Have you ever felt like managing multi-factor authentication (MFA) is more of a hurdle than a security measure? 😕 Constant MFA issues can be frustrating! Here are some common MFA issues; as you read, consider how you might address these challenges.
- Users face frequent prompts even with low-risk apps, causing MFA fatigue. What’s your first step?
- Many users can’t access Microsoft 365 accounts due to MFA failures. What’s your initial step?
- Users can’t access specific Microsoft 365 services despite MFA enrollment. Where do you start?
- What’s your priority assessment before integrating a third-party MFA with Microsoft 365?
- How do you begin investigating phishing alerts that bypass MFA?
For all these MFA issues, admins should first identify the source of MFA deployment to troubleshoot conflicts and configuration issues effectively.
So, this blog provides a PowerShell script to generate an ‘MFA deployment source report for Microsoft 365 users’, which helps you pinpoint the root cause of problems.
Different Sources to Set up Multi-Factor Authentication for Microsoft 365 Users:
Before analyzing MFA deployment sources, it’s essential to know how to enable MFA in Microsoft 365. Currently, admins have three main options:
Enforce Per-user MFA in Entra ID (Free & not recommended): Per-user MFA lets you choose specific users for MFA, but it is outdated and less flexible. Microsoft recommends to move from per-user MFA to Conditional Access MFA.
Security Defaults in Microsoft Entra (Free): This is enabled by default and requires MFA for all users. It’s a good option for basic security in Entra ID tiers but lacks flexibility.
Require MFA with Conditional Access (Recommended): This flexible option allows you to configure MFA based on conditions like user location or device. Recommended for organizations with Entra ID plans (P1 and P2) for a more customized MFA approach.
How to Find How MFA is Enforced in Microsoft 365?
Microsoft 365 admins have several native reports and PowerShell scripts to
- Find Azure MFA registration details of users
- Identify all registered authentication methods by users
- Check if MFA is enabled for Microsoft 365 users
- Identify system-preferred authentication method for each user
However, practically speaking, there is no direct way to find the exact source of MFA deployment for your users! 💯The only way to troubleshoot MFA issues is to manually check every possible source, which is pretty tedious.
What makes it even trickier is both per-user MFA and Conditional Access MFA can’t be used simultaneously. This can make the migration process hard, leaving you unsure who’s enabled for per-user MFA.
Fortunately, we have a great solution for you in this case as well! Our PowerShell script enables you to quickly identify the source of MFA deployment.
- You can use this script to track MFA deployment sources, disable per-user MFA that has been enforced, and troubleshoot MFA issues!
Download Script: IdentifyMFADeploymentSources.ps1
Script Highlights:
- The script identifies and exports MFA enforcement sources for all users.
- Helps you understand user MFA registration status (registered or not) to plan your MFA rollout campaigns efficiently.
- It specifically identifies MFA sources for external users as well.
- The script checks which Conditional Access policies demand MFA and tells you if users have registered for that MFA method as required by those policies.
- Automatically install the missing required modules (Microsoft Graph Beta, MSOnline) with your confirmation.
- The script can be executed with an MFA-enabled account too.
- Exports report results as a CSV file.
- The script is scheduler-friendly, making it easy to automate.
- It supports certificate-based authentication (CBA) too.
Export MFA Deployment Source Report – Sample Output:
Forget about switching multiple tabs in Entra ID! 😌This script simplifies everything with a clear overview of your users’ MFA deployment sources and other essential info.
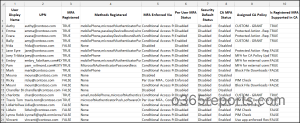
Here is what you will find in the report:
| S.no | Attributes | What does it mean? |
| 1. | User Display Name | Displays the user’s display name. |
| 2. | User Principal Name | Shows the User Principal Name for the user. |
| 3. | MFA Registered | Indicates whether the user has registered for MFA. The possible values are TRUE or FALSE. |
| 4. | Methods Registered | Lists all the multi-factor authentication methods registered by the user. |
| 5. | MFA Enforced Via | This column is the main focus of the script. It shows how MFA is being enforced for the user. The possible sources are Conditional Access policy, per-user MFA, and security defaults. |
| 6. | Per-user MFA Status | Shows if per-user MFA is disabled, enforced, or enabled. |
| 7. | Security Default Status | Indicates whether Security Defaults are turned on or off for your organization. |
| 8. | Conditional Access MFA Status | Shows if the Conditional Access policy requiring MFA is configured for the user. |
| 9. | Assigned CA Policy | Lists Conditional Access policies requiring MFA assigned to the user. |
| 10. | Is Registered MFA Supported in CA | Indicates whether the user has registered the specific MFA method required by their Conditional Access policy.
|
How to Run ‘MFA Deployment Source” PowerShell Script?
Script downloaded? Awesome! Here’s how to run the script in Windows PowerShell. Choose any of the methods below to get started.
Method 1: Run the script with MFA-enabled and non-MFA accounts.
|
1 |
.\IdentifyMFADeploymentSources.ps1 |
The script will prompt you to enter credentials twice to connect MS Graph and MS Online PowerShell modules. Once the execution is complete, the script will export the MFA enforcement source report for all Microsoft 365 users.
| Heads up: This script requires the MSOnline PowerShell module version 1.1.166.0 or higher to retrieve per-user MFA status. Ensure your MSOnline module is updated to at least version 1.1.166.0. |
Different Ways to Use ‘MFA Deployment Source‘ Report!
So, you’ve run the script and found how your users are prompted to register for MFA. But it does not stop there. 😜
The script goes beyond just showing you the source of MFA deployment! There are different ways this script can be useful. So, here are some practical scenarios where you can effectively apply and adapt this script:
- Retrieve a list of authentication methods registered by users.
- Find MFA status for external users.
- Switch from per-user MFA to Conditional Access MFA.
- Check if security defaults are enabled or disabled.
- Export Conditional Access Policies Assigned to Microsoft 365 Users.
- Verify if a user is registered for Conditional Access MFA.
This script isn’t just for one-time use—it’s a versatile one that helps you manage and troubleshoot MFA issues effectively.
1. List Authentication Methods Registered by Users
Many users still use less secure methods like SMS or voice calls for MFA.
- With this report, admins can easily spot those users and run a registration campaign in Entra ID to register for Microsoft Authenticator.
- Plus, you can use this report to get all authentication methods registered by users in a jiffy!
Why push for Microsoft Authenticator? Well, Microsoft recommends Microsoft Authenticator for the utmost security. It uses MFA number matching as the default method, which means you’ll know exactly where the request is coming from, and which app triggered it.
2. Enforce MFA for External Users
It’s not just your internal users you need to worry about!
- This script helps you check how MFA is deployed for external users as well. It works for various external user types in Azure AD: B2B collaboration users (guests & members), B2B direct connect users, and even local guest users, all through Conditional Access policies.
For guests who do not have MFA enabled, it is suggested to enable MFA for all external users to prevent unauthorized access. If you enforce MFA on guests, they’ll need to register MFA in your tenant unless you set up cross-tenant access settings & trust their home tenant’s MFA.
3. Switch From Per-user MFA to Conditional Access MFA
Users stuck with per-user MFA often face two extremes: constant MFA prompts or no prompts at all, leaving them vulnerable to attackers! 🚨
- To fix this, this script helps you identify these problematic situations. See who has per-user MFA enabled, enforced, or disabled, and then move them to Conditional Access policies for a smoother, more secure experience.
4. Check If Security Defaults are Enabled or Disabled
Organizations with Entra ID (Azure AD) premium licenses should manage MFA with Conditional Access policies. However, the security defaults must be disabled in your Microsoft 365 organization before setting up CA policies.
- Use this script to check if your security default setting is disabled. If it shows as Enabled, disable it and then create Conditional Access policies to enforce MFA.
5. Export Conditional Access Policies Assigned to Microsoft 365 Users
Most MFA lockouts are often caused by Conditional Access policies. Yet, pinpointing the specific policy among many can be daunting for admins, right? 😖
- With this script, identifying the culprit policy becomes effortless! It exports Conditional Access policy names that require MFA for users by analyzing conditions like included & excluded users & other policy specifics.
Now, admins can quickly spot and troubleshoot issues without navigating into numerous policies!
6. Verify If User is Registered for Conditional Access MFA
Still with me? Let’s dive deeper! Imagine this scenario: You set up a Conditional Access policy requiring ‘Passwordless MFA – authentication strength‘ for logins outside the office. If they use SMS or voice call MFA, sign-in fails.
- But how do you know if users have registered for these methods? Manually checking through Entra ID? Too much hassle! Instead, run this script and check the ‘IsRegistered MFA Supported in CA’ column.
If it says ‘FALSE’ – the user hasn’t registered the required method mentioned in the CA policy, and their authentication may fail. Time for a gentle nudge!
If it says ‘TRUE’ – perfect! The MFA method in your CA policy is registered and ready to go.

That made a lot of your work so easy, right? 😌Additionally, just as you prioritize discovering MFA deployment sources of users, it’s equally crucial to track the frequency of MFA prompts.
How to Schedule the Script in Task Scheduler?
Want to automate the MFA deployment report? Just schedule the PowerShell script in the Task Scheduler or Azure Automation to get the report periodically.
|
1 |
.\IdentifyMFADeploymentSources.ps1 -UserName <UPN> -Password <Password> -TenantId <TenantId> -AppId <AppId> -CertificateThumbprint <CertThumbprint> |
Note: This method only works for non-MFA accounts. You can disable MFA for a specific account using a Conditional Access policy. By setting this up, you’ll always have up-to-date MFA status reports without lifting a finger. Happy scheduling!
Decode MFA Complexities with AdminDroid’s Detailed MFA Reports
Tired of constantly switching tabs in Entra ID and manually running PowerShell scripts every time, you need a report? 🤔If you’re spending most of your time on that, how will you manage your other major Microsoft 365 tasks?!
| Heads up: Let me introduce you to the AdminDroid Microsoft 365 reporting tool that takes the hassle out of your day-to-day operations! 🚀 |
AdminDroid features a dedicated MFA dashboard that displays essential details like an overview of MFA, authentication methods registered by users with their percentages, admins without MFA, and more in one place.
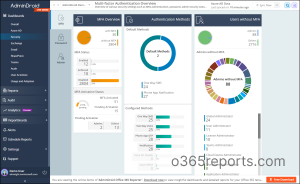
Get Detailed MFA Reports📊
AdminDroid doesn’t stop at dashboards! It offers a suite of detailed MFA reports that make managing multi-factor authentication straightforward and efficient:
- MFA Sign-Ins by authentication method
- Monitor MFA sign-ins based on MFA enforcement Sources
- User MFA status
- MFA device details
- Users with and without MFA
- MFA-enabled/enforced/non-activated users
- Policies with MFA
- Sign-ins failed to pass the MFA challenge
- Sign-ins via CA policies
- Sign-ins blocked by CA policies and more
Beyond MFA: Comprehensive Microsoft 365 Reports
And the best part? AdminDroid doesn’t stop at MFA and Conditional Access! 😌AdminDroid offers 1900+ pre-built reports and 20+ visually stunning dashboards covering every Microsoft 365 service.
AdminDroid provides everything you need: Microsoft 365 usage statistics, security insights, Microsoft 365 audit details, and more.
Also, AdminDroid offers a free Azure AD reporting tool covering users, licenses, groups, logins, passwords & license changes, and more. Test-drive its capabilities with over 100 free reports & dashboards, all at no cost.
Download AdminDroid now and see how it can simplify your Microsoft 365 administration and free you to focus on what matters most!
I hope this blog gives you the answer you expected! 🙂 Feel free to reach out with any questions or concerns about the blog in the comments—glad to help you promptly!