Yesterday (Nov 1st 2022), Dropbox admitted a breach in which their 130 code repositories were exposed to attackers and revealed that it happened by phishing emails impersonating CircleCI, a code integration and delivery platform. Do you believe that lack of DMARC configuration is a potential cause of this breach? Yes, lets see how it impacts the organization. First, when I came across the news, I found that
A few thousand names and email addresses of Dropbox employees, current and past customers, sales leads, and vendors were exposed.
On October 14, the account got breached by the attackers through a phishing campaign impersonating CircleCI. The phishing link redirects employees to the fake CircleCI login page and asks for their GitHub username and password. Also, it requires users to use a hardware authentication key to pass an OTP.
How threatening! Please remember that
Not all types of multi-factor authentication are created equal, and some are more vulnerable to phishing than others.
Nowadays, the threat attackers go beyond account harvesting. They can gather MFA codes too! So, I would like to tell that every organization should configure phishing-resistant MFA to have more security. We need to consider that MFA fatigue attack is also on the rise. Dropbox reveals that using less secure MFA is one of the reasons the attacker gain access to their repositories. So, they are going to reconfigure their MFA settings in near future.
For attention to Dropbox Customers…
Dropbox said that the attackers never had access to customers’ accounts, passwords, or payment information, and its core apps and infrastructure were not affected. So, customers don’t need to worry about this.
Then, how about CircleCI?
IMO, there should be some sort of security lag in CircleCI that makes the attackers impersonate them. So, I researched in that way and found that
Missing Dmarc Configuration becomes a trump card for attackers.
DMARC is a must-have configuration, especially for third-party providers like CircleCI. When I surfed, I came to know that CircleCI has configured DMARC with a ‘none’ policy. That’s why the attackers can able to impersonate them successfully.
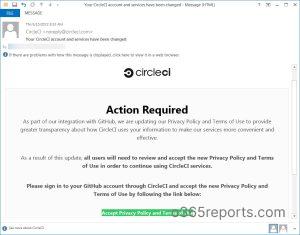
Now, they changed their DMARC configuration with a reject policy. Because domain reputation is the foremost thing that every domain owner looks for. We should adopt email authentication methods not only to secure the domain but also to ensure that our domain is not used for such attacks and to maintain our domain reputation. Learn more on how to implement email authentication methods for your domain.
Phishing Resistant MFA methods are already in place!
All major Identify Providers are already providing support for phishing-resistant MFA methods. Recently Microsoft also added support for enforcing phishing-resistant MFA via Conditional Access Policy. If you are using Microsoft 365, you should avoid using less secure MFA methods. You should adopt phishing-resistant MFA.
Also, for your attention, during this cybersecurity awareness month, AdminDroid published a series of blogs that gives Microsoft 365 essential security checklists to make your organization remain secure. In the series, we have covered both DMARC configurations and Phishing Resistant MFA implementation. The campaign helped thousands of organizations to make a move to the necessary security settings. You can explore the compilation of all the essential security settings for Microsoft 365 in our final blog on Microsoft 365 Security Hardening for Reduced Attack Surface. Be more secure in the so-called modern yet threatening world!