Blog / All Posts

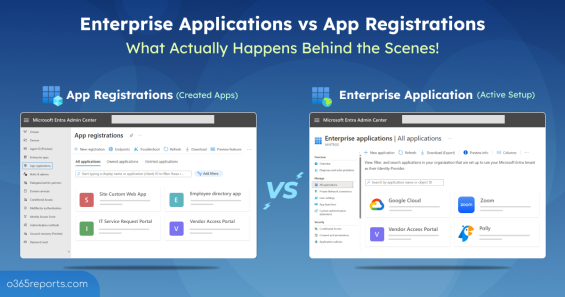
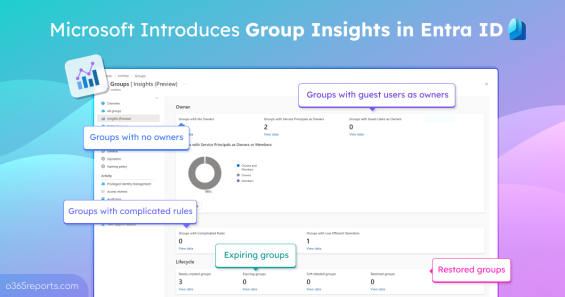
Difference Between App Registrations and Enterprise Apps
If you’ve ever opened the Microsoft Entra admin center to view your organization’s applications and asked yourself: Why does Entra have two separate sections for managing applications — App Registrations and Enterprise Applications? Why does the same app sometimes appear in two places? Why do I need both? You’re not alone! This is a common point of confusion for many M365 administrators. It usually starts when…
10 min read
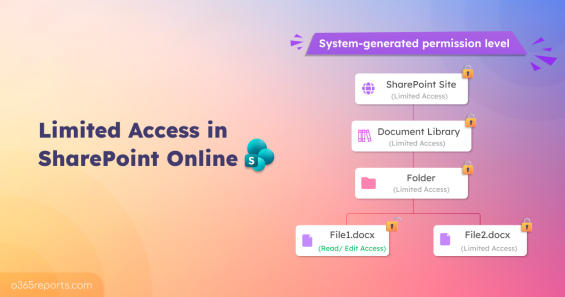
Limited Access in SharePoint Online
Summary: Limited Access in SharePoint Online is an automatically assigned permission that allows users to access a specifically shared file or folder without granting full site visibility. It is system-managed, cannot be customized, and appears when item-level permissions are created. Understanding it is essential for effective permission governance. When you…
10 min read
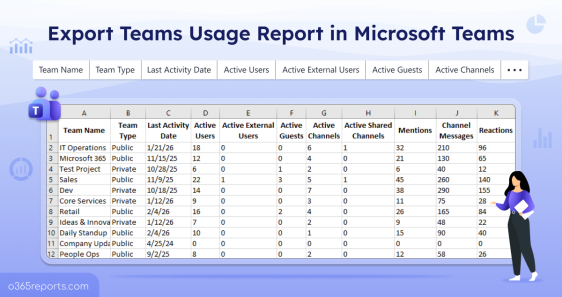
Export Teams Usage Report in Microsoft Teams
Summary: Microsoft Teams usage reporting enables administrators to monitor team activity, engagement levels, and external access to maintain governance and security. While the Microsoft 365 admin center, Teams admin center, and PowerShell provide reporting options, they come with limitations in automation and deep visibility. Using automated PowerShell scripts helps streamline…
7 min read
How to Temporarily Disable Sign-ins for Entra Applications
Summary: When reviewing a risky application, admins must decide whether to temporarily block access to the app or disable it across all tenants. This post outlines two ways to block user access (deactivation and disable user sign-ins to apps), with step-by-step actions and bulk operations. It explains the differences between…
12 min read

How to Resolve Connect-MgGraph : InteractiveBrowserCredential authentication failed: A window handle must be configured Error
Summary After a recent Microsoft update, many admins started seeing Microsoft Graph PowerShell sign-in failures with the error “A window handle must be configured.” This blog explains the root cause behind the issue and outlines four proven fixes that help restore Microsoft Graph connectivity. Recently, one of our readers dropped…
5 min read
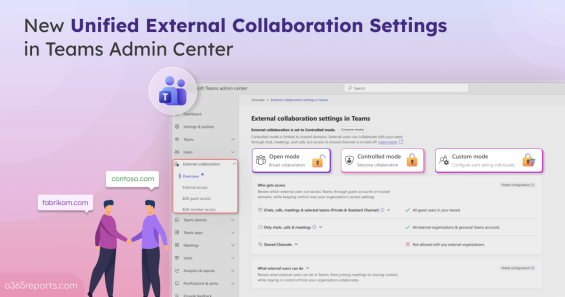
Unified External Collaboration Settings in Teams Admin Center
External collaboration in Microsoft Teams is essential but managing it is often where the real headache begins. Until now, key controls like external and guest access and B2B collaboration were scattered across multiple pages in Entra and Teams admin center. 😓 So, when a client can’t access a Teams channel,…
8 min read
What are Web Parts in SharePoint Online
If you work with SharePoint Online long enough, you quickly realize that creating a site is the easy part. The real challenge begins after the site is live, when content needs to stay relevant, and constantly updated. Users ask for announcements on the homepage; HR needs policy updates, holiday lists; executives expect key documents like guidelines, or…
8 min read

How to Configure Risk Remediation Control in Conditional Access Policy
Microsoft 365 users are frequently targeted by attacks such as anonymous IP sign-ins, unfamiliar sign-in properties, and password compromise. When such activity is detected, users are flagged as risky. Admins can review and take actions like risk remediation, dismissal, confirm compromise, or block the account. To streamline risk remediation, Microsoft introduced the Require risk remediation option in Conditional…
3 min read

Must-Read Microsoft 365 Admin Blogs: 2025 Edition
As we move into 2026, it’s the perfect time to look back at the Microsoft 365 admin blogs that created the most impact over the past year. This curated roundup brings together a diverse range of topics, from key Microsoft 365 security updates to in-depth explorations of newly released features. …
10 min read