When it comes to identity and access management, there’s no doubt that Entra and Azure AD B2C take center stage💯. These guardians stand as a holistic defense against threats, fortifying your security of Microsoft 365. By the way, the key to these defenses lies in their configurations.
So, any misconfiguration in these settings could open doors for potential attackers. Therefore, regular monitoring of the Entra settings is crucial for an organization.
To get insights into Entra settings, you might have initially considered Azure AD Exporter. However, it has been deprecated from the PowerShell gallery. So, what’s the next step for obtaining those insights🤔? No worries! The Entra Exporter module steps in to fill the gap. This PowerShell module exports a local copy of Entra and B2C settings configuration similar to the Azure AD Exporter.
Let’s learn how to efficiently backup Azure AD configurations and Azure B2C settings with the Entra Exporter PowerShell module.
Importance of Using Entra Exporter Tool
As the Entra Exporter module exports JSON files of B2C and Entra settings, it becomes the ideal solution for admins to keep backup. Here’s a list of specific reasons why the Entra Exporter is a compelling tool to consider:
- Backup and Versioning: The Entra Exporter’s ability to export Entra settings to JSON files serves as a robust backup mechanism. This becomes valuable in scenarios of data loss or accidental changes. With this feature, you can restore configurations to previous states, ensuring data integrity.
- Nightly Scheduled Task: The Entra Exporter module seamlessly can be integrated with Task Scheduler. This eliminates the need for manual effort, as it facilitates the execution of the cmdlet at scheduled intervals.
- Integration with DevOps Pipelines: Seamlessly integrating with DevOps pipelines, the Entra Exporter maintains an audit trail of setting changes, bolstering transparency and accountability. Moreover, this historical configuration view simplifies troubleshooting and debugging, enabling you to pinpoint changes that might have led to unexpected behavior.
- Replication of Settings: Leveraging the exported JSON files, you can easily migrate or replicate configuration settings across various tenants. This simplifies the process of creating new environments with consistent configurations, reducing the potential for errors and inconsistencies.
- Documentation Purpose: The JSON files exported by the Entra Exporter serve as documentation of configuration settings. This documentation is especially valuable for new administrators who can quickly grasp the Azure AD configurations and can modify changes according to the need.
Thus, the Entra Exporter module, equipped with scheduling capability and integration functionality, empowers you to keep an eye on Azure settings without interruption.
Now, let’ get into the steps to install Entra Exporter PowerShell module.
Install Entra Exporter PowerShell Module
To export Azure AD and B2C settings, you need to download and install Entra Exporter first. You can open the Windows PowerShell in administrator mode and can install the module using the following cmdlet. By the way, it is recommended to use PowerShell 7 or above to achieve optimal output.
|
1 |
Install-Module EntraExporter |
After confirming the prompt, the installation process for the module will be completed within seconds.
Connect Your Microsoft 365 Account Using Entra Exporter
Once the module installation is finished, the subsequent step involves connecting your M365 environment. You can establish this connection by executing the following cmdlet.
|
1 |
Connect-EntraExporter |
Upon executing the aforementioned cmdlet, you’ll be prompted to provide the necessary consent. By granting consent, you enable access to your Microsoft Entra.
Note: Instead of using Connect-EntraExporter , you can use Connect-MgGraph with the following scopes for authentication. Following successful authentication through Connect-MgGraph, you can seamlessly proceed to employ the export cmdlets for your tasks.
|
1 |
Connect-MgGraph -Scopes 'Directory.Read.All', 'Policy.Read.All', 'IdentityProvider.Read.All', 'Organization.Read.All', 'User.Read.All', 'EntitlementManagement.Read.All', 'UserAuthenticationMethod.Read.All', 'IdentityUserFlow.Read.All', 'APIConnectors.Read.All', 'AccessReview.Read.All', 'Agreement.Read.All', 'Policy.Read.PermissionGrant', 'PrivilegedAccess.Read.AzureResources', 'PrivilegedAccess.Read.AzureAD', 'Application.Read.All’ |
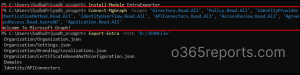
Backup Azure AD Configurations and Objects Via Entra Exporter
Once you’ve established a successful connection with the tenant, you can utilize the following cmdlet to export Azure AD and B2C settings. However, it’s important to note that the given cmdlet exports fundamental Entra settings alone. Because the below default cmdlet is intentionally designed to prioritize the settings and objects that administrators use the most. So, details about the static groups, group memberships, applications, service principals, users, PIM are not exported by this default cmdlet.
|
1 |
Export-Entra -Path '<JSONfilePath>' |
This cmdlet will export the list of settings and objects showed in the below screenshot.
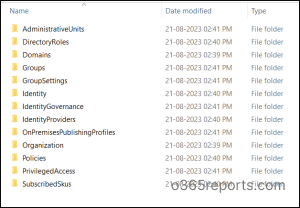
To retrieve additional Entra settings, you need to run the Export-Entra cmdlet with “All” parameter.
|
1 |
Export-Entra -Path '<JSONfilePath>' -All |
Here you can be able to view the additional settings like privileged access, groups, identity governance, etc.
Note: This module exports all Azure AD configurations that can be accessed via the Microsoft Graph API, with the exception of specific settings and objects such as Enterprise State Roaming and a few others that are currently not supported by the Graph API. As this tool exports configurations via the MS Graph API, its activities are captured in the Microsoft Graph activity logs.
Backup Specific Entra ID Settings and Objects with Entra Exporter
Since this module includes a filtering capability, you can utilize it to generate JSON files containing specific Entra objects, such as groups, PIM configurations. Instead of scouring through an extensive array of Entra settings, you can focus solely on the settings you require.
To get details of specific settings/objects, you can run the given cmdlet with the ‘Type’ parameter like below.
|
1 |
Export-Entra -Path '<JSONfilePath>' -Type <SpecificObjectorSetting> |
Note: Currently this module supports the few valid ‘Types’ alone. To know the valid Types, you can run the below cmdlet.
|
1 |
(Get-Command Export-Entra | Select-Object -Expand Parameters)['Type'].Attributes.ValidValues |
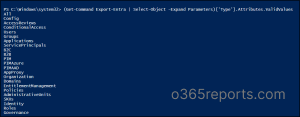
We have illustrated the utilization of the cmdlet by showcasing its execution with several valid Types, aiming to provide you with a clear example.
- Gain service principal information via Entra Exporter
- Export App registration details with Entra Exporter Module
- Monitor directory roles using Entra Exporter
- Export M365 license details into JSON file
- Review tenant policies using Entra Exporter
- Back up Azure AD users using Entra Exporter module
- Review Microsoft 365 groups with Entra Exporter
- Extract Conditional Access policy details to JSON files
- Get details of PIM settings with Entra Exporter
Gain Service Principal Details via Entra Exporter
Service Principals are the secure identities used by applications, and services to authenticate and access Entra. So, you need to monitor the service principal settings regularly to prevent malicious attacks in the organization.
To get details of the service principals created in your Microsoft 365 environment, you can make use of the cmdlet below.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type "ServicePrincipals" |
This will export all the details of Service Principals in JSON format. Added to that, you can effectively monitor service principal sign-ins to track daily application usage and resource access in the organization. By observing this, you can easily identify unusual sign-in activities in your organization.
Sample JSON Format:
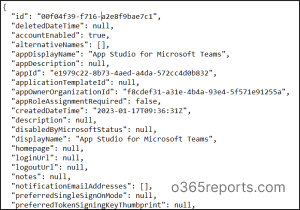
Export Azure AD App Registration Details with Entra Exporter Module
To retrieve the details of the Azure AD app registrations, simply run the default export cmdlet with “Applications” Type like below. This will export all the registered applications to your tenant along with the details like application Id, app creation time, OAuth2Permissions, token issuance, etc.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type "Applications" |
Sample JSON Format:

Monitor Entra Roles Using Entra Exporter PowerShell Module
Reviewing O365 users with Entra roles is crucial due to the possibility of misconfigurations in role assignments. Such misconfigurations can lead to security vulnerabilities in Microsoft 365. So, you can use the below cmdlet to review Azure AD role assignments in your organization.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type "Roles" |
Sample JSON File:
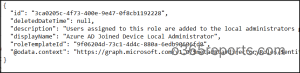
The given cmdlet primarily provides the user’s ID associated with the designated Azure AD role. However, recognizing users solely by their IDs might not be optimal for quick identification. To address this, you can use the PS script provided in the blog to export Office 365 admin role report. The exported report will display the name, email address, and other relevant information of users with Entra roles.
Export M365 License Details into JSON File Using PowerShell
By exporting license data, you gain a clear and comprehensive overview of your organization’s license details. This will help you to check the license availability in your organization.
You can use the below PowerShell cmdlet to export license details using “SKU” Type.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “SKUs” |
Sample JSON File:

By the way, you can make use of the PowerShell script to get detailed Microsoft 365 license report with subscription name, subscribed date, subscription type, license expiry date, subscription status and more. These comprehensive insights help you to renew your licenses in a timely manner.
Review Azure AD Tenant Policies Using Entra Exporter
You can gain insights into policies like authentication method policy, token issuance policies, token lifetime policies using the Entra Exporter.
To export tenant policy configurations, you can use the below cmdlet.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “Policies” |
Sample JSON File:
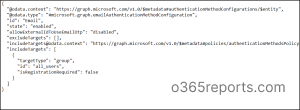
Export M365 Users to JSON Files
Reviewing Microsoft 365 user details is crucial to maintain security and compliance within the organization. But manually navigating through user accounts in the admin center to find specific data is time-consuming. However, you can significantly reduce this effort by employing Entra Exporter to export all user account details into a JSON format.
To do so, you can utilize the below PowerShell cmdlet.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “Users” |
Sample JSON File:

Review Microsoft 365 Groups with Entra Exporter
Monitoring Microsoft 365 groups’ details and configurations is crucial for enhancing data security and access control. You can use the below Entra Exporter cmdlet to export Microsoft 365 groups.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “Groups” |
The exported JSON format contains details like groupId, membership type of the group, mailbox status, guest user access permission, group expiration date, and various other relevant information.
Sample JSON File:

Additionally, you can utilize the PowerShell script provided in the blog to export a more detailed Microsoft 365 group report. This script enables you to gain insights into group memberships, group sizes, member counts within each group, identification of empty groups, and more.
Extract Conditional Access Policy Details to JSON Files
To keep track of changes in your Conditional Access policies and named locations, you can leverage the power of Entra Exporter PowerShell module.
The Entra Exporter cmdlets below enables you to export Conditional Access policy details into JSON files. These files serve as a valuable resource for reviewing and auditing your security settings over time.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “ConditionalAccess” |
Sample JSON File:

Get Details of PIM Settings with Entra Exporter
PIM enables you to manage access to critical resources in your organization, with its three components: Microsoft Entra roles, Azure roles, and PIM for groups. So, it is essential to monitor and manage PIM settings regularly for an effective access control.
Thus, you can derive a copy of PIM settings anytime by simply running the below cmdlet.
|
1 |
Export-Entra -Path '<JSONfilepath>' -Type “PIM” |
Sample JSON File:

Along with continuous monitoring of PIM settings, you can enhance the security of PIM groups by integrating PIM with Conditional Access. You can also audit PIM role activations to keep track of who actually used privileged roles and when.
Integrate Exported Entra JSON files with GitHub
Along with the task scheduler, this module paves the way for the constant reviewing of Entra settings. However, the superior approach is to integrate the module with the DevOps pipelines. This approach preserves a comprehensive history of Entra settings’ changes. Moreover, it enhances the organization and efficiency of managing your Entra and Azure AD B2C configuration settings.
Also, instead of spending your efforts and time in manual exporting and pushing files to the repository, you can make use of Git commands. This will save you time by automating the process, thereby maintaining a history of settings’ changes efficiently.
To do so, follow the steps below to fulfill the prerequisites for pushing the changes to the remote repository.
- Install Git on your local device and open Git CMD after confirming consents.
- Use the command mkdir <folderName> to create a repository folder.
- Navigate to this folder using cd LocalGit.
- Create a Git repository with mkdir <Repository name>.
Now, run the code below to integrate the JSON file with Git.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
$LocalRepo = '<PathofyourlocalRepository>' $tenantId = '<tenantId>' $remoteRepoUrl = '<remoteRepositoryUrl>' Write-Host 'Switching to the main branch' git config --global core.longpaths true git checkout main Write-Host 'Clearing the local Git repository...' Remove-Item $LocalRepo -Force -Recurse Write-Host 'Installing modules...' Install-Module Microsoft.Graph.Authentication -Scope CurrentUser -Force Install-Module EntraExporter -Scope CurrentUser -Force Write-Host 'ConnectingtoAzureAD...' Connect-EntraExporter -TenantId $tenantId Write-Host 'StartingBackup...' Export-Entra $LocalRepo -All Write-Host 'Updating repo...' git config user.email "<email>" git config user.name "<name>" git add -u git add -A git commit -m "AzureAD Update" git remote add origin $remoteRepoUrl git push -u origin main Write-Host 'Done!' |
🚀 Update 17/11/2025: Entra Exporter 3.0 is Live!
Entra Exporter 3.0. has now been released with major improvements in export coverage, accuracy, and speed.
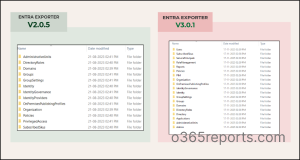
Here’s a breakdown of what’s new:
✅Smarter PIM Export
The entire Privileged Identity Management export is rebuilt using the latest APIs. This delivers more accurate results and replaces the old PIMAzure and PIMAAD options with new, cleaner export categories: PIMDirectoryRoles, PIMResources, and PIMGroups.
✅ IAM Role Assignments & Azure Resource Access Policies Export
You can now export IAM assignments and Azure resource access policies using Azure Resource Graph. This makes it much easier to audit permissions in a single place.
✅ Application Management Policies Export
Tenant default and custom application management policies can now be exported. This is useful for documenting governance settings and tracking configuration changes over time.
✅ Expanded Export Coverage
The exporter now covers even more areas including Teams, SharePoint, Directory Roles, Intune Roles, Cloud PC Roles, Entitlement Management settings, and reports like authentication methods. With this expanded coverage, you get a full snapshot of your entire tenant without switching between multiple tools.
✅ Conditional Access Authentication Context Export
Authentication Context configured in Conditional Access can now be exported, helping you review the advanced access setups to protect the application data and actions.
⚡ Performance Improvements
API calls are now processed in batches instead of sequentially. By sending multiple requests at once, the tool reduces network overhead, avoids throttling, and delivers exports much faster.
If you want to experience these enhancements, update your module using the cmdlet below
|
1 |
Update-Module -Name EntraExporter -RequiredVersion 3.0.1 |
I hope you have learned about the useful PowerShell module which will help you to backup Azure AD configurations and Azure AD B2C settings with just simple cmdlets. Wait! There is a further beneficial tool- “Microsoft365DSC“. You can automate M365 tenant settings with Microsoft365DSC tool across various services Entra ID, SharePoint, Exchange Online, and more, with ease.
Furthermore, feel free to reach us in the comment section for any assistance.