External email warning helps to alert users from clicking malicious links, phishing emails sent by external senders. It plays a vital role in protecting against spam and phishing threats. For these years, admins use a transport rule to prepend [External] in the subject line. This approach has few limitations like,
- It takes a lot of space in the subject line, making it hard to preview the subject.
- As the transport rule might not be aware of the end user’s language, it leads to localization issues.
- Multiple external tags: If the external users keep replying to the thread, it will add multiple [External] tags in the subject.
To overcome these limitations, Microsoft introduced native external sender callouts in Outlook.
Native External Sender Identification – External Tag
To provide a native experience to identify external emails, Microsoft introduced a new ‘External’ tag. It shows the External tag on emails from external senders to view and verify the real sender’s email address.
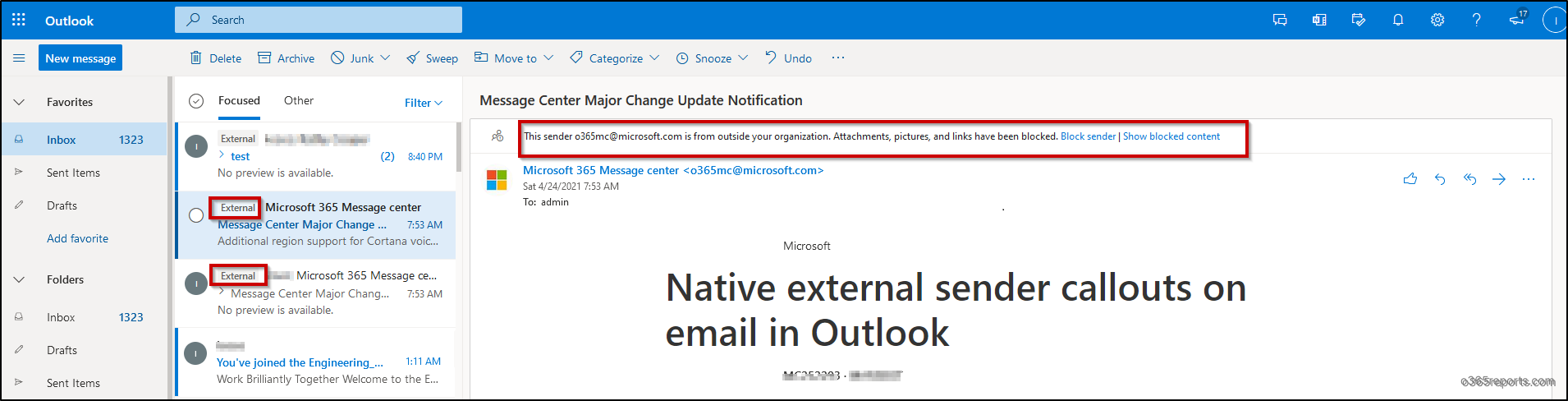
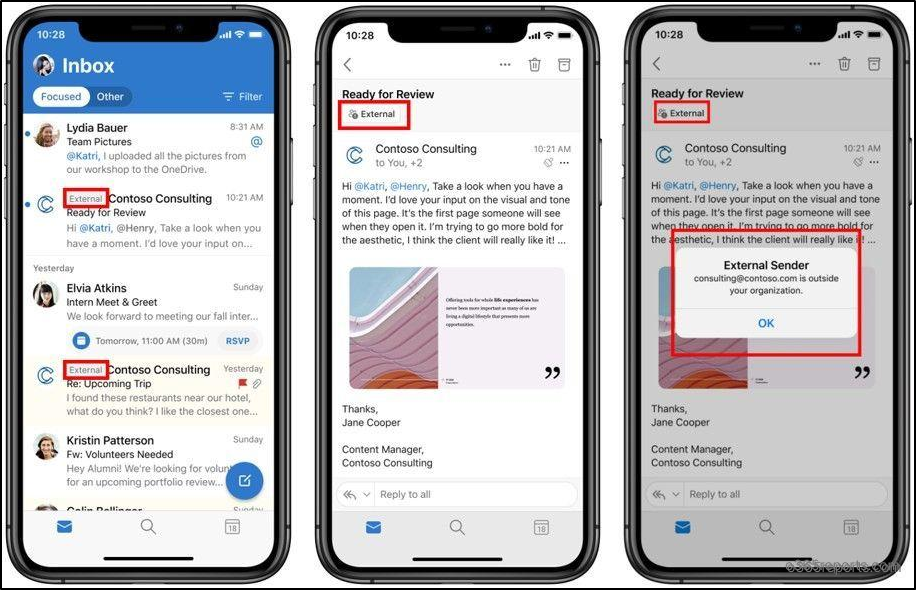
After enabling external tagging, the external email alert looks similar to the below screenshots:
Outlook on the web view of external sender:
Outlook for iOS view of external sender:
Enable External Tagging in Exchange Online
External tagging is disabled by default. You can enable it through Exchange Online PowerShell.
Note: If you are using the transport rule to add a [External] tag in the subject line, we encourage you to disable it before enabling native external tagging to avoid emails being marked ‘External’ twice.
To enable external tag, please follow the steps below:
- To use external tagging cmdlets, you need to connect to Exchange Online PowerShell.
- Run Set-ExternalInOutlook cmdlet as follows to activate external tagging.
|
1 |
Set-ExternalInOutlook –Enabled $true |
To view external tagging settings, you can use the Get-ExternalInOutlook cmdlet.
After enabling this feature, new external emails that arrive are automatically tagged with ‘External’. It won’t impact existing emails.
💡Tip: As an admin, you can use PowerShell to track all emails received from external domains by users in your organization.
How to Exclude Certain Email Address or Domain from External Tagging
In some situations, you don’t want to add the ‘External’ tag for some external senders or external domains. In that case, you can exclude them by adding in the ‘AllowList’ parameter.
Method 1: To enter multiple entries and overwrite any existing entries,
|
1 |
Set-ExternalInOutlook –AllowList "John@microsoft.com","fabrikam.com" |
The above cmdlet excludes external tag, if the sender is John@microsoft.com or from fabrikam.com domain.
The maximum number of entries is 30, and the total size of all entries can’t exceed one kilobyte. Else, you will end up with following errors.
- Maximum AllowsList count exceeded.
Maximum AllowList count exceeded. Max 30, Current: 31.
+ CategoryInfo : WriteError: (SetExternalInOutlook:String) [Set-ExternalInOutlook], Exception
- Maximum AllowList length exceeded.
Maximum AllowList length exceeded. Max 1024, Current: 1129.
+ CategoryInfo : WriteError: (SetExternalInOutlook:String) [Set-ExternalInOutlook], Exception
Method 2: To add new values without affecting existing values,
|
1 |
Set-ExternalInOutlook –AllowList @{Add="contoso.com","Emma@fourthcoffee.com"} |
The above command excludes external tagging for contoso.com and Emma@fourthcoffee.com along with the previously mentioned domains.
To remove the domain or external user from the AllowList, you can use the below cmdlet.
|
1 |
Set-ExternalInOutlook –AllowList @{Remove="contoso.com","Anne@Fabrikam.com"} |
Exchange Online External Tag Not Working
After enabling external tagging, if you can’t see the external tag for the external emails then, you might fall under any one of the below cases.
- Since External tagging is an org-wide setting, it will take some time for Exchange Online to enable tagging. Microsoft says that after enabling external tagging, it can take 24-48 hours. So, users should wait to see the external tag in emails from external senders in supported versions of outlook.
- External email tagging is supported in the following versions of Outlook. If you are using an older version, you need to upgrade to the latest version.
- Outlook on the web
- Outlook mobile (IOS & Android)- version 4.2111.0 and higher
- Outlook for Mac – version 16.47 and higher
- Outlook for Windows
- As external tagging is a new feature, make sure that your account is enabled in Microsoft 365 admin center for targeted release. Users on targeted release can see new updates early than other users.
When to Choose Transport Rule Over Native External Tag
Native external tagging is a global setting and it has limited customization when compared to the transport rule. If the organization needs more granular requirements to add/exclude external tagging, then you should go for the transport rule.
For example,
- If the org is a consultancy, mostly they receive emails from external users. So, it is essential to exclude external tag for external facing mailboxes like support or sales mailbox to avoid all mails tagging as External.
- If you want to add sender-based warning – one for common domains such as gmail, outlook, yahoo, etc. Other for the rest of business emails.
- Customization – if you want to customize the look and feel of the external warning message, then the native cmdlet is not suitable for you.
In that case, you can configure an external email warning through transport rule.
Conclusion:
Native external tagging cmdlet is one of the most awaited features and there is no doubt it adds additional security to email. As an admin, would you like to stay in the transport rule or switch to native PowerShell cmdlet? You can share your thoughts through the comment section.