Recently, Microsoft announced a significant update: “We’re retiring 3DES (Triple Data Encryption Standard) in Office 365”.
3DES cipher is mostly used for TLS/SSL to encrypt HTTPS and SSH traffic. Since 2016, it has been marked as vulnerable due to SWEET32 attack (Attackers recovered small portions of plaintext when encrypted with 3DES) and planned complete usage deprecation before 2023. To provide security to data, Microsoft made changes in TLS service.
Before moving into how to plan for 3DES removal, let’s see about TLS and how 3DES removal impacts TLS.
What is TLS?
Transport Layer Security (TLS) is a cryptographic protocol that provides secure communication over a network. For ex, Websites uses TLS to secure all communications between their servers and browsers/clients. There are currently four versions of TLS protocol in use today: TLS 1.0,1.1,1.2 and 1.3.
Why Office 365 moving to TLS 1.2?
Microsoft is planning to move all of its online services to TLS 1.2 or a later version to provide best-in-class encryption to its customers. As of February 28, 2019, Microsoft will begin retiring 3DES. As a result, if your connections are currently using a 3DES cipher suite, they will fail when 3DES cipher suites are disabled. TLS versions 1.0 and 1.1 include cipher suites based on the 3DES algorithm. Office 365 will retire TLS 1.0 and 1.1 starting June 1st, 2020 in Worldwide and GCC Environments. So, all client-server and browser-server combinations must use TLS 1.2 or 1.2+ to maintain a connection to Office 365 services.
Stay informed with Upcoming Microsoft 365 changes and end-of-support milestones.
How does this affect me?
Office 365 stopped support for TLS 1.0 and 1.1. Hence Microsoft will not fix new issues that are found when connecting Office 365 by using TLS 1.0/1.1. To ensure uninterrupted access to the Office 365 services, you need to update TLS to 1.2 or later version. If you want to get a list of users who uses TLS 1.0/1.1, you can make use of Microsoft’s TLS deprecation report.
July 2020 Update: Microsoft has announced TLS 1.0 and 1.1 deprecation in Office 365 to be October 15, 2020.
Due to the Corona pandemic, Microsoft has temporarily halted deprecation enforcement of TLS 1.0 and 1.1. Now, Microsoft has announced update regarding TLS 1.0 and 1.1 deprecation.
Office 365 TLS Deprecation Report:
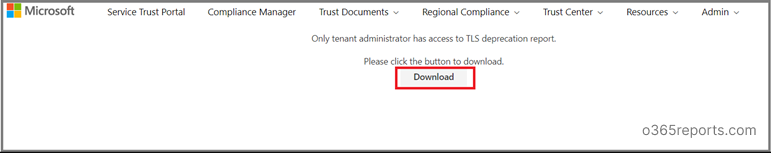
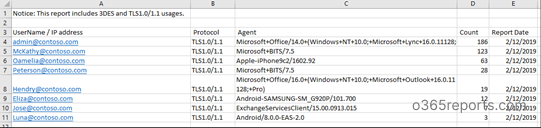
To ease your work, Microsoft has provided a new report to track users, devices or applications that use TLS 1.0/1.1 or 3DES. You need to be a tenant administrator to generate a TLS deprecation report. The report gives the following information
- Usernames/IP addresses of the users/devices connecting to Exchange using TLS 1.0/1.1 or 3DES
- Protocol/cipher used for the connection – this will either be TLS 1.0/1.1 or 3DES
- The user agent string that is being used for this connection – this gives information about the type of device used for the connection
To download TLS deprecation report directly, you can use this Microsoft’s quick link: https://servicetrust.microsoft.com/AdminPage/TlsDeprecationReport/Download.
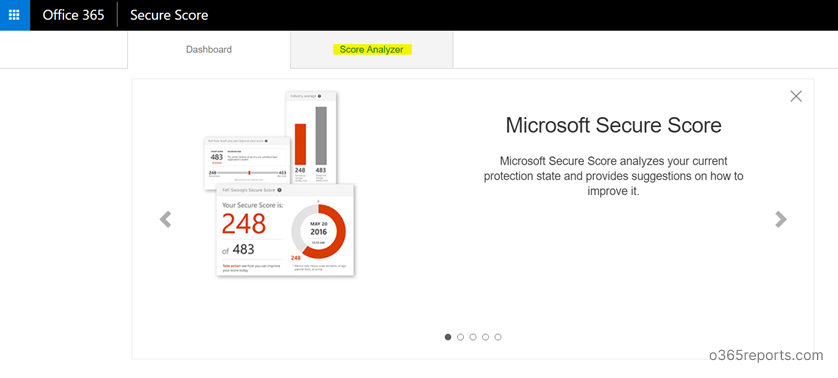
Alternatively, to download the TLS deprecation report through Microsoft secure score portal, follow the below steps.
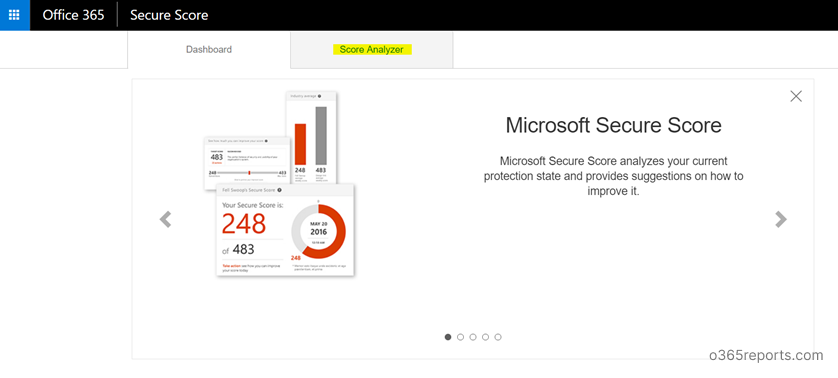
Step1: Login to Microsoft’s secure score: https://securescore.office.com and click on “Score Analyzer”.
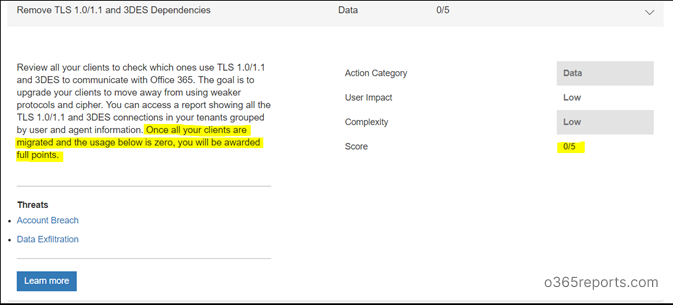
Step2: Scroll down to ‘All Actions’ . Search for “Remove TLS 1.0/1.1 and 3DES Dependencies” in Completed actions/Incomplete Actions. If you scored 5/5, You have already moved to TLS 1.2. Else, you need to plan for a migration.
Step3: Click on the ‘Learn more’ button to get details on who is connecting using TLS 1.0/1.1 or 3DES. It will launch a flyout where you can click on ‘Launch now’.
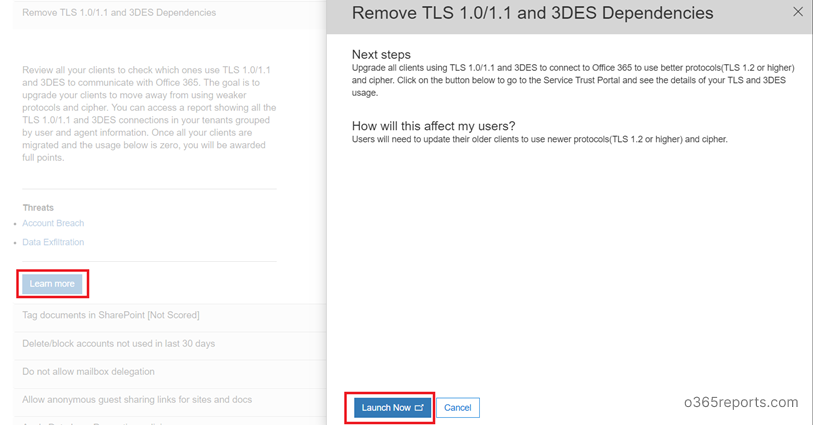
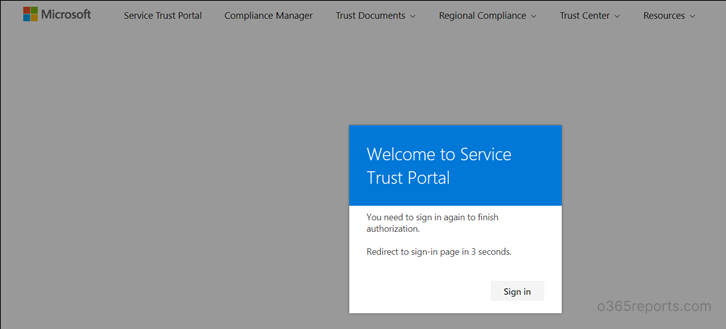
Step4: ‘Launch Now’ will take you to the Secure Trust Portal (http://servicetrust.microsoft.com). Login and then click ‘Download’ to get TLS-Deprecation-Report.csv. Or you can use quick link to download Office 365 TLS deprecation report.
Step5: If you have users or devices listed under TLS1.0/1.1, start planning for an upgrade.
The TLS deprecation report is refreshed daily. If you have made any changes and updated any clients/devices, you would need to wait for 24hrs to see this change in the reports.
As already mentioned, you can get a TLS usage report using TLS deprecation report. If you need more detailed TLS usage report for SMTP in Exchange Online, you can use a TLS usage report from the Security & Compliance Center.
TLS Usage Report for SMTP in Exchange Online
Email clients uses different protocols to submit email messages. The SMTP Auth (SMTP Authenticated Submission) protocol is primarily used by devices and applications that send automated messages on behalf of customers. To protect against the disclosure of credentials, TLS is mandatory for SMTP Auth. So, when TLS 1.0 is disabled, no messages can be sent from devices or clients that do not support TLS 1.2.
You can use SMTP Auth Clients Reports to know which users are using this protocol, the volume of message sent, and the version of TLS used to connect to Office 365. Using these data, you can determine which clients and servers are still using TLS1.0 and TLS1.1 to connect to the various email protocol endpoints in Exchange Online.
SMTP Auth Clients Reports – TLS 1.0 Deprecation
1.To download SMTP Auth Clients Reports, you can go here: “Security & Compliance > Mail Flow > Dashboard- for SMTP Auth Clients Report.”
Alternatively, you can go directly using link: https://protection.office.com/mailflow/dashboard
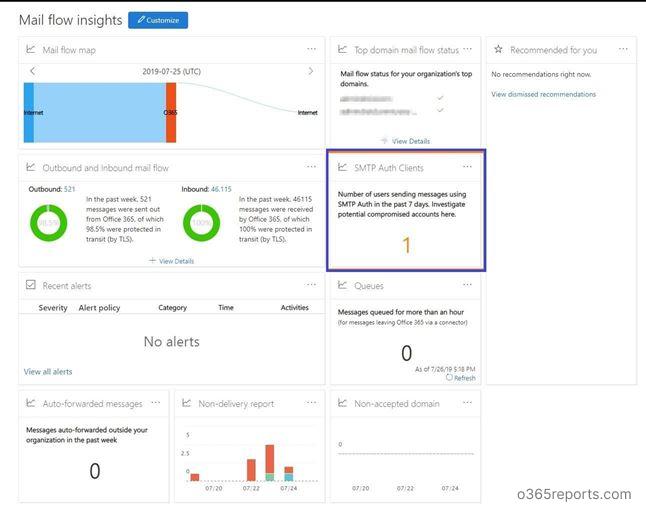
2. Click ‘SMTP Auth Clients‘, it will show pivot for TLS version usage.
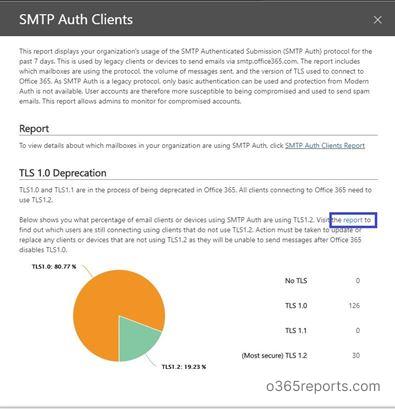
3. Click ‘report’ link as shown in above screenshot.
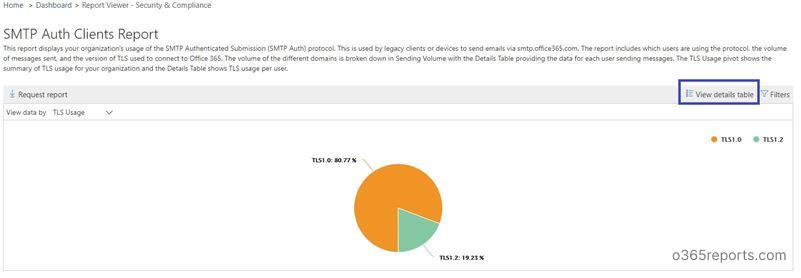
The TLS pivot shows the summary of TLS usage for your organization. Click ‘View details table’. It will show TLS usage per user.
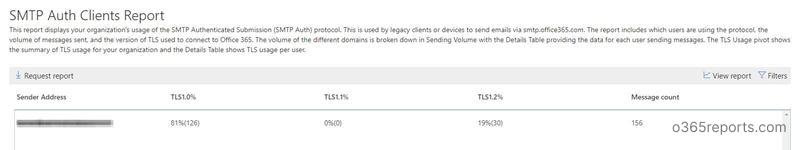
SMTP Auth Client reports apply to SMTP related mail flow and submission alone. For other protocols, you need to refer TLS deprecation report.
If you are reading this blog because you are planning to migrate TLS to 1.2, chances are you already read and executed the Microsoft guidance to make your connection guarded. If so, please share your experience/difficulties during TLS 1.2 migration in the comment section to assist other admins.
Update History:
July 2019 Update: “Office 365 will retire TLS 1.0 and 1.1 starting June 1st, 2020 in Worldwide and GCC Environments” which means that all connections to Office 365 using the protocols TLS 1.0 and TLS 1.1 will not work After June 1st. So, you must migrate clients and devices to TLS 1.2 or TLS 1.2+ prior to June 1, 2020.
April 2020 Update: Due to the Corona outbreak, Microsoft has temporarily halted the the TLS 1.0 and 1.1 deprecation
July 2020 Update: Microsoft announced TLS 1.0 and 1.1 retirement date in Office 365 to be October 15, 2020.
Nov 2021 Update: From Jan 03, 2022, Microsoft retiring TLS 1.0 and 1.1 usage for Direct Routing SIP interface.
Note:
- To know detail about which versions of TLS supported on Windows, refer: https://blogs.msdn.microsoft.com/kaushal/2011/10/02/support-for-ssltls-protocols-on-windows/
- To know detail about which versions of TLS supported on browsers, refer: https://en.wikipedia.org/wiki/Transport_Layer_Security#Web_browsers