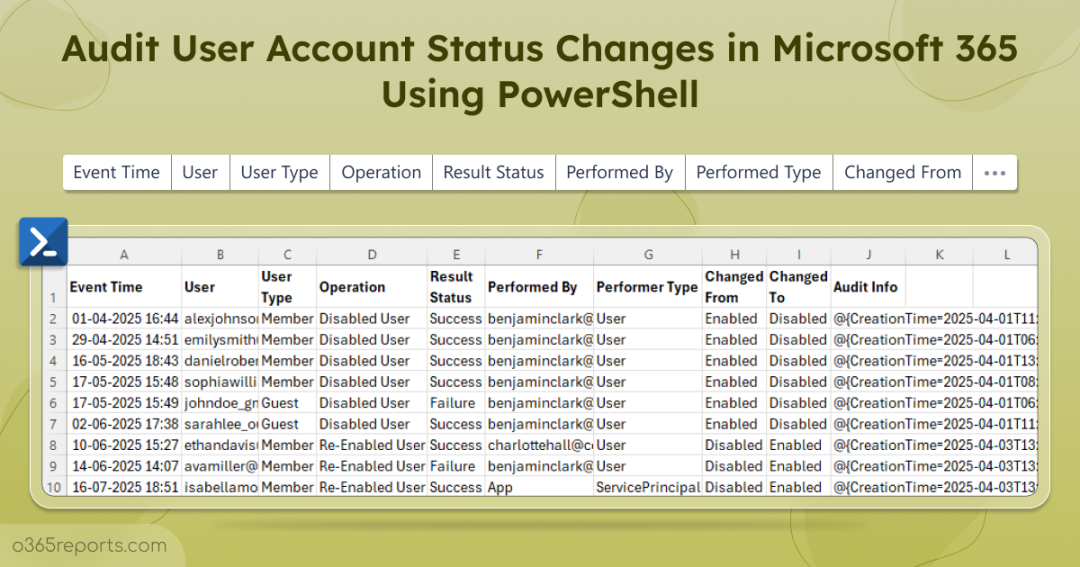
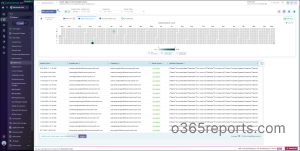
M365 Users Account Status Changes Report – Sample Output
The exported report of Microsoft 365 user account status changes appears as shown in the screenshot below:
The script exports account status change events along with attributes such as Event Time, User, User Type, Operation, Result Status, Performed By, Performer Type, Changed From, Changed To, and Audit Info.
Audit User Account Status Changes – Script Execution Steps
- Download the script.
- Start Windows PowerShell.
- Select any of the methods provided to execute the script.
Method 1: Execute the script with MFA or non-MFA account.
|
1 |
.\AuditUserAccountStatusChanges.ps1 |
This method will export all account status change events over the past 180 days.
Method 2: Execute the script by explicitly mentioning credentials.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -UserName admin@contoso.com -Password XXX |
The above method supports only non-MFA accounts. For admin accounts with MFA, you must disable MFA using the CA policyfor this method to work.
Method 3: Execute the script using certificate-based authentication. This method is scheduler-friendly.
To use certificate-based authentication, you must register app in Entra ID, which help you connect Exchange Online PowerShell using certificate.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -Organization <Domain> -ClientId <AppId> -CertificateThumbprint <CertThumbPrint> |
You can either use a CA certificate or create a self-signed certificate, which is cost-effective.
Make the Script Work for You!
With a range of filters built in, this script can meet different requirements. Here’s how to make it work for you:
- Generate an audit report for a custom period
- Monitor when user accounts are enabled in Microsoft 365
- Review when user accounts are disabled in Microsoft 365
- Track successfully completed user account status changes
- Identify failed user account enable/disable attempts
- Track account enabled/disabled events for guest users
- Audit account enabled/disabled events for internal users
- Find account status changes made by a specific user
- Identify all account status changes affecting a specific user
1. Generate Account Status Change Report for a Custom Period
By default, the script displays account sign-in status change activities for the past 180 days. If you want to audit activities for a specific date range, you can use the -StartDate and -EndDate parameters.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -StartDate 06/20/25 -EndDate 07/24/25 |
This format generates a report containing all account status change activities between June 20 and July 24.
2. Monitor When User Accounts Are Enabled in Microsoft 365
Auditing account status enabled activities is essential because enabling a user account grants access to Microsoft 365 resources, including sensitive data, applications, and organizational information. By auditing these actions, administrators can verify that new hires, returning employees, or contractors are granted correct access and ensure that all enabled events are properly tracked.
To track all user account sign-in status enabled events in Microsoft 365, use the –EnabledEventsOnly switch as follows.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -EnabledEventsOnly |
This report shows when user accounts were enabled in Microsoft 365, making it easy to track who gained access and when.
3. Review When User Accounts Are Disabled in Microsoft 365
Disabled user accounts, if left unnoticed, can lead to confusion in group memberships and unnecessary license usage. To check all user account disabled events in Microsoft 365, use the –DisabledEventsOnly switch as follows.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -DisabledEventsOnly |
This report shows when user accounts were disabled in Microsoft 365, helping you track who lost access and when.
Tip: Additionally, generate a report of groups with disabled users to spot inactive memberships, maintain proper access and find unused licenses to cut costs and boost security.
4. Track Successfully Completed User Account Status Changes
Filtering only successful operations helps streamline compliance audits by confirming which account status changes were actually implemented. For example, if a user’s account was temporarily disabled due to suspicious activity, using the -SucceedOnly switch lets you quickly verify that the disable action was completed successfully, without showing other failed attempts.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -SucceedOnly |
This command lists all enable or disable actions that were executed successfully for user accounts in Microsoft 365.
5. Identify Failed User Account Enable/Disable Attempts
Failed operations can indicate misconfigurations or potential unauthorized attempts to modify account statuses. For example, repeated failed attempts to disable a user account could signal a compromised account or suspicious activity. Using the -FailedOnly parameter, this script helps you quickly identify such patterns, enabling faster investigation and response to possible security threats.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -FailedOnly |
This report shows all account status changes that failed in Microsoft 365, helping you spot issues or unauthorized attempts.
6. Track Account Enabled/Disabled Events for Guest Users
Tracking guest user account status changes helps ensure external access is properly managed and controlled. Misconfigured external user settings or cross-tenant collaboration policies in Entra can lead to unauthorized access or collaboration issues. Using the -GuestUserOnly switch, you can quickly audit guest account changes and detect potential misconfigurations.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -GuestUserOnly |
This report shows when guest user accounts were enabled or disabled in Microsoft 365, making it easy to review external access activity.
7. Audit Account Enabled/Disabled Events for Internal Users
Monitoring internal user account status changes ensures proper control over employee access and helps detect any unusual or unauthorized modifications. To retrieve these events, use the -InternalUserOnly switch as shown below.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -InternalUserOnly |
This report shows when internal users’ accounts were enabled or disabled in Microsoft 365.
8. Find Account Status Changes Made by a Specific User
Knowing which user is responsible for a change allows you to quickly address unauthorized actions and maintain proper access controls. Using the -PerformedBy parameter, you can verify if an admin actually performed the action, identify activities done by apps or users, and filter actions performed by a specific user or admin.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -PerformedBy "admin@domain.com" |
This command generates a report of all account status change activities performed by the specified user in Microsoft 365.
9. Identify All Account Status Changes Affecting a Specific User
If you want to see all changes made to a particular user’s account, in other words whose account was affected, the -TargetUser parameter lets you track and verify these modifications.
|
1 |
.\AuditUserAccountStatusChanges.ps1 -TargetUser "user@domain.com" |
This report shows when the specified user’s account was enabled or disabled in Microsoft 365.
Simplify Microsoft 365 Account Status Tracking with AdminDroid
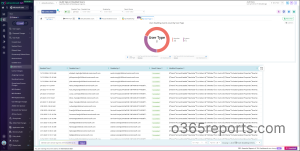
PowerShell offers granular control, but it doesn’t clearly surface enable/disable events, forcing admins to sift through every user update, apply complex filters, and write custom scripts. AdminDroid solves this with ready-to-use reports that instantly show account status changes.
With AdminDroid M365 reporting tool, , you don’t just see which accounts are enabled or disabled. You can audit every change with complete context. Reports can be filtered by time, user type, or result status to focus on specific events. You can also analyze daily and hourly trends of enabled/disabled events and even drill into modified properties to see exactly what changed.
Microsoft 365 User Account Status Reports
- Sign-in re-enabled users
- Sign-in disabled users
- Disabled users
- Enabled users
- Sign-in disabled service principals
- User sign-in activity overview
- All user sign-ins with detailed information
- Groups with sign-in disabled members
Entra ID User Login Reports
- All user logins
- Successful/failed login attempts
- First/last logon time for each user
User Action Audit Reports
- All user events
- MFA-enabled/disabled users
- User sponsors added/removed
- License changes
- Password reset/change activities
The free Entra ID auditing tool deliver unmatched insights into user activity, group dynamics, password changes, and more.
And the best part? The AdminDroid’s management tool allows you to take direct actions like enabling or disabling users without having to switch between tools.
The full AdminDroid suite offers 3,500+ reports, 100+ dashboards, and 450+ management actions across Teams, Exchange, OneDrive, Entra ID, and other Microsoft 365 services—all in one intuitive interface.
Unlock advanced features with a 15-day premium trial, including reporting, alerting, delegation, and compliance tools.
Download AdminDroid today and simplify your Microsoft 365 management with effortless reporting and administration.
We hope this blog has been useful in providing you with the PowerShell script for auditing enabled and disabled user account events by admins in Microsoft 365. Thanks for reading. For further queries, reach out to us in the comments section.