Recently, Microsoft announced a significant update: “Basic Authentication retirement for legacy protocols in Exchange Online.”
Sept 2021 Update: Microsoft has resumed the basic authentication retirement program
Today, Microsoft announced that they are restarting the program to end the use of Basic Auth in Exchange Online. Beginning October 1, 2022, Microsoft will begin to disable Basic Auth in all tenants, regardless of usage.
In short, no more Basic Authentication for following protocols to access Exchange Online.
- EWS (Exchange Web Services)
- EAS (Exchange ActiveSync)
- IMAP4
- POP3
- RPS (Remote PowerShell)
This blog will help you to understand what is Basic Authentication, Basic Authentication vs Modern Authentication, how the Basic Auth deprecation will affect the organization, etc. Mainly, it focuses on the following things.
- Basic Auth deprecation – How to prepare for this change
- Download Office 365 Basic Authentication report
Basic Authentication in Exchange Online:
Microsoft has planned to end Basic Authentication in Exchange Online from Oct 01, 2022.
Most client apps use Basic Authentication to connect to servers, services, and endpoints as it is simple to set up. Basic Authentication in Exchange Online sends username and password with every client access request.
The trouble with Basic Authentication is that it easily compromise through brute force or password spray attacks. To protect our environment from a security threat, we need to move to better a option.
No more Basic Authentication in Exchange Online – How does this affect me?
From Oct. 01, 2022, client apps that use any of the above mentioned legacy protocols won’t be able to connect to Exchange Online using Basic Authentication.
Beginning in early 2022, Microsoft will roll out the changes to support basic authentication deprecation. As an effect, Microsoft will select tenants and disable basic auth for all affected protocols except SMTP AUTH for 12-48 hours. During this time, all clients and apps that use basic auth in that tenant will be affected, and they will be unable to connect. Tenant admins can manually re-enable basic auth using the self-service tool. If not, those protocols will be re-enabled automatically after the specific period.
Stay informed with Upcoming Microsoft 365 changes and end-of-support milestones.
Alternative to Basic Authentication – Switch to Modern Authentication:
The best solution is moving to Modern Authentication approach. Modern Authentication is based on the Active Directory Authentication Library (ADAL) and OAuth 2.0 tokens.
Modern Authentication (which is OAuth 2.0 token-based auth) has many benefits that help to overcome the issues present in Basic Auth. OAuth tokens have limited usable lifetime and are specific to the applications they are issued for. So, they can’t be reused. Exchange Online Modern Authentication ensures a more secure and reliable way than Basic Auth.
What do I need to do to Prepare for this Change?
There are several actions that you and your users can take to avoid service disruptions on client applications, and we describe them below.
- You can start updating the client applications your users are using to versions that support OAuth 2.0.
- If you have written your own code using protocols with Basic Authentication, you will need to update your code to use OAuth 2.0.
- If you are using 3rd party application, either you need to reach out 3rd party app developer to update the application to support OAuth 2.0 or switch to an application that supports Oauth2.0.
- RPS: Connect to Exchange Online PowerShell without Basic Authentication – Are you a tenant administrator who spend more time on Remote PowerShell to access Exchange Online? You can use Exchange Online PowerShell V2 Module which supports modern auth.
- Unattended script: To connect Exchange Online with unattended authentication, you can use EXO V2 module (2.0.3 preview or later).
- Exchange ActiveSync: If your organization still using Exchange ActiveSync, you can use Outlook Mobile clients to connect with Exchange Online.
- IMAP/POP: Microsoft Planning to add OAuth support to both IMAP and POP in a few months. If you want to keep using these protocols, you will need to update the app to one that supports Modern Auth.
Note:
- This change does not impact SMTP AUTH – Microsoft continues supporting Basic Auth for the time being. April 2024 Update: The exception is no more! Recognizing the critical importance of strengthening security measures, Microsoft announced the deprecation of SMTP auth by September 2025.
- This change doesn’t affect Exchange Server on-premises products.
How to Discover Basic Auth Connections – Office 365 Basic Authentication Report
As a tenant admin, you probably have the question – How do I know who are using Basic Authentication in my tenant? Microsoft has answered your question. Yes, Microsoft has updated Azure AD sign-in report to include lists users and client applications that use basic authentication to connect Exchange Online.
Export Office 365 Basic Authentication Report:
The improved Azure sign-in report helps you to get a list of users who uses legacy authentication to connect Exchange Online. Follow the below steps to generate Office 365 legacy authentication report.
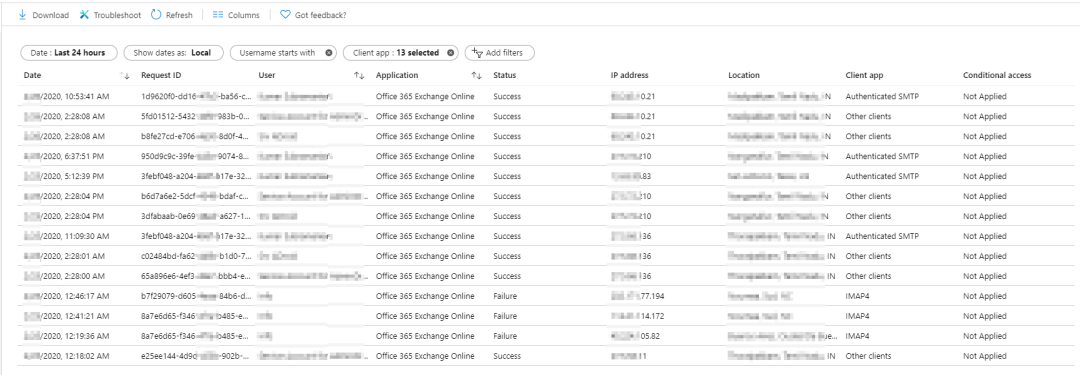
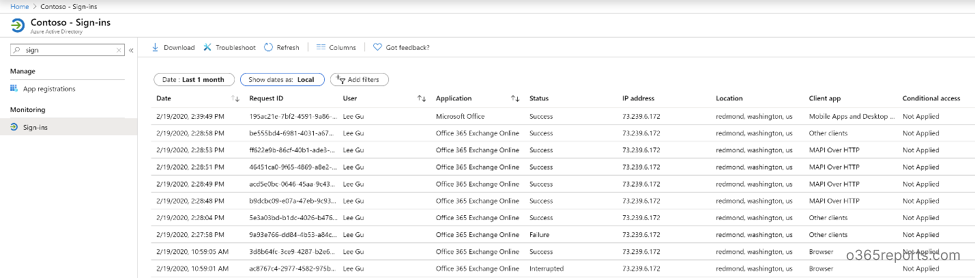
Step1: Go to Azure Sign-in report in the Microsoft Azure portal. The sign-in report shows sign-in activity in the tenant, date, time, user IP address, login location.
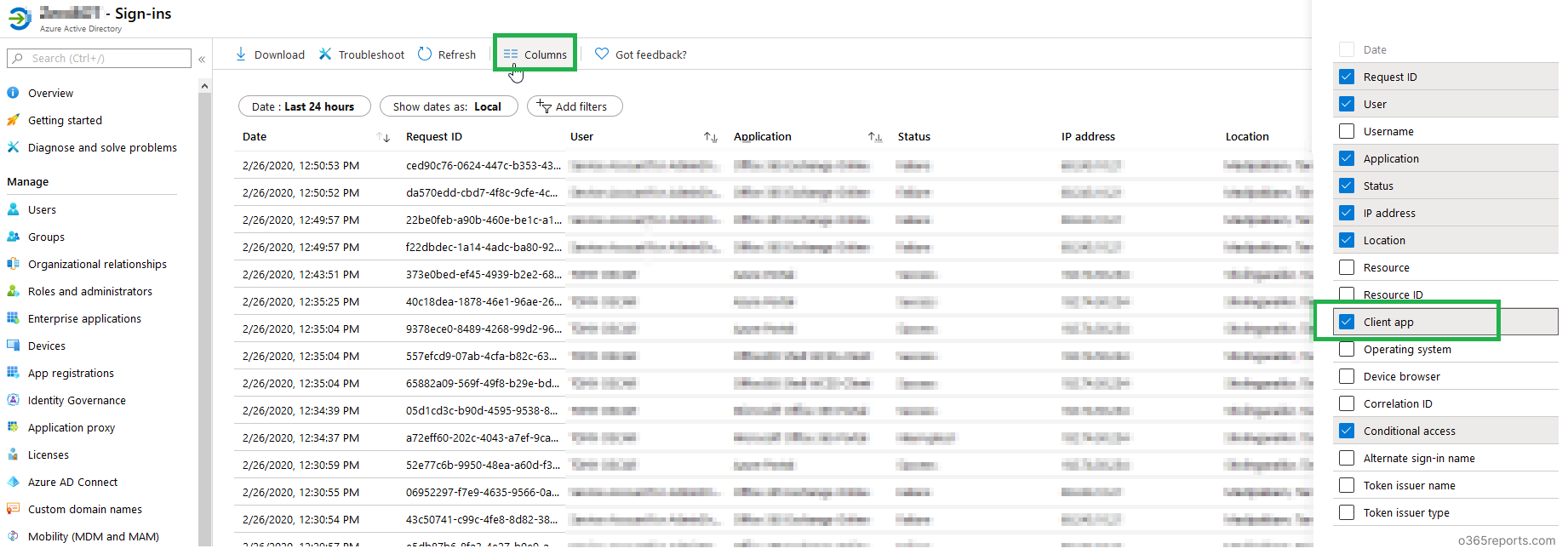
Step2: Add the ‘Client app’ column to the report (Client app is not displayed by default). The ‘Client app’ column will show you the protocols used by the user to connect Office 365.
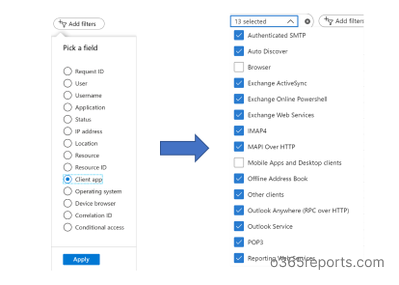
Step3: To view O365 basic authentication report, click ‘Add filters’ and then select ‘Client app’. Apply the changes. Now select the ‘Client app’ filter to choose legacy authentications like Exchange Active sync, Exchange Online PowerShell, IMAP4, POP3, etc.
After applying a filter, you can view connections/sign-ins that meet your criteria – I.e., Users who use basic authentication connection.
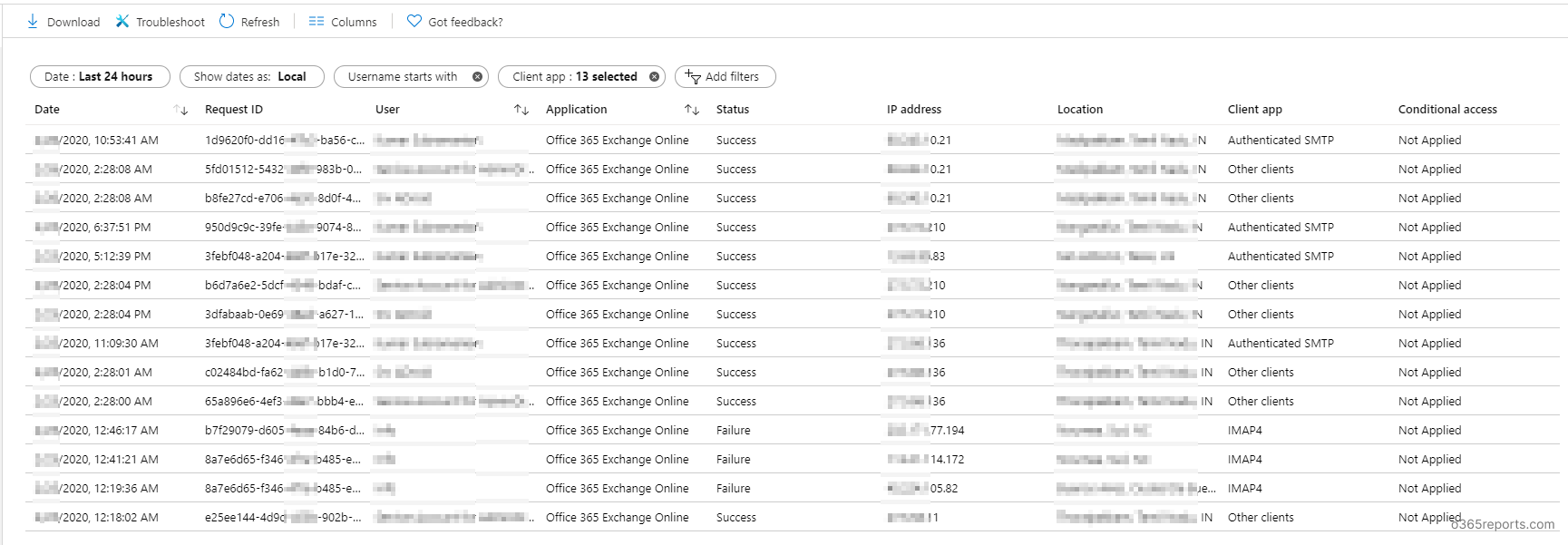
Note: To generate all basic authentication connections, select everything in the ‘Client app’ except Browser and Mobile Apps & Desktop Clients.
To get details pane, you can click any of the line. The details pane has contains basic info, location, device info, authentication details, conditional access, etc.
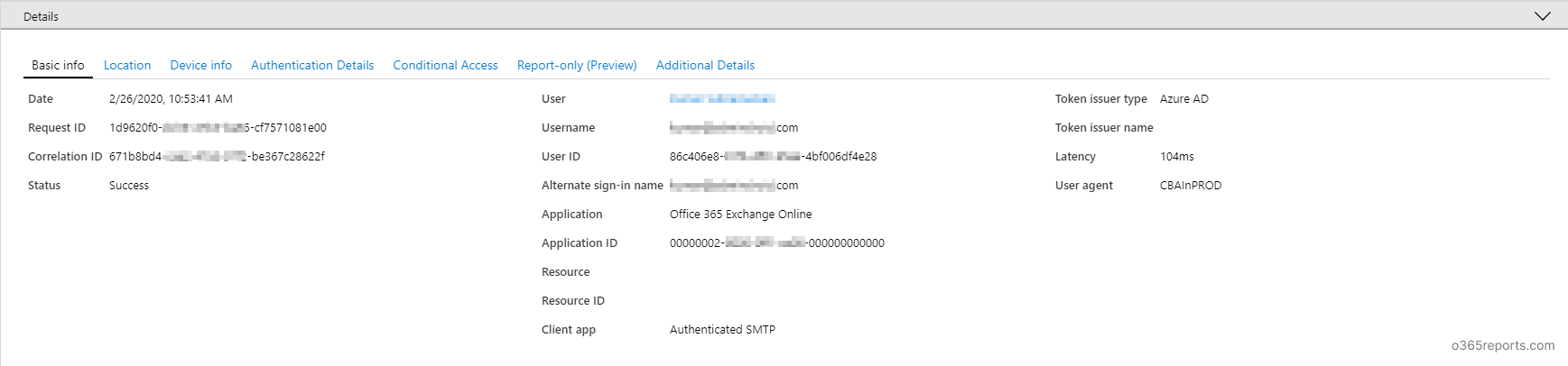
The basic authentication report can be downloaded as a CSV or JSON file. You can use this Exchange Online basic authentication report to find users who use basic authentication to connect Exchange Online and take the necessary steps to adopt modern authentication.
Basic Auth Deprecation – Update History:
- Feb – 2020 update: Microsoft has updated Azure AD sign-in report to include lists users and client applications that use basic authentication to connect Exchange Online.
Note: To access the Azure sign-in report, you need to have an Azure AD Premium license. I can hear you scream! Don’t worry. Microsoft is planning to make this report available for all. We can expect the update soon.
- Mar 12 -2020 Update: Azure sign-in report now available to all.
- April 2020 Update: Microsoft postponed disabling basic authentication in Exchange Online to 2021
Due to the COVID-19 crisis, Microsoft postponed disabling basic authentication in Exchange Online to the second half of 2021 for tenants that use basic authentication.
For newly created tenants, basic authentication disabled by default and basic authentication will be disabled if the tenant has no recorded usage from Oct 2020. Since Microsoft wants to improve the security, it will continue to roll-out OAuth support for POP, IMAP, SMTP Auth, and Remote PowerShell.
- Sept 2021: Microsoft retires basic auth in Exchange Online from Oct 2022.
Conclusion
:
Changing from Basic Authentication to Modern Authentication will cause some disruption and is more challenging. But together, we need to plan for this change to protect our data.
Are you ready for the change? Which method are you going to implement in your organization? Please share your experience/difficulties during Modern Authentication adoption in the comment section to assist other admins.