Recent months have seen MFA fatigue attacks in multiple large enterprises like Uber, Microsoft, and Cisco. All these attacks involved social engineering and theft of employee credentials to gain access to internal VPNs and privileged user accounts in the organization. Taking these incidents into account, Microsoft announced several Multi-factor Authentication strengths to safeguard the organization way back in November 2021.
“New MFA Enhancement Alert!”
Finally, the wait is over. Advanced Microsoft Authenticator security features are now generally available. It is expected that number matching and additional context features will be implemented for all Authenticator users by the end of February 2023. Now, let’s explore the advanced MFA settings that are available in Azure AD.
Why do we Need Advanced MFA Settings Enabled?
Today, every organization enables basic multi-factor authentication and believes they are protected. No, that’s not what’s happening. It has become apparent from the recent MFA fatigue attacks that SMS, phone calls, and tap approvals are not remarkably effective as a security measure.
In times of breach, the attacker will repeatedly push out MFA notifications to convince the user to accept the MFA prompt. At some point, victims become so distraught that they accidentally click on the ‘Approve’ button or simply accept the MFA request. This will stop the deluge of notifications they have been receiving. To prevent such accidental approvals, Microsoft came up with advanced MFA push techniques to tackle threat vectors.
Advanced MFA Settings in Azure AD that you must Know:
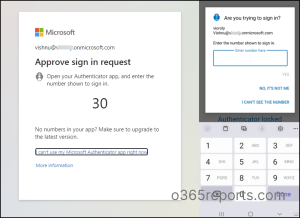
1. Number Matching with Microsoft Authenticator
Number matching prevents accidental approval by requiring the user to type in a two-digit code from the login screen to their authenticator app. With the Authentication app, admins can require users to enter the number displayed on the sign-in screen when approving an MFA request.
Steps to Enable Number Matching in Azure AD:
- Log into the Microsoft Azure portal.
- Navigate to Azure Active Directory –> Security –> Authentication Methods
- Select Microsoft Authenticator Method.
- Under the Basics tab, select Yes to enable MFA.
- Specify all users or certain users based on requirements under Target tab.
- Then, set the authentication mode to Any/Push.
- Switch to Configure Tab.
- Set the Enabled status to allow number matching.
- Save it after choosing whom to include or exclude from number matching.
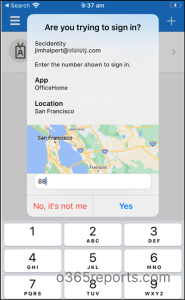
2. Geographic Location with MFA Push Notifications
Other than number matching, showing users additional content like MFA location in authenticator notifications will also reduce accidental approvals. By looking at the user’s IP address, this feature will reveal which application they are signing into and where they are signing in from.
Steps to Enable Geographic Location in Azure AD
- Log into the Microsoft Azure portal.
- Navigate to Azure AD Directory –> Security –> Authentication Methods.
- Select Microsoft Authenticator Method.
- Under the Basics tab, select Yes to enable MFA.
- Specify all users or certain users based on requirements under Target tab.
- Then, set the authentication mode to Any.
- Switch to Configure Tab.
- Set the Enabled status to show geographic location in the push and passwordless notifications.
- Save it.
3. Phishing Resistant MFA
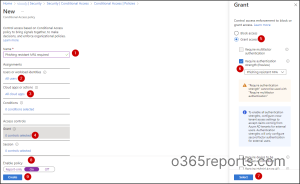
Authentication strengths are an additional control in conditional access policies. This newly released access control is now generally available and can be used to get over weak authentication methods (SMS, phone calls) and to limit external access to sensitive applications. A conditional access authentication strength allows admins to specify which combination of authentication methods can be used to access a resource.
For example, the in-built Phishing-resistant MFA strength allows the following combinations.
- Windows Hello for Business (or)
- FIDO2 security key (or)
- Azure AD Certificate–Based Authentication (Multi-factor)
To specify an authentication strength, admins must create a conditional access policy enabling ‘Require authentication strength’.
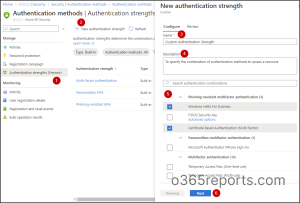
At times, admins may require different authentication methods for different circumstances. Apart from the built-in authentication strengths, admins can create up to 15 of their own custom authentication strengths to meet their requirements.
Steps to Create Custom Multi-Factor Authentication Strength
- Log into the Microsoft Azure portal.
- Navigate to Azure AD –> Security –> Authentication Methods –> Authentication strengths.
- Select New authentication strength.
- Name your policy and give a description.
- Choose the necessary combination of multifactor authentication.
- After reviewing, save it.
How to Check Which Users Have Registered for MFA?
In an organization, it is imperative to ensure that all users comply with current MFA standards. Microsoft has come up with the following significant reports where you can manage MFA registration and ensure 100% compliance across your organization. You can also use these reports to troubleshoot MFA issues.
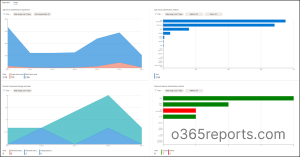
1. Get MFA Authentication Methods Activity Reports
Navigate to Azure Portal –> Azure AD –> Security –> Authentication Methods –> Activity
This new report helps you track MFA adoption and manage the authentication methods of users in your organization.
Registration – This tab shows how many users have registered for each authentication method. By clicking on a specific authentication method, you can see which users have registered for that method.
Usage – This usage report provides an overview of the authentication methods used to sign in and number of password resets. Under the usage tab, graphs on the following authentication information will be obtained.
- Sign-ins by authentication requirement
- Sign-ins by authentication method
- Number of password changes and resets
- Password resets by authentication method
Note – An Azure AD Premium P1 or P2 license is required to access usage and insights.
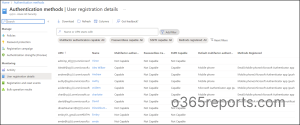
2. Get MFA User Registration Details Report
Navigate to Azure Portal –> Azure AD –> Security –> Authentication Methods –> User Registration Details
You can use the user registration details report to view the users capable of Multi-Factor Authentication (MFA), password authentication, and Self-Service Password Reset (SSPR) authentication in your organization. Further, you can check who has registered those authentication methods. Apart from overall registration numbers, this report provides info on registration success and failures by the authentication methods. Admins can use this report to determine which method is used the most between SSPR and MFA in their organization.
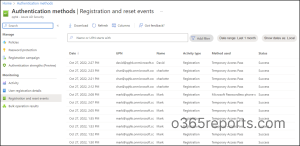
3. Get MFA Registration and Reset Event Reports
Navigate to Azure Portal –> Azure AD –> Security –> Authentication Methods –> Registration and Reset events
Here, admins can fetch the details of MFA registration and reset events up to the last 30 days along with the method used, status, activity type, and time. It is a well-common fact that when a user is compromised, an attacker may register their own MFA to access the account. In times of hack, registration and reset events will be a great spot to examine if the new registration events have occurred recently.
Though MFA is a real concern, there are several ways to protect against it as well. In the context of Microsoft 365, MFA is a major part to prevent attackers from breaking into tenant accounts and compromising user data. Like advanced MFA settings, new conditional access authentication context in CA policies is also introduced to granularize control over the organization’s sensitive information. It’s believed that MFA settings in Azure AD will continue to evolve at an even greater pace, with Microsoft Entra.
Deploy MFA and stay harder to break through!
Gain Insights into MFA Implementation with AdminDroid’s Comprehensive Reporting
It is true that native MFA reports help you understand the adoption of Multi-Factor Authentication (MFA), password authentication, and Self-Service Password Reset (SSPR) in the organization. But to access these reports, you will need an Azure premium P1 or P2 license which is costly. There comes AdminDroid where you can access a comprehensive range of reports on MFA authentication methods that provide valuable insights into your organization’s MFA implementation.
AdminDroid’s MFA Reports on Authentication Methods cover the following areas:
- Organization Sign-Ins by Authentication Method – Report on orgs authentication methods.
- User Sign-Ins by Authentication Method – Report on user authentication methods.
- Successful MFA User Sign-Ins – Ensures MFA is used correctly and effectively.
- Failed MFA User Sign-Ins – Identifies unauthorized access and MFA challenges.
- MFA User Sign-Ins via Text Message – Tracks MFA sign-ins verified via text message.
- MFA User Sign-Ins via Mobile App – Tracks MFA sign-ins verified via mobile app notification.
- MFA User Sign-Ins via Verification Code – Tracks MFA sign-ins verified via verification code.
- MFA User Sign-Ins via Phone Call – Audits MFA sign-ins authenticated via phone call.
- MFA Configuration via Conditional Access Policies – Tracks MFA configuration via CA Policies.
- MFA Configuration via Azure AD Portal – Tracks MFA configurations via Azure AD portal.
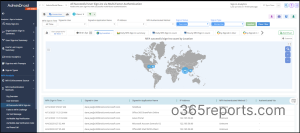
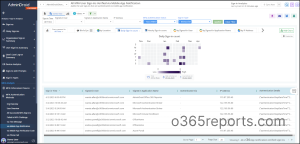
In addition to this, AdminDroid Azure AD reporting tool offers reports on MFA Activation, MFA Usage, MFA Compliance, MFA Device Details, MFA User Details, MFA configured CA policies, etc.
By providing in-depth reporting on all aspects of MFA, AdminDroid can help you make informed decisions about how to improve your organization’s security posture.
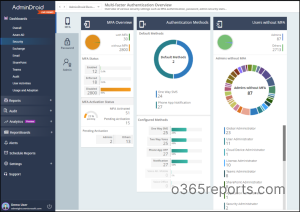
Microsoft 365 MFA Dashboards
Apart from reports, AdminDroid has a dedicated MFA dashboard that provides an overview of:
- Users’ MFA status (including their activation and authentication status)
- Authentication methods they use (both default and alternate methods)
- Admins who do not have MFA enabled.
This customizable dashboard allows you to tailor your security monitoring to your organization’s specific needs!
AdminDroid Azure AD Management tool goes beyond MFA reporting & auditing, it also offers 1800+ pre-built reports for a wide range of Office 365 services, including Azure AD, Exchange Online, SharePoint Online, Microsoft Teams, and so on.
- These reports provide comprehensive insights and auditing information, allowing you to gain a deeper understanding of your organization’s performance.
- With AdminDroid’s AI-powered graphical analysis, you can easily visualize complex data and extract valuable insights in a visually appealing manner.
- Whether you’re looking to monitor user activity, track service usage, or ensure compliance with regulations, these reports offer the in-depth information you need to make informed decisions.
Choose AdminDroid for your Office 365 reporting and auditing needs and experience the power of data-driven insights in a simple, intuitive interface.
Download AdminDroid – Microsoft 365 reporting tool and see how it works.






