It’s time to say goodbye to ‘Get-MsolUser MFA Status’. With Microsoft’s plan to deprecate the MS Online and Azure AD PowerShell modules in March 2024, the shift towards migrating to or writing MS Graph PowerShell scripts has begun. Now, it’s imperative to leverage the Microsoft Graph PowerShell module to retrieve the MFA status of Microsoft 365 users in your organization.
If you are fond of the MS Online module, you can use our earlier script to export the MFA status report. It uses the Get-MsolUser cmdlet and ‘StrongAuthenticationMethods’. You can use this report until Microsoft deprecates it. For those who are excited to use Microsoft Graph to get MFA status, let’s start.
June 2024 Update:
Now, MS Graph supports retrieving per-user MFA status through its beta endpoint.
How to Check MFA Status using Microsoft Graph?
You can view Office 365 users’ MFA status through Microsoft Graph API or Microsoft Graph PowerShell. But retrieving MFA status using MS Graph is different from the Get-MsolUser cmdlet.
Microsoft Graph does not provide MFA status directly as enabled, enforced, or disabled. Instead, it will show the list of configured authentication methods for a user. You have to conclude the MFA status based on the authentication method. We have documented a list of authentication methods at the bottom of the blog.
To make it simpler, we have created a PowerShell script by analyzing all the challenges and use cases. This script will help you get MFA status for all users and authentication methods using PowerShell.
Script Download: GetMFAStatusReport.ps1
Script Highlights:
- The script exports MFA status for all users.
- You can filter results based on MFA status. I.e., you can export MFA enabled/disabled users separately.
- Exports report to CSV file
- You can filter the result to display Licensed users alone.
- You can generate MFA report for sign-in allowed users only.
- Shows MFA registration done through Conditional Access and Security Defaults too.
- The script is scheduler-friendly! Therefore, you can automate the report generation easily.
- Automatically installs Microsoft Graph PowerShell module (if not installed already) upon your confirmation.
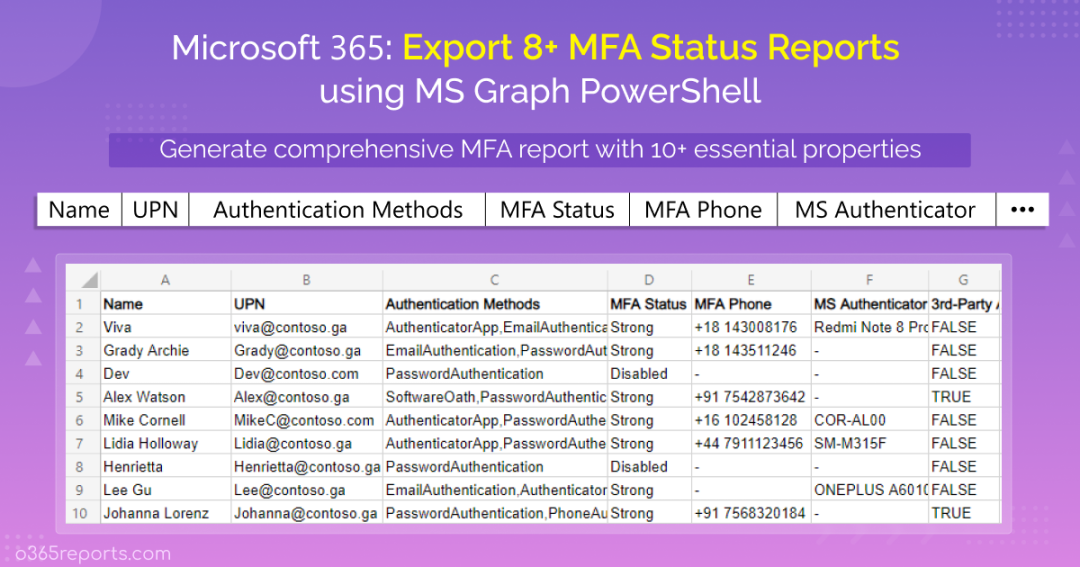
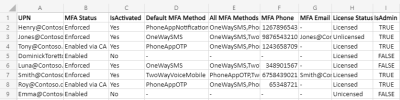
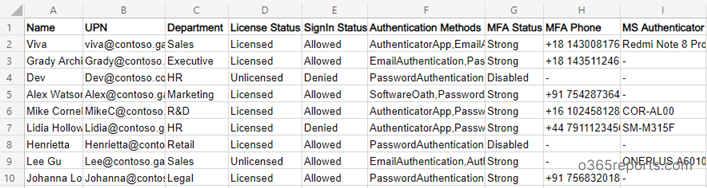
Export Office 365 MFA Status Report – Sample Output:
The exported MFA report contains the following attributes:
- User Name,
- UPN,
- Department,
- License Status,
- Sign-in Status,
- Authentication Methods,
- MFA Status,
- MFA Phone,
- Microsoft Authenticator Configured Device,
- 3rd Party Authenticator Info,
- Additional MFA Details.
How to Execute ‘MFA Status Report’ PowerShell Script?
Method 1: The script will get MFA status for all Azure AD users by default. You can use the format below to run the script.
|
1 |
.\GetMFAStatusReport.ps1 |
The output file will be stored in the current working directory.
Method 2: You can execute this script using certificate-based authentication, as mentioned below. This method would be useful for scheduling the script and obtaining periodic reports.
|
1 |
.\GetMFAStatusReport.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint  <CertThumbprint> |
If you prefer not to invest in CA certificates, you can generate self-signed certificates for internal and testing purposes. You can refer to the connect MS Graph with certificates blog in order to register and obtain certificates for an Azure app.
Method 3:
If you want to generate MFA report for multiple tenants, you need to disconnect existing MS Graph session and enter credential of another tenant. To close existing session, run the script with -CreateSession parameter.
|
1 |
.\GetMFAStatusReport.ps1 -CreateSession |
How To Get More Granular MFA Registration Status Report?
This All-in-One PowerShell script allows you to generate 5+ Microsoft 365 MFA status reports. I have listed the most required use cases below.
- Get MFA status for all users
- Get MFA enabled users report
- List Azure AD users without MFA
- Identify MFA Status for licensed users
- Export MFA report for sign-in enabled users (Excludes disabled user accounts)
- Find licensed users without MFA
- Identify sign-in enabled users without MFA protection
- View users registered by authentication methods
Get MFA Status for All Office 365 Users:
Since ‘Password authentication’ is a primary authentication, it isn’t considered a multi-factor authentication method. To check the MFA registration status of all users, you can run the script as follows.
|
1 |
.\GetMFAStatusReport.ps1 |
By referring to the ‘Authentication Methods’ and ‘MFA Status’ attributes, you can identify the users’ MFA registration status.
Note: MS Online module cannot list new methods like FIDO2 and Windows Hello authentication. In contrast, Microsoft Graph enables you to manage all authentication methods of a user, from FIDO2 to passwordless authentication.
Get MFA Enabled Users Report:
To check if MFA is enabled in Office 365, you can generate MFA enabled users report. You can use the –MFAEnabled switch parameter to get a list of users with MFA.
|
1 |
.\GetMFAStatusReport.ps1 -MFAEnabled |
It will show both ‘Strong’ and ‘Weak’ MFA. If you want to know how MFA status is calculated, you can refer to our documentation at the bottom.
Get MFA Disabled Users Report:
If the Azure AD accounts use only password authentication, it is highly prone to attacks. To identify users without MFA, run the script with –MFADisabled parameter.
|
1 |
.\GetMFAStatusReport.ps1 -MFADisabled |
The report will show users without MFA authentication methods like Phone authentication, FIDO2, Windows Hello for Business, and Microsoft Authenticator app.
Identify MFA Status for Licensed Users:
Instead of generating an MFA report for all users, you can export the MFA registration status for licensed users alone. It will be helpful to filter shared mailboxes and former employees’ accounts.
|
1 |
.\GetMFAStatusReport.ps1 -LicensedUsersOnly |
The exported report will contain all licensed users and their MFA status.
Export MFA Report for Sign-in Enabled Users:
Most organizations disable the employee’s account when they leave the org. To get MFA status for sign-in allowed users, execute the script using the – SignInAllowedUsersOnly parameter.
|
1 |
.\GetMFAStatusReport.ps1 -SignInAllowedUsersOnly |
Find Licensed Users without MFA:
You can combine one or more parameters to generate a more granular MFA Status report. To view MFA disabled licensed users, you can run the script as follows.
|
1 |
.\GetMFAStatusReport.ps1 -MFADisabled -LicensedUsersOnly |
Get Sign-in Enabled Users without MFA:
Signing in without multi-factor authentication leads to account compromise. Identifying sign-in enabled users without MFA is one of the easiest ways to secure your business. To get a list of sign-in enabled users without MFA, execute the script using the following format.
|
1 |
.\GetMFAStatusReport.ps1 -MFADisabled -SignInAllowedUsersOnly |
Get Users Registered by Authentication Method:
To know how many users are registered for each authentication method, open the report with Excel and filter the desired authentication method from the ‘Authentication Methods’ column. In this way, you can get a list of users with FIDO2 authentication, users registered for passwordless authentication, etc.
List of Authentication Methods Supported by Microsoft Graph
You can refer to the table below to know more about each authentication method.
- PasswordAuthenticationMethod – It is primary default authentication method.
- PhoneAuthenticationMethod – A user can register phone (SMS or Voice call) for authentication.
- FIDO2AuthenticationMethod – User can use FIDO2 security key to sign-in to Microsoft 365.
- MicrosoftAuthenticatorAuthenticationMethod – With the Microsoft Authenticator app, users can authenticate through Android and iOS.
- PasswordlessMicrosoftAuthenticatorAuthenticationMethod (deprecated)– Users can authenticate in a password less way through Microsoft Authenticator app.
- EmailAuthenticationMethod – Email authentication can be used in Self-Service Password Reset (SSPR).
- WindowsHelloForBusinessAuthenticationMethod – Windows uses Windows Hello to authenticate users. It is one of the passwordless authentication methods.
- TemporaryAccessPassAuthenticationMethod – Temporary access pass is a time-limited passcode that is used for authentication.
- SoftwareOathAuthenticationMethod – When a user uses a 3rd party authenticator app or application that supports OATH specification for MFA.
How MFA Status is Calculated?
Based on the security considerations for the available authentication methods, MFA status is categorized into three classifications – Strong, Weak, and Disabled.
- Windows Hello for Business, Microsoft Authenticator app, FIDO2 security key, and Phone authentication – Strong authentication methods.
- Since OATH software tokens use 3rd party authenticator application, it is considered weak.
- Email Authentication is only used for SSPR. So, it is considered disabled.
- Password authentication is a primary authentication. So, users with only Password authentication are considered MFA disabled.
Note: When a user uses a specific authentication method for the first time, it will be added to the list of authentication methods used by the account.
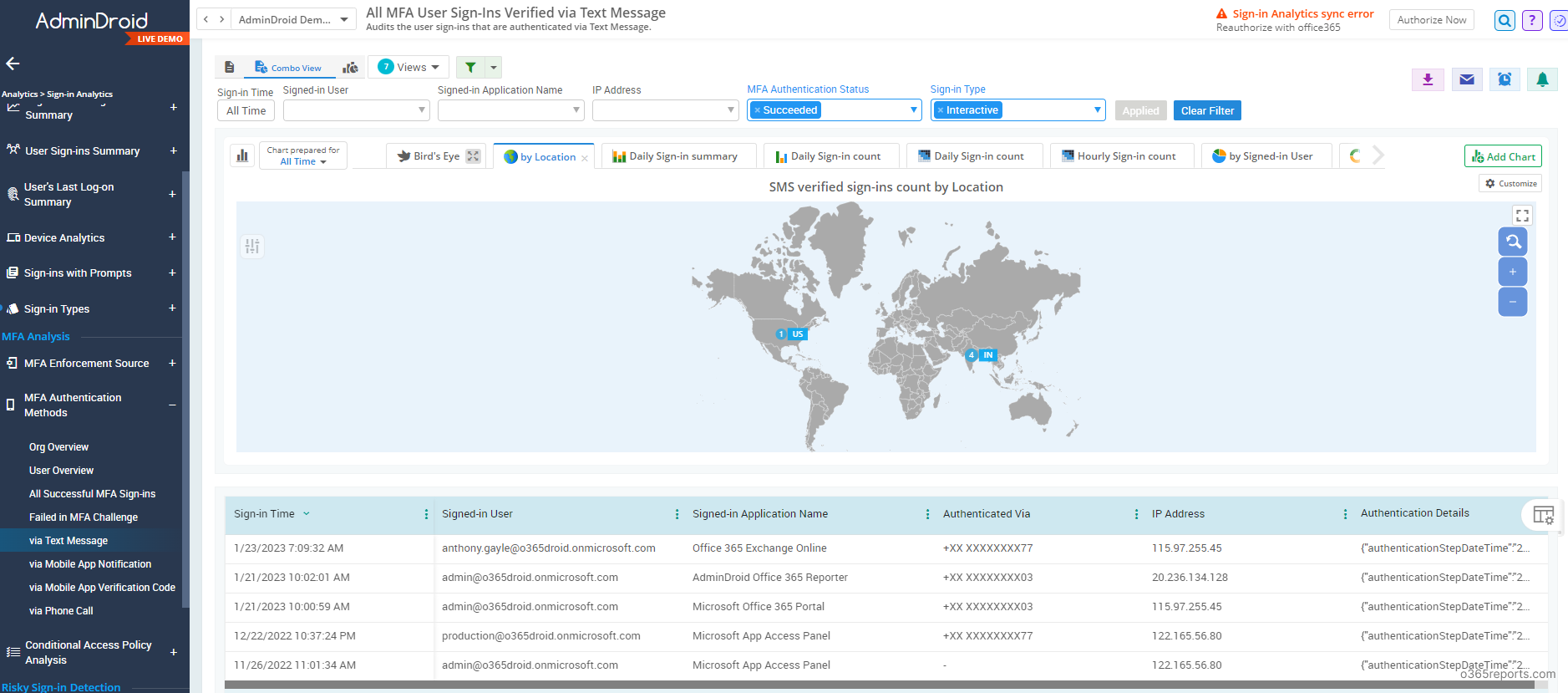
Detect Security Threats with MFA Auditing in Office 365:
Monitoring MFA logins can provide insights into user behavior and help identify any trends or patterns that may indicate security risks. For example, a sudden spike in MFA login failures may indicate a phishing attack or a vulnerability in your authentication process. By monitoring MFA logins, you can detect and respond to potential security threats, such as unauthorized access attempts or fraud. But Microsoft doesn’t provide built-in reports to identify MFA login failures in a user-friendly manner.
If you need such reports, you can try AdminDroid Microsoft 365 reporting tool. AdminDroid provides the following MFA reports,
- MFA sign-in based on status
- Logins failed to pass MFA
- All successful MFA sign-ins
- MFA sign-ins based on authentication methods
- MFA logins via text message
- MFA logins via mobile app notification
- MFA logins via phone app notification
- MFA logins via phone call
- Summary report of organization’s sign-ins count based on authentication method
- MFA configuration reports
- MFA configured through Conditional Access
- Users with MFA
- Users without MFA
- MFA enabled users
- MFA disabled users
- MFA activated users
- MFA non-activated users
- MFA device details
Additionally, AdminDroid provides 1600+ pre-built reports and 20 smart visually appealing dashboards to know about your Office 365 environment at a glance. This tool provides reports on Office 365 reporting, auditing, analytics, usage statistics, security & compliance, etc.
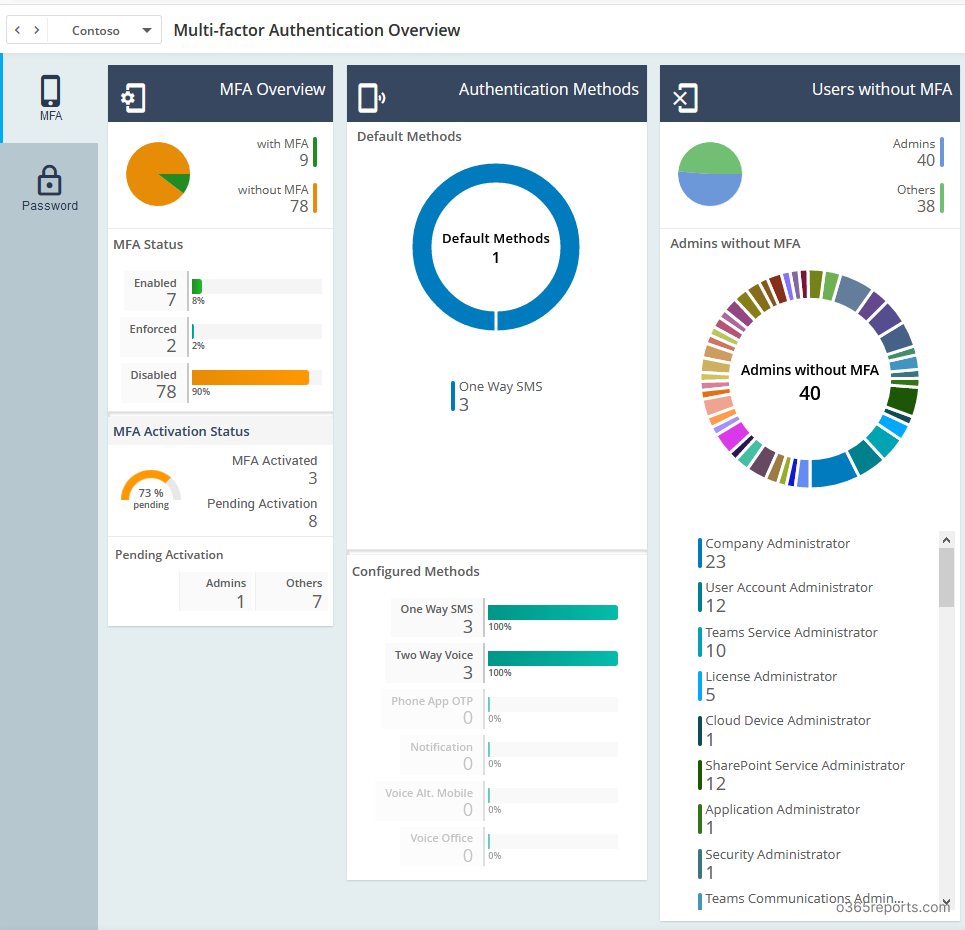
Furthermore, AdminDroid offers more than 100 free reports and several dashboards. These reports cover various aspects such as User information, Licenses, Group details, Group Members, Devices, Login activities, Password changes, License changes, and more. If you are seeking a solution for Azure AD reporting and auditing, you can try the AdminDroid’s Free Office 365 reporting tool to experience its capabilities for yourself.
I hope this blog will help you get MFA status using Microsoft Graph PowerShell and monitor the authentication methods’ usage in an effective way.