We all know that any user in Microsoft Entra ID can read the users’ details and directory information using Entra ID portal, PowerShell, and Graph API Explorer. Although restricted from making changes, non-admins can still explore user information, group details, device details, etc. This poses a big security issue as hackers always exploit the least privileged users to gain access to extensive information within your Microsoft 365 environment. So, let’s dive deep into learning how to restrict user access to Azure AD PowerShell and Microsoft Graph Explorer.
Where Can Non-Admins Access Entra Directory Information?
Users can access other users’ information in several ways, even if they’re not admins.
- Admin Center and Entra ID Portal: Users can navigate to the Microsoft 365 admin center as well as the Entra ID portal to access user information.
- PowerShell: Through PowerShell commands, users can retrieve directory information from Microsoft Entra ID. Even if they are not admins, they can execute cmdlets like ‘Get-MgUser’, ‘Get-MgGroup’ cmdlets to retrieve user and group information.
- Graph Explorer: Microsoft Graph Explorer allows users to interact with Microsoft Graph APIs to access a wide range of data, including user information. Users can authenticate and make API requests to retrieve user details.
As users’ information is scattered everywhere, it becomes essential to restrict non-admins from accessing Entra ID portal, Azure AD PowerShell, Graph PowerShell, and Graph Explorer. Let’s get started.
- Restrict User Access to Azure AD PowerShell
- Restrict User Access to Microsoft Graph PowerShell and Graph Explorer
Restrict User Access to Azure AD PowerShell
Even though Microsoft Graph has become the go-to tool for Entra ID management, MSOnline still remains a powerful option to access user information. To mitigate this security risk, admins can restrict users from accessing Azure AD PowerShell.
1. To block user accounts from accessing Azure AD PowerShell using MS Graph, follow the steps below.
Firstly, connect to the Microsoft Graph PowerShell.
To block users from accessing other users’ data using MSOnline, execute the following cmdlet. The command requires an AuthorizationPolicyId parameter to specify which policy you want to update. You can run Get-MgPolicyAuthorizationPolicy to retrieve a list of all authorization policies.
|
1 |
Update-MgPolicyAuthorizationPolicy -AuthorizationPolicyId <AuthorizationPolicyId> -BlockMsolPowerShell $true |
The ‘-BlockMsolPowerShell’ cmdlet prevents users from using an older tool (MSOL PowerShell) to manage your Microsoft 365 tenant. This doesn’t affect Microsoft Entra Connect or Microsoft Graph.
2. To block user accounts from reading other users’ information using MSOnline, follow the steps below.
Firstly, connect to the Azure AD PowerShell and execute the following cmdlet.
|
1 |
Set-MsolCompanySettings -UsersPermissionToReadOtherUsersEnabled $false |
Here, Set-MsolCompanySettings is used to modify company-wide settings in Microsoft 365. -UsersPermissionToReadOtherUsersEnabled parameter controls whether users have permission to read information about other users.
After running this cmdlet, users still have access to Azure AD through PowerShell, but they cannot read the information of other users. If users attempt to read Azure AD data, they will encounter the ‘Access Denied’ message.

3. To restrict PowerShell access to everyone except a list of admins, Microsoft has developed a PowerShell script. Running this script will block PowerShell for everyone except for a list of admins specified in the CSV file.
Keep in mind – The Azure AD cmdlet and Microsoft script referenced above rely on cmdlets, which Microsoft already retired on March 30, 2024. However, Microsoft ensured MSOnline will continue to function through March 30, 2025. Older versions of MS Online before 1.1.166.0 (released in 2017) won’t get updates anymore and might have problems after June 30, 2024.
Apart from Azure AD PowerShell, users can still navigate to ‘portal.azure.com’ and ‘entra.microsoft.com to access users’ information. Hence, it is advisable to also consider restricting user access to the Azure portal. But executing these methods will block entire user accounts in the organization, which is not cool.
Restrict User Access to Microsoft Graph PowerShell and Graph Explorer
To block non-admin access to Microsoft Graph PowerShell and Graph Explorer, we can use Microsoft Entra admin center or Conditional Access policy.
Block User Access to Microsoft Graph PowerShell in Entra ID
Case 1: Limit User Access to Microsoft Graph PowerShell in Entra ID
To block unauthorized users from accessing Microsoft Graph PowerShell using Entra ID portal, please proceed with the following steps.
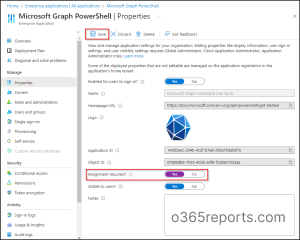
- Open Microsoft Entra admin center.
- Navigate to Identity –> Applications —> Enterprise applications –> All applications.
- Select Microsoft Graph PowerShell.
- Click on Properties under the ‘Manage’ tab.
- Switch the ‘Assignment required?’ toggle to Yes for access restriction.
- Select Save.
If the ‘Assignment required option’ is set to Yes, then users must be assigned to this application before being able to access it.
Note– If you want to entirely block users from signing into Microsoft Graph PowerShell, switch the ‘Enabled for users to sign-in?’ toggle to No on the same page.
Case 2: Add or Remove Users from Accessing Microsoft Graph PowerShell in Entra ID
Now, admins can add specific users or groups who can access Microsoft Graph PowerShell.
- In the same ‘Microsoft Graph PowerShell’ page, click on Users and groups under ‘Manage’ tab.
- Select Add user/group.
- Under ‘Users and groups’, choose the required users and groups, and click on Save.
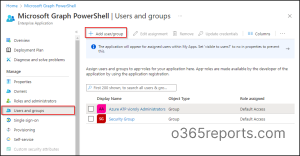
Note – Likewise, you can restrict user access for Graph Explorer application in Microsoft Entra by choosing ‘Graph Explorer’ from the application list. Graph Explorer won’t appear in the ‘All applications’ list unless they’ve been utilized by at least one user.
Now, let’s move on to the next method!
Block User Access to Graph Explorer with Conditional Access Policy
Apart from Entra ID portal, you can make use of the Conditional Access policies to restrict Graph Explorer to a select group of users. However, keep in mind that creating a Conditional Access policy requires at least one Microsoft Entra ID P1 license for your tenant.
To restrict Graph Explorer for specific users using the Conditional Access policy, follow the steps below:
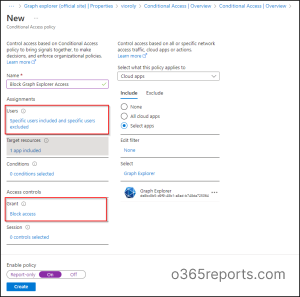
- Open the Conditional Access page in Microsoft Entra admin center.
- Click on Create new policy.
- Name your Conditional Access policy.
- Under Assignments, select ‘Users’. Now specify the users and groups to whom this policy will apply. You can exclude administrators from this policy based on requirements. In case if you want to restrict all users, then select ‘All users’.
- Then, select ‘Target resources’ and choose Select apps from the ‘Cloud apps’ section. Now, click on ‘Search’ and add the application named Graph Explorer. Click on the ‘Select’ button.
- Under Access Controls, select ‘Grant’ and choose the ‘Block access’ option. Then, click the Select button.
- Confirm your settings and enable the policy.
- Click ‘Create’ to create your CA policy.
Note – In the same way, you can block user access to ‘Microsoft Graph PowerShell’ using Conditional Access policy by choosing ‘Microsoft Graph PowerShell’ under ‘Cloud apps’.
By following these steps, you can effectively restrict access to MS Graph Explorer for designated users, blocking the ability for attackers to access user details. Additionally, admins can use PowerShell to export CA policies, allowing them to review and verify policy configurations offline.
Following this, users who try to access the Graph Explorer may encounter an error message similar to the one below:
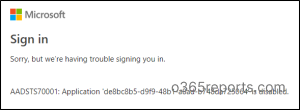
Although these powerful tools like MS Graph PowerShell, and Graph Explorer are helpful in user management, even slight misuse can lead to potential data threats. In this way, you can prevent hackers from exploiting least privileged accounts, ensuring security.
I hope this blog helped you learn how to restrict user access to Azure AD PowerShell, MS Graph PowerShell, and Graph Explorer. If you have further queries, reach us through the comments section.