PowerShell makes work easier for admin by automating processes that require repetitions thereby reducing the possibility of errors. There is a common issue that admins face every day when they use PowerShell. As a Microsoft 365 admin, it is difficult to keep typing user names and passwords when connecting to multiple tenants, SharePoint sites, or various Office 365 services. To avoid being prompted for a user name and password in such cases, there are a few ways for it. Let’s check them out!
How can you Bypass PowerShell Prompts?
When running PowerShell scripts, credentials need to be saved in order for them to be fed into scripts that are run autonomously.
Hard-coding the password in scripts – One of the common methods is to write the user name and password directly into the PowerShell script as plain text and then create PowerShell credential object to pass. The method does work to run a PowerShell script bypassing the Get-Credential cmdlet. But it is quite insecure, since PowerShell script stores string variables in plain text. Passwords that are hardcoded can easily be exploited by hackers to hijack into high-powered administrator accounts. Instead of hard-coding passwords within PowerShell scripts, admins must securely store credentials using different methods like PowerShell vault method, PowerShell extension method, etc, to avoid unauthorized access.
Storing Credential in a file – In few situations, admins may store password in a file as a plain text to run PowerShell without prompt. But it is generally not a good idea to store passwords in files. Even if the file is encrypted, there is still a risk that the encryption could be compromised, allowing attackers to access the passwords.
Since the risks associated with storing passwords in a file and hard coding the password in scripts far outweigh any potential benefits, using Credential Manager became more of a practice.
Using Certificates –
Certificates are the best option when you don’t want to enter credentials multiple times to access the network. You can easily create self-signed certificates and use them for internal and testing purposes. For production and external facing environment, you need to use CA certificates, which are expensive. However, only a few services support certificate-based authentication.
Windows Credential Manager – Windows Credential Manager is a user-friendly password manager where you can save credentials for accessing network resources, websites, and apps. It allows keeping 4 types of credentials which includes Windows Credentials, Certificate-Based Credentials, and Web Credentials. In addition to saving your login user names and passwords, Credential Manager also allows you to view, delete, add, backup, and restore credentials.
Let’s dive right in and learn how Windows Credential Manager helps to bypass PowerShell scripts without getting prompted for passwords.
How to Access Windows Credential Manager from PowerShell?
Learn how can you manage saved credentials using Windows Credential Manager by PowerShell.
To access the Credential Manager in PowerShell, the first step is to install the Credential Manager module.
|
1 |
Install-Module -Name CredentialManager |
How to Save Passwords in Credential Manager?
The New-StoredCredential cmdlet helps in storing credentials for different users, tenants or applications.
|
1 |
New-StoredCredential -Target Contoso -UserName admin@contoso.com -Password XXX -Type Generic -Persist LocalMachine |
The above example stores admin credential for the Office 365 tenant Contoso. When you pass persist as local machine, you can view the stored generic credential in UI.

You can retrieve all the stored credentials in the Credential Manager by running the following cmdlet.
|
1 |
Get-StoredCredential |
How to Access Windows Credential Manager using PowerShell?
Using Get-StoredCredential you can retrieve the stored credential and use it in the PowerShell scripts.
To get and store the credential in a variable, run the following cmdlet.
|
1 2 3 |
$Cred=Get-StoredCredential -Target Contoso $Cred |
To connect to multiple Office 365 services without prompting credential popup, you can pass the $Cred while creating session.
For example, to connect to Exchange Online PowerShell, you can call the Connect-ExchangeOnline cmdlet by passing Credential param.
|
1 |
Connect-ExchangeOnline -Credential $Cred |
To check whether you are connected successfully, you can use cmdlets like Get-Mailbox, etc.
If you want to remove the credentials from Windows vault, run the following command:
|
1 |
Remove-StoredCredential -Target Contoso |
So, this is how you can avoid PowerShell credential prompts using Windows Credential Manager.
Storing Passwords in Windows Credential Manager
Apart from PowerShell, get to know how passwords can be stored in Windows Credential Manager. Later, you can retrieve it and use in your PowerShell script.
Step 1: Search for Credentials Manager in your system.
Step 2: Click the Windows Credentials.
Step 3: Navigate to Add a generic credential.
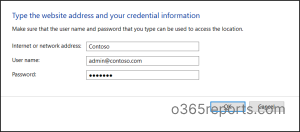
Step 4: Then you will be prompted to a new page where you have to enter the URL, user name, and password.

Say, for example, you are storing the credentials of an Office 365 Contoso tenant user using the Windows Credential Manager.
In Internet or network address section, you need to enter the target. And then enter the User name and Password respectively.
Why Admins Prefer Credential Manager for Efficient Password Management?
Here are a few reasons why admins might prefer to use the Credential Manager to store the credentials.
- User-Friendly Approach – Storing credentials in Windows Vault doesn’t require any hard cmdlets. Users can manually enter the credentials and can run them in PowerShell scripts with ease.
- Scheduled Tasks are no longer a pain – Consider the case of an automated script that runs as part of a scheduled task or an automation framework. No one will likely be monitoring the console to type in a user name and password in these situations. The Get-StoredCredential function can also be easily integrated into scripts that you are running as scheduled tasks.
- Multi-service compatibility – As an in-built feature of Windows, Credential Manager is compatible with a wide range of applications and services. Thus, it is a convenient option for storing credentials on a regular basis.
- Encrypted Storage – With Credential Manager, all of your credentials are encrypted, ensuring that they are secure and protected from unauthorized access.
Although Credential Manager is convenient for storing passwords, there are also some security risks associated with it.
- Your passwords are indeed stored in encrypted format in Credential Manager. But, once your computer gets compromised, hackers can easily be able to access all of your credentials stored at Windows Vault.
- The fact that stored passwords in Credential Manager will not work on account with MFA is highly unamusing. As we all know, Strong MFA practices are required to keep your users away from famous identity attacks such as phishing, MFA fatigue, sim swapping, replay, etc.
- Since the Credential Manager is a basic password manager, it does not offer many of the advanced features that you might find in a dedicated password manager.
In conclusion, the Credential Manager is an essential tool for anyone who uses PowerShell on a regular basis. Whether you are an administrator or simply someone who needs to automate tasks and avoid prompts, the Credential Manager can help you store and manage your credentials, saving you time and improving your productivity. Additionally, integrating Windows LAPS (Local Administrator Password Solution) into your security approach enhances the protection of local administrator accounts. Windows LAPS automates password rotation, ensuring each machine has a unique password securely stored in Active Directory.
I hope this blog helped you gain info on how to use the Windows Credential Manager to store credentials and avoid prompts when running PowerShell scripts. Feel free to leave a comment below with your thoughts on this topic and any other efficient methods you follow for storing credentials.