Azure AD Conditional Access (CA) policies are the backbone of Microsoft 365 security, shaping how users access resources and protecting sensitive data. While enforcing strong authentication for users, demanding MFA for admin portals, or implementing token protection in Azure AD, admins rely heavily on CA policies. However, even minor changes to CA policies can impact Microsoft 365 security, highlighting the need for continuous monitoring.
Previously, tracking these changes was complex, with audit logs offering limited insights. Now, Microsoft has introduced a new feature to view Conditional Access policy changes (currently in preview). Let’s explore how this preview feature simplifies the process of monitoring Conditional Access policy changes.
Audit Conditional Access Policy Changes
As CA policies are crucial for accessing resources, periodic monitoring is essential. Even a minor misconfiguration can lead to unexpected sign-in failures, affecting the functionality of your Microsoft 365 environment. In such cases admins need to check which CA policy is blocking sign-ins and troubleshoot them.
Microsoft also provides Azure AD audit logs to monitor Conditional Access policy changes, making it easier for everyone to stay on the same page. Now, let’s see how to audit changes to Conditional Access policy with new view feature in Microsoft Entra ID.
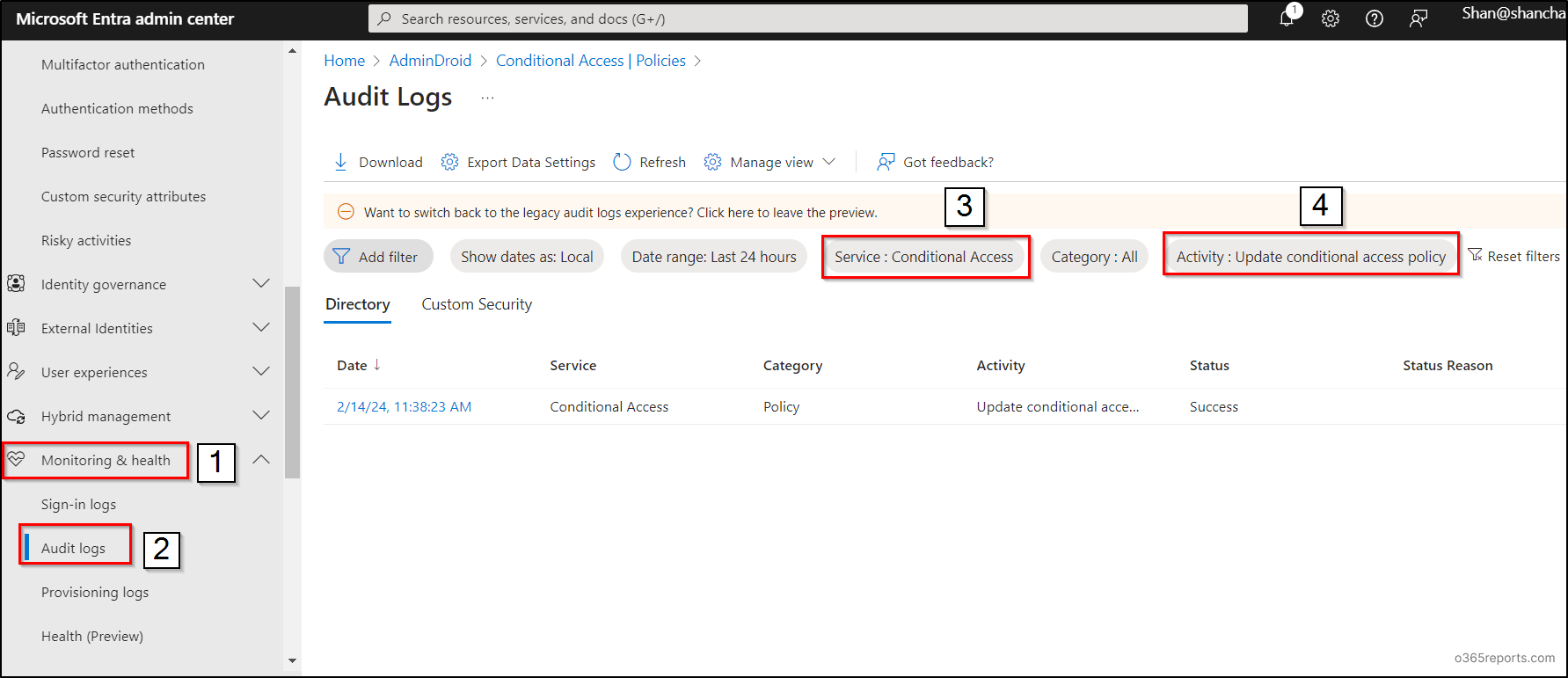
1. Login to the Microsoft Entra admin center with at least Conditional Access administrator privileges.
2. Navigate to the “Identity” section and find “Monitoring & health”.
3. Click on “Audit logs” under “Monitoring & health”.
4. Choose the “Date range” you wish to examine.
5. In the “Service” filter, select “Conditional Access” and click “Apply”.
6. Under the “Activity” category, search for and select “Update conditional access policy”.
7. Choose a Conditional Access policy from the list.
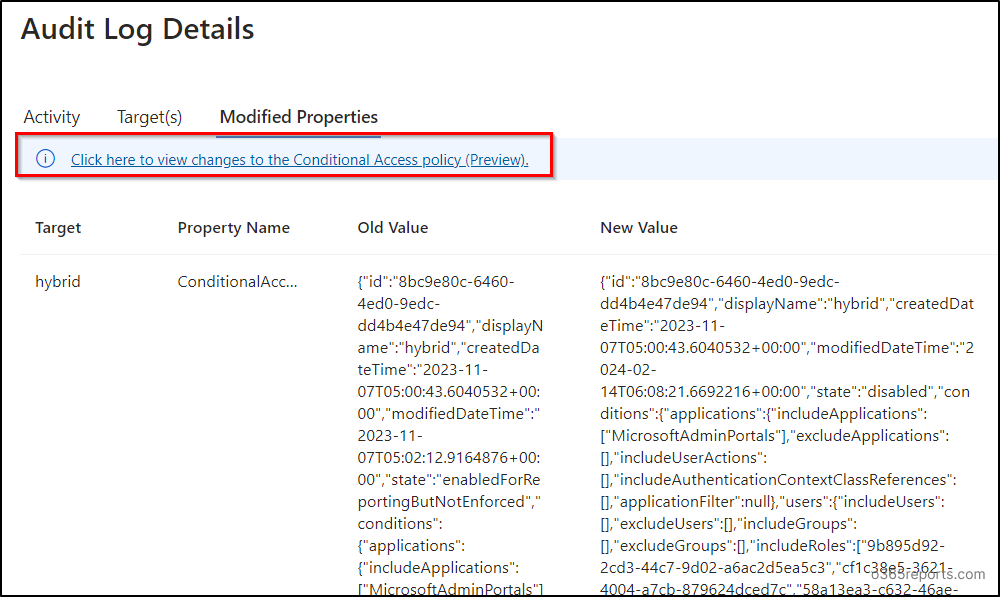
8. Then, navigate to the “Modified Properties” tab to see the modified properties in Conditional Access policy.
9. Then, select the “Click here to view changes to the Conditional Access policy (Preview)” link.
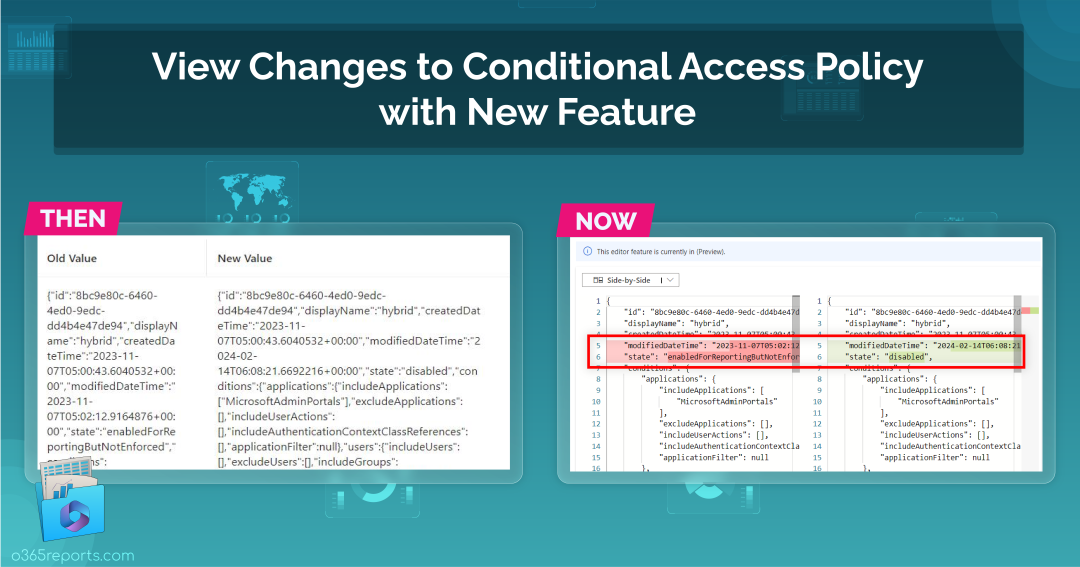
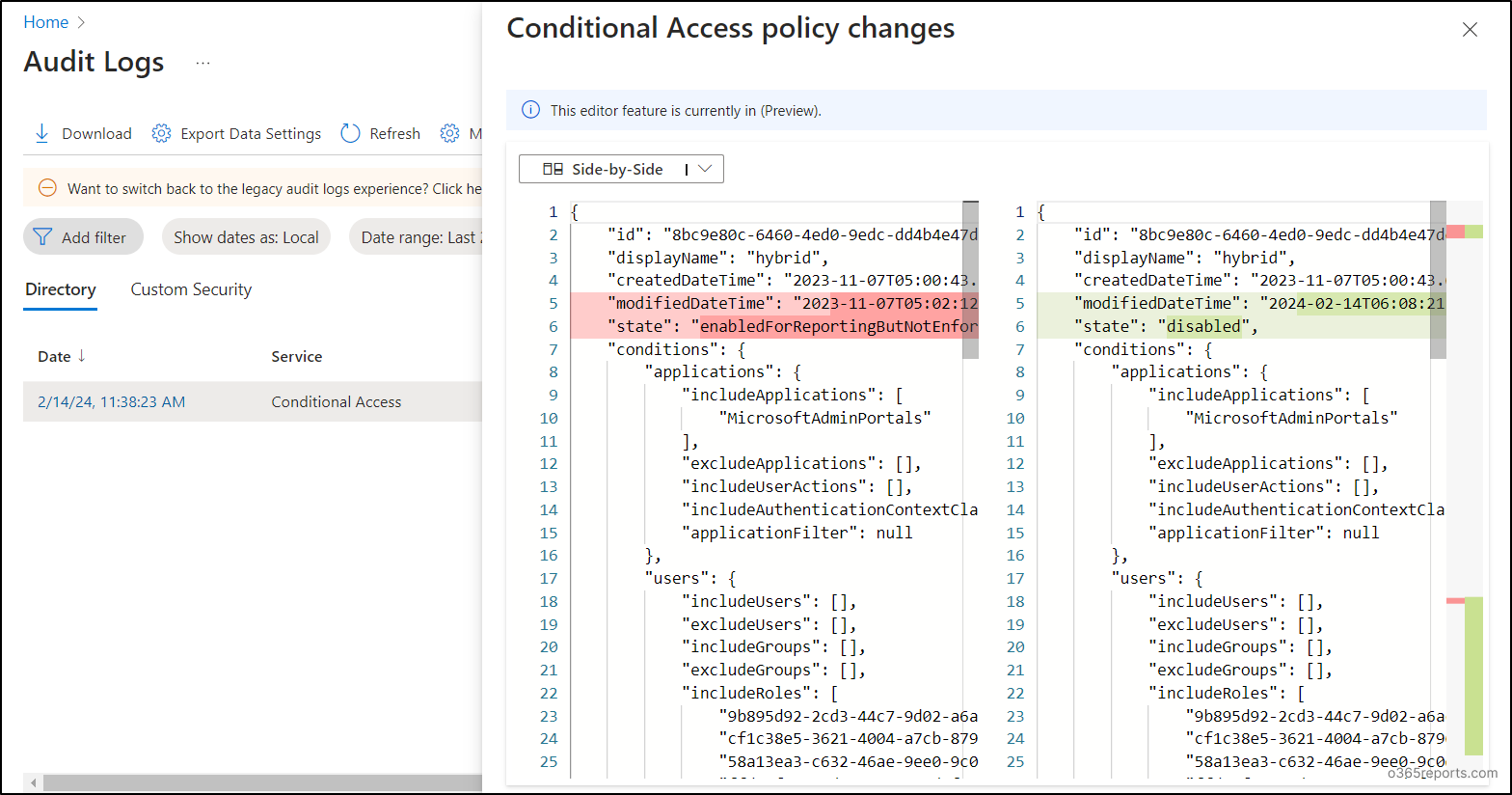
This showcases the side-by-side comparison of Conditional Access policy changes. Alternatively, you can choose the inline view to find the changes.
- Audit CA Policy Changes in Side-by-Side View:
The side-by-side view presents the old and new values alongside each other, facilitating easy comparison of Conditional Access policy modification.
- Audit CA Policy Changes in Inline View:
On the other hand, the inline view displays the values on the same page, with the modified properties highlighted in different colors for quick identification.
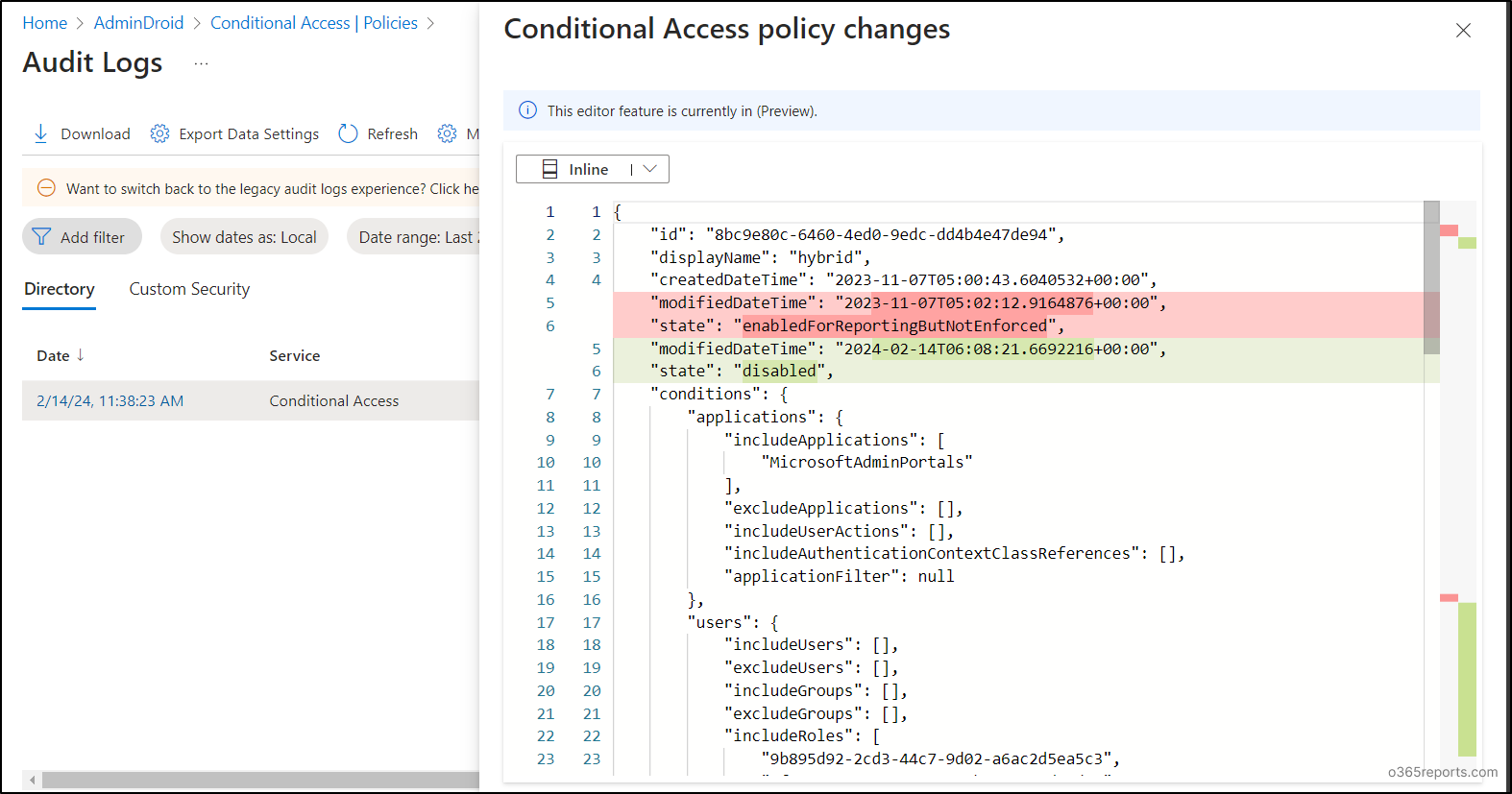
The new view feature offers a better way to audit and troubleshoot Conditional Access policy changes.
Create Alerts for Conditional Access Policy Changes:
Admins set conditional access policy with various conditions to meet security requirements. If any conditional access policy is modified suspiciously, it might lead to severe attacks. Thus, it is crucial for admins to see who changed conditional access policy and whether it is modified by a new user.
To create alerts when a conditional access policy is modified, Log Analytics is the only option. By getting instant notification on CA policy changes, you can avoid suspicious activities and harmful risks. Additionally, admins can use PowerShell to export CA policies, allowing them to review and verify policy configurations.
Benefits of Viewing Changes in CA Policy Audit Logs
Let’s explore how auditing Conditional Access policy changes with new view can be useful!
- Improved Visibility: The new view provides two viewing options, side-by-side and inline, for easy identification of changes.
- Efficient Comparison: By highlighting changes in old and new values with different colors, the new view facilitates efficient comparison of CA policy changes.
- Reduced Manual Effort: This feature reduces the manual effort of finding and tracking CA policy changes, saving time and resources for administrators.
You can also simulate how CA policies apply to a user in real time using the Conditional Access What If tool, and fine-tune your policy setup with the Conditional Access Optimization agent, which flags rarely used or overlapping policies.
These new features that allows viewing CA policy changes is great, but it’s not enough to enhance security. In order to keep the system secure, administrators need to be aware of any changes made to the policies in the first place. This is where AdminDroid Microsoft 365 Reporter comes in handy!
Effortlessly Identify Conditional Access Policy Changes with AdminDroid!
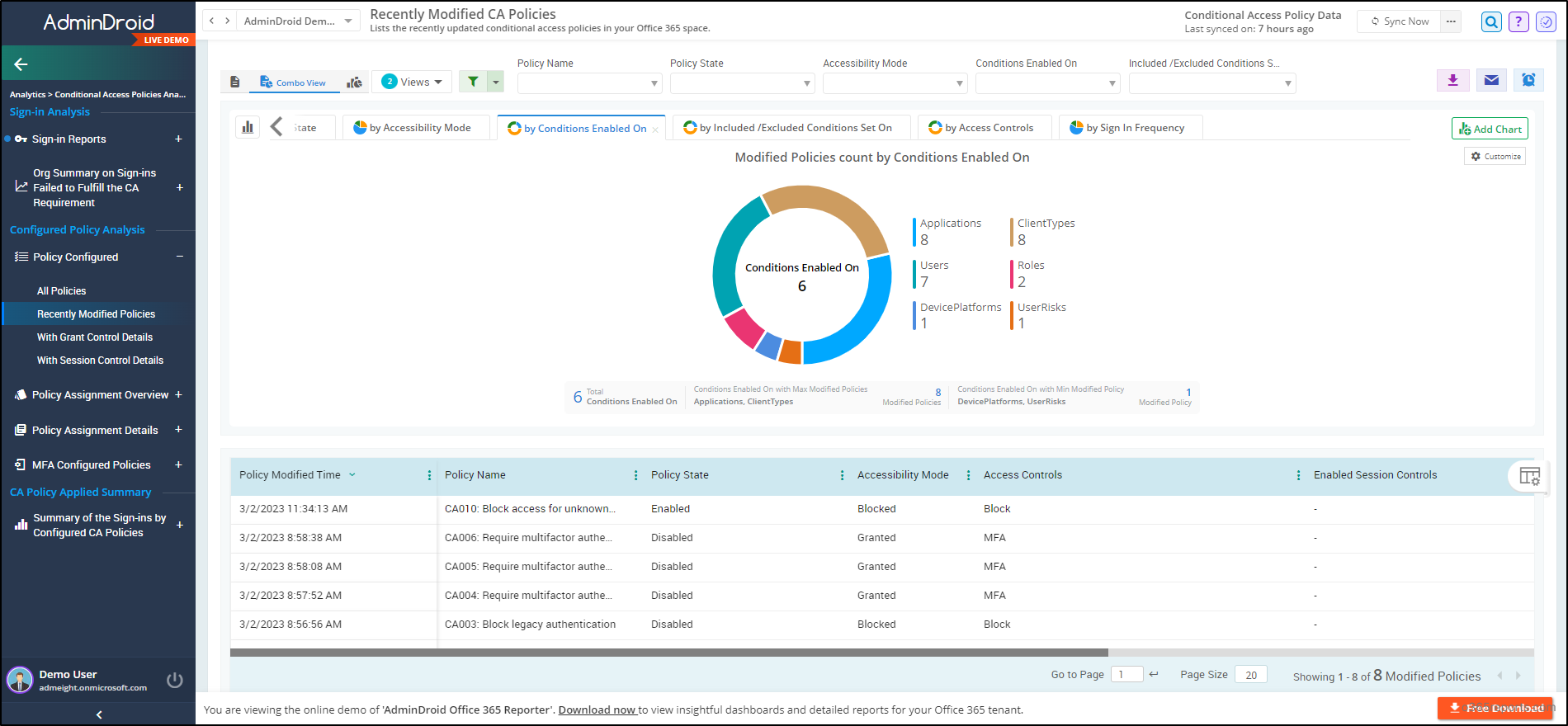
AdminDroid’s Azure AD reporting tool provides in-depth analytics on Conditional Access policies, including lists of all CA policies, recently modified, grant control & session control details, and more. AdminDroid provides detailed CA policy insights and reports including,
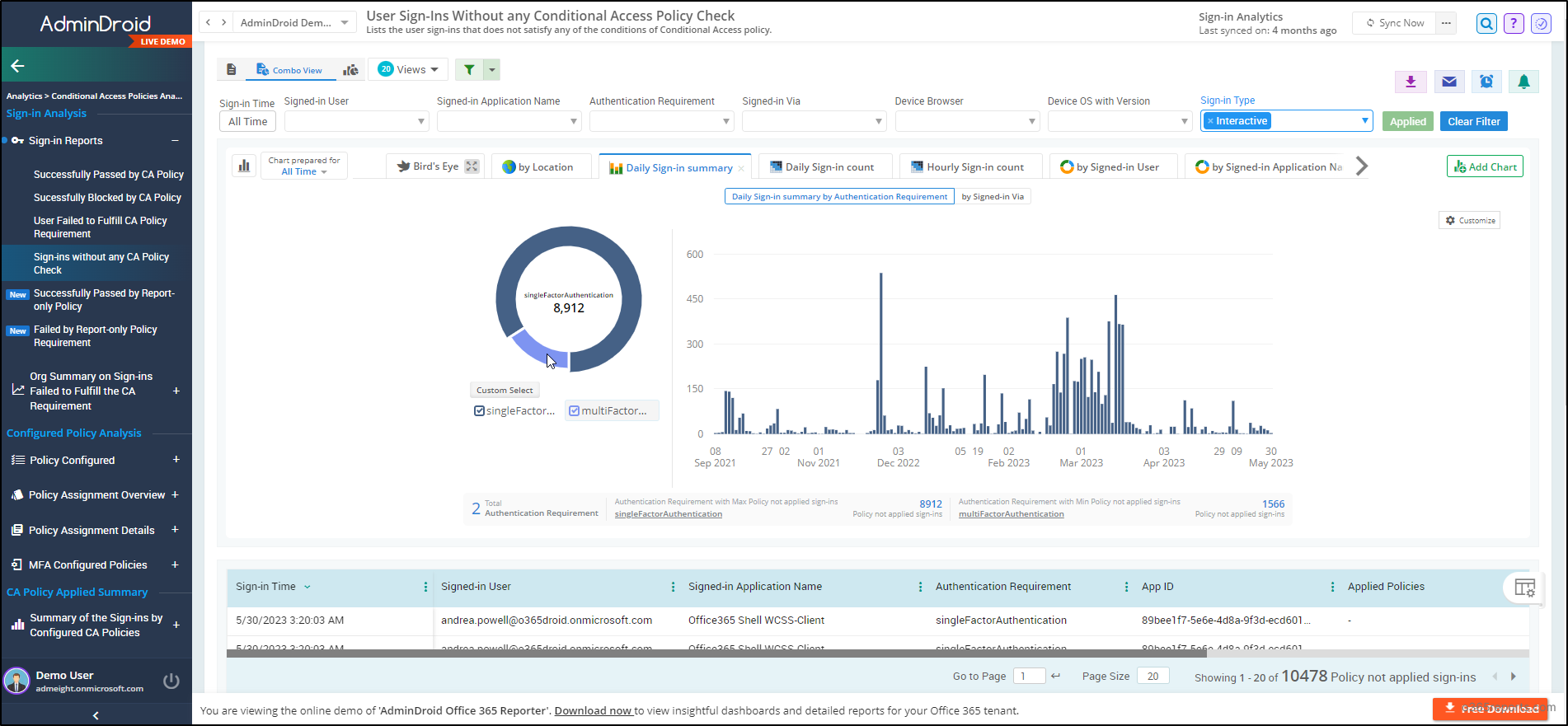
Sign-in Analysis based on CA policies
- Successfully passed sign-ins by CA policy
- Successfully blocked sign-ins by CA policy
- Users failed to fulfill CA policy requirements
- Sign-ins without any CA policy check
CA Policy Configuration Analysis
- Policies with user conditions
- Policies with group conditions
- Policies with application conditions
- Policies with role conditions
- Policies with location conditions
This is just a glimpse of the CA policy reports that AdminDroid offers! Moreover, you can create Conditional Access alerts in AdminDroid by leveraging the CA policy insights. Plus, to simplify the alert creation process, AdminDroid offers over 45+ pre-built alert policy templates, saving your time and effort.
In addition, AdminDroid provides 120+ Azure AD reports completely for free. With these reports, you can easily gain a panoramic view to enhance your Azure AD management.
AdminDroid goes beyond CA reports, offering 1800+ detailed reports and 30+ sleek dashboards covering various M365 services such as Teams, SharePoint Online, OneDrive, Exchange Online, Stream, Power BI, and Viva Engage.
Looking to simplify your Microsoft 365 administration? AdminDroid has you covered with features like quick scheduling, granular delegation, advanced customization filters, and more. Plus, you can try it out for free for 15 days! Don’t wait; streamline your admin tasks with AdminDroid today!
That’s it! The fresh perspective on auditing Conditional Access policy changes not only enhances utility but also adds a visual appeal. We encourage all admins to explore this feature within their environments and share their feedback. Additionally, you can also use Microsoft365DSC to monitor Conditional Access policy changes, and it even helps you to receive immediate alerts on policy drifts. If you have any questions or feedback, the comments section is open for discussion. Enjoy exploring and happy securing!